STEEMIT was DDoS ATTACKED by hackers?
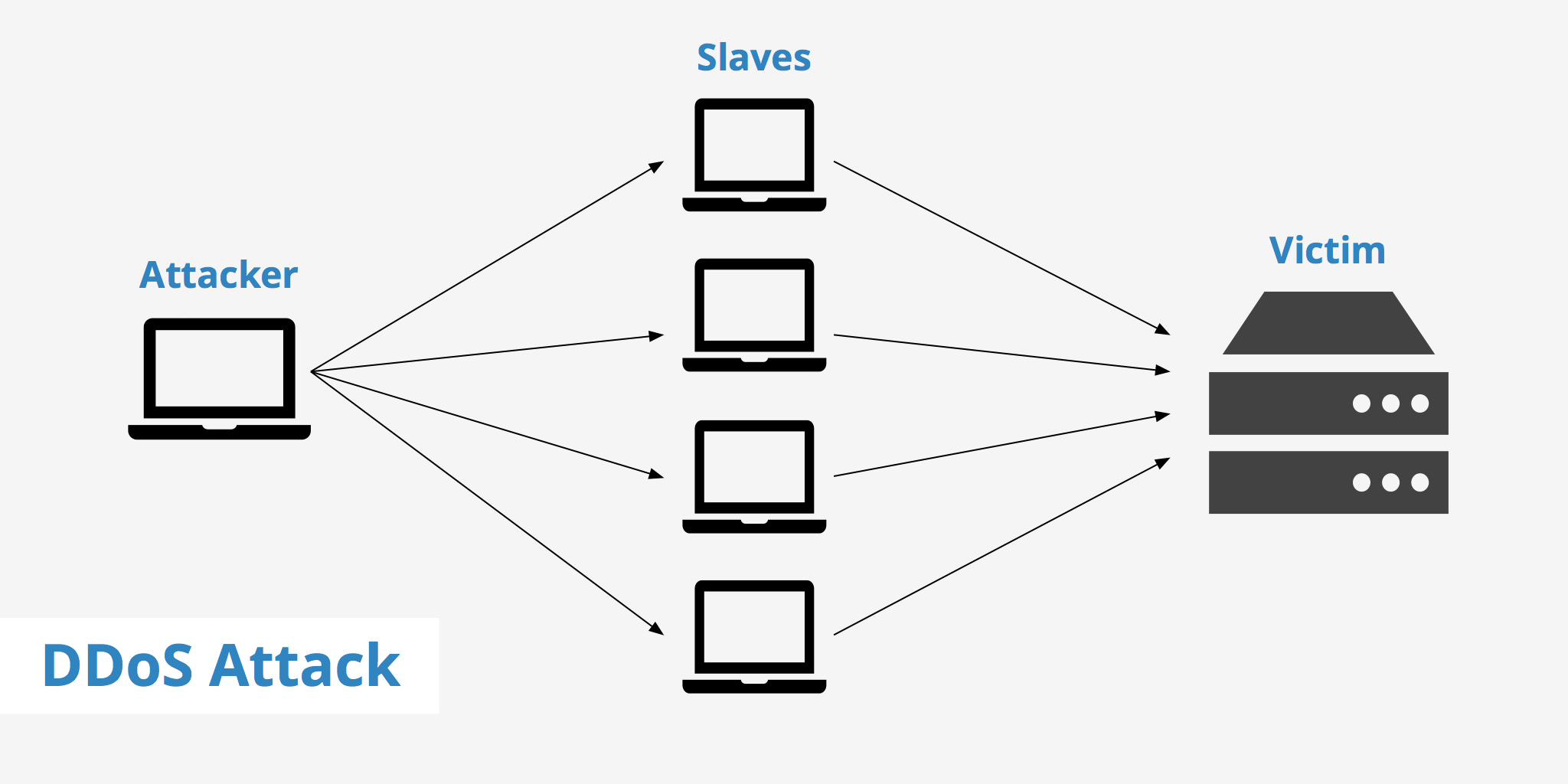
A distributed denial-of-service (DDoS) attack occurs when multiple systems flood the bandwidth or resources of a targeted system, usually one or more web servers. Such an attack is often the result of multiple compromised systems (for example, a botnet) flooding the targeted system with traffic.
How to defence!
In general there are three paths of dealing with DDoS/DoS attacks:
Having enough resources (bandwidth, servers, etc) - not realistic option as attack volume can exceed the bandwidth you have and the cost of having unlimited computation power is huge.
'Renting' Security Service Provider services - a good solution, depends on the specific provider's capabilities. However, you should note that most MSSP work with scrubbing centres in Out-of-Path mode. This means they rely in many cases on traffic analysis protocols, such as NetFlow, to identify the attacks. While this option works swell with DDoS or large volumetric attack, it cannot identify low and slow attacks. You can overcome this limitation if you are ready to make the call yourself to the MSSP once you detect problems with the traffic yourself. Another limitation of "scrubbing centres" approach is that usually only one direction of the traffic is inspected.
Having your own Anti-DoS solution, installed inline. Though sometimes more expensive, this option will provide you the best security as scanning attempts brute-force attempts and many other security threats can be dealt by an inline device. Inline device is effective as long as the attack's volume doesn't exceed your pipe bandwidth. Working in inline mode guarantees detection of low and slow attack, and even intrusions, depends on the equipment you want to use.