An overview of blockchain privacy mechanisms and how Zerocoin in Zcoin $XZC (not Zcash) stacks up
This post will hopefully give you a brief overview of the major blockchain privacy mechanisms that are implemented in cryptocurrencies today and in particular how the Zerocoin protocol used in Zcoin stacks up.
Blockchain privacy is a particularly difficult thing to achieve as a public blockchain is designed so that all transactions are transparent and the supply of coins can be publicly verified. Privacy mechanisms have to ensure that these elements are preserved so it’s a conflicting mix of protecting privacy while maintaining public verifiability. To understand the innovation behind Zerocoin, we need to examine the history of blockchain privacy.
Cryptocurrency Tumblers and Coinjoin
As used in: Dash, PIVX
Pros:
- Works on top of most cryptocurrencies without the need for specific consensus rules
- Relatively simple to implement
- Lightweight
Cons:
- Basic anonymity
- Requires mixers to be online
- Earlier implementations involve trust in a third party mixer
One of the first methods people sought to achieve this was through the use of cryptocurrency tumblers. They work by mixing funds with others by sending your coins to other people and then giving their coins to you. An easy way to visualize this is a group of people each putting the same number of coins into a common pot, mixing it up and then taking the same amount of coins back from which you started with. The idea is that it is now hard to prove whose coin originally belonged to who thus providing some degree of privacy. This comes with several drawbacks, foremost that you need to trust the tumbler not to steal your coins.
Coinjoin is an improvement of this mixing idea and removes the possibility for the tumbler to steal the coins, it was popularly used in Darkcoin (now known as Dash). However there are still many drawbacks with Coinjoin.
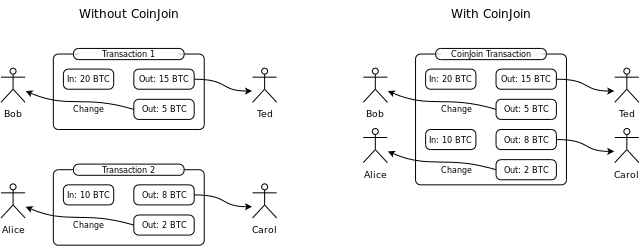
- You need to trust the tumbler for your anonymity as the mixer can log identifiable information and knows how the mix is happening along with each user’s input address and the address they are receiving coins to. This issue can be avoided by using blind digital signatures but then the anonymity of coinjoin relies strongly on the possibility to connect to the tumbler in an anonymous manner, e.g., via the Tor network.
- It requires people involved in the mixing to be online for a mixing transaction to happen. If no one wants to mix for the right denominations, your mix can be delayed.
- The anonymity is limited by the amount of people you mix with. A typical round of Dash’s privatesend mixing involves 3 participants only though this can be repeated.
- Even with multiple rounds of CoinJoin mixing, recent research (https://arxiv.org/pdf/1708.04748.pdf) shows that a user’s wallet can be identified if they are not careful with browser cookies when making payments because mixing only obscures the transaction links between addresses but does not break them completely.
- It is easy to disrupt a run of Coinjoin and delay the completion of the coinjoin transaction for the other participants.
Other improvements to CoinJoin such as CoinShuffle++ removed the need for a trusted third party but are still subject to the other drawbacks of CoinJoin namely a limited anonymity set and the requirement that participants are online.
The main benefit of Coinjoin type schemes is that they are relatively simple and work on top of the cryptocurrency without the need to use specific consensus rules. With appropriate precautions, CoinJoin can provide a basic degree of anonymity.
Cryptonote and Ring Signatures
As used in: Monero
Pros:
- No need for a mixer and mixing is done automatically
- Can be implemented with privacy on by default
- Anonymity increases as time passes as outputs become the new inputs of new mixes
- Hides transaction amounts when implemented with RingCT
- Well researched cryptography
Cons:
- Scalability issues because of large transaction sizes and a non prunable blockchain
- Risks of blockchain being deanonymized in the future or through incorrect implementations
- Cannot take advantage of existing Bitcoin ecosystem and requires separate integration work
- Ring size is practically limited
The next anonymity scheme we will explore is ring signatures as used in Cryptonote currencies such as Monero which greatly improves anonymity over Coinjoin type schemes. A ring signature works by proving someone signed the transaction from a group of people without revealing which person it was. One common proposed use case of ring signatures is for it to be used to provide an anonymous signature from a “high ranking White House official” without revealing which official signed the message.
Cryptonote uses ring signatures in a way whereby a user can craft a transaction and use the outputs of other similar transactions on the blockchain automatically to form the inputs to a ring signature transaction so that it is unclear which input belongs to the person actually doing the transaction. It does this automatically without requiring other users to specify that they wish to mix and does not need to wait for other people to provide funds since it’s just scanning the blockchain for those outputs to use. As there is no mixer, there’s no mixer you need to trust. Monero also recently implemented RingCT (Ring Confidential Transactions) which hides transaction amounts as well.
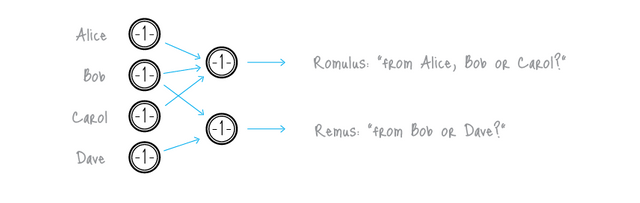
The main drawback of Cryptonote is that its transactions especially with RingCT are very large occupying several kilobytes and this greatly increases the amount of storage space required to store the blockchain. There currently isn’t any way to prune spend outputs in a Cryptonote blockchain like in Bitcoin. Using an entirely different codebase than Bitcoin also means third parties have to do more work to integrate Cryptonote into their existing ecosystems.
Ring signatures as currently implemented in Cryptonote currencies also have limitations in terms of practical ring size (the number of other outputs you are taking) as the size of a transaction grows linearly as the ring size increases. This is why by default Monero has a relatively small default ring size of 4. In fact, using a different ring size then the default might unintentionally deanonymize you by highlighting it. This means on a per transaction basis, the anonymity is limited by the number of participants in the ring. Blockchain analysts although they might not be able to prove transactions are linked, they can calculate the odds that they are.
Another criticism of Cryptonote is that if there’s a weakness in its ring signature implementation or a reasonably powerful quantum computer becomes feasible, the entire blockchain history is deanonymized and retroactively exposed. This cannot be fixed after the fact. In fact, a flawed implementation in a Cryptonote currency called Shadowcash allowed for its blockchain to be deanonymized in its entirety.
It is also to be noted that with RingCT which hides transaction amounts, this sacrifices supply auditability. Supply auditability means the ability to verify that no new coins are being secretly generated and to know exactly how many coins exist at a point in time. In Monero’s implementation of RingCT, someone who breaks the discrete logarithm that underpins RingCT can forge coins without anyone knowing it, granted it is probably very hard to do so with current knowledge and technology.
Despite these drawbacks, Cryptonote today has proven itself to be one of the better and well reviewed privacy technologies out there and the only instances where it has been publicly deanonymized arose from improper implementation such as the Shadowcash fiasco or through the use of mixin-0 transaction in Monero which resulted in a cascade effect that rendered 87% of inputs traceable (https://eprint.iacr.org/2017/338) (which were subsequently mitigated for newer transactions). Cryptonote solves many of the problems of cryptocurrency tumblers and offers good anonymity at the cost of scalability with large transaction sizes and a non prunable blockchain.
Zerocoin and Zcoin
As used in: Zcoin
Pros:
- No need for a mixer
- Very high anonymity in the many thousands (if not more) with a single mint and spend transaction and completely breaks transaction links between addresses.
- Retains supply auditability
- Uses well researched cryptography
Cons:
- Proof sizes are currently large
- Requires a trusted setup
- Incorrect implementation or leakage of trusted setup parameters can lead to forgery of coins.
- Some care is required when doing Zerocoin mints and spends.
We now come to Zerocoin as implemented in Zcoin. Unlike the previous anonymity schemes which involve obscuring the real transactions with other inputs or transactions, the Zerocoin protocol completely breaks the transaction links between coins through the use of zero knowledge proofs.
In simple terms, a zero knowledge proof is a proof you did something or know something without revealing any other information other than you did it. For example, proving that you know a password without actually revealing the password.
Zerocoin works by allowing you to burn coins up (otherwise known a Zerocoin mint) and then later redeem an equivalent number of brand new coins (known as a Zerocoin spend). These coins appear with no prior transaction history and are similar to newly mined coins. The zk-proof is used to prove that you indeed burnt coins without revealing the specific coins that you burnt and therefore are entitled to redeem an equivalent number of new clean coins.
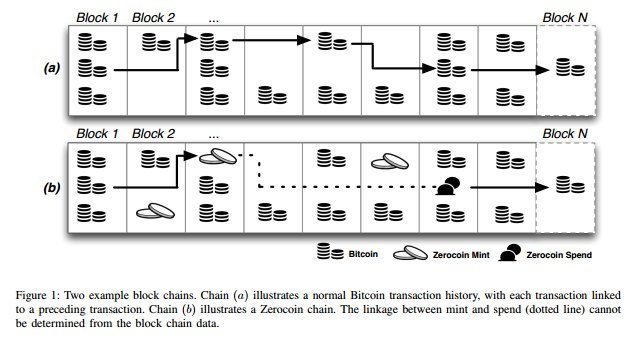
This means that unlike in Coinjoin and Cryptonote where the anonymity set is limited by either the number of participants or the ring size, Zerocoin would allow you an anonymity set of every other person who has done a Zerocoin mint of a particular denomination and achieve this immediately. This allows the anonymity set to scale into the many thousands with a single Zerocoin mint and spend cycle. Also the coins truly have their transaction links broken as they appear as completely brand new coins compared to merely being obscured through previous methods.
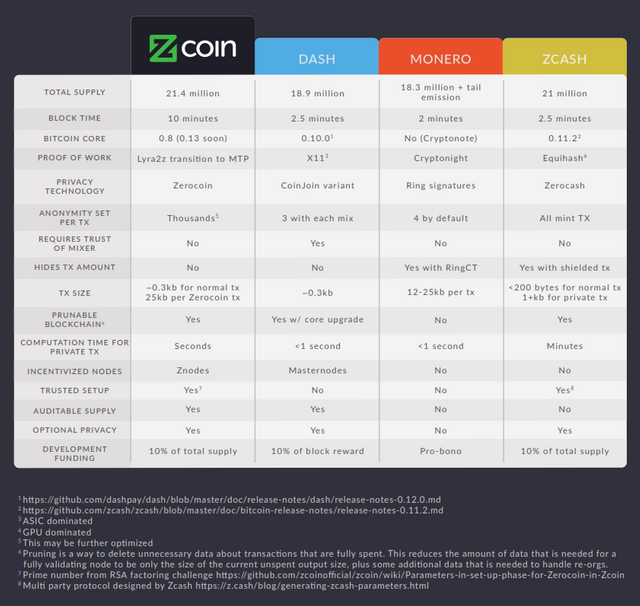
This anonymity scheme is not without some drawbacks. In return for the huge anonymity set and breaking of transaction links, Zerocoin requires a one time trusted setup to generate initial parameters. In Zerocoin these are two very large prime numbers that need to be destroyed. Knowledge of these two large prime numbers would allow someone to forge Zerocoin spends and create coins out of thin air. To mitigate this, Zcoin uses parameters from the RSA Factoring Challenge held in 1991 where they took special steps to destroy the prime numbers and had a USD200,000 bounty to successfully factor it for 16 years before the challenge was ended. Till today the RSA-2048 parameters used remain to the best of our knowledge unfactored and 2048 bit RSA remains widely used today having stood the test of time at least until the advent of quantum computing.

It is worth noting that the knowledge of these two primes or successful factoring will not compromise the anonymity of Zerocoin merely allowing the forging of coins. Additionally this is mitigated that Zcoin’s supply is auditable so the forging of coins can be detected. In fact due to a bug in the implementation (and not from the breaking of RSA), the forging of coins actually happened to Zcoin but was thankfully detected and stopped. It goes to show how in zero knowledge proof coins which involve some form of burning and creation of new coins, supply auditability is particularly important.
Another limitation of Zerocoin is that fixed denominations need to be used for minting and spending and the zero knowledge proof sizes for a Zerocoin spend are relatively large at 25 kb, comparable to a RingCT transaction. It is to be noted that unlike in Cryptonote whereby all transactions are to be of this size, only Zerocoin spend transactions occupy this amount of space with normal transactions occupying the same size as Bitcoin transactions. Zerocoin spend transactions are also comparatively computationally intensive to verify taking about half a second to do so.
Also incorrect use or predictable use of Zerocoin mint and spend transactions such as always minting and spending at regular intervals or using the same IP address for a mint and spend can possibly compromise anonymity thus some care is required.
Summing up, Zerocoin offers very strong anonymity with a huge anonymity set with no transaction linking but currently requires a trusted setup, additional storage on the blockchain and additional computational resources to verify. Despite this, there is research that show that removing trusted setup and reducing proof sizes are possible with Zerocoin through the use of the Sigma protocol and the Zcoin team are currently researching and evaluating its use further.
Zerocash and Zcash
As used in: Zcash, Zencash, Komodo
Pros:
- Potentially the best anonymity set encompassing all coins minted and breaks transaction links between addresses.
- Proof sizes are small and fast to verify
- Hides transaction amounts
- No need for conversion to a base coin and anonymized coins can be sent directly to each other.
Cons:
- Private transactions take a while to generate (almost a minute on a decently powerful computer)
- Complicated trusted setup that has to be done by the developers.
- Incorrect implementation or leakage of trusted setup parameters can lead to forgery of coins.
- Supply cannot be audited therefore forgery can be very difficult to detect.
- Uses relatively new cryptography
The final anonymity scheme we will consider is the Zerocash protocol as used in ZCash. Zerocash builds on the work of Zerocoin and seeks to address the perceived shortcomings of Zerocoin. With Zerocash and its use of zkSNARKs, proof sizes are now only 1 kb and are very fast to verify. Furthermore, all transaction amounts are hidden and there is no longer a need to use fixed denominations when doing a minting transaction. Zerocash also allows people to transfer Zerocash’s equivalent of ‘Zerocoins’ to each other without the need to convert back into the base coin. Its anonymity set is also the largest among all previous anonymity schemes involving all minted coins regardless of denomination on the blockchain.
A cursory glance at this would make it seem that Zerocash makes Zerocoin obsolete. However to achieve this, it had to trade off certain benefits that Zerocoin has.
First of all Zerocash lacks supply auditability. Like Zerocoin, Zerocash requires a trusted setup but Zerocash’s setup is much more complicated. Zcash utilized a multi party ceremony involving 6 people setup in a way that the only way these parameters could be leaked is if all 6 in the ceremony colluded to retain the keys. In other words you have to trust any of these 6 people that they destroyed the initial parameters and also trust that the ceremony was carried out correctly.

If there is a bug in the code, or a cryptographic flaw or an issue with the multi party trusted setup, an attacker can possibly generate unlimited Zcash and unlike in Zerocoin, this additional supply cannot be detected. Especially in a system that operates on similar principles with Zerocoin that allows the creation of new coins, supply auditability becomes increasingly important.
Another trade off is the use of new cryptography called zkSNARKs which are effectively only used in Zerocash. There is a lot less scrutiny on it and therefore is not as battle tested as RSA which has been in use and reviewed for many years and continues to be widely used.
The other main drawback of Zerocash is that due to the complex math required, the generation of a private transaction takes significantly longer than any of the previous privacy schemes approaching a minute on a powerful computer and much longer for lesser systems. This makes it less likely for people to use its privacy features and also may exclude less powerful systems such as mobile devices.
So although Zerocash offers potentially the highest anonymity, it does this at the cost of supply auditability combined with a complicated trusted setup, the use of new cryptography and a long generation time to create private transactions.
Summary
Every anonymity scheme has its own sets of benefits and trade-offs and we believe that continuous exploration and research of these privacy schemes can only serve to improve blockchain privacy as a whole. We at Zcoin strongly believe that the Zerocoin protocol compares very favorably to other anonymity schemes by providing a very well rounded anonymity package, giving very strong anonymity using proven cryptography while remaining scalable and auditable. We continue to research into ways to further improve Zerocoin.
I hope this article gives you a much better understanding of how various privacy tech works on the blockchain!
Excellent article. PIVX is actually moving over to Zerocoin privacy protocol for most of the reasons highlighted. In fact we've already implemented it successfully on the testnet and will be pushing for full implementation within weeks, once we've finalised setup parameters and GUI. The fundamentals of anonymity are very much the same but our implementation will come with some advancements over most current implementation increasing efficiency & usability. All source code will be open so all projects can audit and use the improvements we've made. We do disagree that leaked setup credentials can lead to forged coins, but agree it can cause zpiv origins to be calculated thus rendering the anonymity useless. However it's not a problem worth worrying about for any of the coins mentioned as they're all well organised and setup. Great to see so much progress in the realm.
Hi @pivx! Thanks for chiming in. Saw the GUI you made for Zerocoin which is pretty neat.
Also good to hear that you would be making all of your developments open source. We have some pretty nice improvements and important fixes in libzerocoin which you might want to take a look at once we release so we can all benefit from the space.
I'm assuming you are still using RSA accumulators in your Zerocoin setup and still require the RSA modulus N ? Where would you be taking the parameters of the accumulator trapdoor p,q from?
If this is the case, then leakage of p,q will definitely lead to forgery of coins but it would NOT break anonymity unless you're not using RSA accumulators in your Zerocoin setup, in which case we would be very curious what you are using in its stead.
Relevant part of Zerocoin paper:
http://zerocoin.org/media/pdf/ZerocoinOakland.pdf
Pivx stands up to the closest of scrutiny - it's making all the right moves, moving slowly (not too much) and making steady progress. Great community and great project and the implementation of zerocoin is another example of this.
Come on @matrixdweller we can be adults here :D
Glad to see Zcoin now publishing their articles in Steem. Blockchain for the win.
This was a good read. Will look into investing in Zcoin myself. I mean not a lot but significant for me. I see Zcoin's commitment to opensourcing their code as very noble.
What I would suggest is to release your product and prove it usable. When the market understands its use case or say a given time frame ( 6 months ). Then release the code. Gotta give credit to where the credit is due.
Thanks for the detailed yet easily digested post on the popular privacy coins, definitely helped me in understanding their similarities and differences so much better.
I'm glad you liked it! Took a lot of research and time to get it right and remain fair. :D
Still trying to work on a TL:DR version.
Thank you again, your time on the post is very appreciated as the information is out there but for someone who is not techy, it's hard to make sense of it all.
Seems to me Zcoin is the best privacy coin there is right now and continuously improving to stay on top.
@originalworks
@OriginalWorks Mention Bot activated by @zcoinofficial. The @OriginalWorks bot has determined this post by @zcoinofficial to be original material and upvoted it!
To call @OriginalWorks, simply reply to any post with @originalworks or !originalworks in your message!
For more information, Click Here!
With zcoin, you can't stay anonymous. When you spend your anonymized coins, they have to go to a transparent address. With zclassic, you can stay anonymous forever and no one can trace your transactions. Correct?
Risks of blockchain being deanonymized in the future or through incorrect implementations
What?
Great article! Keep giving us more info we need.
You forgot about NAVCOIN: here is how dual-blockchain works! https://medium.com/nav-coin/a-guide-to-navtech-1-2-ca0e28bc403a
Navcoin setup seems to use trusted servers to do the anonymization. What are its benefits over centralized tumbler services?