How to capture Network packets with Tcpdump!
In this part we‘ll have a look at packet-capturing and ARP-Spoofing. So what‘s going to happen now?
We are going to tell Machine A(the target) that we are machine C(the router) and route the packets for Machine A to C(and vice versa) through us so that we can capture these packets.
So the Setup we use here is the following:
We‘ll use two virtual machines. One with a kali linux installation(attacker) and another one with debian running(victim). The victim-machine can also be a windows machine. It doesn‘t really matter.
The Kali machine has the following programs we‘ll use preinstalled:
arpspoof
tcpdump
If you use another linux distribution you can install these two via your packet manager. These programs should be available to nearly all linux distros.
ARP-Spoofing:
ARP-Spoofing is the process of sending crafted responses to a network device in order to trick it into routing its packets the wrong way(your way).
First we‘ll fire up our Kali machine and open a terminal where we type:
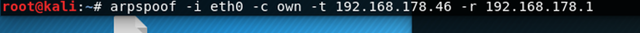
You might ask yourself what does that all mean? Don‘t worry because we‘ll get into it.
Arpspoof is, as mentioned earlier, the name of the program we‘ll use.
-i: specifies the interface we want to use(if you don‘t know the name type ifconfig or ip a)
-c: specifies the HW-Address when restoring the ARP-configuration other options are host and both
-t: is the targets IP-address
-r: is the routers IP-address
Now the packets will get routed through us because the router thinks we are the IP-address 192.168.178.46 and vice versa. Thats because the arpspoof will send ARP-Response to both, the router and the target. If you don‘t know what‘s an ARP-Response you can look it up here
Next we open another terminal and type the following
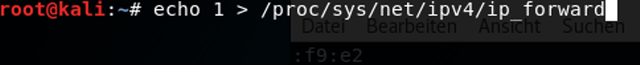
This command will enable packet-forwarding so that the packets don‘t get stuck with us and will be routed to the router and from there on out to the Internet.
Now we need to open another terminal and type the following
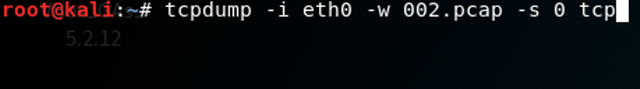
Tcpdump is again the name of the program
-i: specifies again the network interface(Your Networking card) you want to use
-w: tells tcpdump to write the captured packets to the specified file(This is important because otherwise you‘ll get the output of the captured packets in the terminal)
-s: specifies the size of the packets to be captured. 0 tells tcpdump to capture whole packets
tcp: tells tcpdump which type of packets you want to capture. In this case there won‘t be any DNS-Queries because we won‘t capture UDP packets
So now we are capturing packets which will be written to the file 002.pcap that can be analyzed with a tool called wireshark. If you want tcpdump to stop you can press ctrl +c while in the terminal. The same goes for arpspoof. When you end arpspoof you‘ll see the following output.
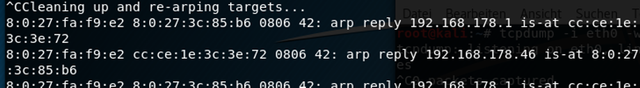
You see that arpspoof is cleaning up behind you so the packets will get routed from the target to the router and back again.
So that‘s it for today. Hope to see you soon!
I will be featuring it in my weekly #technology and #science curation post for the @minnowsupport project and the Tech Bloggers' Guild! The Tech Bloggers' Guild is a new group of Steem bloggers and content creators looking to improve the overall quality of our niche.
Wish not to be featured in the curation post this Friday? Please let me know. In the meantime, keep up the hard work, and I hope to see you at the Tech Bloggers' Guild!
If you have a free witness vote and like what I am doing for the Steem blockchain it would be an honor to have your vote for my witness server. Either click this SteemConnect link or head over to steemit.com/~witnesses and enter my username it the box at the bottom.
I would be honored to be featured!
Good stuff, upvoted and followed you.
I post about security, coding and photography if you want to take a look:
https://steemit.com/security/@gaottantacinque/javascript-pills-3-download-a-file-programmatically-website-affected-by-xss-vuln
Thanks :D
upvote for me please? https://steemit.com/news/@bible.com/6h36cq