Double authentication: why steemit really have to do it
The password is an archaic technique that should be deleted because of its vulnerability. While waiting to have an innovative technology available, the best solution is to activate a second authentication factor.
If you spend half of your life on the Internet, some may have already told you, but you must ABSOLUTELY switch to double authentication, this technique which validate a password for example by sending a password, a code by SMS or a security key. Why? Because nowadays, a password is no longer enough to secure access to an online service.
Hackers have dozens of techniques at their disposal to penetrate your personal accounts. They can send you fake emails to make you enter your credentials in fake forms. They can also try to intercept them when you are connected through a poorly secured public Wi-Fi hotspot. Or, they may be sending you a Trojan horse hidden in an Android application.

DATA LEAKS
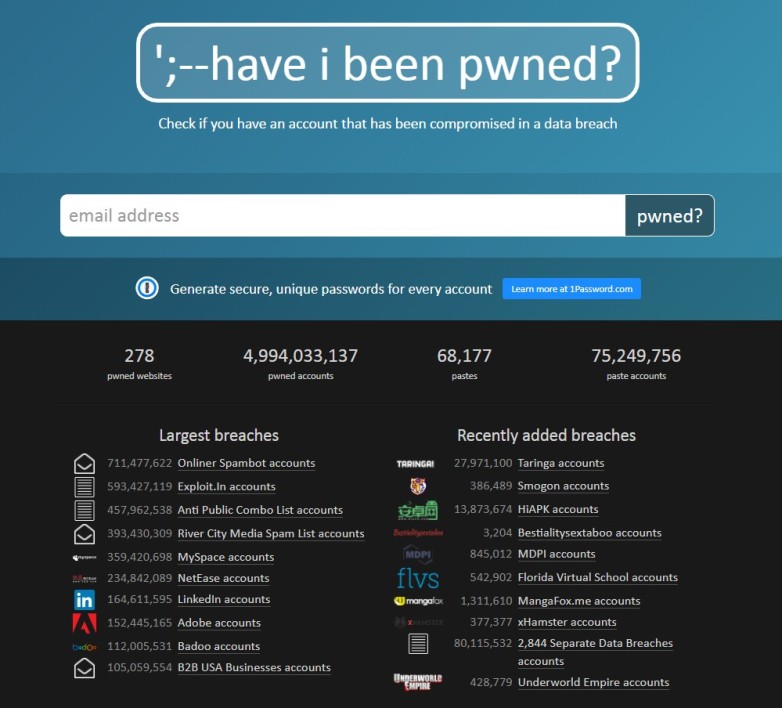
Hackers can also steal your password directly from the poorly protected servers of your service provider. Yahoo users know it well. Last year, the portal revealed that it was stolen all 3 billion accounts he managed in 2013. And just visit the site haveibeenpwned.com to find that the theft of identifiers has become a widespread practice. The site references almost 5 billion stolen identifiers on 277 sites, Yahoo's is not included.
It makes you dizzy.
This intrinsic weakness of the password is well known. Industrialists may one day succeed in replacing this archaic authentication method. FIDO2 technology, recently awarded W3C recognition, is a credible candidate. But its adoption may take longer. In the meantime, the only solution is double authentication. Indeed, even if your password falls into their hands it is not enough to connect.
Some people will probably tell you that dual authentication is complicated and not very practical. This is true because using a second factor necessarily slows down the connection process. But what one loses in comfort, one gains it larger in safety.
MESSAGING, THE CLOUD AND SOCIAL NETWORK
The first accounts to protect are email accounts that are typically used as a last resort to reset passwords on your other services. A hacker who compromises an email account can access toyou’re your other resources. Priority accounts that must also be protected include social networking accounts and cloud accounts, to prevent identity theft and data leakage respectively. Finally, it would also be good to enable dual authentication for online banking, where possible.
But then how? It depends on the supplier, because it is up to him to make his service protected with the different solutions are on the market. A good tip: if your email provider does not offer this type of option, go elsewhere. The major brands of the web, for their part, all offer one or more methods of double authentication. One of the simplest to implement is the one-time code. At each connection, the user enters his password and then receives, by another means, a code that will work only once.
For Google services, use the Google Authenticator mobile app. For Microsoft services, did you guess? - Microsoft Authenticator. These apps must first be associated with the account, for example by scanning a QR code. Then, they generate at regular intervals codes to use. This system is called "TOTP" for "time-based one-time password".
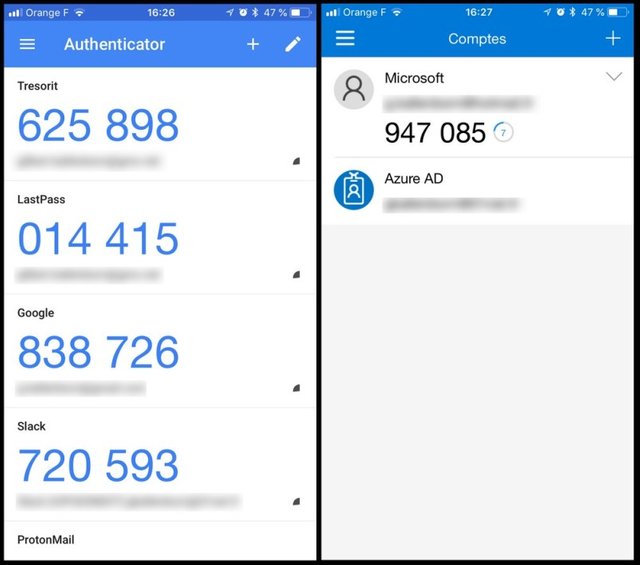
The advantage is that these applications can also be used for other online services. Thus, it’s quite possible to use Google Authenticator to protect its access on LastPass, Coinbase, Binance, Slack, Amazon Web Services, Facebook and ProtonMail, for example. Other apps do it too, such as Authy or Duo Mobile.
At Apple, however, no need for an application, the mobile device is enough (iPhone, iPad). Each time an iCloud or Apple ID connection is attempted, the user receives a single-use code directly from the iOS system.
For its part, Twitter relies on its mobile application to send the user a code of this type. And at Facebook, several options of double authentication are available. In addition to the application of single-use codes, the social network proposes to receive a code by SMS or to connect a security key.
This last case is a bit the ultimate method of double authentication. The best-known actor in this field is Yubico who has an entire range of security keys. They offer several methods such as TOTP individual use codes or the U2F standard. But there are also other providers like Neowave or Key-ID. You choose.
So plz steemit, hear my call

Great article, more people should be aware of this!! Everyone needs this or the everykey I believe it is called.
Thx man! Yes that would be so great!
It will be fantastic if Steemit had double authentication, we all know that's here you are full responsible for your security! :D Good post :D
Yes exactly! Thx man! ;-)
This post has received a 1.01 % upvote from @booster thanks to: @vijbzabyss.
Hmm I don't think everything requires two factor auth or MFA. I also wouldn't want to trust one specific autheticator provider to be the sole provider to be used for example Yubikey. Btw it is really easy to steal a Yubikey from a co worker or anyone who has one. Not that I've done this, but we had a co worker who tried to prove a point by hiding Yubikeys of people that left them lying around the desk.
Yes I agree but the password isn't enough nowadays, don't you think?
Something for you to read: https://hal.archives-ouvertes.fr/hal-01759199/document
The guy who wrote it is on steemit btw!
Thx man! Gonna read it with pleasure :)