Canadian Business Banking Customers Hit With Targeted Phishing, Account Takeover Attacks
IBM X-Force research has been following the activity of a cybergang that has been targeting Canadian businesses with customized phishing attacks, likely operating out of Ukraine. The attacks are designed to trick those with account access to divulge their company’s online banking credentials, one-time passwords and two-factor authentication codes. The goal of this targeted phishing attack is to take the account over and transfer money to mule accounts that the criminals control.
A Custom-Crafted Email Arrives
The first step in the attacks is an email. Much like other targeted attacks, this was a spear phishing email that was sent to very specific stakeholders with content made to appear legitimate, featuring the correct bank logos and accurate information. Inside that email, the storyline that was designed to gain the victim’s trust came in PDF format. This enabled the threat actors to hide the URL links, keywords and brand abuse from detection mechanisms that would pick these elements up had they been included in the body of the email. It also enabled them to ensnare users who possess enough security awareness to avoid clicking suspicious links in email messages.
To set up for the email campaign, the attackers registered a few domains and created email addresses that contained the bank’s name and appeared to represent the bank’s customer service, security or technology departments.
The group behind this targeted phishing campaign took its time to craft customized PDF lures that appeared to come from actual employees of the victim’s bank. The attackers may have had prior knowledge about the targeted business’ account from a more widespread campaign or from another source. To actually take over the account, however, they needed token codes, and they needed them in real time.
Malicious PDF Lures Use Tried-and-True Ploy
Upon opening the email, recipients encountered the attacker’s ploy: asking victims to synchronize their devices. This one was not especially ingenious — in fact, it is used often in many phishing and malware injection attacks. That fake synchronization is designed to include the process of generating one-time passwords with hardware tokens typically issued to business banking customers.
The attackers also leveraged the urgency factor, another common hallmark of phishing attacks, by warning victims that they must open the PDF promptly for instructions to prevent canceled payments and transaction delays.
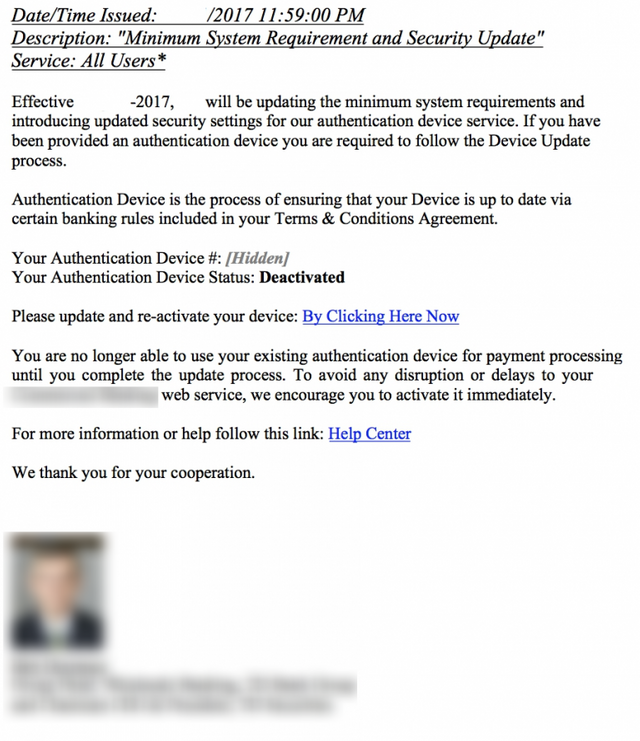
Figure 1: Contents of the fake PDF sent in spear phishing attacks to business banking customers
Out to the WWW
Inside the PDF, the recipients saw properly branded content made to look like it came from one of the bank’s employees. In some cases, these documents contained valid employee names and titles. Others mixed the names and photos of different people. The PDF continued the ploy to pressure victims into undergoing the fake synchronization process, advising them that the device cannot be used until the process is complete.
The PDF contained embedded links that redirected victims to phishing pages the attackers set up in advance. This page also resembled that of a legitimate bank.
X-Force researchers noted that the content of the PDF changed slightly in some cases to address a specific victim’s role, another indication that the attackers had prior knowledge of their selected recipients. Some cases addressed a business banking user, for example, while others addressed an administrator with service access and additional users.
If victims clicked the embedded link inside the PDF, they were first directed to an initial URL that simply bounced them off to the next one. The second hop is where the phishing attack was actually hosted, presenting victims with the stages of the fake process to synchronize their token devices.
The attack was facilitated by a simple fake webpage on which victims were led to submit token codes. The codes went directly to the attackers in real time, allowing them to initiate a fraudulent transfer from an endpoint they controlled.
A schematic flow of events appears below:
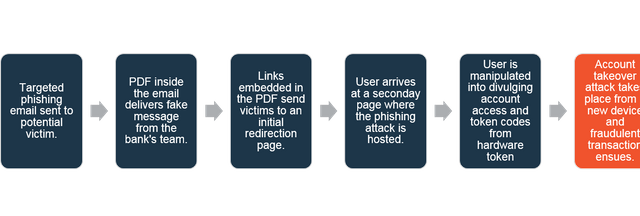
Figure 2: Schematic flow of events of the targeted phishing attack and subsequent fraudulent transaction
The ABCs of XYZs
Having analyzed the domains that served up these targeted attacks, X-Force researchers noted that they hosted a number of other attacks that also targeted Canadian banks. The domains’ IP address came from Ukraine’s IP range, most of which are registered with the .xyz top-level domain (TLD).
Past spam trend analysis from IBM X-Force found that .xyz domain names are typically very cheap to register and can be sold for as little as pennies each, making them more lucrative to attackers that register multiple domains for malicious purposes.
The identified IP address, 176.119.5.123, was served via a local internet service provider (ISP) in Ukraine under the autonomous system AS58271.
WhoIs map of malicious server location
Figure 3: Geolocation of the IP address hosting targeted phishing attacks against Canadian banks
The initial bounce page victims arrived at was the domain www6com.xyz. From there, they were sent to a designated attack page that matched the bank’s brand. Each attack featured a few pages that moved the victims through the steps of the fake process to sync their token devices, starting with a login, then “sync,” “verify” (likely to get a second code), confirmation and end page.
More Where That Came From: Direct Deposit Bait
Continuing the analysis of attacks hosted on the same infrastructure, X-Force researchers discovered that the same group also has a more generic format for Canadian consumer accounts.
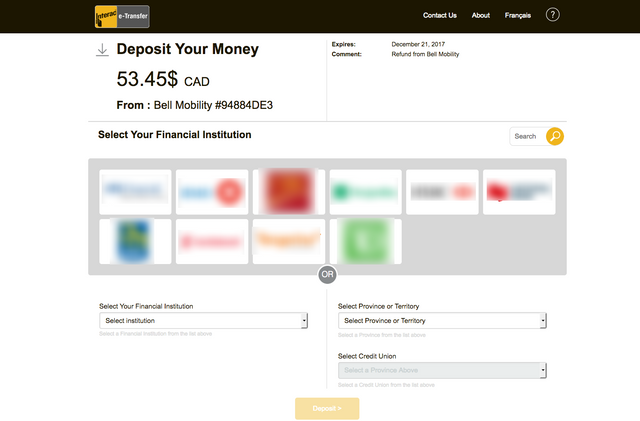
The generic attacks featured a different ploy. This time, victims were supposedly going to receive a refund that could only be deposited directly into their bank account. They were directed to a main page that prompted them to select their banking institution before redirecting them to the corresponding attack page.
IBM X-Force ResearchFigure 4: Main phishing page designed to redirect victims to their corresponding bank
Once on the next page, a succession of phishing pages requested the victim’s login details. It then asked for account security elements typically used for password resets, personally identifiable information (PII) and, finally, a note that the refund transfer could not be completed or that it had expired.
IBM X-Force research labs
Figure 5: Fake page informs victims that the deposit had expired
These generic attacks were most likely sent in larger quantities to recipients in Canada without any specification of which bank each recipient uses. Older versions of the page simply indicated “Refund,” but the more recent ones name a telecommunications provider as the supposed issuer of the refund.
The domains created for the generic attacks were initially registered individually. After about a month, however, the attackers moved on to using a domain generation algorithm (DGA) to create subdomains. This was likely implemented to widen the campaigns, automate the need to recycle ones that are discovered and taken down, and dedicate resources to each targeted brand. The setup of the phishing infrastructure highlights the operators’ access to cybercrime know-how.
Cybercrime Sharpens Focus on Businesses
Cybercriminals’ focus on business banking services is an ongoing trend that became increasingly evident in 2014 with the emergence of financial crime groups that operated Trojans such as Dyre, Dridex and Neverquest. In many of these cases, the attackers are either situated in or otherwise linked to Eastern Europe, hosting malware and phishing operations from countries in the region.
This trend has only been increasing, with malware such as TrickBot, QakBot and IcedID showing that their focus is primarily on business banking and high-value accounts rather than consumer accounts. It is therefore not surprising to see financially motivated targeted attacks emerge from the same part of the world, delivering sophistication and familiarity to rob businesses in the West.
X-Force research noted that, overall, the Russian-speaking underground and fraud economy has always been the most advanced in technical terms. That environment produces financially motivated actors with the skills and savvy to create advanced attack tools and enjoy support from fraud commodity and service vendors. It stands to reason that, due to the already developed network of cybercrime activity and tools in the region, groups that operate in that fraud arena use information sharing and various criminal-operated services designed for their chosen endeavors.
Thwarting Targeted Phishing Attacks
The fight against phishing in the workplace is an ongoing educational process. One of the most effective ways to detect spear phishing is role-based security training for employees, especially those with access to company resources such as bank accounts.
During the investigation of these targeted attacks, the X-Force team noted that, in many cases, the victims were small and midsized businesses (SMBs). According to a recent IBM survey, 58 percent of large companies reported that they offer security training to employees, but only 30 percent of smaller companies do, which potentially exposes SMBs to greater risk of compromise, since their security budgets may be limited to begin with.
Security training and incident response planning can go a long way toward helping to protect the business and recovering stolen funds in case of this type of compromise. Banks and businesses that wish to take a technological approach to detecting account takeover and protecting against phishing are invited to learn more about the IBM Trusteer Fraud Protection Suite.
To view a list of domains, IP addresses and currently live attacks, check out the public collection on X-Force Exchange.
You do things when the opportunities come along. I've had periods in my life when I've had a bundle of ideas come along, and I've had long dry spells. If I get an idea next week, I'll do something. If not, I won't do a damn thing.