Hack Alert : Users exposing private keys in memo while transfer !
The Problem
The issue of users unknowingly exposing their private keys in memo while transferring their funds is a problem that has been time and again exposed by developers. The issue was raised by @noisy in a very famous article (6 months ago):
Then again the same problem was pointed out by popular steemit user Jerry Banfield, 2 months ago, in his article titled : I Found $63,278 of Private Keys on Steemit.com in 10 Minutes!
The private keys of user get exposed unknowingly as the users transfer their steem/SBD using the transfer option on steemit.
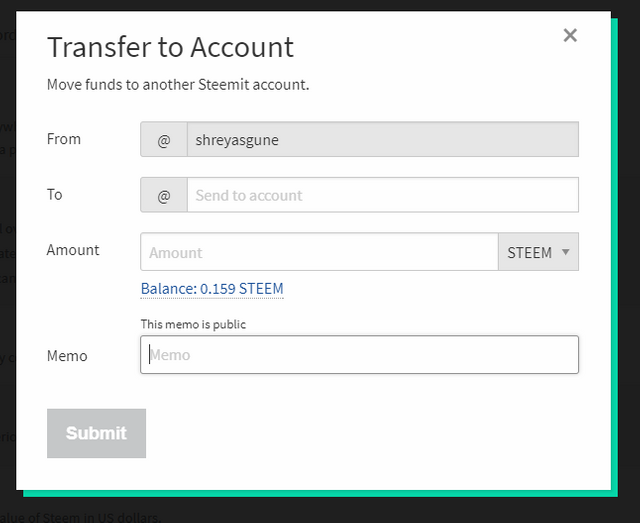
In the memo field, users tend to enter their private memo keys. Some users have exposed even their master passwords in the memo field.
How I accessed the exposed private keys:
It was really easy to query the steem database for exposed private keys using SteemData.
@Furion has provided an awesome tutorial on using SteemData titled: Getting started with SteemData.
I used RoboMongo as a cross-platform GUI utility for playing around with SteemData.
Accessing master passwords
I used the following simple query to get master passwords exposed on steem blockchain:
db.getCollection('AccountOperations').find({'memo': /^P5/})
This query yields 28 results. These are 28 independent transactions after the last hard fork where the private keys got exposed. I checked the length of these keys using https://www.lettercount.com/. (Yes, the password length is 52 ). I checked this by repeatedly generating new passwords using generate new password option in steemit.
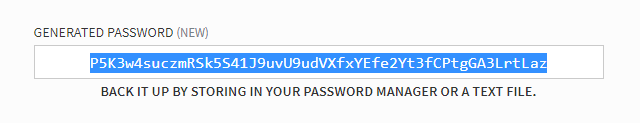
The passwords have now been changed. That's a good thing. I will partially reveal only few of the account name and passwords anyway so that you know I am not bluffing. Anyways you can acess the other names by the query mentioned previously.
| Account Name | Private Key | Transaction id | Timestamp |
|---|---|---|---|
| @scigar | P5HrWfmKXXXXX | 5293f4c83846a2c4b50c1bf2c52381f260b9a06c | 2017-06-03 23:17:57.000Z |
| @steemboad | P5JJYBFXXXXX | 70069c982e98e7917fe13093f63266d2f995c912 | 2017-11-12 09:15:54.000Z |
| @fittrex | P5Kk17eRvytzXXXXX | b18ac26c09f88c1e4211e30a6094a41f2b965440 | 2017-10-13 00:32:00.000Z |
| @herman2141 | P5JJYBFNwYrn1m9ZFHHGXXXX | 70069c982e98e7917fe13093f63266d2f995c912 | 2017-11-12 09:15:54.000Z |
| @prosperous | P5KDF2BRMQcCVcRDHuzT6iy2oNshZw1JqyMfSuV4QXXXXX | f3d62cba41df96db0f55be9a0f0752cb5a4d6eab | 2017-06-15 00:48:21.000Z |
Accessing private memo/posting keys.
Hundreds, if not thousands of private memo keys have been exposed publicly in the blockchain transaction memos. Since these are publicly available, I will mention some them. They can be used to login to the accounts although any other action like posting/voting requires private posting keys.
I used the query mentioned below:
db.getCollection('AccountOperations').find({'memo': /^5/})
Then I checked which keys contained 51 characters. This gave me private memo keys or private posting keys of a large number of accounts. Some of them I will disclose below. I sincerely request these account owners to reset their passwords.
| Account Name | Private Key | Transaction id | Timestamp |
|---|---|---|---|
| @bestjt | 5K1deWWcqGecvzsfNWDSPGZHTwXXXXXXX | ed26183ec4284c568e30c6fc2ce190db1dc14438 | 2017-11-16 17:23:48.000Z |
| @beoped | 5KU12e2JPyh31iz5bYLKXVCAi4y79366gPku2keEwJ1XXXX | 3d562b3acebab7936da253e3671f71b0b4d83cf6 | 2017-11-16 14:00:36.000Z |
| @ccoindigger | 5K1UyjjZiVpUH2mAFdnChfZH2fEFte2qk8EVfCVDXXXXXX | 3cb3e6fe46733f9dd2be60453594be429deaf2bd | 2017-11-09 21:35:24.000Z |
| @caspell | 5Ka2iTeUpzWYSYdF8wcw2pkf2tsMGr7QeTLsi7qC4GxmXXXXXX | de2df1c7fde1dc8bb5ac2093f9a865293e81605a | 2017-11-15 03:06:57.000Z |
| @cryptocryptov | 5Jqu16YDY83QKWWnwDinwmKhxK51DuCjdduXXXXX | ac39c483bd8cb7f21672a48f3fd9b5dde64c0861 | 2017-11-16 05:16:06.000Z |
Hundreds of other private memo keys have also been exposed. It is a sincere request to all users to not enter their private keys as memos. Please spread awareness about this issue so that the problem can be resolved. As of now, the memo keys don't really do much. But in future, they may perform important functions as steem blockchain evolves.
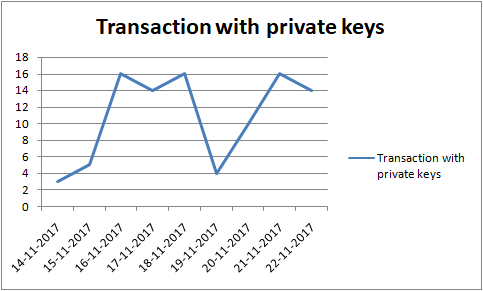
Last 10 days Data Analysis:
Analysing last 10 days data for date-wise number of transactions exposing private keys we find the following pattern:
Thank You and take care.
Posted on Utopian.io - Rewarding Open Source Contributors
Although I agree with your safety concerns, I do not think blogging about this openly is the right way to go, especially so in the Steem ecosphere where real money is involved.
Maybe deleting the mongoDB queries on your post could help protect the wallets involved from getting robbed by scriptkiddies.
Edit: self-upvoted for visibility / preventing people getting robbed.
While I agree that sensitive topics should be handled carefully, I think that it is hard to find a better way to expose such an issue on Steemit. Maybe contacting Steemit Inc. directly instead of blogging it...?
Two aspects are important here:
-1- implementing your memo rejection suggestion (via [email protected])
-2- protecting the accounts / wallets involved, via notifying them (via email if possible) and urgently suggesting to change their keys ASAP.
The accounts I have exposed have changed their master keys. I have confirmed that. As for the queries, similar queries are available in countless blogs on steemit itself. This is now new.
I get your point. Hope you get mine !!
I have not exposed the real queries, with these anybody will have a little hard time.
The actual queries I used let me check character length there itself.
Talking about it more could actually save users from getting robbed. Steemit Inc is well aware of the problem. They have included warning signs. But they can't do anything about memo people leave on bittrex while transferring them to steem account. This shows in their memo field non encrypted and ready to be read by anyone.
The text input should detect private keys and reject them with an alert for the user.
A similar thing happened to me recently. I just confused the input fields. Luckily I just sent my public key per memo.
In my opinion this is an UX issue. It is too easy for the user to confuse keys. Generally, Steemit needs to educate people more about keys. Knowing how to manage multiple levels of private and public keys is not laymen's knowledge.
Bravo, that is the only thing which could help and should be implemented.
Even I did a similar mistake. Thankfully changed the password immediately.
Thank you for the contribution. It has been approved.
You can contact us on Discord.
[utopian-moderator]
Congratulations! This post has been upvoted from the communal account, @minnowsupport, by thorough_research from the Minnow Support Project. It's a witness project run by aggroed, ausbitbank, teamsteem, theprophet0, someguy123, neoxian, followbtcnews/crimsonclad, and netuoso. The goal is to help Steemit grow by supporting Minnows and creating a social network. Please find us in the Peace, Abundance, and Liberty Network (PALnet) Discord Channel. It's a completely public and open space to all members of the Steemit community who voluntarily choose to be there.
Hey @shreyasgune I am @utopian-io. I have just upvoted you at 9% Power!
Achievements
Community-Driven Witness!
I am the first and only Steem Community-Driven Witness. Participate on Discord. Lets GROW TOGETHER!
Up-vote this comment to grow my power and help Open Source contributions like this one. Want to chat? Join me on Discord https://discord.gg/Pc8HG9x