Secure your internal Network
The Security Tools, Security Protocols and Policies which I propose are includes: Dynamic NAT, DMZ, Firewalls, Network Monitoring, Server Policies, Using VLANs, Hiring expert Security Specialist and Technicians, Using high quality physical devices, arranging awareness sessions, documenting and proper maintenance.
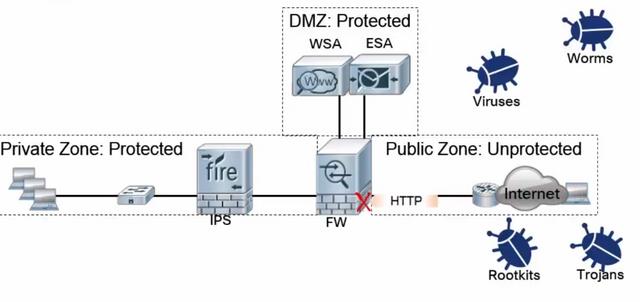
Each of them has its own pros and cons, but for a better network security, we need to configure all of them. For example: Dynamic NAT can help to send out the outbound packets fast using different publics IPs which we have configured in the NAT. Although, that is not a must for a small or medium scale company, but it can help to amend the security.
Secondly, configuring DMZ is a very important aspect in IT Security. In the DMZ we put all the servers and data which are being accessed publically. So it can help us to protect our internal network. Inside the DMZ we can configure so many other security policies, devices, and protocols such as: ESA (Email Security Appliance), WSA (Web Security Appliance), and Etc. which can help us to minimize the threats to zero.
Thirdly, configuring several firewalls before, within, and after the DMZ zone for specific purposes can assure that our network is 100% secure from outside threats.
Another important thing which I had proposed above for better network security is Network Monitoring. In IT Security if we don’t know what packets are going out, and what packets are coming in, then obviously we have no idea about the possible flaws in our network as well. In order to minimized the risks from outside threats we must clearly monitor all the inbound and outbound traffics.
Furthermore, configuring the policies in our domain, user privileges, using high quality security and updated devices, configuring VLANs within our internal network, and finally hiring experienced and skilled IT Security specialists and technician to maintain and regularly checkup our network.
All the mentioned security devices, protocols, software, and policies will align with the IT Security, if we configure them based on our needs. If we have a clear knowledge of our internal network, ports, types of services, and whatever which is going on within our network, then we can secure our network successfully. But if we don’t have a clear idea of our network, configuring hundreds of devices, protocols and policies may not help us.
(Soshiance - 2019)
Hi, @soshiance.tech!
You just got a 0.01% upvote from SteemPlus!
To get higher upvotes, earn more SteemPlus Points (SPP). On your Steemit wallet, check your SPP balance and click on "How to earn SPP?" to find out all the ways to earn.
If you're not using SteemPlus yet, please check our last posts in here to see the many ways in which SteemPlus can improve your Steem experience on Steemit and Busy.