Blockchain Technology for Kids: Nancy the Node spots a lie

Last time, we saw that nodes are busy gossips, checking up on the truth of what they're hearing from other nodes. In the case of a bitcoin transaction, what the nodes are talking about is whether the bitcoin being traded really belongs to the person trading it.
So it's possible for some of the gossip reaching a node to be a lie. A type of cryptocurrency fraud called a “double spend” can occur. Let's say Jack buys something from Jill, but then tries to buy something from Jennifer with the same bitcoin. In a double spend, Jack no longer owns the bitcoin he's trying to trade with Jennifer. That bitcoin now belongs to Jill. It's the job of the nosey nodes to prevent these double spends by verifying, each and every time, whether or not Jack owns the bitcoin he's trying to spend.

The verification process involves something called the node's “proof of work.” Remember, Nancy the Node is just a computer, and she has to do some calculating to show – to prove – that she's actively trying to make this verification. And part of her proof of work involves figuring out a random number that's been encrypted.
A number, or any other piece of data, is encrypted to disguise it. Here's how basic encryption works: you start with an input number that you're trying to disguise. Our input number will be 9,437 – it's the number we don't want anyone to see. Next, we'll apply a hashing algorithm to our input number: [input number] x 319. If we multiply 9,437 by 319 we get 3,010,403. So 3,010,403 is our hash value and that's the number we allow people to see, hoping they won't guess our input number.
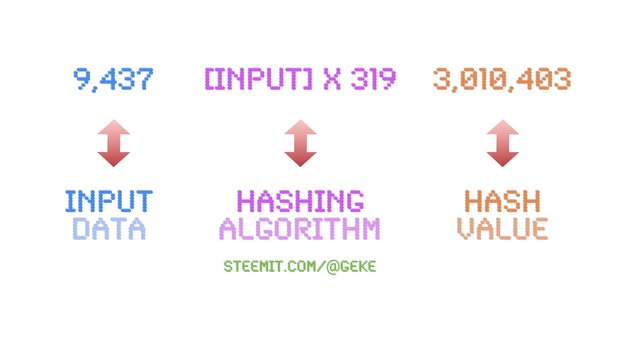
If we're trying to figure out the encrypted input number, we'll take the hash value and try to work backward. It would be very hard for us to figure out that this hash value came from the multiplication of 9,437 by 319. But if we know the hashing algorithm, we can figure out the input number. This is how basic encryption works, although it involves much bigger numbers and much more complicated algorithms.

This process of “hashing” can be used to prove work has been done by the node. In order to figure out the input number, the computer has to make many guesses until it finds the right one. So Nancy the Node will add on this extra input number she's figured out to the verification of Jack's bitcoin transaction.
But what happens when Nancy spots a double spend? She'll verify the first transaction that came through, but not the second. And because this second transaction isn't verified, it won't get added to the blockchain and won't be forwarded on (via gossip) to any other nodes.
I hope that all makes sense! Please let me know any questions in the comments. Next time we'll take a look at the blocks, themselves.

Think you'd like to wash up on our shore?
The treasure map will bring you right to our door!
cover art created with a pixabay.com image ]

Thanks for the easy read. Question though: when we get to the input data and hashing algorithm, those numbers don't have to be clean, right? In your example, you used 9,437 and 319 - but these could be values like 9437.139 and 319.005385235808, right? That would make the system a lot stronger in my opinion and literally infinitely harder to find the original input value. Great post and thanks for sharing!
Oh, absolutely -- just trying to make it uber-simple and clear for kids
really amazing tecnology thanks for sharing
@xonan...... Hehe
@Steemeducation i like it
I must to learn for be better forward
What a fantastic way to explain how the blockchain and nodes work people will definitely be able find this more understandable. Btw is the hashing done manually or not???
It makes perfect sense, the simplicity in explaining is just wow. Loved how you use analogies, Nancy, Jack, Jill and Jennifer, makes the concept even more understandable.
SteemOn!