"BASICS OF ETHICAL HACKING:SERIES #4.2"

Hi friends,I am continuing my post of "BASICS OF ETHICAL HACKING SERIES".
I am continuing my previous post of Malware Research -Trojans and Keyloggers
I my previous post I have discussed Some popular local keyloggers that are:
Spy Agent
Refog Keylogger
Now we learn details about them.
- Spy Agent
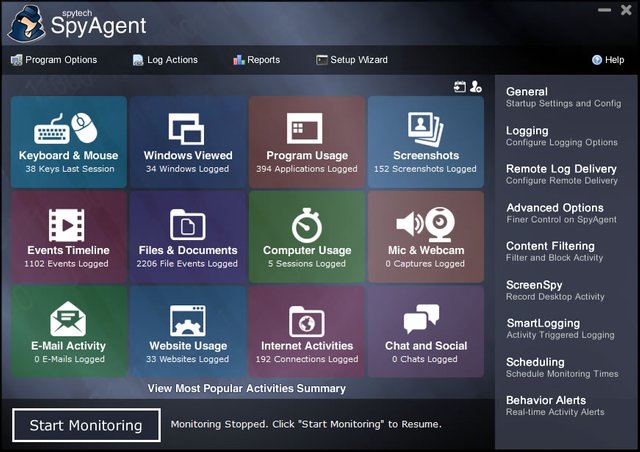
Spy Agent is an award-winning software,which is used to monitor both local and remote computers.It invisibly monitors all computer usage and internet activities.SpyAgent's logging capabilities are unmatched.Spy Agent can log anything from what the users type,to the files they print and programs they run,all time stamped by date for easy viewing.All logs are easily saved and exported for later use.SpyAgent can be configured to log all users on your computer with ease.Spy Agent monitors and logs both sides of all chat conversations made on chat clients like "yahoo Messenger","Msn Messenger" etc.
Features of SpyAgent Keylogger
It records:
Keystroke monitoring
Internet connections
Internet conversations
Website activity
E-mails sent and received
Files/documents accessed and printed
Window activity
Application usage
Screenshot capturing
Clipboard logging
Events logging
Activity logging
2.Refog Keylogger
Refog is extremely powerful and has very low antivirus detection rate.It is one of the leading remote passwords hacking software combined with Remote Viewing features.
Once installed on the remote PC(s),the user only needs to login to his/her personal Refog account to view activity logs of the remote PC.This means that the user can view logs of the remote Pc from anywhere in the world,as long as he/she has Internet access.
Features of Refog Keyloggers are as follows:
Keystroke recording: once installed and running,Refog registers all keys pressed by the user,thus acting as a keylogger.This function captures all data that has been entered using the keyboard,including chats,usernames,passwords,e-mails,search queries and other content.In addition to keylogging,Refog is also enabled to log clipboard text.
Web history logging: Even if users delete their "browser history",the information is retained in Refog's log database and is always available via the reports function.All relevant information can be collected including URL'S visited,page titles etc.
Application monitoring: Since Refog can record all programs executed on a PC,it is hence possible to establish if a child is playing games instead of doing homework,an employee is wasting time Online,data theft etc.
- Remote Keylogger:- Remote keyloggers are used for the purpose of monitoring a remote pc,Once a remote keylogger is installed on your computer the attacker can get your keystrokes,your webcam shots,chat logs etc sitting in any part of the world.
You can find tons of Remote keyloggers on web but lots of them are either not capableof properly recording keystrokes or they have "antivirus detection" rate.One keylogger worth the price is "Win Spy"
- Win Spy Keylogger
download Link: http://www.malavida.com/en/soft/win-spy-software/#gref
WinSpy software is a complete Stealth Monitoring Software that can both monitor your Local PC and Remote PC.It includes Remote Install and Real-Time PC viewer.Win Spy software will capture anything the user sees or types on the keyboard.
Features:
Remote Screen capture
Remote Monitoring
Remote PC Browser
Notify's User Online
Remote Sound Listening/Recording
Remote camera View/Recording
Remote File launch
Dual side Chat Recording
Remotely shutdown your computer
Remote Ftp(File Transfer Protocol)
WebCam- Motion Detect
WebAccess Remote PC
SMS Intruder Alert
works behind Firewall.
There are many topics in Malware Research -Trojans and Keyloggers,so I will continue it in my next post.
Objectives of writing this post:
My main purpose of writing this post is to inform you all that there is no way to completely protect a network unless one knows what he is up against.Only by knowing how an attack happens,and what all an attacker can do to compromise with a machine,individuals and organisations can properly protect their systems.
Legal issues:
I request to all readers to follow legal procedures under all circumstances because you are hacking into a system.
The government has made it mandatory to get prior permission before running any of the tools against any network.
There are many cyber laws made by the government,we must follow that otherwise It will be considered as a crime.
I have only basic information of ethical hacking learned from internet and by reading various books but I also want to learn it deeply.I want to join some big organization of ethical hacking institutes.But they are very costly.So I am finding a way to earn money and when I have enough money I will take admission to that ethical hacking institutes.
If you are interested to read my all previous series,please follow the link below:-
https://steemit.com/hacking/@danishali22786/basics-of-ethical-hacking-series-1
https://steemit.com/hacking/@danishali22786/basics-of-ethical-hacking-series-2
https://steemit.com/hacking/@danishali22786/basics-of-ethical-hacking-series-3
https://steemit.com/hacking/@danishali22786/basics-of-ethical-hacking-series-3.1
https://steemit.com/hacking/@danishali22786/basics-of-ethical-hacking-series-3.2
https://steemit.com/hacking/@danishali22786/basics-of-ethical-hacking-series-3.3
https://steemit.com/untalented/@danishali22786/basics-of-ethical-hacking-series-4
https://steemit.com/untalented/@danishali22786/basics-of-ethical-hacking-series-4-1
Thank you friends. If you like my post Please support me..
Congratulations! This post has been upvoted from the communal account, @minnowsupport, by DANISHSTEEMIT from the Minnow Support Project. It's a witness project run by aggroed, ausbitbank, teamsteem, theprophet0, someguy123, neoxian, followbtcnews, and netuoso. The goal is to help Steemit grow by supporting Minnows. Please find us at the Peace, Abundance, and Liberty Network (PALnet) Discord Channel. It's a completely public and open space to all members of the Steemit community who voluntarily choose to be there.
If you would like to delegate to the Minnow Support Project you can do so by clicking on the following links: 50SP, 100SP, 250SP, 500SP, 1000SP, 5000SP.
Be sure to leave at least 50SP undelegated on your account.