DISMANTLING THE FAKES: The Podesta Email About Soros and Voting Machines, The MS-13 "Hit" On Seth Rich, The DOJ Memo Supposedly Proving It and More

Introduction
The Internet has become a jungle of pandering, disinformation, political marketing, manipulation, fear-mongering, war-mongering, misdirection and chaos.
We are swimming through an ocean of lies and I am seeing a lot of people get caught out on issues relating to topics I've been researching over the past 14 months (Guccifer 2.0, the alleged hacking of the DNC, CrowdStrike, etc).
This article is an attempt to clear up some of the confusion and remove the misdirections and distracting chaos that I've become aware of.
This is just a warning from someone who has investigated the relevant topics in detail, has been studying information warfare theory (to try to protect their own investigation efforts from 'gaslighting') and that has retained a friendship with an independent team that have been investigating the murder of Seth Rich in more detail than anyone else throughout that same period, (that team being America First Media Group).
I will try to concentrate on the flawed information itself rather than seek to blame or undermine individuals that may have produced or propagated it (after all, some of them may be getting fed fake intel from a source trying to take advantage of their popularity), but, I apologize in advance if you feel I'm unduly attacking your favorite truth-teller, prophet, luminary or insider. Please keep in mind that I'm only disagreeing with a tiny fraction of what any of them may have told you and trying to explain why that is.
However, I am concerned that intentional information corruption efforts are likely active at present. (They often bombard you with information that is verifiable at first to gain your trust. It is only once they gain trust and build an audience that the distortions and misdirections start being introduced.)
If you've stopped demanding that your 'insider' or 'truth-teller' demonstrate their claims and make a coherent argument (or are accepting evidence that is sourced from them and not verifiable elsewhere), you are likely to be vulnerable to disinformation and may unwittingly propagate it.
Those that want to deceive you and undermine you will often pretend to be on your side - don't let your guard down.
Podesta Email About Soros And Voting Machines
This one was fairly easy to debunk, well, in the minds of those with healthy levels of skepticism, at least. The content being pushed around was supposedly an email from Todd Macklerr to Donna Brazile and John Podesta on March 19, 2016 regarding meeting with George Soros for "pre-programming" of machines:
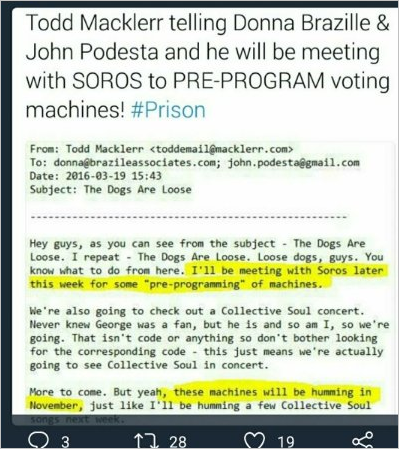
First of all, If you see an email where the date on it falls in line with a batch of leaked emails that were published online it really isn't difficult to check it, yet so many people fail to think or check.
The email above, if genuine, should appear on the WikiLeaks dump of Podesta emails, however, it's nowhere to be found there. The red line in the following image shows where it would have appeared:
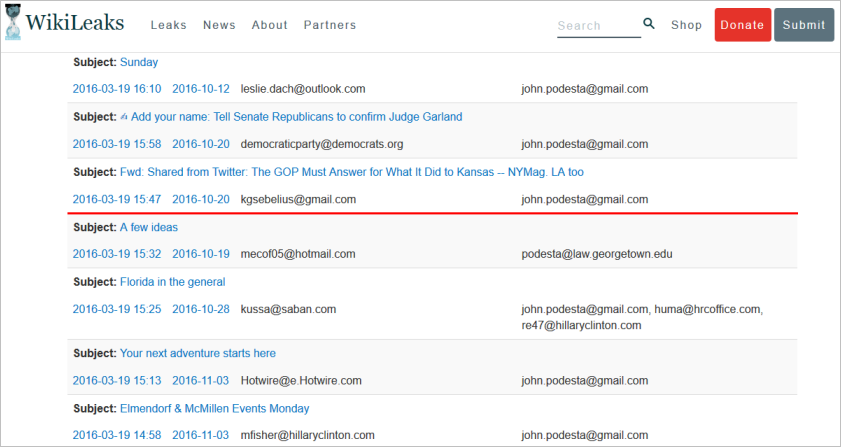
If the email was legitimate, it should have been in that batch as those all came from Podesta's GMail account.
Wasn't It A Deleted Email?
Since highlighting this, I've heard that the source has claimed it was a deleted email that was retrieved. This is also not true even though many seem to have accepted the excuse.
How do I know? - Because they tried too hard and the language gives it away.
The whole "dogs loose" repetitive rhetoric without specificity drums up drama but it's highly unlikely Macklerr would even use this sort of language in his emails.
The statement about meeting Soros for pre-programming machines is absurd, why would Soros get his hands dirty with direct involvement in pre-programming machines? The language here is already unusually conspiratorial and there's dog-whistling to the right-wing going on (if you don't recognize it, it's probably because it's intended for you!).
From that, we jump to an inane sentence referencing what seems far more reasonable to see in an email, regardless of whether there's plausibility to the premise or not.
Then we immediately jump back to conspiratorial rhetoric, "that isn't code or anything", "don't look up the corresponding code" and that's followed by another statement about the machines.
If you believe this, you need to learn to recognize bait and really think through the plausibility of what you're being told and the way you're being told it.
The MS13 "Hit" on Seth Rich
Recently someone on 8-Chan posted something that seemed to hint at MS-13 having ties with Seth Rich's murder and it seems this has evolved into a story about Debbie Wasserman-Shultz hiring MS-13 gang members to carry out the murder. There are several reasons to strongly doubt all aspects of this.
First of all, if Seth Rich was the source of the DNC Leak emails, it is not Wasserman-Shultz that his existence would have posed any sort of threat to, murdering him after the emails were leaked would be pointless.
Those directly involved in an operation to undermine those leaks, however, actually would have a motive for that as Seth, if he was the source for WikiLeaks, would serve to be an operational security threat to the perceived legitimacy of their operation if he spoke out (I am referring to the Guccifer 2.0 operation and those behind it, just to be clear).
US politicians would also be very unlikely to use members of a gang like MS-13 to carry out an execution, there are far more subtle choices that would be opted for long before taking such risks.
Having spoke with Matt Couch and Larry Beech (of America First Media Group), I've been advised that, according to Frank Whalen (Ret. Detective Sergeant, 22 years with NYPD), the murder of Seth Rich does not match up with what would be expected from MS13 gang members executing someone.
(Whalen's sentiment is also supported by other LEOs working with Couch's team, including a Metro SWAT Commander and a reigning Metro PD Officer of the Year.)
In fact, the method of execution coupled with the perpetrators ability to disappear (apparently leaving no evidence behind with which they could be identified) did give rise to speculation, in 2016, that the murderer may have been working in (or had previously worked in) law enforcement.
The basic premise of it being an MS13 "hit" is implausible and the parameters don't really make for a coherent motive except as an incredibly risky form of revenge.
The Fake Department of Justice Memo
Following on from the speculation of the MS-13 "hit", a document that looked like a Department of Justice memorandum emerged, besides the fact it was a blatant red herring (drawing in numerous conspiratorial topics, some of which aren't even directly connected to each other), it's easy to spot as a forgery for a number of reasons.
The following is the memo in question with some annotation from myself to explain why it's a fake:

The language is wrong, use of upper-case characters is wildly inconsistent, it conflates topics for the wrong reasons, it references things that would generally be excluded in such a broad memo, lacks a date and the apparent redaction seems to miss out what would have been deemed sensitive classified intel about sources within the document.
Surviving WTC Collapse Framed As Suspicious
Watch out for anything framing survival of the WTC collapse as suspicious.
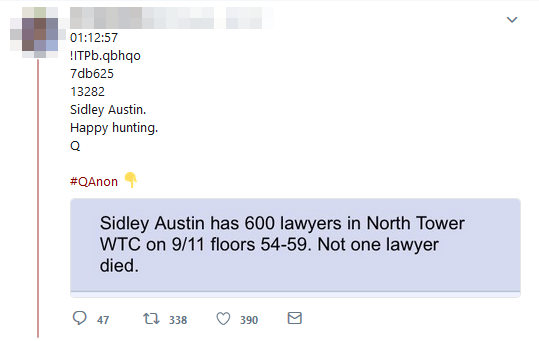
If it's about an entity on or above the floors of impact, fair enough, but if it's below those floors, even if an entire company's staff surviving, especially in WTC-1 - is not quite as strange as it probably seems.
Accounting for both buildings combined, for all floors below the impact sites, there was a 99% success in evacuating.
Helping Sidley Austin's staff survival rate was the fact that, although WTC-1 (North Tower) was the first hit, it remained standing longer than WTC-2 - so they had more time to evacuate.
The impact in WTC-1 was between floors 92-98, so Sidley Austin's offices were already a third of the way down from where the impact had occured.
High staff survival rates relating to businesses below the points of impact is not unusual.
Separating CrowdStrike, Stonetear & BleachBit
Recently someone did an interview and in it they implied that CrowdStrike had bleachbitted Hillary's emails.
The only time I've actually seen BleachBit mentioned in relation to any of the scandals surrounding the US general election was actually in relation to someone called Paul Combetta who was working for Hillary Clinton and had made inquiries on Reddit about how to delete emails.
Combetta, who's online handle was "Stonetear", was given immunity according to reports in September 2016.
In contrast, I'm not sure that conflating CrowdStrike and BleachBit is actually supported by anything on public record and suspect that this may have just been a mistake.
Don't Unduly Conflate: The Awans, Guccifer 2.0 & WikiLeaks
In 14 months of investigating Guccifer 2.0 I have found no credible connection between:
Guccifer 2.0 and the Awans.
Guccifer 2.0 and WikiLeaks.
The Awans and WikiLeaks.
...and if there is a relationship between Guccifer 2.0 and Seth Rich, it's certainly not the one described by Guccifer 2.0 in the conversation had with Robbin Young.
Also, anything referencing transfer rates between 22Mbps and 38Mbps, local transfers being demonstrated, etc. solely relates to Guccifer 2.0 and the NGP-VAN archive.
These transfer rates and the indication of a USB device being used are completely separate from anyone sending files to WikiLeaks.
Information Warfare - Further Reading
If you are interested in learning about information warfare theory and tackling deception/disinformation, please check out the following (for the links to Google Books - even just the previews provide some interesting and useful information):
Considerations on Deception Techniques Used in Political and Product Marketing
Classical Deception Techniques and Perception Management vs. the Four Strategies of Information Warfare
How To Detect Propaganda
JTRIG Manipulation Techniques
The Weaponization of Social Media
Deceptive Mimicry In Humans
12 Methods of Propagandists and more
The Interplay of Illusion and Deception
Deception: Essays from the Outis Project on Deception
Detecting Deception: Current Challenges and Cognitive Approaches
Behold a Pale Farce: Cyberwar, Threat Inflation, & the Malware Industrial Complex
Deception in the Digital Age: Exploiting and Defending Human Targets Through Computer-Mediated Communication
Social Media Warfare Equal Weapons For All
Cyber Denial, Deception and Counter Deception: A Framework for Supporting Cyber Defense
Outstanding article @adamcarter! Very informative on some disinformation floating around, most of which I wasn't even aware of yet. I really enjoyed looking through the links you provided too, thanks for the excellent resources. 👊
Thank you Adam, I love your in depth articles. Truth is far more convincing that a lie.
Highly rEsteemed!
Thanks so much! There is too much disinformation on all sides.
I've also read a story in one of the those "Breaking news"-Magazines about a wikileaks E-Mail "Hilary confirmed alien contact". It was easy to find the REAL E-Mail which was much longer and she just was joking about such conspiracy theory they found in the internet.
Very informative discussion of the disinfo we've been having to parse. I appreciate you're investigation and revelation of the details that can help us to focus on stories that have potential to be more productive.
Thanks!
Great article - good thoughtful info. I'd like to see more about the Awans and their control over massive amounts of data! You are spot on concerning the graphic errors in the fakeDOJ memo - prob CIA hit anyways. Thanks for the insight!
I would like to see more about the Awans too - been following George Webb for quite a long time.
So very useful! Truth advocates care that the facts make sense. Thanks Adam!
Hi Adam - great information here. I'm fairly new to this platform, and I usually write with a spiritual tone about what's going on in the world. Also happy to find some people to follow in your comments - so COOL - here's one of my related articles about the age of Spin - https://steemit.com/transformation/@talk2momz/the-age-of-spin