NSClient ++: Run PowerShell scripts with NRPE
Supervision of Windows servers with Centreon often passes through the use of SNMP and / or the famous NSclient ++ software and acts as a real supervisory agent, compatible with the NSCA and NRPE functions. Although it integrates natively different modules including check_nt to check the use of CPU, RAM, disks, etc. It may be necessary to do more detailed, more personalized checks.
By means of Nagios Remote PluginExecutor (NRPE), we will be able to execute scripts locally on the Windows server and then return the information to Centreon. In this tutorial, we will see how to configure NRPE to execute scripts, in this case PowerShell, but it also works with other languages (VBS, DOS, Python, etc.).
II. Configure NRPE on NSClient ++
We will assume that NSClient ++ is already installed on your server, but it is not sure that the NRPE is active! It all depends on the options selected during installation.
If you are installing, here is how to configure NRPE (after all depends on the monitoring solution that will query NRPE).
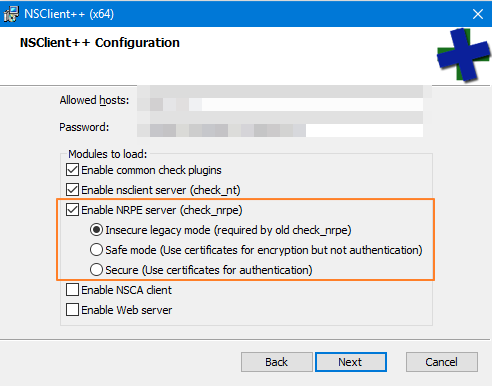
It is quite possible to return to this configuration later. This is done in the nsclient.ini file. Here are some indications:
Enable the NRPE server
NRPEServer = enabled
Enable the execution of external scripts
CheckExternalScripts = enabled
Setting up the NRPE server
The options in this section are to be adjusted, depending on whether you want to use a certificate or not, authentication or not. The most basic configuration is:
[/ settings / NRPE / server]; Undocumented key verify mode = none; Undocumented key insecure = true
For the change to be taken into account, it will restart the service but before that we will continue the configuration.
III. Add a PowerShell script to NSClient ++
Still in the nsclient.ini file, we will declare the external scripts that we want to use. In my example, this will be the PowerShell script "check-dhcp-failover.ps1". It is imperative to store it in the "scripts" directory of the NSClient ++ installation folder.
Here is the line of code to include:
[/ settings / external scripts / scripts] check-dhcp-failover = cmd / c echo scripts \ check-dhcp-failover.ps1; exit ($ lastexitcode) | powershell.exe -command -
The name of the command / plugin that can be used in NRPE is "check-dhcp-failover" and then we indicate the path to the script.
To add another script, it will not be useful to include the line "[/ settings / external scripts / scripts]" but only to declare another script under the first one.
Now, we restart the service to take into account the changes:
Restart-Service nscp
We will modify the execution strategy of the PowerShell scripts on the server so that it is authorized:
Set-ExecutionPolicy Unrestricted
Finally, we will check that it works, we can test the script from the server directly, before switching to the Centreon. We will validate a first step with the command "test nscp.exe" followed by the name of our plug-in declared in nsclient.ini.
cd C: \ Program Files \ NSClient ++ nscp test check-dhcp-failover
The last command entered above must return the check status of your script, ie the state / value that will be sent to your Centreon.
IV. Check_nrpe from Centreon
From the Centreon server this time, we are going to interrogate NRPE remotely. The check_nrpe script is located in the following folder:
/ Usr / lib64 / nagios / plugins /
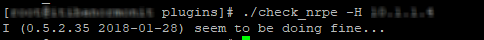
If we execute the script with the -H option and specify the IP of the remote server that we have just configured, we must obtain this:
./check_nrpe -H 192.168.1.50
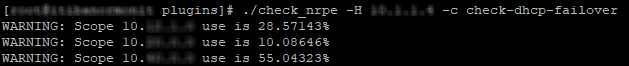
Now, we will directly execute our custom plug-in associated with the PowerShell script. The "-c" option will be used, which gives:
./check_nrpe -H 192.168.1.150 -c check-dhcp-failover
If the state is returned, it's all good! For my part, this is a script that checks the status of DHCP including the use of DHCP scopes (scope) where the following return:
Upvote this for me please? https://steemit.com/christianity/@bible.com/verse-of-the-day-hebrews-4-16-nlt
Congratulations @jemmy! You have completed the following achievement on Steemit and have been rewarded with new badge(s) :
Click on the badge to view your Board of Honor.
If you no longer want to receive notifications, reply to this comment with the word
STOPCongratulations @jemmy! You have received a personal award!
Click on the badge to view your Board of Honor.
Do not miss the last post from @steemitboard:
Congratulations @jemmy! You have completed the following achievement on the Steem blockchain and have been rewarded with new badge(s) :
Click here to view your Board
If you no longer want to receive notifications, reply to this comment with the word
STOPDo not miss the last post from @steemitboard:
Congratulations @jemmy! You received a personal award!
You can view your badges on your Steem Board and compare to others on the Steem Ranking
Do not miss the last post from @steemitboard:
Vote for @Steemitboard as a witness to get one more award and increased upvotes!