Scanning A Target For Vulnerabilities(Hacking-103b)
Have you ever wondered how hackers find ways to break into a system? In this hands-on tutorial we're going to cover step by step methods of finding ways into systems. Even better we will do all this on a real-life target. You will learn many important skills such as:
finding open & vulnerable ports using Nmap
finding hidden directories/login pages using DirBuster
finding hidden files/directories and other important info using Nikto
combining it all together using Sparta
Let's get to it!
Prerequisites:
- Mr Robot/Kali VM's(go here to learn how to create them)
Getting Started:
First make sure both Kali & Mr robot machines are on and set up correctly. The mrRobot machine should show a startup page similar to what's below. Once you are sure they're both on we now need to find the IP address of the mrRobot machine on our network.

Finding IP Address of a Computer
The very first thing you need to do when examining a system is to know the IP address of it. Depending on if this is a computer on the internet or if it's a computer on a network you're connected too(like our MrRobot VM is) will determine how you do that. In my previous guide I explained how to find the IP address of a computer on the internet but what if it is on a network your connected too? It's very simple.
Finding The Network Range To Scan
First you need to Simply go to the terminal and type:
- ifconfig
You should see something like below. This is the IP address range you need to scan.
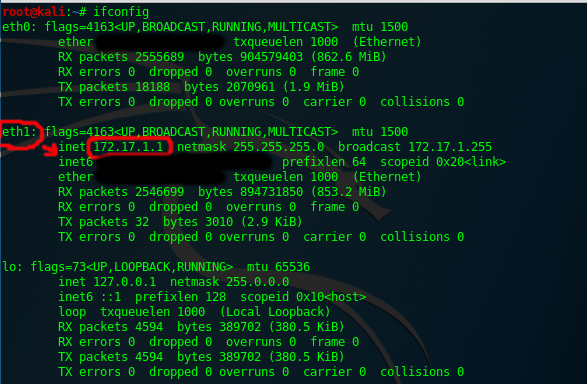
Scanning The Network Range For IP's:
Now it's time to actually find the IP address of the MrRobot machine. We do this by using a tool called netdiscover. In the above example we saw that our network IP address was 172.17.1.1. This number may be different depending on your settings. When using net discover we simply change the last series of numbers of it to 0/24(shown below). We simply go to a terminal and type:
- netdiscover -r 172.17.1.0/24
Once we have done this wait a few moments(even if it already says it's finished you should wait at leasty a minute. You should see something like below.
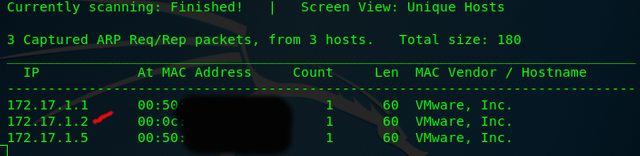
These are the machines on our local network. The one with red is the IP address(which you could find out by looking at the MAC address if you know it or by typing in your web browser the IP addresses and seeing which one opens a web page)
Now that we know the right IP let's test it out by going to our web browser and typing in the number we found. Once you do hit enter and you should see something like this...
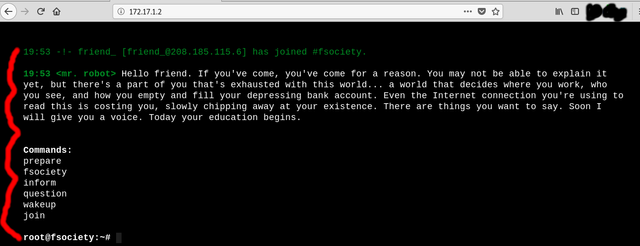
Congratz! You've found the machine. The reason we see a web page is b/c the MrRobot machine has an HTTP server on port 80(as you'll shortly discover). This will not always be the case but in most machines we will practice on it will be. Now that we know the proper IP it's time to get to the serious business of scanning it.
Scanning The Machine
There are several things we need to scan for with this machine.
Using Nmap To Find/Enumerate Open Ports/Services
The first thing we need to do is see what ports and services are open on the machine. Remember each of these are a potential opening to getting into the machine. Running Nmap is very simple. Simply go to the terminal and type
- nmap -A 172.17.1.2
You should get an output like below. Pay attention to the items circled in red.
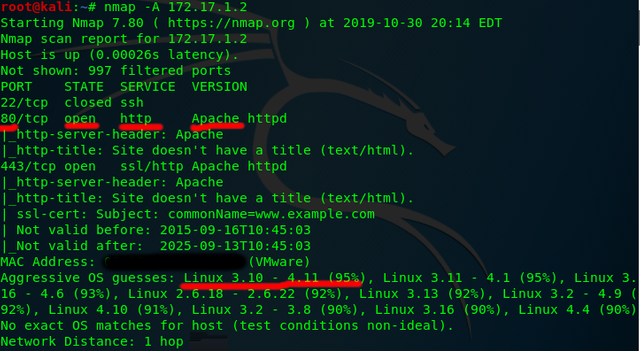
As you can see there is only http port 80 open. An HTTP port(frequently port 80) means that there is a web server which often contains a website on the machine. It looks like this is one of our only ways in which means we need to focus on web hacking for this machine.
You should save all this information into a file which you can do by selecting the text, copying it, create a new text file(nano textfilename) and pasting it by hitting Ctl-Shift-V, then hitting Ctl-X, hit Y, and press enter. You should save to this file all information gained during scanning.
Using Nikto To Check For Common Web Vulnerabilities:
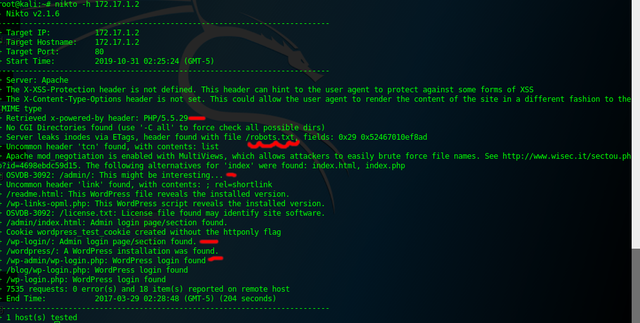
Now that we've checked for open ports along with there versions we need to check for more information. We do this using a program called nikto. Simply go to the terminal and type(making sure to change IP to the one you have):
- nikto -h 172.17.1.2
And you should see something like below. Pay attention to the things in red they will turn out to be very important. Some of the things that are important are:
- The PHP version(which could have vulnerabilities)
- That the website has a robots.txt file(which can often reveal hidden files/directories)
- that there is an admin page
- That the site is running wordpress and has a login page(so we can potentially brute-force it to gain access)
Using Dirbuster To Find Hidden Files/Directories:
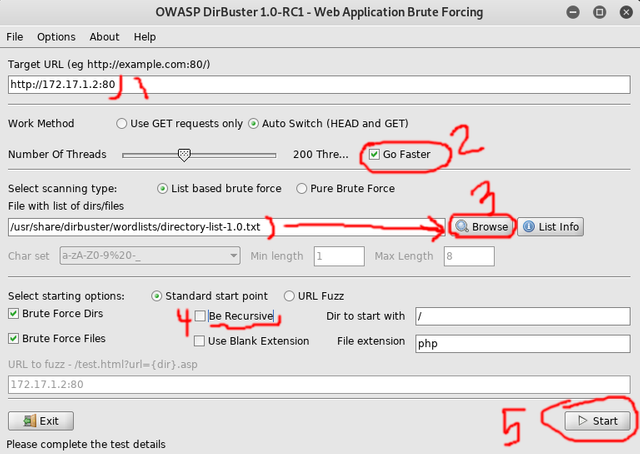
Now we want to find any hidden directories or files. Doing so can reveal login pages or insecure pages we can later exploit. We do this by using dirbuster. Simply type in the terminal:
- dirbuster
And make it look like below(making sure to change IP address to the appropriate one and UNchecking "Be Recursive")
Once the scan has completed you can click on the column labeled "Response" and make it ordered by a 200 response. A 200 response means that the page is valid and accessible(though there can be false positives). In the example below we have found several pages marked by a red dash that could be important.
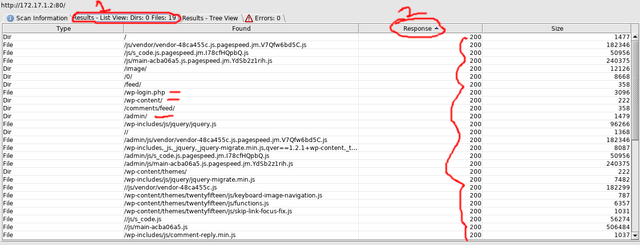
Using Sparta To Automate & Analyze The Scanning Process
Sparta combines several "bread and butter" tools into one centralized, easy to use and analyze program. Some of the tools that Sparta runs that we already covered are:
Nmap
Dirbuster
NiKto
while others like Hydra (for brute-forcing or checking for default passwords to common services like mysql, ftp, etc...) we will cover in the next tutorial.
Using Sparta is very easy. Simply go to the terminal and type:
- sparta
A program will load and in the left side area you want to click and input the IP address of the MrRobot machine(in my case 172.17.1.2)
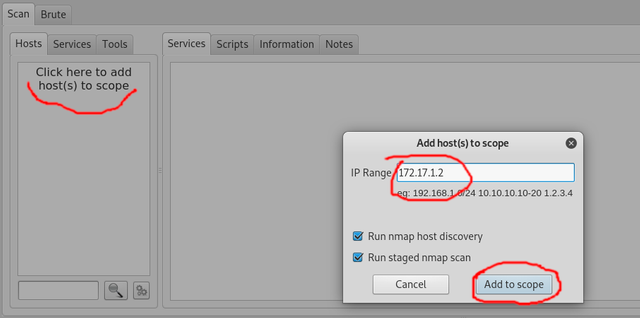
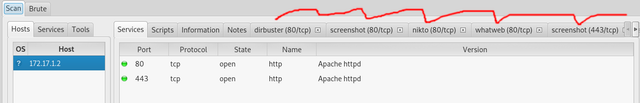
Once you've entered the IP it will begin running several scans against it. As a side note if you only know the domain of a website(like google.com) you can simply type that and it will scan it as well. Anyways once you've done all this it should look like below. Notice you can click on each tab to see more information and the little arrows to move to tabs not currently shown.
Conclusion
So we've covered a whole lot but don't worry you now have some very powerful tools and know the methods hackers use to analyze a website. In the next tutorial we will work on actively exploiting with the information we've found. You'll learn everything from brute-forcing login names, installing persistent malware on the system, password cracking, and more so stay tuned! As always I hope you found this useful. Don't forget to up-vote & if you have any questions or comments leave them below and I'll get back to you ASAP. Until next time happy and safe hacking!
Congratulations @hack-tha-world! You have completed the following achievement on the Steem blockchain and have been rewarded with new badge(s) :
You can view your badges on your Steem Board and compare to others on the Steem Ranking
If you no longer want to receive notifications, reply to this comment with the word
STOPTo support your work, I also upvoted your post!