Why recent data breaches where so successful +200 million accounts !
Why recent data breaches where so successful
We all use the internet nowadays, the internet of things is already here. Computers are everywhere; cars, watches, camera's, refrigerators and so forth. This means that there are the potential risks of getting hacked, all code written by humans can contain one or several flaws. Those eventually will get discovered in a matter of time (it's a ticking time bomb). Think about it, you are updating your computer system and you assume it's safe because it's fully updated doesn't actually mean it's "safe". It is a matter of how you make use of it, and if you continue to update software, which eventually will make your system slower, even through your computer system is clean and running Anti-virus/Intrusion detection security system. Look at Wirth's law.
Wirth's law is a computing adage which states that software is getting slower more rapidly than hardware becomes faster.
So, our transistors aren't really aging over time this badly. Software gets updated, extended so much so often that all those more cpu cycles make your system slower. But then again not really "safer", right? New features added to your OS/ Software can lead to a new undiscovered flaw, that may can get abused eventually overtime when hackers or researchers find out about it (honeypots, payload analyzing kernel hooked sandboxes/virtual machines).
That all comes down to two points
- Is it corruption, do companies add vulnerabilities / bug-doors in software / or spread viruses themselves to help the AV scene (convince people to buy AV software)
- Code reviews may be more efficient than testing (Researchers and practitioners have repeatedly shown the effectiveness of various types of reviewing process in finding bugs and security issues).
Vulnerabilities and default settings
Do you remember Heartbleed bug in the popular OpenSSL cryptographic software library ?
This was a disaster was it, or not?
Obviously it was not really, if we look at recent big hacks, be honest. So that confirms that the bug was either already percent and known by the cyber security of government used to spy on corporations and individuals hosting C&C's to do financial damage. Anyhow Linus's Law wasn't in place here like mentioned before. Such critical used libraries in software used on the net should be getting reviewed and tested much better, in feature releases!
Trust is a really important thing in the cyber environment. I don't have to convince you. Think about this example case below.
Would you ever 'drive' a fully automated Tesla alike car that has no steering wheel, that is controlled by a computer which you don't know it's code of". I think the answer for the audience is mostly no. If it's yes, well, congratulations on taking such a huge risk in trusting people who develop this technology. I think you might get the point, there's always a steering wheel in place and other controls. Because the system isn't perfect and will never be perfect and may contain flaws and can cause accidents (some day)..
Installing and using software or hardware containing software code is a risk you take, you trust the manufacturer of the brand. All you can do is take the right precautions and place a firewall or server in front of it with strict rules sets.
There's CRS that are free to get and maintained by the security community from OWASP. If this isn't good enough you could also go for a paid CRS for as low as 30 bucks for a WAF or other application that fits your needs (maybe DPI). So why not, it's worth the effort. I see so many cases these days of people who "manage" vhosts/hosts with Wordpress/Joomla/Drupal/etc that get hijacked because they install random extensions without thinking of the risks it can bring with it. What they don't know is that code isn't reviewed by someone and/or that the author of the extension might have became a victim of a hack, in which case the hacker which hacked the extension author's website have added malicious code to the extension. The extension now not only adds the features you want to your server but also the features the hacker wants you to install. Your server now becomes a zombie listening for commands from the C&C server(s) or your blog/website becomes a credit-card phishers, mail bomber or flooder..
All kinds of embedded devices become zombie overtime
CCTV camera's connected directly to the net which still use the same default password admin:admin, or with upnp 1.0..
Modems from providers which aren't receiving firmware updates anymore, Firewalls with flawed firmware, NAS drives, print servers those eventually all join a botnet or surface up on Shodan ready to be abused. You name it, they all eventually have a flaw sooner or later.
To me it looks like if nobody cares, even a old friend of mine. They don't care, that's really what's happening.
Providers often also don't care, they only see money signs, I once found a full cross-site scripting vulnerability on my providers fora cms . I reported several other security flaws that were located in my modems firmware to them, and all they did was just fix the xss and ignore me, while I could have done in the worst case is hijack the administrators account and dump the entire fora database (I didn't do that obviously).
The value of a hacked system
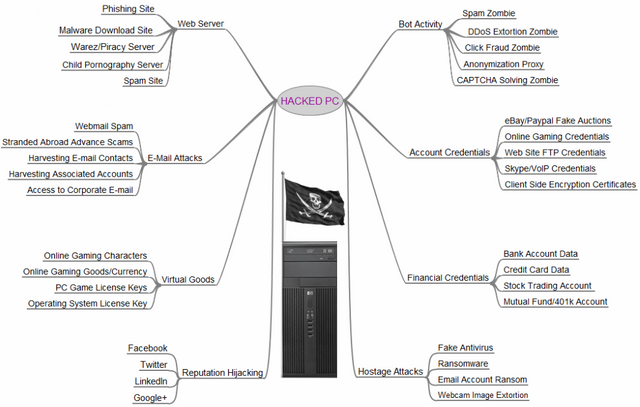
Happening all the time is hackers trying to find out a way to get your password to abuse it in a way they could make a profit out of it or by selling it to other hackers in the darkweb scene or either a website serving the clearweb like Darkode (To clarify things, Darkode is offline for a longer period of time).
The criminals are either selling it, re-using the passwords that are gathered in a data breach to gain more stolen information a nice example for this is to look at the recent MySpace breach and TeamViewer hack. They both have a connection, which you can read in news articles online.
Most companies hire security specialists to keep all software, front-end and back-end stuff up to date. Those security specialized teams also make monthly or weekly reports of the IDS/IDPS systems that are in place or do manual 'pen tests'. Those are the man in black suites, that wear white hats and just do their job under working hours throughout the carrier within the field / company they are deployed in.
The issue is existing in one simple factor.
- We trust too many sources/resources and assume it's all OK.
Resulting in a breach, and another breach followed after the first. People are not learning that the companies can't do anything about the major security issues, since making it all much better secured would take away user friendly, ease of use and makes applications less features rich compared to other software competitors. Think about two factor authentication, stronger passwords, special web-plugins (compatibility of these plugins aren't cross-platform supported and don't work on OSX/Unix, but only on Microsoft or otherwise).
Also often even big corporations still have a fake sense of security and use plain-text passwords behind the screens.
Thinking that even with all precautions and security measures will prevent it from getting hacked. This is a really bad idea to do because nothing is perfect. There's so much potential error in code (firmware, software, ...), humans and whatever is in front of this system that the risk factor rises again, thus making a fake sense of security, again.
First lesson of cyber security education was to strip down a system to the bare minimal of what you need. This means that you disable unused services that are internet facing, and also if you are unsure of other applications running on that machines, like functions that COULD be used in ASP/PHP that are unused, disable them.. We do this to minimize the attack vector for attackers.
Ensuring security shouldn't be this difficult. By putting in place better cryptography algorithms to store passwords in the first place (so if a breach happens it takes some time for the attacker to recover passwords), secondly by NEVER.. sending plain text passwords to someones mailbox (sign).. Thirdly use complex passwords or moderate passwords that fit in your memory, not your hard-disk and if you're this lazy either make a encrypted container on your personal computer/phone and store your 40+ char passwords right there. Never re-use or use obvious passwords in the first place (common sense).
I can partly agree on John mcafee's press about San Bernardino phone (Apple NSA case)..
Cyberscience is not just something you can learn. It is an innate talent. The Juilliard School of Music cannot create a Mozart. A Mozart or a Bach, much like our modern hacking community, is genetically created. A room full of Stanford computer science graduates cannot compete with a true hacker without even a high-school education.
That obviously is also why companies fail to "protect" your data or it was either not being used carefully enough.
It is the way everything is designed. Also the amount of trust people have.
Oh no I won't get any Viruses/Trojans (says educated computer technician), several years later I receive spam emails from him. Alright I do understand that we probably all have a email address that's in a public or unannounced data breach right now. But this one was obviously from a bot looking at the source headers.. They should learn kids at school how to properly use a computer without getting fooled by a fake sense of security aka a AV which is a cat and mouse game (one day malware will make its way to your system, still being undetected, and you're f**ked over anyways) Whatever you did, watching a illegal movie on a website full of ads and malicious JavaScript or one serving you a nice exploit-kit. You can simply not rely on AV system only.
Bonus security advice
Steps you can take to get more privacy and security. It's really basic keep this in mind, I would say add Microsoft's enhanced mitigation experience toolkit (EMET) too if you're still paranoid. Also running Qihoo360 wsus front-end (for Win users) isn't bad either or Microsoft baseline security analyzer (MBSA) to patch up your system.
- A NDIS filter on your main NIC that's internet facing with a nice blocklist on it (Bluetack/Squidblacklist/I-Blocklist)
- Grab a decent proxy/tunnel vpn service, or setup your own one on a droplet/vds (openvpn-as offers 2 concurrent free users, or you could easily hack the pyd by swapping it with a py file which returns the amount of lics YOU want the ZWT way..)
- Disable all plugins in your browser and install something like Policeman/Noscript/Aosll, work with a hypervisor with a feature such as "unity mode" to open files such as office files, and such. (PS I don't think someones will do the effort to hyper jack your hypervizer anyway.. or he/she is really boring)
- Maybe if you want to sacrifice your privacy, Comodo IDS or similar Anti-virus software for your OS.
I hope you enjoyed reading. Sorry if my English isn't the level you wished for.
Peace out -
@Unkn0wnn
Nice @unkn0wnn
Shot you an Upvote :)
Keep up the great work @unkn0wnn
Upvoted