Password Cracking Using Rainbow Tables & Hashcat (Hacking-104)
There are many reasons you may need to crack a password. Perhaps you are examining breach data or have stolen credentials and only have hashed passwords, or maybe you forgot the encryption keys to one of your hard drives and need to crack it. These are just a few examples of instances when you need to know how to do so. In this tutorial you're going to learn several methods to crack passwords. We will cover all of the following:
- Filtering large password lists
- Cracking hashed passwords with Rainbow Tables
- Cracking hashed passwords with hashcat
Prerequisites:
- A Kali Linux VM go here to learn how to create one
- A password list you can download here
A Brief Overview of Password Cracking:
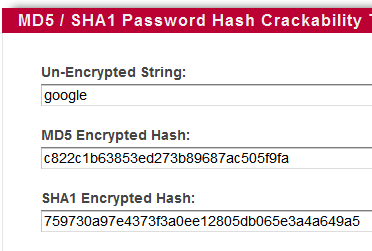
Before we can get to cracking there is some vocabulary you need to know. A hash is a uniquely generated number that represents the bit-by-bit data of a file/text. In other words a hash is a mathematically generated number that can only be obtained with an exact copy of a file. Below is an example of a MD5 hash(the word doggie)
If even a single bit out of trillions is changed, the hash will be different. They are also virtually impossible to reverse engineer. This is why they are used in both security(to store passwords securely) and forensics(to prove evidence hasn't been tampered with).
Many websites store passwords hashed. When you type in a password to a website it usually(at least in a secure site) hashes it then compares it to the hash in the databases. This is so if the database is ever breached the only thing a hacker will have is the hash and not the actual password.
There are rare(and potentially dangerous) exceptions to this known as "collisions"(where two different inputs result in the same hash). These are dangerous for passwords b/c it means a completely different password can be used rather than the one intended.
There are two main ways to find the value a hash represents. The first is to use something called a Rainbow Table. The other method is to use a program like hashcat. Both will be covered shortly but before we can do these we need to actually create a hash that we can practice with.
Creating a Hash To Crack
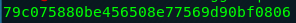
Creating a hash is very simple to do. You can create a hash of a file or of a string of text. In the below example we will create two hashes using the words doggie & Password123. To do so simply go to the terminal and type:
- echo -n doggie | md5sum
- echo -n Password123 | md5sum
You should see the same thing as pictured below...
Next we will create a file containing our hashes so we can put them into a cracking program. To do this go to the terminal and type:
- nano test-hashes.txt
and copy/paste the hashes we made earlier(each on their own line and leaving out extra spaces and dash!), then hitting Ctl-X, Y, Enter
Now that we have our hashes let's try to crack them!
Methods of Password Cracking
Using Rainbow Tables To Crack Hashes:
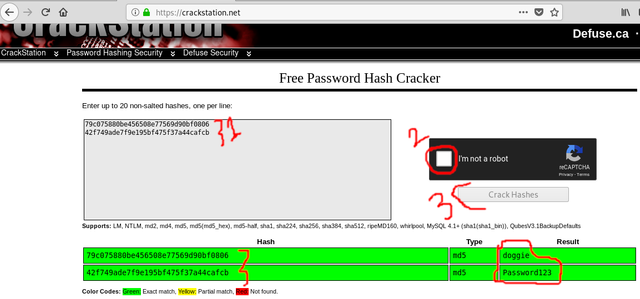
When you have a hash it is always best to first try to use a rainbow table to crack it. This is because it can take an astronomical amount of time to brute force crack the hash. A Rainbow Table is a list of hashes tied to known passwords. You can create your own rainbow tables or use a website(which is usually best).
To save time we will use a well-known website called Crackstation.net. This website has billions of hashes which could save us centuries of time!. So let's enter our hashes into the box and see what we get. As you can see it successfully found passwords for both the hashes! Now that we have this our work is done!
Cracking Passwords With Hashcat
Rainbow tables are great but there are plenty of times where you will be unable to find the password for a hash. When this occurs you will need to brute force a password using either pure brute force(trying every possible character in every possible combination) or using a password list. Brute force is rarely feasible for passwords 10 or more characters. So let's see if we can crack the hashes we created above using a list.
Cracking With a Password List
First we need to download our list. Once we do that we need to trim it to remove any duplicate words.
Trimming The Password List:
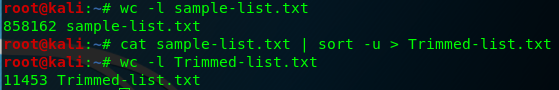
First let's trim the password file as sometimes lists will contain duplicates that can greatly increase the time required to crack something. We can do this by going to the terminal and typing:
- cat sample-list.txt | sort -u > Trimmed-list.txt
The screenshot below shows the list before it was trimmed and after. The numbers to the left show the word count.
Using Hashcat With a Password List:
Hashcat is a very powerful program that can crack hundreds of different hash types. To use hashcat with our list we simply need to type in the terminal:
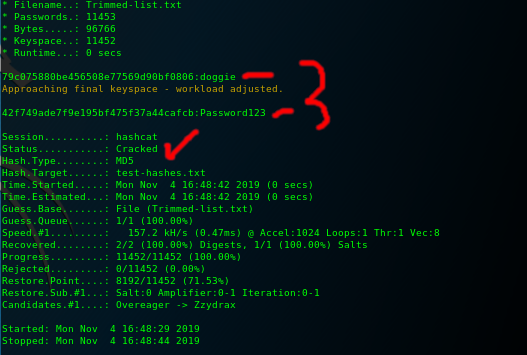
- hashcat -a 0 -m 0 test-hashes.txt Trimmed-list.txt
As you can see in less then a minute it found the passwords to both our hashes.
Conclusion:
Congratulations you learned a lot today and hopefully you found it easy to follow. Though this guide is long there are really only a few commands you need to learn. Password cracking is a field into itself and entire books have been written about it but for now you know the basics.
If you have any questions or comments post below and I'll get back to you as soon as possible. Until next time happy hacking and please up-vote, follow, and share if you found this useful.