Is there a Man in the Middle of your communications? Some Internet security and Privacy concepts

Recently, a friend asked me to explain the difference between http and https and as always I will try to explain it, in the simplest and most basic way that I can, and go from there to introduce some security concepts. Finally, I will present some tools which may help you better take back your privacy.
Some security pros may say that it’s not enough, you are still vulnerable to such and such attack or you can’t avoid this and that. And they are probably right. If some bad-ass hacker group or MI6, NSA or whoever is after “you” specifically that you may need some next level Jason Bourne tech and techniques.
And the truth is, there is no perfect privacy solution, but there is pretty good privacy. But when it comes to privacy, a little bit of pretty good is infinitely better than none.
The casual user has to start somewhere. And in order to develop “basic Internet common sense” you must learn “basic Internet security concepts.” If you want to communicate privately, start with Secure connections and Encryption
------Note- This is written in a simplified way for the Non-technical person, by a non-technical. I will include links at the bottom which may serve you a starting point if you wish to do more research. ----
HTTP or - Hypertext Transfer Protocol is the application layer protocol of the web, and is how servers and clients ( your computer) communicate text, media and data between each other and express it the way see it our browsers.
Http:// is seen at the beginning of a website’s URL. Https means the site has a trusted certificate and has secure communication over the network. Many sites don’t need a secure connection, but this is important if you are transferring sensitive information such as secure logins, credit card numbers, or cryptocurrency wallets info, etc...
Most browser now show a green lock in front of the URL, showing it is a secure connection. Look for it before you login to a site as not to expose your sensitive financial data.

http://www.example.com
https://www.example.com - secure connection
--------- Without a secure connection, a third party could eavesdrop on your conversation, intercept your data and make changes, impersonate you, or make all kinds of mischief as of yet unimagined. - As with most things that involve nerds and geeks, there are specific names and nomenclature for everything, often seeming subtle differences will have there own technical names, but for the sake of simplicity I going to lump this into a broad category of security threats known as Man in the Middle attacks.
As the name suggests, Man in the Middle, involves a untrusted third party in the middle of the communication between two unknowing people or computers.

Sniffing is listening on the data communications, eavesdropping
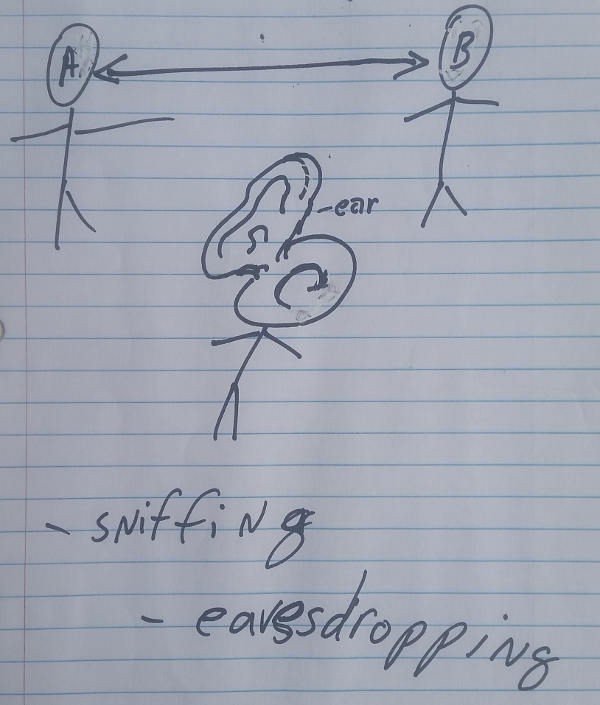
Sidejacking is sniffing data packets sent between computer and server for session cookies that may contain unencrypted passwords, this can be done even if site is secure. Anohter reason why encryption is important.
Evil twin: a fake wifi network that appears legit, but is really just collecting the unknowing users’ data and activity as they browse the internet. -------- The concept that a malicious party can listen and or intercept communications between two parties, whether that is http web browsing, sms, texting or email. --------- The solution is encryption of data and/or secure connections.
Steps you can take
- Https Look for the https or the green lock before you login into a site that handle your private data or, use the plugin Https Everywhere, brought to you by the Electronic Freedom Foundation.
- Signal - Try Signal for secure sms text message. Open-source and free, it encrypts message end to end. And it features disappearing messages, which can be to erase themselves in as little as 5 secs. This is a great product! Highly recommended
- Encrypt your email Encrypt your email or use Protonmail.com. Encrypted email based in Switzerland, with Swiss privacy laws. They have paid and free versions.
- Get a VPN, Virtual private network,
A VPN routes your traffic through a secure network even on public Wi-Fi. Not only does this give the benefits of a private network, it hides your activity from your ISP and changes you IP address and routes you through a different geographic location. The site you are visiting will think you are in a different city or country. Potential uses include accessing site or media in regions that are blocked. Theoretically, one could use it to participate in ICO.
There are lots of VPN providers. Paid VPN are recommended for security and more options. Some providers accept cryptocurrencies like Bitcoin or Monero for added privacy.
I like Proton VPN. made by the same people that make Protonmail. - The Opera browser offers free VPN service built in to the browser. It has limited options and is not open source but its free and worth a try if you would like to experiment with VPNs
- Try to avoid open public Wifi but if you must, consider a vpn.
I typically use my own mobile hotspot and use VPN.
To repeat the truth is there is no perfect privacy solution, but there is pretty good privacy. As with most things, when it comes to privacy, even a little bit is infinitely better than none.
I am still learning as we all are in this every changing world and hope you find this information useful.
---Thanks to @itsmee.bosslady for the suggesting the post
Humbly Yours,
Johnny Dollar
— — — — — — — — — —
Reference:
Signal secure sms mms
Mailvelope — Open source email encryption
