Cracking Project an Application or Information System #1
Cracking Project for Application or Information System
Harold Pantoja - Andrés Vera
ABSTRACT: Cracking has two definitions, depending on whether it is computer security or program crack. In the case of computer security is the permanent attempt to breach security of computer systems, with justified or not. In the case of crackeo of programs the definition is the creator of cracks, is to break, that are programs destined to the desprotection of commercial programs so that they can be used without limits.
KEY WORDS: Crakeo, OllyBDG, Disasm, Virtual DJ, Tuneup, Assembler, Heels, Limited Use, Series,
INTRODUCTION
Almost everyone sees cracking as piracy, as something illegal, although there is some reason here if used incorrectly as in most cases. All science is supposed to be used for good, and cracking should be. It would be good for crackers to learn from the beginning to study commercial protection systems in order to create new ones with greater security or improve existing ones and implement them in future programs instead of cracking crawling on the internet, because that is illegal.
Then we could say that there are good and bad crackers, good ones fortunately there is a good amount, but there are also many of the others that perhaps many of them have very bad intentions like creating viruses to cause damage. The good cracker may or may not consider these types of crackers as "enemies", but unlike the good, the bad one has as enemy # 1 the authors of the programs.
II. PROTECTION OF PROGRAMS
The extraordinary number of programs that have been cracked, most of them were programmers who made the protection system. The rest have been the same crackers who programmed it, and who better if not then? These protections presented great difficulty to unprotect them, although you have seen programs that are almost impossible to crack and only a cracker can do such a system, but as we know nothing is impossible, there is 100% security.
There are endless ways to protect programs, the most common to find in programs are as follows:
Limited use time: The program may expire after a period of time determined by the programmer from the date of installation if the program is not registered. It is usually limited to minutes, hours, days and months.
Number of limited runs: The program expires after running a certain number of times after installation if it is not registered.
Serial Number: This is the most common to find, there are two types, fixed or variable serial numbers, the latter is generated in most cases based on something, such as depending on the user name, organization.
Annoying messages: This is also quite common, they are windows that can appear at the beginning of the program or at the end, or in some action by the user where he reports that he is facing an unregistered copy or some other message related to protection. These messages disappear when you register.
III. HOW TO CRACK A PROGRAM
For cracking an application, the first thing we do is the installation of a program that serves to disassemble the executable program in modules, which we can modify to our benefit.
There are many programs in the market, the difference that has one of the other, is that the result of disassembling the program can be in the source language (Assembler) or in another superior language.
Next what we do is install the program that we are going to carry out the cracking, taking into account of course that the program has some restrictions for its use, such as serial, trial version, etc. Also also bear in mind that not all The programs can be cracked because the same companies where the software is introduced introduce a number of securities in the source code that make it almost impossible to take any action to access this code.
For this part we will use 2 programs to disassemble and assemble again.
The first program that we are going to use is the disasm, this is a program that serves to disassemble a program until its source code (Assembler). This application works by copying the executable file of our program to disassemble to the folder where this Disasm.
Through the console we go to the folder where the program is, so we can use some special commands needed to disassemble, after this we proceed to disassemble the program with a simple command (disams + filename.exe +> text .txt) with this we create a file called text where we find all the code of the program,
In this part of the process, we find perhaps the most important part of the whole process, which is the analysis of the source code.
If the program that we are going to crack requires a code, serial, file, etc., it is intended to observe in detail the windows prior to this event, with which we can associate these events with some type of variable, constant, object that is in the code.
This observation is a fundamental part of the process since here we can get an idea of how our program is working, and also having the source code, can establish a relationship of all those windows, program validation notice, with it.
At the moment of revising the code, we must take into account, two important points, the first, establish what language is made, and the second is to verify the version of such language, usually the result of the programs depends on the Application to be used, and also to identify which language version we should go directly to the processor architecture and in some cases the operating system. Programs that disassemble, are always intended to take the user to the initial source code that is mostly developed on Assembler.
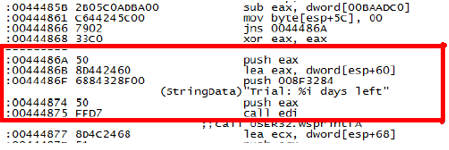
The next step is to check our .txt file where the source code of the program is, and with great detail and patience begin to interpret, and try to find out in which part of the code we find the validation of the program. This task can take a long time, in addition if we find something, only until the end of the steps we can find out if this is really the piece of code we need. In the exercise we find a section of code where it reports that we have a trial version and that we have a certain number of days to use.
Well done, great post!
ty
nice
ty friend