Breaking the Attack Cycle
Breaking the Attack Cycle
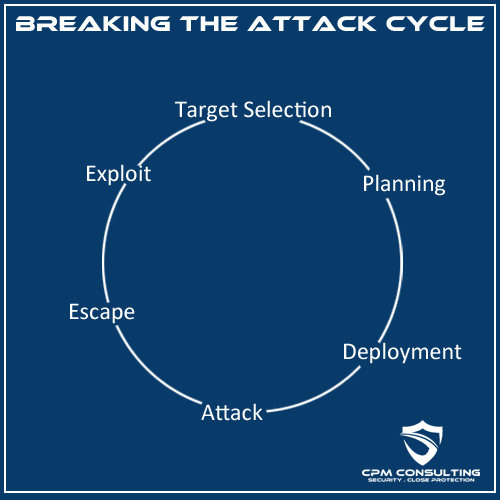
Unless spontaneous and opportunistic, both criminals and terrorists alike will have a plan to follow prior to, during and after an act, this remains the case for an unsophisticated attack as even inept criminal or terrorist will make some attempt at preparation.
At each stage of the attack cycle there are opportunities to detect and break the chain of events, whilst this is not always possible to do, the objective is to make life harder for those planning to conduct a terror or criminal operation, you may force them to slip up and reveal themselves, either way, we certainly shouldn’t make it easy for them!
The purpose of this article is merely to get people thinking about the various stages of the cycle and what you can do to protect yourself or business, and to be less of a target.
If you consider yourself a target (high net worth or in in position of power) or if you have a responsibility for people, either as a business owner or someone working in protective security then the attack cycle is something you should be aware of.
Target Selection
Why choose one target over an other? Dependent on the aims of the operation there could be a multitude of reasons. Is that house the only one without an alarm? Are the security procedures a bit relaxed at that government building? Does a certain location have potential for high victim density?
Attack aims play a role in the selection of a target. One criteria is the viability. If your house is without an alarm then it will be a more attractive target of a thief. If your nightclub door search security policy is poor you may find yourself dealing with a shooting incident or worse. If the person you’re protecting constantly updates social media with their location and pictures of high value possessions then, as seen recently in more than one case, your client may be targeted by organised criminals.
To break the attack cycle at this stage avoid presenting yourself or your asset as an obvious target. Not easy for VIP's, people of high profile or for well known Buildings, Installations and Institutions. By their nature they are in the public domain and require the skills of professional security personnel.
Planning
The level of planning can be dramatically different depending on the target and the organisation or individuals involved. Organisations such as the IRA, Al Qaeda or criminal groups plan at an extremely high level. Evidence suggests that planning for the AQ attack on the twin towers started as far back as 1996.
Those involved in attack planning need to know how to do the job and what is needed. There may be opportunities to spot the purchase or theft of special tools, equipment or chemicals in the lead up to an operation.
Usually there will be an increase of communication. For government level intelligence and surveillance agencies this is a key indicator of an imminent attack. In the past there have been failures to notice communications with devastating consequences. One example being the Omagh bombing carried out by RIRA in August 1998. There was intelligence leading to the bombers, GCHQ were monitoring their communication on the way to the target site but this information was not relayed or shared across all agencies prior to the attack.
It’s about putting together many pieces of a puzzle. If they are not shared then the task is made harder for all those involved in trying to stop a crime or act of terror taking place.
During planning hostile surveillance is likely and although it may be unsophisticated it can be hard to detect. Planning a Bank robbery,for example, the criminal will want to know, where the entry points are , where are the alarms, where are security guards posted, window locations, nearest Police station. Are the security guards highly professional or likely to be more interested in their phones? How many pedestrians are in the street, what's the traffic like? Where are the exit routes via road and public transport?
Many questions, and that’s for a Bank robbery. Planning a complicated act of terrorism or attack against an individual protected by a security team is harder. The level of planning and difficulty may expose the forces involved at the hostile reconnaissance stage.
Keep noticing the same person hanging around? Make a note of it. See someone filming suspiciously? Report it. If you work on a protective security team and the same faces appear in different locations it’s time to take additional precautions.
Mitigating hostile reconnaissance requires deterrence, training and a robust approach to professional security. If you are a UK based business you can receive training on these subjects through a local Counter Terrorism Security advisor, You can find your local office by clicking here – Ask them about Project Argus and Project Griffin.
Deployment / Attack
Well planned attacks, criminal or terror based, often succeed, especially now that we face a new breed of enemy. One which is highly motivated, well trained and willing to die. Less well trained but equally successful lone wolf attackers are hard to detect. However, they may be backed by networks that have a planning structure similar to that of a modern military unit incorporating specialists communications, logistics, explosives, Cyber warfare and Psy-ops.
Surveillance is complete, planning done, time to deploy and attack. Once the attack is initiated the methods to stop or hinder it are preventative security measures, blast walls, blast doors, reactive security teams and the rapid response of government agencies.
Below are detailed the most common types of attack and some mitigation measures, not an exhaustive list but something to get you thinking.
Firearm / weapon attack – Cost effective, little planning required, Easy for a lone wolf – High impact, mass casualty, often ends with a hostage situation – Think the Paris attack or the attack and murder in Woolwich of Lee Rigby, with minimal planning and very lost cost the attack can generate a high impact world wide.
Mitigation measures can include security drills and the use of different alarms. We all know how to respond to a fire alarm and practice the drill in a work setting but we rarely (outside of Government buildings) have specific alarms for a terror attack. Something to think about if responsible for people in an office or public setting.
Advice from the UK Counter Terrorism Security Office on improving your chances in an attack are summarised as follows:
RUN - Escape if you can - Consider the safest options - Is there a safe route? Run, if not hide
Can you get there without exposing yourself to greater danger? - Insist others leave with you
Leave belongings behind.
HIDE - If you can’t run, hide - Find cover from gunfire - If you can see the attacker, they may be able to see you - Cover from view does not mean you are safe, bullets go through glass, brick, wood and metal
Find cover from gunfire e.g. substantial brickwork / heavy reinforced walls - Be aware of your exits
Try not to get trapped - Be quiet, silence your phone - Lock / barricade yourself in - Move away from the door.
TELL - Call 999 - What do the police need to know? - Location - Where are the suspects? - Direction - Where did you last see the suspects? - Descriptions – Describe the attacker, numbers, features, clothing, weapons etc - Further information – Casualties, type of injury, building information, entrances, exits,hostages etc - Stop other people entering the building if it is safe to do so.

Types of Attack Continued…..
Vehicle Borne Improvised Explosive Devices (VBIED’s) – These are High impact, high damage and have the potential to cause mass casualty, fairly easy to plan, able to strike at distance, have a high psychological value on the public in terms of filling people with fear. Mitigations – Hard to mitigate against a large scale blast which will often destroy counter measures and any reactive security teams in the locality. Blast walls, Hesco’s, blast film, barriers, bollards and parking restrictions help protect high value targets. In the City of London much of the infrastructure and building entrances are designed to minimise blast impact. Next time you’re in the city, see how many cleverly designed countermeasures you can spot.
Complex / Combined Attacks – Common in Conflict or Hostile zones such as Afghanistan and Iraq. Generally initiated by a blast followed by an attack, but occasionally, as in the attack on the Serena Hotel in Kabul in 2008, it can start with suicide bombers and rockets. Anything that combines multiple attack methods can be considered complex. The intention of an initial attack phase is to decimate defences and cause panic. A ground force of fighters, often wearing suicide vests follow up to maximise devastation.
Mitigation measures – Mentioned blast measures improve survivability during the initial phase of the attack. A well trained, professional, reactive security presence will be vital to stopping continuation of the attack post the initial blast. Similarly to VBIED attack, drills, repeated training, good communication and continuously reviewed planning for such events is paramount.
Cyber Attacks – One of the biggest threats facing governments and business organisations today, many of whom are unprepared and slow to recognise the danger. The devastation caused by a successful attack on vital national infrastructure cannot be underestimated and a major concern is the possibility that cyber and physical attacks could be combined to create chaos.
How long could you cope without water, gas, electricity and food? The provision of utilities, services, transport and distribution are vital and interdependent. Serious interference affecting one or multiple institutions and infrastructure may have exponential consequences affecting social cohesion.
Mitigation measures – As an individual, educate yourself. Everything you learn about password policy’s, password lockers, VPN’s, dangers of public Wi-Fi, the importance of Anti-Virus, Phishing and Malware will increase your awareness of potential threats.. The subject is immense.
If a determined attack is targeting you directly it is likely to succeed. Simple protection measures are changing pin numbers and passwords frequently, not using the same ones for multiple purposes. Clear history on computers and mobile devices. There are less obvious pieces of information that can be used to build up a target profile. If you add your Bank to your favourites it gives a criminal a head start, your birthday shown on social media is vital information. Photos posted instantly of you abroad or out for an evening advertise that your home may be empty.
Photos of expensive possessions may attract criminals. Simple giveaways such as home addresses on luggage labels have been targeted by criminals at airports to identify unoccupied properties. In recent times there were a spate of Burglaries at the homes of EPL footballers when they were known to be playing.
They have to play but a security assessment would have seen those times as potential risks. At a business level, have your business audited and checked by a Cyber security professional. One that can probe your network looking for the holes that hackers exploit. We cannot emphasise enough to businesses, if you value your organisation then this is absolutely vital.

Just some of the Possible Attack Vectors on a modern Vehicle! (Image from Cyber Matters https://www.profwoodward.org)
The Escape and Exploitation
The escape phase of a criminal act is vital in the planning of an operation. They wish to enjoy the proceeds or outcome of their crime and avoid spending their lives languishing in a prison cell.
In recent years the dynamic of terrorists has changed in that those perpetrating the act have become expendable. At the tip of the spear they are ready to die and often no escape plan is considered. However, at the planning and operational level a large amount of effort is made to cover tracks and effect an escape so as to plan, supply and execute future operations. The bomb-makers, logistics teams and tacticians of Terrorist cells being more valued assets than foot soldiers.
Following attacks exploitation is massively important as a recruiting tool, to spread fear (execution videos etc.) and as an advertisement for further funding. Groups such as ISIS and Al Qaeda have taken this to a previously unseen level with live accounts prolific on social media, newsletters and professionally produced films about their operations and life inside their organisations. It works very well indeed. As fast as Western agencies block or shut down their accounts and remove their films they spread across the internet with ease.
Terrorist attacks by nature, are high profile, always newsworthy, always shocking but in fact are rare. The majority of Worldwide attacks have occurred in just three countries, Afghanistan, Iraq and Pakistan. In Western Europe between 1970 and 2014, 6435 people were killed due to acts of terror. To put that in perspective, double that number are murdered in the USA each year.
The chances of being subjected to a Terrorist event are low but the possibility is real. Threats are there constantly. Vigilance is a safeguard and a deterrent. Complacency identifies you as a target. Be aware, educate yourself about the risks, learn about the correct precautions to take and employ professional help where needed.