A brief rant on password security [Edit: Not so brief after all]
I decided to give the Dashlane password manager a shot. I've been happy with my current password manager, Passpack for several years, but a friend recommended Dashlane, so I thought I'd give them a quick try, see if it was worth switching.
So I set about creating my account on Dashlane, and step one was to enter my email and password. This is a password manager, so I won't use the usual crappy passwords that I might use to quickly post a comment on XYZ blog; I'll use one that won't cave easily.
When I want such a password, I try to construct random nonsense sentences, like Young thieves are edified by discovering the locks in the iron web. I came up with that one by looking at the stuff scattered across my desk and assembling random words and phrases into a sentence. I would bet money that, properly stored, that password will never be cracked in a password database dump. If the NSA decided to target that password in particular and dedicate a datacenter to it, OK, it might go down, but that's not what I'm trying to protect against. And I predict that password would put up a mighty fight before succumbing anyways.
The point of such a password is length and unpredictability. I would use such a password when I don't expect to type it very often, but I care a great deal about what it's protecting, and I want to make sure I won't forget it. This is important with password managers, because the good ones won't give you any recourse if you forget your password. They can't. If they can, that means that your password doesn't prevent them from accessing your data, and in the case of a password manager, that's unacceptable.
So I tried to create my account using a highly secure and easily memorable sentence-style password. Dashlane rejected my password, because it didn't have a number in it.
![]()
Let me remind you, Dashlane is a password manager. Do you expect a password manager to understand password security? Maybe? Just a little bit? So congratulations, Dashlane, you get another one:

Now, there's a lot of conflicting information out there on what makes for a good password. As with almost everything, most of the advice out there is really terrible. To most readers, it isn't immediately obvious why Dashlane deserves three facepalms here, but I hold a password manager company like Dashlane to a higher standard: I expect them to already be intimately familiar with the discussion.
For the rest of us, who haven't started a company whose purpose is helping people pick strong passwords, here's an XKCD comic that examines the issue of password quality:
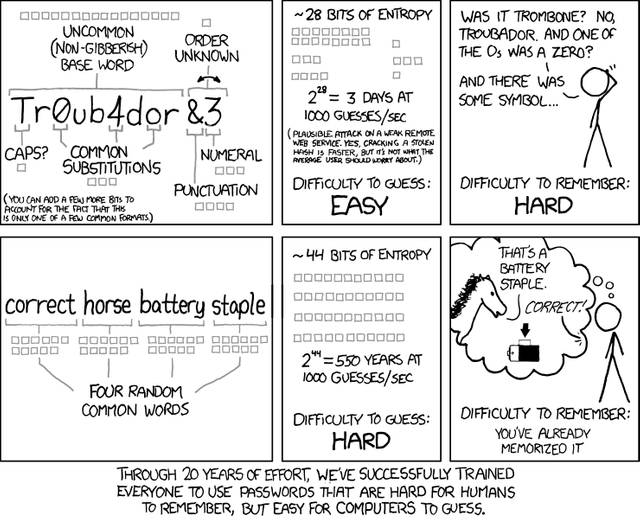
I realize that XKCD is kinda technical, so I especially want to stress the summary at the bottom: requiring people check silly little boxes like "Password has a number" and "Password has a punctuation symbol" trains people to pick passwords that are easy to crack, but hard to remember.
A password manager company should know this, and should promote good password choice, perhaps even providing some educational blurbs about how to pick strong, memorable passwords. But Dashlane rejected my extremely strong password, and cited The Handbook of Picking Guessable Passwords that You Won't Remember.
Now, this is not an in-depth review and analysis of Dashlane, and I don't doubt that from a strictly technical perspective, their password manager is quite sturdy. But security as a whole is about the details. Details like human psychology, and how people interact with an app. And Dashlane seriously missed the mark on this one.
I'll be sticking with Passpack for now, as they've always quite happily let me use a strong and memorable password.
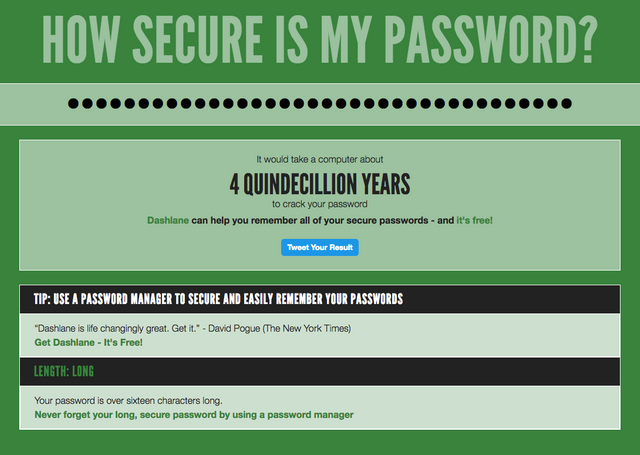
Oh, and one more tidbit: Dashlane sponsors How Secure is My Password?, a site which helps you check the security of your password by estimating how long it would hold up under cracking on a low-powered, consumer-grade computer.
Here's how it ranks a password which passes their checkboxes with flying colors: icy!v1trEol

400 years is a horrible score. That password would fall in minutes or seconds on a professional password cracking rig.
Compare with a simplified version of my example password above: Thieves are edified by the iron web.
This is a phenomenon I like to refer to as "Missing your own point."
Also be sure and check out PassFault, which is my favorite password strength meter. It's not as pretty or slick as HSIMP, but I think it gives a little bit better analysis, and also breaks down why it scored you how it did so you can tweak and optimize your passwords for maximum durability.
Thanks for reading!

With a background in software development and a passion for security, Nathan has identified blockchain technology as his niche. He is dedicated to creating applications which empower individuals to shape a better world for themselves and others.
Important point! I think the reason we're often encouraged you to use a combination of numbers, letters in both cases and those other characters, is because then they can prove to attackers, each character of one of our passwords have many more possibilities. So maybe there's the assumption that if not forced, people will probably just use lowercase letters 😂
But you're absolutely right, it would be better to force long passwords, they scale like crazy. Tell all and shout from the rooftops, I'm resteeming 👍
True, but the irony is that requiring certain character classes reduces entropy. If there are no restrictions, there's a lot more possible passwords than if there are restrictions, and to a bruteforcing algorithm, it's really handy to be able to skip checking all passwords which don't have at least one of each character class.
Even more importantly, when you require people to have all of those character classes, they overwhelmingly pick one of just a few common password formats (as mentioned in the comic, first pane, bottom left).
More restrictions just makes my job as a cracker easier, not harder, because it gives me more information about your password.
That's true, I mean there's always going to be some restriction by the fact of a character necessarily belonging to a set, but I get what you mean. And good point about giving more information, I hadn't thought of that. 🤠 ➡️🎩
Having used pwSafe for many years I recently switched to Dashlane. I find it to be a sound replacement for pwSafe and it does let you put in memorable and long passwords - just need the little extras as you mentioned.
I would recommend Dashlane to most people.
Thanks for the good article.
The trouble with Dashlane is that they are implementing a policy which (1) makes passwords harder to remember, which is insecure, and (2) are promoting a password security anti-pattern, namely, that adding more character types for the sake of adding more character types makes your password more secure. It doesn't; both in theory and in practice, it makes the password strictly less secure.
It's theoretically less secure because by bounding out possible passwords, you guarantee to attackers that they don't have to try guessing several entire classes of password.
It's practically less secure because it funnels the vast majority of people into just a few different common password formats which check all the boxes, and are easy to remember, but also happen to be easy to guess.
I have just replaced all off my passwords with correct horse battery staple , thx!
Me too! Thanks for the password tip, ima tell me friends to also use it
Thanks for sharing
I'l going to up my security because of you
You missed ond problem more. Dashline's website is not SSL from the beginning. So if there is a man in the middle attack attempt, they can intercept the html and convert https urls with http urls. The SSL tunnel connects the attacker to dashlane and there is no SSL tunel between you and the attacker. The new password for Dashlane would be sent in the clear to the attacker. So Dashline gets four facepalms in my opinion.
Hmm, I'm not sure what you're seeing, but requesting any page from Dashlane's website over HTTP returns a 301 redirect to the HTTPS version, and they have HSTS enabled so your browser will not trust content from that domain over HTTP again. That's pretty much best practice all around.
They don't have HPKP, but I don't blame them: that makes you unable to adapt if your CA goes rogue or goes under. HPKP is generally too risky unless you run your own CA.
I am using chrome and it shows https crossed out. Navigate to https://dashlane.com/ in chrome (no www) and see what I mean. Actually its a cert problem. I stand corrected.
Ahh, yes. That's a misconfiguration on their part; looks like the raw domain, without the www, is configured to point to their mailserver, so [email protected] will work correctly (poorly done, should've had the A record point to the website and the MX record point to the mailserver), so if you manually type https://dashlane.com, it breaks.
That is badly insecure, because it means they don't have HSTS on dashlane.com, only on www.dashlane.com, meaning I could sslstrip them as you described, and the address bar would read dashlane.com instead of www.dashlane.com.
Mine's so secure Steemit won't even let me use it!
Yeah, Steemit likes to generate passwords for you so it can guarantee a full 256 bits of entropy. I don't use a password on Steemit at all; I just use the private keys directly (which the web interface supports quite nicely)
I don't understand any of that, I'm not a computer guy...maybe some penicillin would help with that entropy. I just stay logged in. But I'm sure if I wanted some of my money, I'd be fucked!
Ahh, my bad. It's fairly technical, but there are pretty good reasons for it. Essentially, Steemit guarantees that you get the maximum theoretical security in your password. It's a tad annoying, but it's quite secure!
Mine's so secure they won't even let me use it!
Wait, so the password Steemit.com gave you doesn't work?
Yep...I tried to change passwords and they ask for the password Steemit gave me. So when I try to enter it is says invalid password
Hmm, odd. What OS are you on? (Mac or Windows?)
windows 7
OK, well I guess you're working with it for now, but if you ever have trouble (say, getting the money out, etc), and you can't get help from Steemit directly, I may be able to help you figure something out. :)
I just stay logged in all the time
Also check out LastPass and 1Password.
LastPass has consistently failed to impress me. It's better than not using any password manager, but to me it seems they consistently prioritize shiny-new-feature over security.
1Password seems decent enough, but I don't have much experience with it.
I think 1Password is my favorite... they have a great UX. I like them both because I can integrate them with my 2FA provider. :)
I just noticed who you are. Hey, how's it going? :) I love the avatar, it looks just like you!
Thanks Nathan! I randomly found this avatar in Duo's marketing resources and "commandeered" it. It's going really well for me, I'm actually starting a move today (to another place in Detroit), so I've been pretty busy.
How are you doing bud? Are you still working on FMV?
I'm doing well. Living in St. Louis right now, but I'll be moving in a month or so. :)
Want to catch up somewhere a bit more convenient? I'm @nn on Wire or @modprobe on steemit.chat