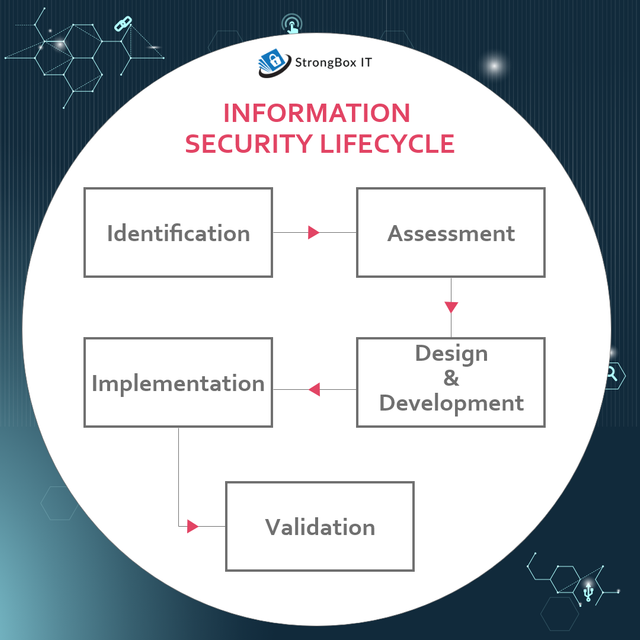
Information security lifecycle
Information security lifecycle is a methodology that ensures a continuous, progressive and evolutionary journey within a firm's information security core principles.
Identification
Identification starts with mapping the network you're working on. This helps your security team understand the assets within a system and how they are related. They also help understand the resources currently available for information security protocols.
Assessment
Security professionals look into points outlined during the identification process and collect more information for possible vulnerabilities by top to bottom approach or looking for flags.
Design & Development
Countermeasures or defence mechanisms are built after considering factors like security layering, local and industry compliances, business continuity in case of an attack, potential areas of effect and lastly the effectiveness of the process chosen.
Implementation
After the final design, it's time for implementation. This involves establishing a change plan, assigning team roles, requesting resources, testing and finally implementing the changes.
Validation
The goal of the validation process ensures that the security of the setup matches your established security policies and standards. This phase may involve repeating the design and implementation stages to correct errors or target areas missed.
looking to secure your information system
click https://www.strongboxit.com/services/