Biometric Technologies

The idea of identifying a person by its physiological characteristics was not born yesterday. Conclusions of artifacts of ancient civilizations in several thousand years indicate that at that time fingerprints or fingerprints were already used. For example, for transactions or for searching criminals.
In a more or less modern form, biometrics began to be used in the nineteenth century in police departments. But it was not until the 1920s that this practice became permanent and systematized in the criminal identification data warehouse. In the 80s, this process was already automated, and fingerprints were the main biometric parameter for the search for criminals.
Modern technologies use a much wider range of biometric characteristics. Usually, depending on the type of biometric parameters used, two groups of systems are distinguished.
The first group of systems uses static biometric parameters (physiological): fingerprints, hand geometry, the retina of the eye, etc. The second group of systems uses dynamic parameters (behavioral ones) for identification: the dynamics of the signature reproduction or handwritten keyword, voice
Biometric technologies for today are needed not only for such routine procedures like issuing a passport or unlocking a smartphone with your finger. In many developed countries, the detection of persons in crowded places is used to ensure safety. For example, in shopping malls, this helps prevent crime and violence. At airports, convenience is improved (faces of owners of biometric passports are automatically checked by the system with photos in the document), and likelihood of terrorist attacks also decreases.
There were some rather unpleasant incidents. On Superbowle 2001 (in American football the name of the final game for the title of champion of the National Football League of the USA), the system of identifying persons mistakenly took more than a dozen people for criminals. In addition, this incident provoked a surge of media speeches about the violation of the right to confidentiality.
But after the tragedy of September 11, interest in biometric technologies again sharply increases, as the usual identification through document verification was not enough to ensure security. The next 5 years there has been an intensified improvement in the systems of facial recognition in the United States and the coordination of efforts of various bodies of the European Union. In 2004, regulatory norms are introduced that improve the joint rules for the safety of EU passports and other travel documents. Their goal is to increase the security of documents, to establish a more effective link between the document and its owner and, thus, to increase protection against counterfeiting or fraud using other people's passports.
By the way, the attitude to biometrics technologies, even in scientific circles, is rather ambiguous. Approximately since 2002 in narrowly specialized publications, as well as in freshwater communication and problem-free access based on biometrics.
One of the most impressive studies of this kind appeared in the summer of 2002, when employees of the German computer magazine "c't", with the help of simple tools, immediately compromised 11 biometric verification systems based on three basic technologies - recognition of fingers, faces and the iris of users' eyes ,
The IAFIS research system ("Integrated Automated Fingerprint Identification System") found the coincidence of one fingerprint with a person who had nothing to do with the crime. Oregon lawyer, Muslim Brandon Mayfield, who previously defended a person in court, suspected of terrorism, was accused of extremism in connection with the terrorist bombings in Madrid. The most important evidence for the investigation was a plastic bag with detonators to the bombs and fingerprints. Fortunately, the Spanish police detained another man, Algerian Unan Daud, who has not one, and all the fingerprints coincide with the tracks on the package with detonators.

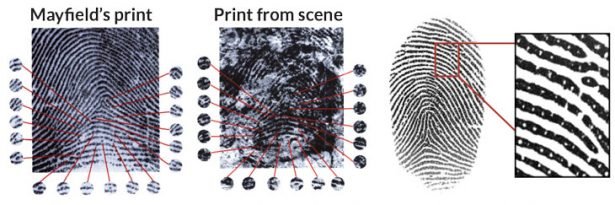
On the picture.
Lawyer Brandon Mayfield and his fingerprints, which are "lucky", coincide with the imprints of the terrorist Unan Daud
But already approximately since 2010 biometric technologies become a part of our daily routine, although we do not think much about it. So, the face recognition function is used in digital cameras, and in smartphone cameras. Built-in search programs can automatically find in the picture frame, images for shooting, human faces by their characteristic features - eyes, ears, nose, etc. Also, social networks and digital albums began to quite accurately recognize both you and your friends by offering them them in the pictures.
In 2016, Samsung will present the device with an iris scanner to increase the level of security of access to the device, MasterCard, Visa and other financial organizations include biometric authentication of payments. They mostly use fingerprint analyzers and retinal scanners.
Last year, the fastest growing sector in the use of face recognition technologies are retail trade networks. In addition, Apple represents the iPhone X with Face Identification technology. Obviously, the newest trend is precisely the identification of individuals, which is being improved every day.
Non-standard methods of biometrics that are developed for future use
Today, experiments are underway with all possible characteristics, from monitoring your heartbeat (such a solution is already being tested by MasterCard) before implanting the chips under the skin, scanning the pattern of intraocular vessels, earlobe shape, etc.
The Abicus project from Google plans to track the unique features of human speech, which will in the future establish the authenticity of your personality, even while talking on the phone.
Experimental CCTV cameras track a person literally by his gait - this technology works well in a single intelligent house ecosystem.
TeleSign has launched a behavior ID based on the user's Internet surfing. The application records how the user moves the mouse, in which places the screen most often clicks. As a result, the program creates a unique digital fingerprint of the user's behavior.
The veins in the wrists, palms and fingers can also be used as unique identifiers - moreover, they can complement existing fingerprint identification methods. It is based on the principle of varying degrees of reflection of infrared rays from blood vessels and other internal organs. At cost, this method is cheaper to identify by the iris of the eyes and face.
Still, despite possible shortcomings of biometric technologies, their use is becoming common in many areas, even in everyday life. In addition, the improvement of the accuracy of popular technologies and the development of innovative methods of recognition is quite fast. Therefore, it is very likely that in the near future we will open our own homes with the help of a wave of the hand or a voice signal.
Congratulations @didus62, you have decided to take the next big step with your first post! The Steem Network Team wishes you a great time among this awesome community.
The proven road to boost your personal success in this amazing Steem Network
Do you already know that awesome content will get great profits by following these simple steps that have been worked out by experts?
Congratulations @didus62! You have completed some achievement on Steemit and have been rewarded with new badge(s) :
Click on any badge to view your own Board of Honor on SteemitBoard.
For more information about SteemitBoard, click here
If you no longer want to receive notifications, reply to this comment with the word
STOP