Monero XMR – Malware’s Favorite Coin?

Privacy within the cryptocurrency ecosystem is a much sought-after feature, and no one does it better than Monero XMR. With ever increasing government and regulatory pressure, Monero offers a privacy solution in the form of ring signatures, ring confidential transactions, and stealth addresses to obfuscate the origins, amounts, and destination addresses of all transactions on the network.
Key features of Monero include:
- Security
- Privacy
- Untraceability
- Fungibility
Often hailed as the King of Privacy within the crypto community, Monero has recently come under close scrutiny for the distribution of hash power across the network. With the recent release by CoinHive of a Javascript library that allows website owners to harness the CPU power of its users to mine Monero, it is clear that malware developers are utilizing this opportunity to make some serious money mining the coin, often by unsuspecting users.
Security experts are discovering that some of the largest malware and malvertising groups are deploying the CoinHive script on a global scale. Online security firm Kaspersky has reported seeing over 1.65 million computers infected with cryptocurrency mining malware. As you can see from the most recent data below from the website MoneroHash, nearly 92% of the hashrate across the network is from “unknown” sources. Many security experts in the space believe that the majority of this mining is being done using malware.
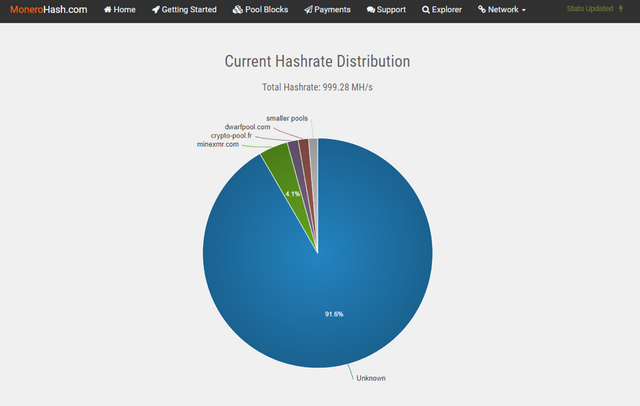
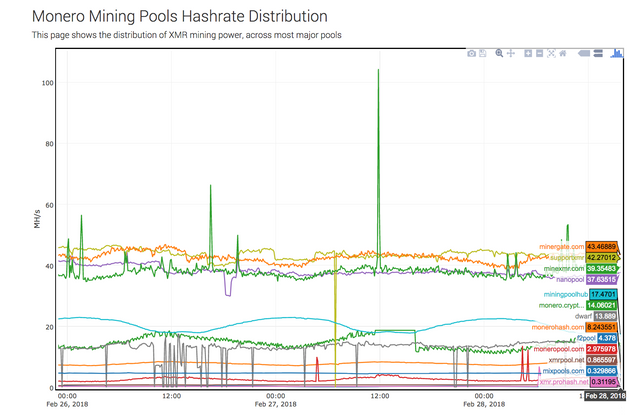
The original idea behind the CoinHive script library was to provide websites the option to forego advertising in exchange for users mining cryptocurrency. This would provide website owners the option of having a cleaner looking website without a lot of advertising distracting the users. This seems like a good idea in practice, but only if users “opt in” to the service. Malware developers have basically taken the code and modified it so that website users are unaware that they are mining the coin.
Taking it a step further, malware groups are embedding the mining script into typosquatting domains. These are domain names that are registered as common “typos” that a user might enter when trying to reach a website. For instance, someone recently registered the domain name “twitter.com.com” and embedded the CoinHive script into the webpage. Users that incorrectly entered the Twitter.com domain name would be unsuspecting miners of Monero, with all of the mining proceeds going to the hacker. Although the user would quickly realize that they were on the wrong site, with hundreds or thousands of these domain names registered, you can see how the mining revenue could add up pretty quickly.
Why Monero?
Many security experts believe that there are two main reasons that malware developers are utilizing the Monero XMR coin for covert mining. First of all, the coin can be easily mined using a CPU. With most of the world’s computers lacking GPUs and ASIC components, this is the perfect coin to mine when launching a global malware attack of this nature. Literally ANY computer or smartphone can mine Monero. Second of all, Monero contains three very powerful privacy components that allow everything the malware developer does to essentially be invisible. Monero hides the sender, the amount being sent, and the recipient. Although privacy is one of the most important features that a cryptocurrency can have, it is a double-edged sword in that it allows hackers and malware developers to work in the shadows.
How do you protect yourself?
Many users want to know how they can protect themselves in this ever-changing landscape, so I’ve listed a few of the best resources below:
- AdBlock Plus and AdGuard are popular ad blockers that provide detection of the CoinHive Javascript library
- AntMiner, No Coin, and minerBlock provide Chrome extensions that scan your browser and terminate anything that looks like Coinhive’s miner script
Another way to protect yourself is to make sure that you are viewing correct web domains. Use bookmarks to browse to your favorite sites instead of typing the domain name into the search bar. This will ensure that you do not type the wrong address and go to a typosquatted domain. In addition, you can periodically monitor the processes running on your computer. If you are only using a web browser, and your CPU power is maxed out, there is a good chance that you could be inadvertently mining Monero or have some other malware running in the background.
How can you profit from mining Monero?
Many would argue that the distribution of the hashrate across a large number of computers only helps to strengthen the decentralized nature of the coin and is in fact a good thing. Whatever your views on the current state of Monero, it is still a highly profitable coin to mine for the everyday computer user. Instead of mining for malware developers, why not mine it for yourself and reap all the benefits!
On the popular website MinerGate, Monero XMR is currently listed as the most profitable coin to mine with a CPU. You can check out how much you can earn by using their Mining Profitability Calculator.
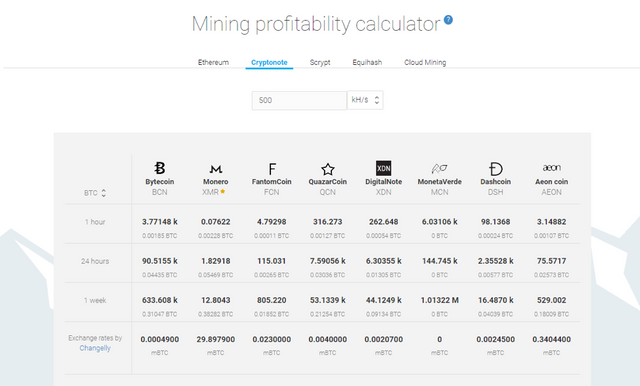
MinerGate makes it incredibly easy to mine cryptocurrencies by doing all of the work for you. It also mines the most profitable coin according to your hardware. If you want to make some extra money with your computer, just download the MinerGate Software, and you can begin mining Monero XMR and other coins in a few minutes. Happy mining and be safe out there!
Join the community of MinerGate and connect your workers for profitable mining!

Nice post! I will follow you from now on.
Thank you, i write a post about your great service, it´s in spanish
https://steemit.com/mining/@futrera/minergate-la-forma-mas-facil-de-minar-criptomonedas