End to end encryption technology: What about the Man in the middle?
INTRODUCTION
Sometimes you would love to stay alone in an enclosure, or probably with someone else without the need for a third party and completely away from possible eavesdropping as your conversations and activities needed to be kept on a personal note or in essence between the two parties involved in such conversation or activity, in some cases this may involve only the parties directly concerned with the agenda.

So,let this be a secret between us!. Source:Wikimedia - CC BY-SA 3.0.
Human privacy has been one of the most important aspect of human existence, not only is it needful for the full actualization of human right and human safety, the process of realization of full or reasonable level of human privacy has been a big puzzle and a huge point of focus. This is because, in as much as human privacy ensures personal safety from external influence and aids the performance of a given task without possible influence from a third party or a random individual or group with an undeclared interest, a full privacy also exposes the environment to other forms of danger as some unscrupulous acts would be carried out without regulations and possible aversion of an impending danger.
This forms a big dilemma as regards what should be kept private and what should be publicized and on a higher level, what those of higher echelon should make known to the lower ranked population. This enlarges the scope of privacy and secrecy and it thus exceeds the scope of just personal privacy. Many organizations, groups and not individuals also posses information which they wish to keep between them and employ these information for their personal use and the actualization of their own goals, maybe because this would place them in a more advantageous position and increase their chances of coming out on top.
Apart from the already mentioned reasons, some information are meant to be kept away from a third party to maintain peace and morality as an access to such records would stimulate ill feelings which leads to a strained personal relationship. In store houses, libraries or places designated for safe keeping of very important equipment or pieces, there arises the need to store objects in such a way that only a few set of people whom these information are meant for actually gets to understand them.

personal and group privacy has always been an important aspect of human existence. Source:Wikimedia - CC BY-SA 3.0.
In war situations too, information are meant to be transferred to the different teams which makes up a nation’s military without leaking the attack and defense plans to the enemy country.
Hence messages are passed through in a coded form in these situations and also in a way which a third party will be unable to decipher the information even if they mistakenly get to these information, while the supposed recipient would comfortably read and understand the information passed without much stress and despite the coding.
This ushered in the idea of end to end encryption communication system, end to end encryption communication system is a system of communication in which only the parties directly involved in a communication can read the messages and understand it’s contents while anyone else will be unable to do this.
A Brief history?
The complete history of end to end encryption is a bit obscured, this is because many ancient times forms of encryption is not actually end to end, better said, the encryption system doesn’t completely disallow the interference of a third party.
_-_Museo_scienza_e_tecnologia_Milano.jpg)
enigma machine, used for information encryption in 1930 during the world war. Source:Wikimedia - CC BY-SA 3.0.
The third party in the modern end to end encryption system maybe the telecommunications network provider in cases of call services or internet services, quintessential end to end encryption prevents even the owner of the network from being able to interfere in the activities going on over his network system. This prototype seems not to be in existence in far history even though historians that a relatively similar system existed in Egypt about a Four thousand years ago. But in essence this system cannot be clearly classified as an end to end encrypted system.
But a more related form of end to end encryption has been used by the military and this has enable the aversion of possible sabotage in the sense that these messages are passed across in such a way that even the soldier or messenger who is delivering the message is unable to read it.
Not until 2016, telecommunications network providers hasn’t really provided an end to end encryption system and what was existing was more of a safe client-server communication system and the users of the network system only have to trust their network providers with the safety of their information and activities over the platform as the network providers had access to their activities on the platform and can always get to it. Many network providers such as Lavabit and Hushmail had been said to run an end to end encryption system but in real sense, these encryption wasn’t actually end-end.
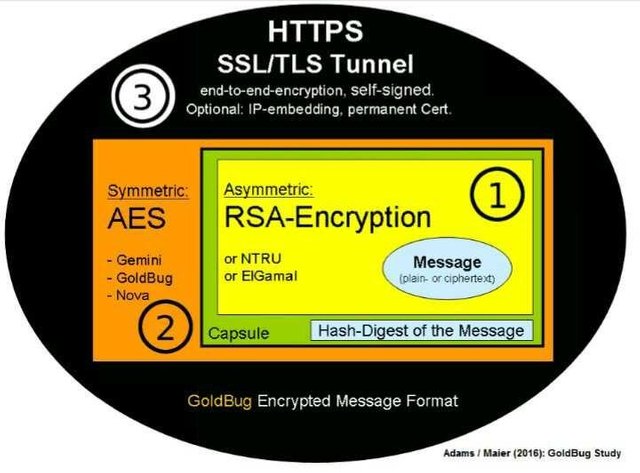
An encrypted message. Source:Wikimedia - CC BY-SA 3.0.
Many other network providers only performed a ‘client-side' encryption in which another client and not necessarily the server will be unable to gain access to your activities over the network, the servers however still holds the ability of decrypting information or activities over their network and thus the encryption isn’t server-user oriented. Popular messaging service Telegram had been criticised for not offering an end to end encryption service which they claimed to provide.
These events of ‘false’ end to end encryption have heralded the history of end to end encryption technology, this is not surprising because it would be really rare for a network provider to accord you a total privacy while the activities are actually performed over the network which they have a full control of. Many contemporary network providers who claims to run on an end to end encryption communication system still eavesdrops on the communications going on over their network when the need arises and this has been tagged a bridge in human privacy agreements.
Let’s move on…
The concept of end to end encryption is rapidly getting more popular than it ever was, many messaging networks today runs an end to end encryption, American based telecommunications gadget producing company Apple have been able to produce gadgets which runs an end to end encryption, this basic feature which seems peculiar to them has made their devices more popular.

iphone 5c, was used by the perpetrators of the San Bernardino attack in 2015 as the phone was encrypted. Source:Wikimedia - CC BY-SA 3.0.
Not everyone owns an ‘iPhone’, but this concept has span across individual messaging applications such as WhatsApp. Hence more people are privileged to have a basic idea of what end to end encryption really means and how it works.
What is an End to end encryption?
A FAQ page of popular messaging application whatsapp reads…
WhatsApp end-to-end encryption ensures only you and the person you’re Communicating with can read what’s sent, and nobody in between, not Even WhatsApp. Your messages are secured with locks, and only the Recipient and you have the special keys needed to unlock and read your Messages. For added protection, every message you send has an unique Lock and key. All of this happens automatically: No need to turn on Settings or set up special secret chats to secure your messages.
This depicts a perfect end to end encryption scheme and explains basically what the feature looks like.
Encryption is the process of coding a message in such a way that only the individuals or parties involved in such conversations are able to get the information; An end to end encryption system offers a hundred percent privacy to the users of a network, messages can only be read by both users or parties, thus eavesdroppers and even the network providers are prevented from being able to access the cryptographic key which enables them to decrypt the messages sent over their network. Thus any attempt of tampering with these information, invigilation or interception of the activities going on over the platform is prevented and only the users have the ability to control these actions.
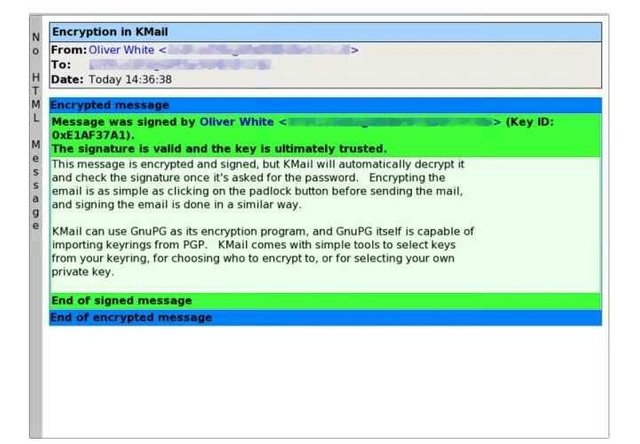
Kmail encryption. Source:Wikimedia - CC BY-SA 3.0.
Information over an encryption scheme is referred to as a plaintext and is encrypted using a cipher to generate a cipher text which can only be read when decrypted. This decryption and encryptions are secured using ‘keys’, to cipher or decipher these messages, one would need these keys before he/she would be able to gain access to these information.
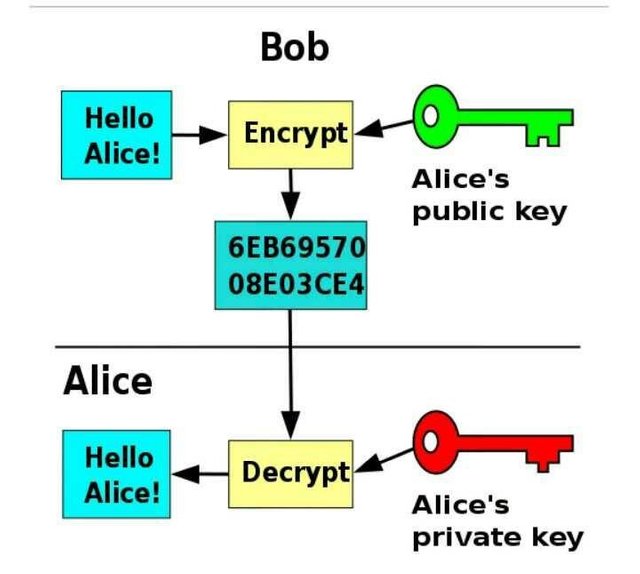
An encrypted message can only be decrypted using an assigned public key. Source:Wikimedia - CC BY-SA 3.0.
The keys however are only known to the parties involved directly in this communication, hence an eavesdropper who has access to these keys can also decrypt the messages sent over the network. This entails that, the safety of an end to end encryption system depends on the ability of these two parties to secure their private keys.
But what about the Man in the middle?
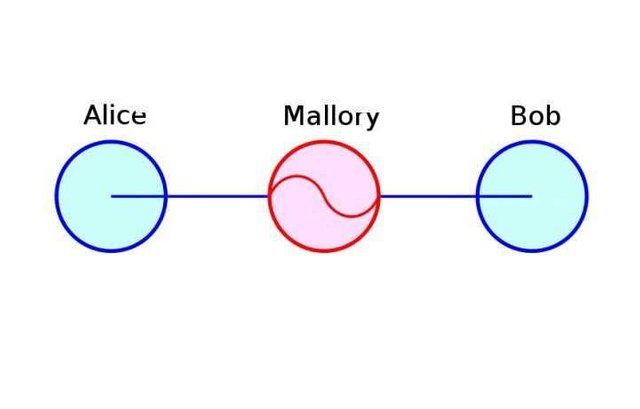
An illustration of a man in the middle attack. Source:Wikimedia - CC BY-SA 3.0.
Not the ‘man in the mirror’ this time around as that would be easier to deal with; the concept of keys has made the process of intercepting encrypted very tedious, time tasking and riskier, thus an eavesdropper might not want to go through all these thorns just to get to decrypt your messages.
‘Man in the middle’ attacks have turned out to be a huge challenge to the concept of end to end encryption, this involves the impersonation of the recipient of the message. Hence instead of attempting to break the encryption, the attacker substitutes his public key with the recipient’s public key and hence during key exchange, the attacker’s key would be recognized instead of the supposed recipient and he would be able to receive this information and to avoid detection by the server or the parties involved in this communication, the snoop can then Encrypt the message again after it has been read with a key that they share with the actual recipient and this message is sent on as encrypted without a trace of previous tampering of the information.
This has been the biggest challenge faced by the encryption technology, many ideas have been introduced to at least curb the incidence of man in the middle attacks (MITM), this includes authentication which involves the use of fingerprint technology. The fingerprints of the sender and recipient is obtained, compared and incorporated such than the man in the middle would need the fingerprints before he would be able to gain access to this information even if he successfully intercepts the communication.
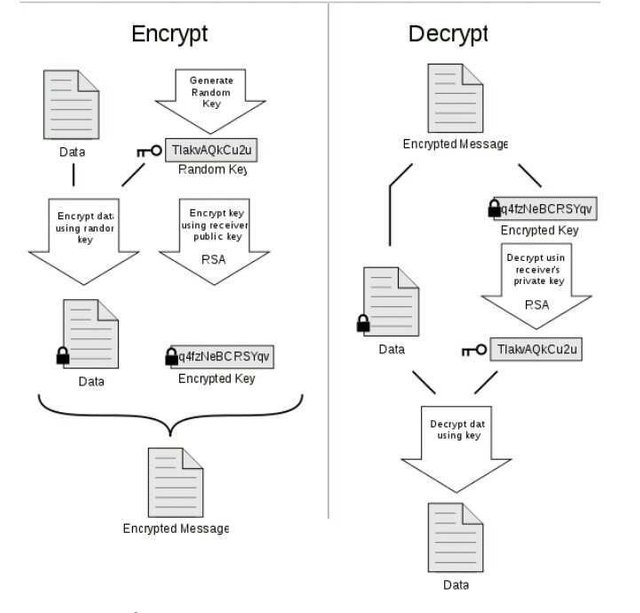
Pretty Good Privacy (PGP) system. Source:Wikimedia - CC BY-SA 3.0.
This has been efficient in preventing a man in the middle attacks, but a knowledgeable hacker could still gain access to these information by hacking either the sender or recipient’s computer and stealing his cryptographic key.
In conclusion…
End to end encryption seems completely safe if the external problems such as hacking, key theft and man in the middle attacks should be solved, but that seems far from it, in fact, as long as these networks are controlled by humans, end to end encryption will be unable to offer a hundred percent privacy.
Even though many communication firms would promise an end to end encryption, there still exists secret means of bypassing normal encryption to gain access to these information, these are known as backdoors and can be employed by the network providers to gain undetectable access to their users' information and activities. Many communication applications such as Skype had been caught in this act as they allowed access to their users' messages to security agencies, and even though they did this for National security reasons, it still represents a severe bridge of privacy agreements. Backdoors even serves more risk than the previous man in the middle attacks and showcases an unsolved problems or human privacy.
In my own opinion, I’d say that a complete human privacy may be an impossible dream, as even if the right privacy technology which would assure that users' activities are not interfered with is invented, the determination of what should actually be kept secret still remains debatable for the security of the environment.
REFERENCES
1.End to end encryption ~Wikipedia
3.When was end to end encryption technology invented? ~quora
If you write STEM (Science, Technology, Engineering, and Mathematics) related posts, consider joining #steemSTEM on steemit chat or discord here. If you are from Nigeria, you may want to include the #stemng tag in your post. You can visit this blog by @stemng for more details. You can also check this blog post by @steemstem here and this guidelines here for help on how to be a member of @steemstem. Please also check this blog post from @steemstem on proper use of images devoid of copyright issues here.

Security both online and offline is super-important given the times that we are in, not just for the military and the protection of social profiles alone, but digital assets as well. I don't think every company out there that promise E2E encryption keep their word. There's the backdoor at times which of course could aid security agencies if terrorism is brought up. Breaches client-consumer privacy policy but maybe the ends justify the means?
I once did an article on Prime numbers and their use in cryptography RSA securities and encryption. They really form the basis for this. who knows, you might find it interesting
It's very hard, cos you can't own a river and accord a fisherman an absolute control over the river, you'd always want to inspect how he surfs your sea, that's a pure picture of the impossibility of end to end encryption and this is inevitable as an unsupervised use of communication gadgets is a huge threat to the general security, if iPhones weren't encrypted, maybe the San Bernardino attack would have been averted if the servers got the Intel on time.
Awesome post over there.
Thanks for stopping by.
This is an instant of a perfect end to end encryption model.
Thanks for letting us know that WhatsApp runs such an encryption model. This I never knew of.
@sciencetech from STEM
It's been about a year whatsapp started running an end to end encryption communication technology on their app, though I can't exactly say how efficient that has been, but I'm sure it hasn't been a bad bait.
Good to know
We cannot escape hacking. Regardless of how strong an encryption security is, it is only a matter of time before hackers get their way in. As we have the CLOSERS so do we have the OPENERS that give whatever it takes to pass through.
Nice post. Lots learnt.
I am @teekingtv and I write STEM.
You know, technology is a home of possibilities, its like a bank of poisons where everyone of them has its own antidote placed beside it. To every security technology is an idea to break through and it only takes time before it comes alive, bad enough.
Thank you so much for stopping by ‘pilot’.
This is a very nice and well constructed write up @joelagbo.
But do you know whether Facebook messenger too has end-to-end encryption?
Thanks.
Not really, because a typical end to end encryption should be automatic, but for facebook messenger, you'd have to turn on a ‘secret conversation’ which is believed to be end to end encrypted, but there's no 100% assurance of this claim.
Thanks, for the clarity.
This post has been voted on by the steemstem curation team and voting trail.
There is more to SteemSTEM than just writing posts, check here for some more tips on being a community member. You can also join our discord here to get to know the rest of the community!
Hi @joelagbo!
Your post was upvoted by utopian.io in cooperation with steemstem - supporting knowledge, innovation and technological advancement on the Steem Blockchain.
Contribute to Open Source with utopian.io
Learn how to contribute on our website and join the new open source economy.
Want to chat? Join the Utopian Community on Discord https://discord.gg/h52nFrV