North Korean hackers are targeting cryptocurrency traders with fake software.
Powered by
WORLD
North Korean hackers are targeting cryptocurrency traders with fake software
Lazarus is back with new tools
North Korean hacking outfit “Lazarus” is now targeting cryptocurrency exchanges. Information security firm Kaspersky Labs has discovered it is exploring new attack vectors and trojanizing cryptocurrency software.
Kaspersky Labs has been tracking Lazarus for over a year. Back in April, it made its investigations public with research proving that the hacker crew had managed to steal $81 million from a Bangladeshi bank.
Now, Lazarus is tricking unsuspecting users into downloading cryptocurrency-related software laced with malware. Research posted to Kaspersky’s media outlet, Securelist, reads:
While investigating a cryptocurrency exchange attacked by Lazarus, we made an unexpected discovery. The victim had been infected with the help of a trojanized cryptocurrency trading application, which had been recommended to the company over email.
Its primary function is to load the malware suite ‘FallChill’ onto machines while opening a series of backdoors. Computers infected with FallChill can be controlled remotely and should be considered completely compromised.
The use of such malware has become the calling card of Lazarus. It should be noted that US-CERT claims the North Korean government has used FallChill against political enemies extensively in the past. US-CERT has another name for the crew, HIDDEN COBRA, which it uses rather than ‘Lazarus.’
Until quite recently, hackers have been content with targeting Windows-based machines. This has led to a belief that macOS and Linux operating systems are more secure, with less instances of viruses, malware, and related hacks.
Lazarus is looking to exploit this complacency by distributing malware for macOS and soon Linux. Kaspersky’s research warns that this “should be a wake-up call for users of non-Windows platforms.”
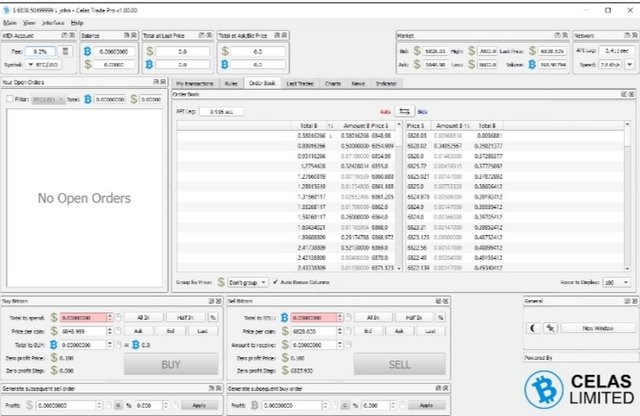
On the surface, Celas Trade Pro really does appear to be kosher. It certainly looks like an all-in-one cryptocurrency trading application, an interface for making trades and reading market data.
Powered by
WORLD
North Korean hackers are targeting cryptocurrency traders with fake software
Lazarus is back with new tools
North Korean hacking outfit “Lazarus” is now targeting cryptocurrency exchanges. Information security firm Kaspersky Labs has discovered it is exploring new attack vectors and trojanizing cryptocurrency software.
Kaspersky Labs has been tracking Lazarus for over a year. Back in April, it made its investigations public with research proving that the hacker crew had managed to steal $81 million from a Bangladeshi bank.
ADVERTISING
inRead invented by Teads
Now, Lazarus is tricking unsuspecting users into downloading cryptocurrency-related software laced with malware. Research posted to Kaspersky’s media outlet, Securelist, reads:
While investigating a cryptocurrency exchange attacked by Lazarus, we made an unexpected discovery. The victim had been infected with the help of a trojanized cryptocurrency trading application, which had been recommended to the company over email.
Its primary function is to load the malware suite ‘FallChill’ onto machines while opening a series of backdoors. Computers infected with FallChill can be controlled remotely and should be considered completely compromised.
The use of such malware has become the calling card of Lazarus. It should be noted that US-CERT claims the North Korean government has used FallChill against political enemies extensively in the past. US-CERT has another name for the crew, HIDDEN COBRA, which it uses rather than ‘Lazarus.’
Until quite recently, hackers have been content with targeting Windows-based machines. This has led to a belief that macOS and Linux operating systems are more secure, with less instances of viruses, malware, and related hacks.
Lazarus is looking to exploit this complacency by distributing malware for macOS and soon Linux. Kaspersky’s research warns that this “should be a wake-up call for users of non-Windows platforms.”
On the surface, Celas Trade Pro really does appear to be kosher. It certainly looks like an all-in-one cryptocurrency trading application, an interface for making trades and reading market data.
courtesy of Securelist
What’s interesting here is that this doesn’t appear to be an attempt to steal cryptocurrency directly. Instead, the hackers appear to be looking to disrupt supply chains and businesses in any way they can. Or in this case, by leveraging the increased popularity of cryptocurrency trading. If people in positions of power download the software, the integrity of their businesses would become but a plaything for Lazarus.
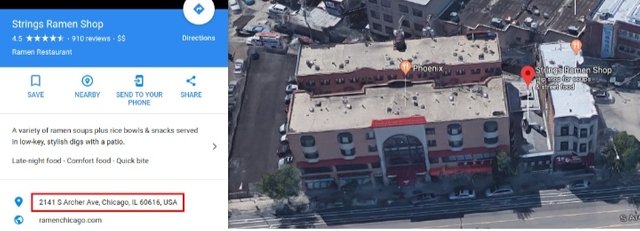
Kaspersky isn’t sure which came first – Celas Limited, who released Celas Trade Pro, or the hackers. The research indicates that the domain was purchased using cryptocurrency; it also notes the site uses poor security certificates. Kaspersky further points out that the headquarters of Celas Limited is really just a ramen shop in Chicago.
It goes deeper: when they tracked the address of a company listed in Celas Trade Pro’s digital signatures, it led directly to an address in, well, the middle of nowhere.
There’s a strong chance that it’s all one big ruse – a fake company with a fake cryptocurrency tool riddled with backdoors. Kaspersky do note, though, that despite all the red flags and the information uncovered, there is not enough proof that the website, company, or application were originally created with malicious intent.
“This should be a lesson to all of us and a wake-up call to businesses relying on third-party software. Do not automatically trust the code running on your systems,” Kaspersky warns in its conclusion. “Neither good looking website, nor solid company profile nor the digital certificates guarantee the absence of backdoors. Trust has to be earned and proven. Stay safe!
Please like comment and follow..kamar raza