The neural network "peeped" the smartphone PIN through accelerometer data and other sensors.
Modern smartphones can contain a lot of confidential information: the history of correspondence, applications for managing a bank account or important documents. Because of this, attackers are developing new ways to crack smartphones, and not all of them do it directly with the help of vulnerabilities in the software. Some developers create methods of hacking, based on the principle of attack by third-party channels. It implies that the attack is not performed on the system as such, but on its practical implementation - for example, you can find out the operations performed by the processor and their parameters, measuring its power consumption.
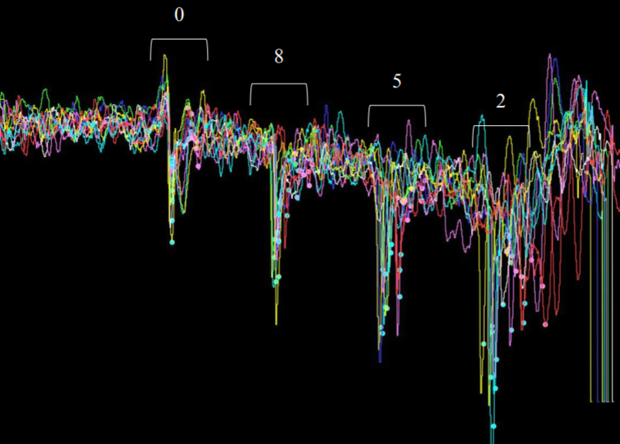
Source image Example of entering the combination 0852 on the graph of data from the accelerometer.
Researchers in the field of information security used to discreetly identify the smartphone's PIN-code data from its sensors. They wrote an application for Android smartphones that collects data from sensors, and then sends them to the server for analysis. The developers chose six sensors that are present in most modern smartphones, and at the same time for their use the application does not need to get the user's permission: an accelerometer, a gyroscope, a rotation sensor, a magnetometer and an ambient light sensor.
Since the numbers on the keyboard are located in known places, by tilting the device or changing the amount of light that falls on the light sensor, you can calculate which key the user pressed, without the need for data directly from the touch screen. In order to automatically calculate the figures from a large amount of data, researchers used different algorithms, but eventually settled on the type of neural network, called a multilayer perceptron.
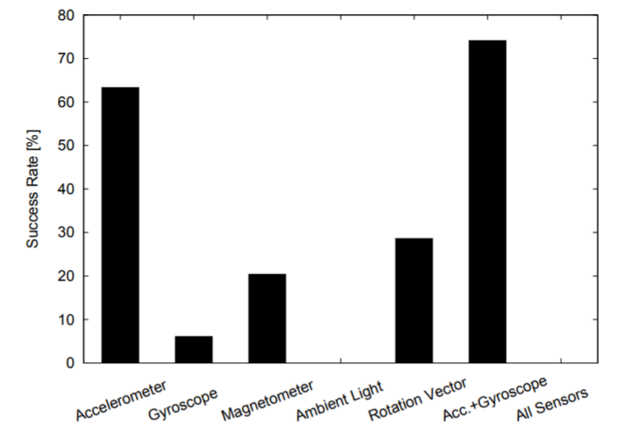
Source image The success of the code selection, depending on which data from which sensor was used.
There were a few other authentication attacks that I found interesting, but this takes the cake. I remember reading about how someone broke touch ID by lifting a fingerprint off the screen, and how face ID could be broken using a 3d printed mask. Face ID seems especially vulnerable as you are literally wearing your password on your face. Picking up someones pin based on accelerator data is clever and interesting to say the least, as it opens up new attack vectors on ATMs and PoS systems. - Resteemed
=)
So, place phone on a flat, soft surface, cover front camera then enter your pass code one digit at a time with a one second space between each digit... that might thwart this attack, probably not though, lol...
=))