Your device is vulnerable to hackers, if you don't...
It is scary to think that you are likely reading this post from a computing device that is vulnerable to attack. All modern computing devices (computers, mobile phones) that are less than 20 years old have been flagged to be susceptible to Spectre and Meltdownprocessor vulnerabilities.
Google's Project Zero Team led by Han Horn discovered the vulnerabilities and reported it to Intel, ARM and AMD on June 1, 2017.
What is Meltdown?
Meltdown attacks out-of-order execution on microprocessors to read kernel-memory location for personal information and passwords. Out-of-order execution in microprocessors is used to make use of instruction cycles that would wast by costly delays in waiting for inputs. That is modern processors look ahead to schedule future operations instead of strictly perform operations sequentially in program order, they perform operations as soon as all the required resources are available. Hence, processors can run another set of instruction ahead while the current process is occupied. Therefore, instructions can be run in parallel as long as it follows the architectural definition. Out-of-Order is a performance feature and available in many modern processors. Microprocessors that have the performance "Out-of-order" execution feature allows Speculative operations to the level that CPUs out-of-order logic performs operations before the microprocessor is satisfied if the instruction is needed and committed.
What is Spectre?
Spectre
Microprocessors use branch predictive and speculative execution to optimise performance. Branch prediction allows a CPU to guess instruction in a computer program and thus deviates from the default behaviour of executing the instructions sequentially.
In Spectre, an adversary induces the victim to perform a speculative operation that would not be performed and in which the victim's information is leaked via side channel to the attacker.
These kinds of attacks present severe threats to over a billion devices in the market today since Processors from Intel, AMD and ARM are capable of speculative execution.
Meltdown VS Spectre
- Meltdown exploits out-of-order execution to leak physical memory
- Spectre uses branch prediction execution to achieve speculation
- Meltdown attacks a privilege escalation vulnerability specific to Intel processors which causes speculatively executed instructions to bypass memory protection.
Mitigations.
We have not seen any known attacks based on Spectre and Meltdown. But because of the number of affected devices, we are in a race to mitigate.
Since we have known the problem, is it not ideal to turn out-of-order and speculative executions on modern Processors? Well, these are crucial performance features in modern Processors and would impact heavily on our devices.
Spectre and Meltdown vulnerabilities affect hardware.
The race is now on by both Software and Hardware manufacturers to push updates and patches to mitigate against known vectors of attack for spectre and meltdown.
Google, Microsoft, McAfee etc. have released patches for their products, some of the updates require user action while some do not.
What can we do?
We are to ensure that our personal computers and mobile devices are running the latest security software released at least from January 3, 2018. We are to update devices both hardware and software including firmware and in some cases antivirus as they are released by vendors. On Windows devices, just turn on "Automatic Update."
What I have done to protect my workspace.
In an Enterprise IT environment, Software updates and patches are managed/controlled because it could be catastrophic to break workstations and servers. Security updates are tested before deploying to workstations/Servers, Spectre and Meltdown security patches need to be treated as such. OEMs are rolling out patches since January 2018 to address the vulnerabilities users (individual and Corporate organisations) are expected to update their_devices_.
Microsoft has rolled out updates for browsers, operating system etc. and also says that computers that do not meet a specific registry setting requirement will not receive the update. If your computer is running Microsoft antivirus or antivirus from a Microsoft partner that is compatible, the registry settings will be set automatically, and you will receive the security update else, you will have to set this manually. Setting registry on one computer is obviously easy but in a organization with many computers, you need to find a way to automate this task.
I will be discussing how to set the registry settings using Group Policy. Before that, this is what Microsoft says about the registry settings and security update
Setting the Registry Key
Caution Using Registry Editor incorrectly can cause serious problems that may require you to reinstall your operating system. Microsoft cannot guarantee that problems resulting from the incorrect use of Registry Editor can be solved. Use Registry Editor at your own risk. For information about how to edit the registry, view the "Changing keys and values" help topic in Registry Editor (Regedit.exe) or view the "Add and delete information in the registry" and "Edit registry data" help topics in Regedt32.exe.
Note: Customers will not receive the January 2018 security updates (or any subsequent security updates) and will not be protected from security vulnerabilities unless their antivirus software vendor sets the following registry key:
Key="HKEY_LOCAL_MACHINE" Subkey="SOFTWARE\Microsoft\Windows\CurrentVersion\QualityCompat" Value="cadca5fe-87d3-4b96-b7fb-a231484277cc" Type="REG_DWORD”
Data="0x00000000" Source
Since there is a caveat to this: it must be done carefully.
I have created Group Policy for this purpose. Group Policy is a feature in Microsoft Active Directory that controls Operating System, User and Application settings, It provides centralised management of those settings. The GPO I have created is called "Registry Settings." as in figure 1
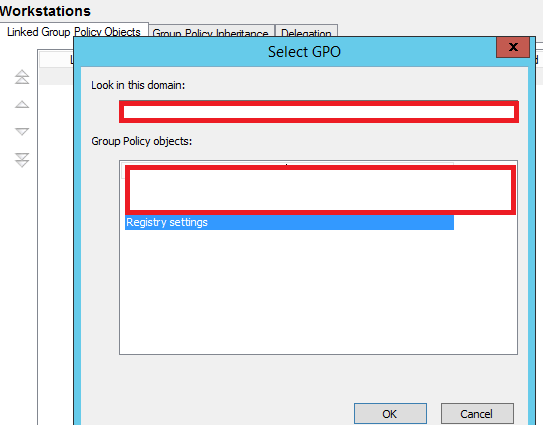
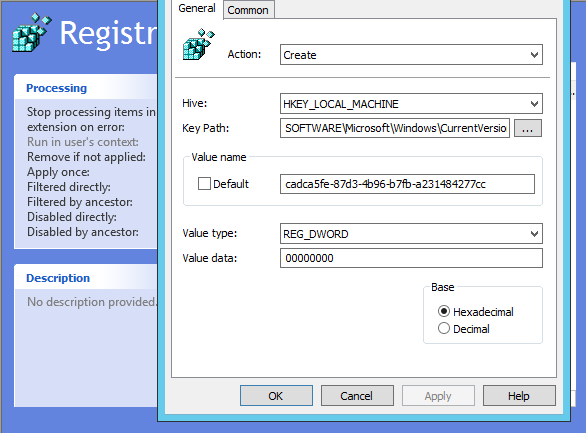
and linked it to a "Container" also known as Organizational Unit where I have all my Workstations.
All the computers will receive the Group Policy and hence be ready to receive Microsoft security updates of January 2018.
Dear Steemians, if your antivirus Vendor has released an update that creates the registry, you will receive Windows security update from Microsoft, and no action is required from you. More importantly, ensure that your devices are updated. Until next time, stay safe
Thank you.
References
Project Zero
Protect Windows Devices against Spectre and Meltdown
Windows Security and Antivitus
It's a great article...nice post
Thanks.
It is scary indeed but most people that are not as tech savvy as you obviously are would not know the trouble they are until it is too late to do anything about it. Thanks for sharing.
The number of devices affected are alarming.
Good right up.