WikiLeaks Vault 7 - Part IX: AfterMidnight

Originally redacted in Year Zero the contents of AfterMidnight, namely Assassin, are as sinister as they sound. Both tools were designed to target Windows systems using persistent implants that provide backdoors, data exfiltration and further exploitation methods. The tools we are provided documentation for in this release are AfterMidnight, its components Octopus and AlphaGremlin, as well as Assassin.
Some may recognize these Windows exploits as being similar to Part IV's Grasshopper Framework. As it turns out, Assassin can indeed interface with Grasshopper and other similar persistence modules to diversify its methods of attacks. If one recalls, Grasshopper Framework persistence modules could exploit such things as Windows Services, registry keys, drivers and more! (1)
This post will summarize the contents of AfterMidnight, each tool and component, footprints for finding such tools and finally the dark, dire implications of this release.
The complete set of documentation of AfterMidnight is available on WikiLeaks.
Here are my summaries of the Vault 7 releases thus far:
- Part I: The CIA and NyanCat: The hackers and tools of Vault 7's "Year Zero"
- Part II: "Dark Matter" - All your Macintosh are belong to CIA
- Part III: Marble Framework - The CIA's cloaking device for hackers
- Part IV: Grasshopper and more research challenges!
- Part V: HIVE, Longhorn and the CIA's reign of cyberterror
- Part VI: Weeping Angel is listening...
- Part VII: Watch out for Scribbles!
- Part VIII: Archimedes/Fulcrum
AfterMidnight, Octopus and AlphaGremlin
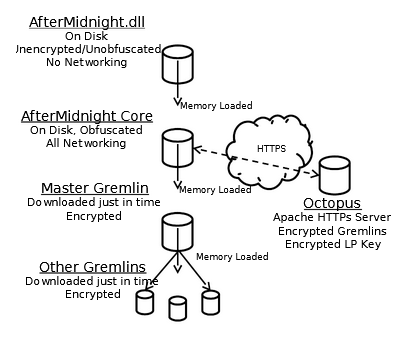
AfterMidnight as it turns out would be a reference to the infamous 1984 film, Gremlins (nice date, eh?). AfterMidnight, similarly to Grasshopper, allows an operator to install a persistent backdoor on to the target Windows machine. Unlike Grasshopper which only sends back XML data back to the operator, however, AfterMidnight can utilize sophisticated "Gremlins" with a broad range of capabilities.
Gremlins are essentially individual Windows exploits -- some undermine functionality, some exfiltrate the target's personal data, etc. -- that are then fed to a secured "listening post" called "Octopus". AfterMidnight can be configured with options for how and when it will contact the listening post and receive new commands and/or Gremlins.
Several Gremlins are built into AfterMidnight, but one of the more notable of these would be the "annoying" Process Gremlin:
The Process Gremlin has the capability to subvert the execution of existing or started processes in a few annoying ways by either temporarily delaying the execution of a process, killing an existing process, or “locking up” a process permanently, requiring the user to manually kill the process.
These activities can be set to occur after a set period of time (plus or minus a jitter) and can be set to only affect a certain percentage of target processes.
Source: AfterMidnight v1.0 User Guide
AlphaGremlin was developed alongside AfterMidnight and is functionally similar to an AfterMidnight Gremlin but with many notable additions. For instance AlphaGremlin can be configured with its own schedule and plan separate from AfterMidnight. In addition AlphaGremlin includes a custom script language which allows the operator to schedule such things as console commands to run routinely on a target and report to Octopus.(2)
Assassin
Assassin is functionally similar to both AfterMidnight and Grasshopper in that it is an automated implant for exploiting Microsoft Windows systems, but it has some sinister twists. Assassin's command and listening post subsystems, collectively labeled "The Gibson", allow operators to perform specific tasks on an infected target. Not only can Assassin interface with Grasshopper's stealth-persistence modules, but one of the payloads for Assassin, a "Pernicious Ice DLL", was also developed to interface with NSA's "Pernicious ICE" capabilities.(3)
Apparently one such ability of Pernicious ICE is the ability to avoid forensic detection. More specifically, Pernicious ICE is able to hide a specific file from even Deep Freeze(4) -- a commercial tool used to restore disks and workstations which currently (albeit falsely) claims to make such configuration files "indestructible".(5)
Assassin was developed up to at least v1.4 and includes some highly sophisticated and nefariously stealthy exploits. For instance Assassin can be configured to not just beacon back to its listening post at a scheduled time, but also programmed to run or not run based on other processes currently running on the target.(6)
Assassin payloads come in two flavors -- injection launchers and service installers. Injection launchers carry an Implant DLL embedded as a resource, which it is responsible for deploying by injecting into an existing SYSTEM process, typically netsvcs svchost. By contrast the service installer does this injecting itself into the Windows service registry.(7)
What's profoundly disturbing about all this is that Assassin, perhaps one of the most technologically advanced tools released in Vault 7 so far, was specifically designed "to support third-party tools".(8) Worse yet, it seems it was designed, quite literally, "for fun and profit":

Source: Assassin v1.3 Training
Footprints (or lack thereof)
As for AfterMidnight, there are a number of methods for detecting and/or uninstalling the program. For starters, there are four conditions which will cause AfterMidnight to uninstall:
- The configured Uninstall date is reached
- The configured “dead man” timer expires
- The configured kill file is seen to exist on disk (I believe the CIA owe us all a "kill file")
- The Midnight Core file is not present at startup
In addition, there are processes run by AfterMidnight which can be detected. For instance, before the target reboots AfterMidnight will run using the process which loaded it. In addition after the first reboot AfterMidnight runs as a DLL inside of the netsvcs svchost.exe process running as SYSTEM.(9)
Here's where it gets a little crazy, however. After the first reboot has happened:
The service is only loaded long enough to load Midnight Core before it stops. In this way there is nothing, no running service entry or loaded DLL, to show that AM is actually running.
Source: AfterMidnight v1.0 User Guide
Assassin produces different "footprints" in the target's system depending on which payload is used. Similarly to Grasshopper it may leave behind executables, folders and registry keys, but as noted earlier the payload executables in Assassin come with sophisticated methods for specifically avoiding forensic detection. Nonetheless, Assassin's service installer payloads produce registry keys under "HKLM\SYSTEM\CurrentControlSet\Services", but the name is chosen by the operator.(10)
As difficult as it is to express these tools are among the most stealth-enabled, highly advanced and least traceable to date.
Implications
When Vault 7's Year Zero was released, I could never have imagined where it was going to take us. Unfortunately it's becoming frighteningly apparent that perhaps the CIA has not only been developing incredibly dangerous cyberweapons but perhaps they have been selling them as well. Together with the NSA, the CIA created a new cyberworld order that has been imposed on everyone, taxpayer included, without any oversight or conscience whatsoever.
Between this and today's cyberattacks on British hospitals using NSA software I have a strong feeling there are some intelligence and defense agencies in severe need of restructuring and/or abolishment.

The spooks at the IOC listening post