CLOUD AND CLOUD SECURITY
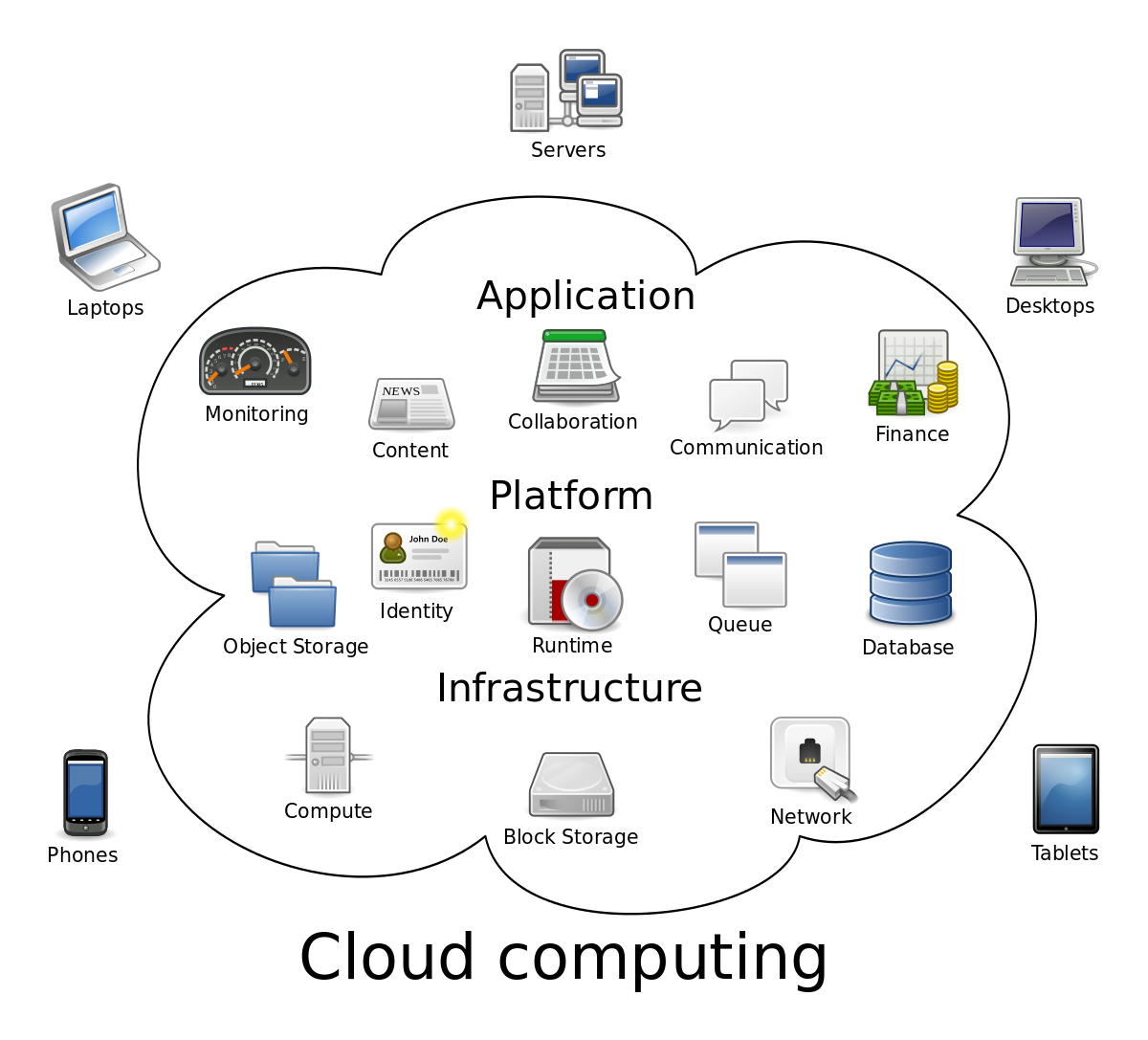
Cloud Computing can be classified as a new paradigm for dynamic provisioning computer services supported by data centres that usually employ virtual machine (VM) technology for consolidation. Cloud computing provides infrastructure, platform and software as services that is available to the consumer under the pay as you use model. The customers using a particular cloud, can access the resources provided by a cloud provider, according to the Service Level Agreement (SLA) given by the same cloud provider. In distributed data centres, the technology named virtualization is being used by the clouds to provide the resources to the customer whenever required. Clouds are provided to the customers for giving them three models: Software-as-a-Service (SaaS), Platform-as-a-Service (PaaS), and Infrastructure-as-a-Service (IaaS). Cloud Computing has widely been adopted by the industry or organization though there are many existing issues like Load Balancing, Virtual Machine Consolidation, Energy Management, etc. which have not been fully implemented. Central to these issues is the issue of load balancing, that is required to distribute the excess dynamic local workload equally to all the nodes in the whole Cloud to achieve a high user satisfaction
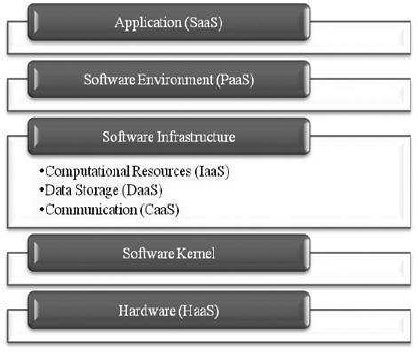
Layers: Cloud Computing architecture has the below given abstract layers which begins from bottom and works upwards. The attached image can be referred for the five layers that are constituted in cloud computing. The bottom most layer is known as the physical hardware (HaaS). The customers using the cloud for this particular layer are mostly the big corporations whose requirements are extremely large amount of Hardware as a Service. As a result, the cloud-provider runs, oversees, and upgrades its subleased hardware for its customers .
The next layer coincides of the cloud’s software kernel. The layer acts as a path between the data being processed
in the layer of Hardware and software infrastructure layer which is operating the hardware. It is the lowest level of abstraction implement
ed by the cloud’s software and its main job is to manage the server’s hardware resources
while at the same time allowing other programs to run and utilize these same resources. The layer above the software kernel is the abstraction layer called the software infrastructure. This layer provides basic network resources to the two layers above it so that it can facilitate a new environment in a cloud that can be delivered to end users as an IT services. The services offered in the software infrastructure layer can be divided into three different categories: Computational resources (IaaS), data storage, and communication
The services provided by Cloud also divide it into different types of Cloud. For understanding more about cloud, the services provided by cloud may be given as follows:
Platform as a service (PaaS): This provides environment for applications, development of various preparation tools etc. It provides the runtime environment that controls the applications. This type of Cloud, primarily aims to manage the storage, servers and information systems. It aims to facilitate the management problems related to the application development and also helps the customers.
Infrastructure as a Service (IaaS): This provides the elementary resources access such as virtual machinery, storage, physical machinery etc. The manageable things can be the operating system, application, chosen network elements, application. It actually provides the processing, networks, storage and essential resources for the user.
Software as a service (SaaS):
This model provides one o use the application as a service to the users. The network, operating system, servers, storage or applications are not managed by the user. The environment is provided for the software distribution.
Here are four different types of cloud deployment models which can be named as Public Cloud, Private Cloud, hybrid cloud and community cloud. The details of these types may be given as follows:
Public Cloud: A cloud infrastructure is managed by a third party and is provided to many customers and which is beyond the firewall of the company. The infrastructure provided, can be used by more than one enterprise at the same time and the resources can be provisioned by users dynamically. The cloud providers are responsible for the management, provisioning, installation and maintenance of the cloud. The cloud providers solely manage and host these clouds. The under usage of the resources are eliminated and the Customers only pay for the resources they use. As the consumers have very less control over the infrastructure, processes requiring powerful security and regulatory compliance which are always not a good fit for public clouds. In this model, there are no restrictions applied on the access and authorization and authentication techniques cannot be used. Public cloud providers such as Google or Amazon offer an access control to their clients. Examples of a public cloud include Microsoft Azure, Google App Engine.
Private cloud:This type of cloud can be owned or rented and managed by the organization itself or somebody not from the organisation that is the third party and exist at on-premises or off-premises. When compared to the public cloud, It is more expensive and secure than it. There are no additional security regulations, legal requirements or bandwidth limitations are there in private cloud that can be present in a public cloud environment also but by using a private cloud, there is control of the infrastructure and improved security at the end of cloud service providers and the clients have optimized, since the
user’s access and the networks
used are restricted. One of the best examples of a private cloud is Eucalyptus Systems.
Hybrid Cloud: It is a combination of two or more cloud deployment models, linked in such a way that data transferred, takes place between the two different clouds without affecting each other. These clouds would typically be generated by the enterprise and responsibilities for management would be split amongst the enterprise and the cloud provider. In this model, a company can outline the goals and needs of services. A well-constructed hybrid cloud can be useful for providing secure services such as receiving customer payments, as well as those that are secondary to the business, such as employee payroll processing. The major flaw in the hybrid cloud is the difficulty in creating and governing such a solution effectively. Services from different sources must be obtained and provisioned as if they originated from a single location, and interactions between private and public components can make the implementation even more complicated. These can be any type of a cloud combination i.e. private, community or public clouds which may be linked by a proprietary or standard technology that provides portability of data and applications among the composing clouds. An example of a Hybrid Cloud includes Amazon Web Services (AWS).
Community Cloud : Infrastructure shared by several organizations for a shared cause and may be managed by a third party service provider or them and rarely offered cloud model. These clouds are based normally on an agreement between business organizations which are related such as banking or educational organizations. A cloud environment operating according to this model may exist locally or remotely. An example of a Community Cloud includes Facebook .
Cloud computing as of now we know that it refers to the sustained storage and the advanced sharing of data over the internet. But, the threats from the security is embedded in cloud computing approach is proportional to the offered advantages directly. Also, it allows the users to store the data privately as per the requirement. Various methods for computation and strategies in cloud computing for different functioning are elaborated. Every person who accesses the internet does not use the applications of cloud properly so that the use of cloud can be efficient.
This is because of the threats to the entire concept of Cloud computing and its security which
creates the doubt in user’s mind to use and rely upon the services being provided. Security issues may be of any
kind. There are new security techniques being added to the list of different techniques already being used to reduce the risks in cloud. But still there are many more hindrances and computational problems that are and might occur today or in the coming future. The work has to be done in order to support cloud computing and understanding the challenges regarding security issues in cloud.
Welcome to Steem Community @sirhid! As a gentle reminder, please keep your master password safe. The best practise is to use your private posting key to login to Steemit when posting; and the private active key for wallet related transactions.
In the New Steemians project, we help new members of steem by education and resteeeming their articles. Get your articles resteemed too for maximum exposure. You can learn more about it here: https://steemit.com/introduceyourself/@gaman/new-steemians-project-launch
Congratulations @sirhid! You have completed some achievement on Steemit and have been rewarded with new badge(s) :
Click on any badge to view your own Board of Honor on SteemitBoard.
For more information about SteemitBoard, click here
If you no longer want to receive notifications, reply to this comment with the word
STOP