4 commonly used attacks by hackers.
hello guys!!!
this is tanshu blogs and i am going to tell you about some of the commonly used attacks
by hackers.
so dont forget to follow the account and upvote and comment.
1 . Man-in-the-middle (MitM) attack
A MitM attack occurs when a hacker inserts itself between the communications of a client
and a server. Here is a common man-in-the-middle attacks: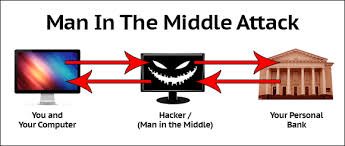
Session hijacking
In this type of MitM attack, an attacker hijacks a session between a trusted client and
network server. The attacking computer substitutes its IP address for the trusted client
while the server continues the session, believing it is communicating with the client.
For instance, the attack might unfold like this:
A client connects to a server.
The attacker’s computer gains control of the client pc/network.
The attacker’s computer disconnects the client from the server network.
The attacker’s computer replaces the client’s IP address with its own IP address and
spoofs the client’s sequence numbers.
The attacker’s computer continues dialog with the server and the server believes it
still communicating with the client.
2 . SQL injection attack.jpg)
SQL injection is a common issue with database consisting websites. It occurs when a
malefactor executes a SQL query to the database via the input data from the client to
server. SQL commands are inserted into data-plane input (for example, instead of the
login or password) in order to run predefined SQL commands. A successful SQL injection
exploit can read sensitive data from the database, modify (insert, update or delete)
database data, execute administration operations (such as shutdown) on the database,
recover the content of a given file, and, in some cases, issue commands to the
operating system.
3 . Cross-site scripting (XSS) attack
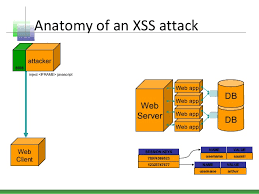
XSS attacks use third-party web resources to run scripts in the victim’s web browser or
scriptable application. Specifically, the attacker injects a payload with malicious
JavaScript into a website’s database. When the victim requests a page from the website,
the website transmits the page, with the attacker’s payload as part of the HTML body,
to the victim’s browser, which executes the malicious script. For example, it might
send the victim’s cookie to the attacker’s server, and the attacker can extract it and
use it for session hijacking. The most dangerous consequences occur when XSS is used
to exploit additional vulnerabilities. These vulnerabilities can enable an attacker to
not only steal cookies, but also log key strokes, capture screenshots, discover and
collect network information, and remotely access and control the victim’s machine.
whatsapp can be hacked using this attack.
4 . Malware attack
.png)
Malicious software can be described as unwanted software that is installed in your
system without your consent. It can attach itself to legitimate code and propagate; it
can lurk in useful applications or replicate itself across the Internet. some
most common types of malware are:
=>File infector malware — File infector viruses usually attach themselves to executable code,
such as .exe files. The virus is installed when the code is loaded. Another version of a
file infector associates itself with a file by creating a virus file with the same name,
but an .exe extension. Therefore, when the file is opened, the virus code will execute.
=>System or boot-record infector/malware — A boot-record virus attaches to the master boot
record on hard disks. When the system is started, it will look at the boot sector and
load the virus into memory, where it can propagate to other disks and computers.
=>Trojans — A Trojan or a Trojan horse is a program that hides in a useful program and
usually has a malicious function. A major difference between viruses and Trojans is that
Trojans do not self-replicate. In addition to launching attacks on a system, a Trojan
can establish a back door that can be exploited by attackers. For example, a Trojan can
be programmed to open a high-numbered port so the hacker can use it to listen and then
perform an attack.
=> Worms — Worms differ from viruses in that they do not attach to a host file, but are
self-replicating programs that propagate across networks and computers. Worms are
commonly spread through email attachments; opening the attachment activates the worm
program. A typical worm exploit involves the worm sending a copy of itself to every
contact in an infected computer’s email address In addition to conducting malicious
activities, a worm spreading across the internet and overloading email servers can
result in denial-of-service attacks against nodes on the network.
hope you liked it .
thank you.
my post up vote me and follow me.
ok. same dude you also upvote me and follow me.