Learn Cryptography #2 - Hashing using Python

Hi Guys!!....
This is the programming part of the previous tutorial "Hashing vs Encryption" in this "Learn Cryptography" series.
View Part 1 in Steemit, Github
In previous tutorial, some basics is covered regarding Hashing & Encryption and the main differences between them.
In this tutorial, we will be programming using Python for hashing any text with hash algorithm.
Tools Installation
We will be using Anaconda for accessing the features.
Create a separate environment. It's not necessary but recommended so as to avoid conflicts in case of multiple type of projects running in a PC/ laptop.
conda create --name learn-cryptography python=3Now, when the notebook opens, choose the correct shell (where all tools are installed)
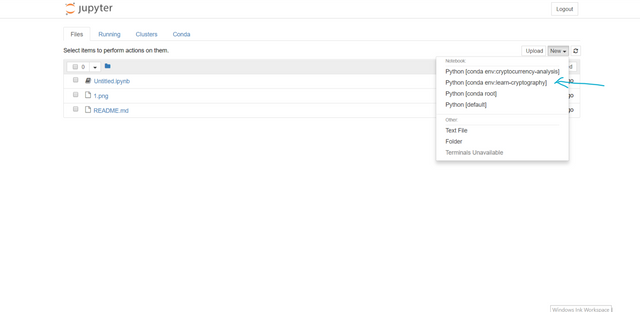
After choosing the "learn-cryptography" notebook it opens like this..
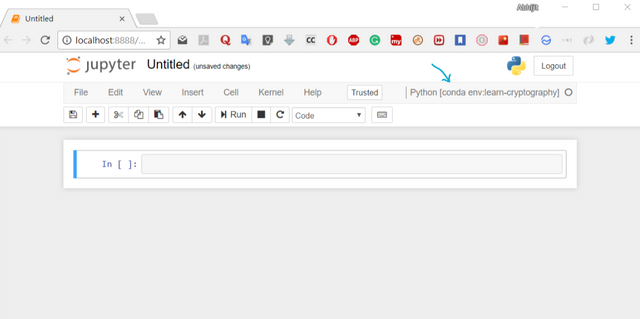
Now, enter into the environment so as to install the required libraries.
activate learn-cryptography
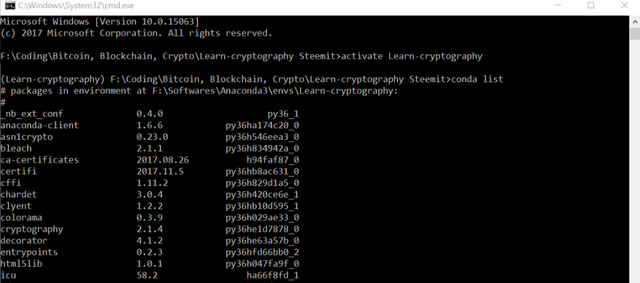
Install the nb_conda (specifically for an environment) using
conda install nb_condaOpen the jupyter notebook in your directory (where project files are to be saved)
Usejupyter notebook
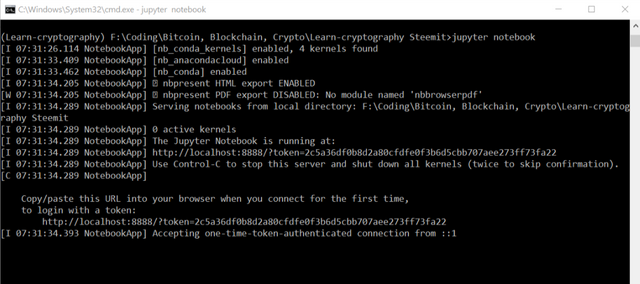
- Now, install the libraries for practising cryptography -
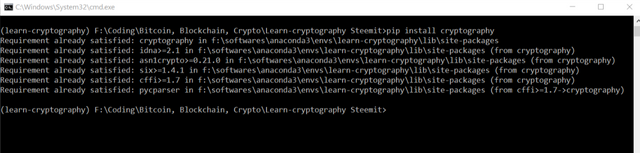
'cryptography' -
pip install cryptography
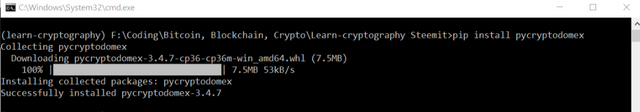
pycryptodome -
pip install pycryptodomex. Just to avoid any conflict while importing Crypto library. Also , install this usingpip install pycryptodome.
Now, there is no conflict at all importing libraries.
Let's start coding now....
Coding
We are going to cover Hashing in this tutorial. And Encryption-Decryption shall be covered in the subsequent tutorial. In encryption-decryption, there are 2 main types - symmetric and assymetric.
Hashing
Let's start with hashing a string - "abc" using SHA256 method.
from Crypto.Hash import SHA256
SHA256.new(b'abc').hexdigest()
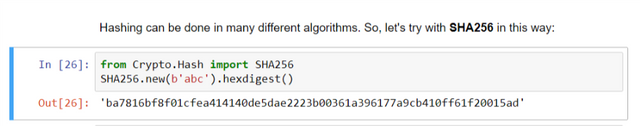
Here, string 'b' in the input of the function new() represents byte string.
So, ba7816bf8f01cfea414140de5dae2223b00361a396177a9cb410ff61f20015ad is the hash for string abc using SHA256 hash algorithm. And this is unique. Everytime this string will give the same output and no other input shall give this particular hash.
In cryptography hash function, any algorithm which fails the 2 properties (mentioned below) are not used anymore. And this happened with MD5 algorithm-
- collision attacks - when 2 different inputs result in the same hash output. It was found in 2004 and 2008.
- preimage attacks - when a hash 'h' is put into the MD5 function and message m is obtained. where
hash(m) = hthat means the function is reversible which violates the property.
Application
Password management and Storage
Used for matching the password input with the hash of the password stored in the database.
Code snippet:
from Crypto.Hash import SHA256
# a function defined for checking if correct password entered?
def check_password(input_password, actual_password):
# here, SHA256.new() function input as bytes. So, used str.encode() function for
# encoding string into bytes.
actual_password_hash = SHA256.new(str.encode(actual_password)).hexdigest() # hash of actual password
input_password_hash = SHA256.new(str.encode(input_password)).hexdigest() # hash of input password
return input_password_hash == actual_password_hash
Let's make a small application where one enters the password and its hash gets stored.
While entering the password next time, it will return TRUE or FALSE by inserting into
check_password() function.
# save the actual password
a = input("Enter the actual password:") # runs 1 time.
# This loop ends only when the correct password is entered, otherwise it continues.
while(1):
i = input("Enter your actual password again:")
result = check_password(i, a) # checks the password
if result == True:
print("Congrats!... Correct password.")
break
else:
print("Sorry!... INCORRECT password\n\n")
# End of the code...
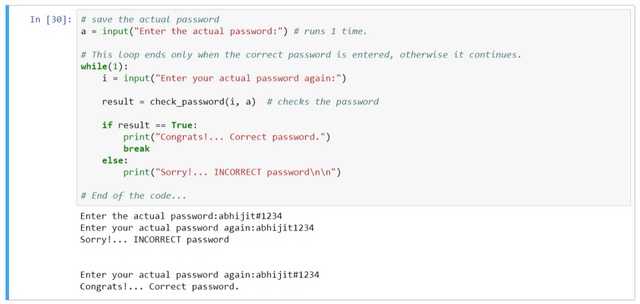
So, entering wrong returns FALSE i.e. 'Incorrect password'.
This is how the Login screen works in the back-end of the code.
Conclusion
At last, this is the summary about the hash functions in tabular format.
| Hash function | Hash output size (bits) | Secure? |
|---|---|---|
| MD2 | 128 | No |
| MD4 | 128 | No |
| MD5 | 128 | No |
| SHA-1 | 160 | No |
| SHA-256 | 256 | Yes |
In recent date, there are many more hash functions like X11 which is present in Bitcoin Segwit2x, the new version of Bitcoin (old one uses SHA-256) for mining purpose.
In the subsequent tutorials, we will learn more about programming Cryptography methods using python.
That's all for now...
Stay tuned for more such tutorials.....
View in Github
Posted on Utopian.io - Rewarding Open Source Contributors
Thank you for the contribution. It has been approved.
You can contact us on Discord.
[utopian-moderator]
Hey @abhi3700 I am @utopian-io. I have just upvoted you!
Achievements
Suggestions
Get Noticed!
Community-Driven Witness!
I am the first and only Steem Community-Driven Witness. Participate on Discord. Lets GROW TOGETHER!
Up-vote this comment to grow my power and help Open Source contributions like this one. Want to chat? Join me on Discord https://discord.gg/Pc8HG9x