Always wanted to protect your private information? Then start from learning basics of cryptography!
Encryption - the most important mean of security ensuring. The encryption mechanisms help to protect the confidentiality and integrity of information, to identify the source of the information. However, the encryption itself is not a solution for all problems. It is only a delaying action. It is obvious that any encryption system can be hacked.

Basic encryption concepts
Encryption - is hiding information from unauthorized persons providing access to authorized users. Members are called authorized if they have the appropriate key to decrypt the information.
The goal of any encryption system is to maximize the complexity of access to information by unauthorized persons even if they have the cipher text and know the algorithm that is used for encryption.
Encryption provides three security conditions of information:
Confidentiality - is used for hiding information from unauthorized users during the period of transmission or storage.
Integrity - is used for preventing some information changes during the period of transmission or storage.
Identifiability - is used for authenticating of the information source.
Attacks on the encryption system:
- through weaknesses in the algorithm;
- an attack on the key by "brute force" (manual key selection);
- through a vulnerability in the system environment.
There are two basic types of encryption: a secret key and a public key.
Encryption with a secret key
Secret-key encryption provides confidentiality of the information in an encrypted state. Only those who know the key can decrypt the message.
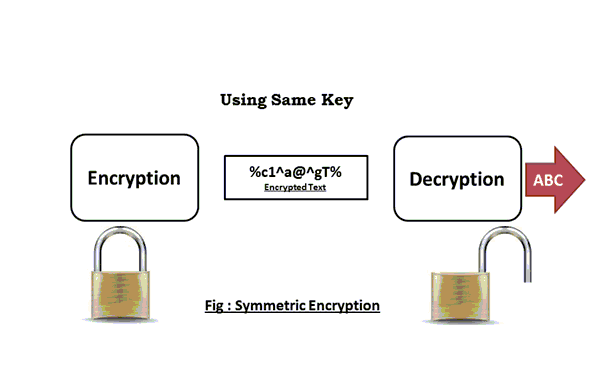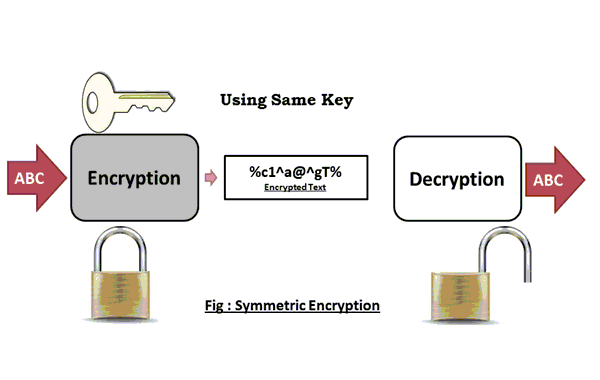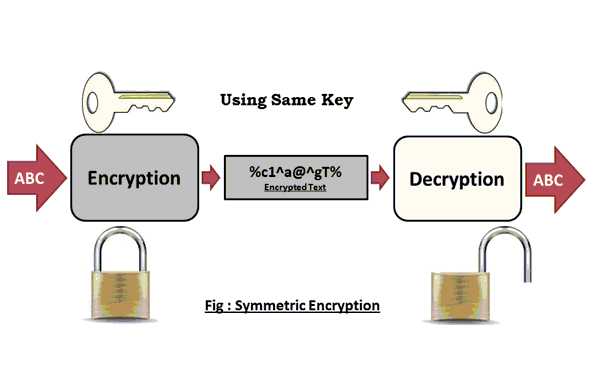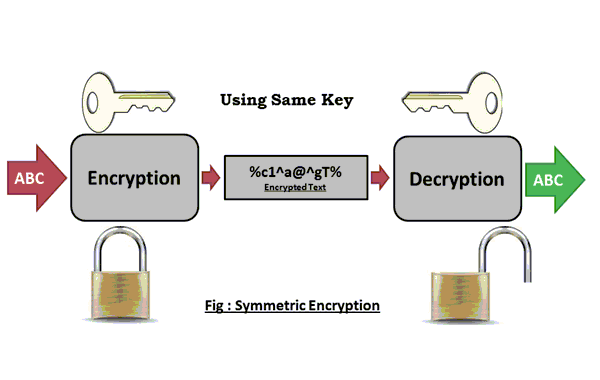
There are a lot of types of secret key encryption:
Substitutional cipher
Substitutional cipher processes single letter of the plaintext at one time. The message can be read by both users with the same permutation scheme. Key in the substitutional cipher is a shift of letters, either a completely reordered alphabet.
One-time Pad
The only theoretically uncrackable encryption system, which is a list of numbers in a random order, used to encode the message. OTP can be used only once.
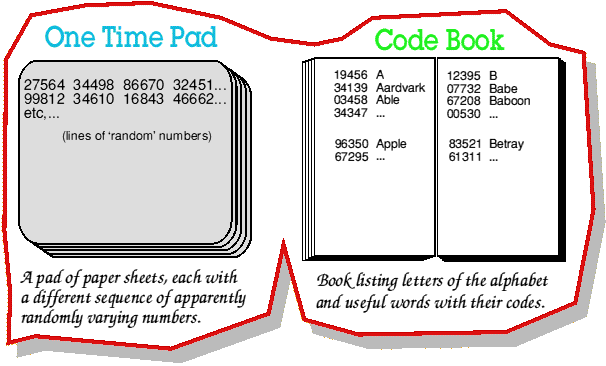
Disposable pads are used in IT environments with a very high level of security (but only for short messages).
Data Encryption Standard (DES)
DES uses a key with a length of 56 bits. It uses 7 bits of a byte, eight bits of each byte is used for parity. DES is a block encryption algorithm that processes 64-bit block of plaintext at the same time. 16 cycles with a different subkey in each of the cycle are performed in the DES algorithm of encryption. The key is exposed to its own algorithm for the formation of 16 subkeys.
All these algorithms are typically powerful enough to be used for general purposes.
Public-key encryption
Public key encryption - the most widely used encryption method, because it ensures the confidentiality of information and information remains unchanged during the transmission.
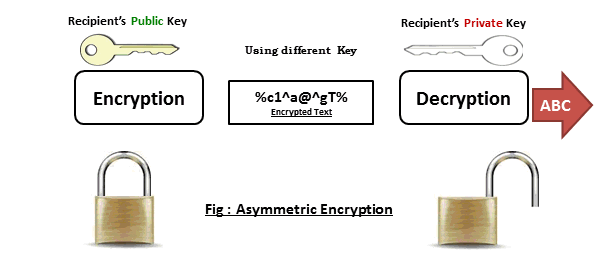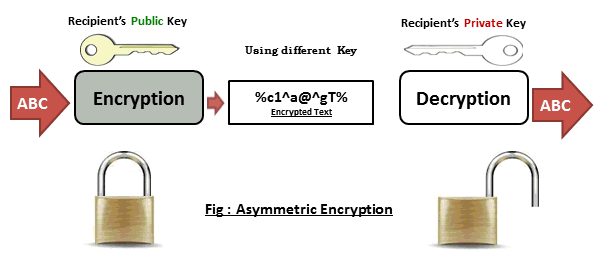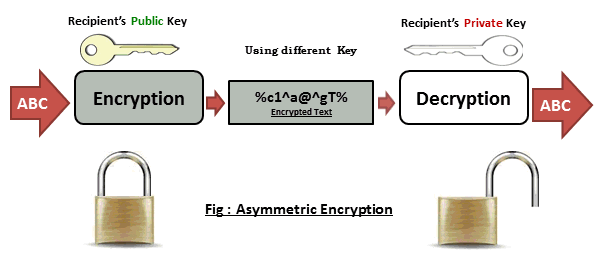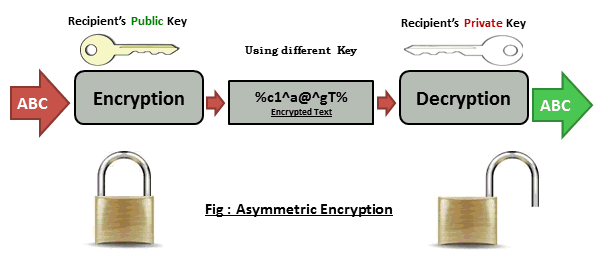
Both users (sender and recipient) must have the key. Keys are associated with each other (so they are called a key pair), but they are different. If the message is encrypted with the key K1, then the message can be decrypted only by using a key K2. And vice versa. Thus one is called the secret key, and the other - open.
The private key is kept secret by the owner of the keys.
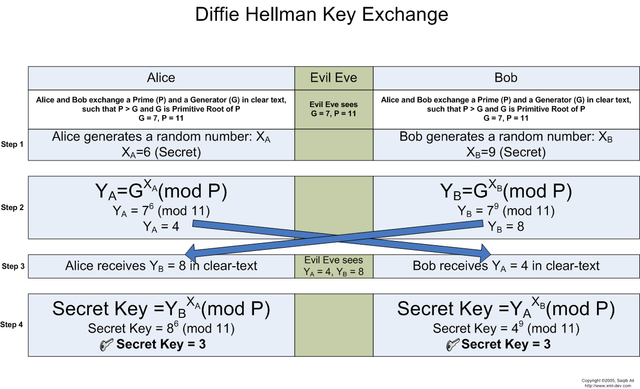
Key exchange algorithm of Diffie-Hellman
Whitfield Diffie (Whitfield Diffie) and Martin Hellman (Martin Hellman) developed a public key encryption system in 1976. The system of Diffie-Hellman (Diffie-Hellman) was designed to cope with the problem of key distribution with the help of encryption systems with secret keys. The idea was to use a secure method of matching private key without transmitting the key in any other way.
- Two subscribers (P1 and P2) pick an encryption key for a stable connection with each other.
- P1 and P2 use two big integers a and b, and 1 <a <b.
- P1 picks a random i number and calculates I = ai mod b, and transmits the subscriber I P2.
- P2 j selects a random number and calculates J = aj mod b, and transmits J to the subscriber P1.
- P1 calculates k1 = Ji mod b.
- P2 calculates k2 = Ij mod b.
- We have k1 = k2 = ai * j mod b.
So we see that k1 and k2 are the secret keys, intended for use in the transmission of other data.
And also another example:
Encryption using elliptic curves
Encryption using elliptic curves: there are two points A and B on an elliptic curve so that A = kB, it is very difficult to determine an integer k. The biggest advantage is that the keys have a smaller length (because of the complexity of the problem), causing faster calculations that are performed while maintaining security.
Digital signatures
Digital signatures - a form of encryption that provides authentication. The popularity of digital signatures is constantly growing, and they were advertised as a way to move to full electronic information environment.
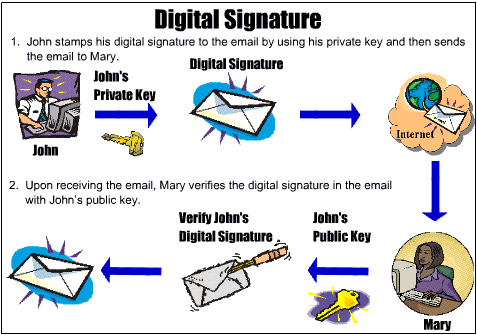
The information is processed by analyzing messages or using a hash. A hash function creates a checksum of data, which is then encrypted using the private key of the user and transmitted to the recipient of information. After receiving the information the same hash function is processed. The recipient decrypts the checksum received with the message and compares two checksums. Matching of checksums means that the information has not been changed.
It's obvious that I haven't told you everything about encrypting, as there are a lot of other interesting algorithms like International Data Encryption Algorithm, RC5, Skipjack, Blowfish, Twofish, CAST-128, Taher Elgamal algorithm, Rivest-Shamir-Adleman algorithm and a lot of others; there are a lot of different methods of their use and this is just the beginning of the list of things that I want to tell you next time!
If you enjoyed reading this article, then follow me and you will learn a lot of new scientific and technical stuff.
Alex aka @phenom
thanks for sharing
@techguru, I'm glad technical guru gave a look at my article)
Stay tuned
Wow thanks for sharing a detailed post. I think it is important for us to learn. Even someone who doesn't know computers.
Sure, everyone who uses a computer should know basics of cyber security.
Thanks for the feedback. Appreciate it
I was needing this thanks!
Cool! Follow me and you'll learn much more)
Good article. I'd add some info about OpenPGP standard and its implementations though.
good idea. Probably will tell about it in more details in a separate post
Very nice article! Easy to read, to follow! Thanks for sharing!
I think this is also the first time I notice your first name ^^
thanks for your feedback. Stay tuned to keep learning)
(well this time I learned a bit :p)