Microsoft: Petya ransomware attacks were spread by hacked software updater!
Microsoft says some of the first Petya infections yesterday were due to a legitimate software update from a Ukraine accounting software firm.
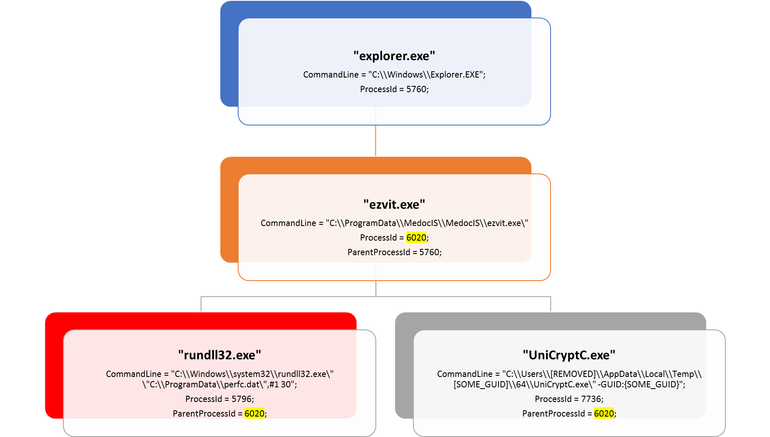
Microsoft has detailed the infection chain from the compromised MEDoc updater.
Image: Microsoft
Microsoft on Tuesday confirmed some initial infections in the Petya ransomware attacks occurred via Ukraine-based tax accounting software firm M.E.Doc, which develops MEDoc.
The finding solves part of the mystery surrounding yesterday's huge ransomware outbreak that hit industry giants like shipping firm Maersk, but took a particularly heavily toll on organizations in the Ukraine, including banks, energy companies and even Kiev's main airport.
Security researchers speculated a corrupted MEDoc updater was the initial infection vector. However, Microsoft now says it has solid evidence that at least some infections were due to a software supply-chain attack that started with a legitimate MEDoc updater process.
"Although this vector was speculated at length by news media and security researchers -- including Ukraine's own Cyber Police -- there was only circumstantial evidence for this vector. Microsoft now has evidence that a few active infections of the ransomware initially started from the legitimate MEDoc updater process," Microsoft said.
Its telemetry data shows that at around 10:30am GMT the MEDoc software updater "EzVit.exe" executed a malicious command-line C:\Windows\system32\rundll32.exe" "C:\ProgramData\perfc.dat",#1 30. It's also provided a diagram detailing the chain that leads to the ransomware infection.
The company recently detailed a similar updater attack against high-profile tech and financial firms.
Microsoft's says 12,500 machines in the Ukraine were exposed to the threat yesterday. It also observed infections in 64 countries, including Belgium, Brazil, Germany, Russia, and the US. According to Kaspersky Lab's data, most infections occurred in the Ukraine.
There's some debate on exactly what to call this ransomware. Initially it was thought that the malware was a strain known as Petya. However, Kaspersky Lab reported that it was different enough to warrant its own name. Microsoft says it shares similar code to Petya but is "more sophisticated".
As Microsoft notes, the malware has multiple lateral movement techniques, which allows it to spread on a network if it infects just once machine. Besides using SMB vulnerabilities as WannaCry did, it also features a credential-dumping tool to target password reuse and active sessions on multiple machines.
TheShadowBrokers, the hacking group that leaked the EternalBlue exploit used by WannaCry and now Petra, resurfaced in the wake of yesterday's Petya ransomware outbreak.
As it did after WannaCry, the rant-prone hacker group is riding on news of the Petya/NotPetya ransomware to promote its July "dump of the month", which will cost significantly more than the $23,000 it charged for the June dump.
The group details its offer in a new post on Steemit, claiming its June dump service was "being great success for theshadowbrokers" which had "many subscribers". Because of this supposed success, the price of its July dump will be 200 Zcash, which is double the amount in the said cryptocurrency of its June offer but converts to $65,000 at today's exchange rates.
The group promoted its June dump in mid-May, a few days after the WannaCry outbreak. A month earlier it dumped several hacking tools, two of which, EternalBlue and DoublePulsar, were used to spread WannaCry.
Yesterday's Petya ransomware outbreak uses EternalBlue and EternalRomance. The tools were developed by EquationGroup, which is believed to be the hacking unit of the NSA.
The group hasn't said what it may include in the July dump. It promised a range of potentially dangerous tools in the June dump, including exploits for browsers, routers, and mobile devices, as well as exploits for Windows 10, hacked network data from SWIFT providers, and nuclear and missile programs of Russia, China, Iran, and North Korea.
Researchers were divided over whether to pay for a subscription. Co-founder of security firm HackerHouse Matthew Hickey attempted to crowd-fund a subscription so patches could be developed, but later canned the plan due to the legal risks of paying a criminal group for the exploits and compromised data.
TheShadowBrokers doesn't take credit for yesterday's outbreak, but notes it was a "fitting end" for the first month of its dump service, which followed its fail attempt to auction attack tools developed by EquationGroup.
It's also threatened to dox a person it refers to as "doctor" who the group thinks is a former EquationGroup member. The apparent target of that threat, @DrWolff on Twitter, has denied ever being part of EquationGroup.