Virtual private network
A Virtual Private Network (VPN) is a service that creates a secure and encrypted connection over a less secure network, such as the internet. This ensures that the data transmitted between your device and the VPN server is private and protected from prying eyes. Here’s a detailed breakdown of how VPNs work and their various applications:
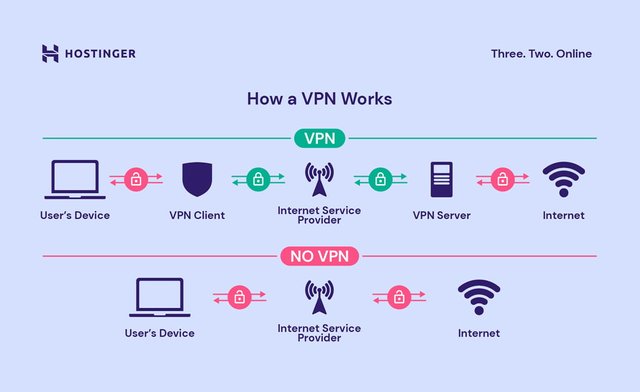
How VPNs Work
Encryption: When you connect to a VPN, it encrypts your data. Encryption scrambles your data so that only the intended recipient (in this case, the VPN server) can understand it. This prevents anyone from intercepting and reading your data as it travels over the internet.
Tunneling: VPNs use a process called tunneling to encapsulate and secure your data packets. This creates a "tunnel" between your device and the VPN server, ensuring that your data remains private as it travels across the internet.
IP Address Masking: When you connect to a VPN server, your real IP address is hidden and replaced with the IP address of the VPN server. This makes it appear as if you are accessing the internet from a different location, providing anonymity and helping to bypass geographical restrictions on content.
Applications of VPNs
Security on Public Wi-Fi: Public Wi-Fi networks, such as those in cafes, airports, and hotels, are often unsecured, making it easy for hackers to intercept your data. A VPN encrypts your connection, protecting your data from being accessed by malicious actors.
Privacy Protection: VPNs prevent your Internet Service Provider (ISP) and other third parties from tracking your online activities. This is particularly important in regions with strict internet surveillance and data retention laws.
Access to Geo-Restricted Content: Many streaming services, websites, and online platforms restrict access based on the user's geographical location. By connecting to a VPN server in a different country, you can bypass these restrictions and access content as if you were in that location.
Secure Remote Access: Businesses use VPNs to provide employees with secure remote access to the company's internal network. This ensures that sensitive data and resources are protected, even when accessed from outside the office.
Bypassing Censorship: In countries with heavy internet censorship, VPNs allow users to access the open internet and bypass government-imposed restrictions and firewalls.
Types of VPNs
Remote Access VPN: This type is commonly used by individual users to connect to a private network remotely. It provides secure access to the internet and the ability to access resources on a private network.
Site-to-Site VPN: Often used by businesses, this type of VPN connects entire networks to each other. For example, it can connect the network of a company's main office to the networks of its branch offices, allowing for secure communication between locations.
Personal VPN: These are consumer-grade VPNs used for personal purposes, such as browsing the internet securely, accessing geo-blocked content, and protecting online privacy.
Considerations When Choosing a VPN
Security Features: Look for strong encryption protocols, a no-logs policy, and additional security features like a kill switch and DNS leak protection.
Speed and Performance: A good VPN should offer fast and reliable connections. Consider the number of servers and their locations, as well as the VPN's impact on your internet speed.
Ease of Use: Choose a VPN with user-friendly software and apps for all your devices. The setup process should be straightforward, even for non-technical users.
Cost: While there are free VPNs available, they often come with limitations and potential security risks. Paid VPNs typically offer better performance, security, and customer support.
Reputation and Reviews: Research the VPN provider's reputation and read user reviews to ensure they are trustworthy and reliable.
In summary, VPNs are a versatile tool for enhancing online security, privacy, and accessibility. They are essential for protecting data on public networks, maintaining privacy from ISPs and other trackers, accessing restricted content, and securing remote access to private networks.
Congratulations, your post has been upvoted by @upex with a 0.21% upvote. We invite you to continue producing quality content and join our Discord community here. Keep up the good work! #upex