Basic info about new Jaff ransomware virus
Jaff extortion virus encrypts user data using RSA and AES-256 algorithms, and then requires a buyback of about 1.82 to 2.036 BTC to get the files back.
The .jaff extension is added to the encrypted files. Files names remain unchanged For example: Image1.gif.jaff
Jaff crypto-extortionist started its activity at the beginning of May 2017. It is particularly aimed at English-speaking users, which does not prevent it from spreading around the world too.
Ransom notes with payment demands are called:
ReadMe.txt
ReadMe.html
ReadMe.bmp
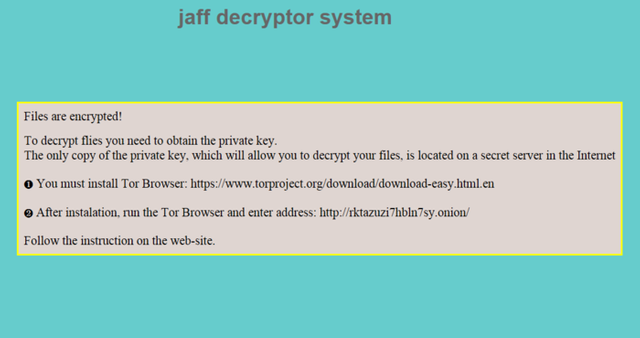
The contents of the notes read like this:
Jaff decryptor system
Files are encrypted!
To decrypt flies you need to get the private key.
The only copy of the private key, which will allow you to decrypt your files, is located on the secret server in the Internet
You must install Tor Browser: hXXps://www.torproject.org/download/download-easy.html.en
After instalation, run the Tor Browser and enter address: hXXp://rktazuzi7hbln7sy.onion/
Follow the instruction on the web-site.
Your decrypt ID: 00335 *****
Developers of Jaff Ransomware have borrowed a template of redemption requirements and HTML-note for the Tor-site from Locky Ransomware (from one of its last iterations).
Jaff virus spreads via email spam and malicious attachments (Word document with macros, PDF, etc.), Necurs botnet, fraudulent downloads, exploits, web injections, fake updates, repackaged and infected installers.
Malicious attachments can be sent in the following format:
Copy_ [Random Numbers]
Document_ [Random Numbers]
Scan_ [Random Numbers]
File_ [random numbers]
PDF_ [Random Numbers]
These are MS Office documents, OpenOffice, PDF, text files, databases, photos, audio files, video, image files, archives, application files, etc.
Jaff Ransomware can encrypt files without connecting to the Internet, thanks to a special encryption scheme, but it still connects to the server fkksjobnn43.org to report that the new victim is encrypted by sending the word "Created".
Possible locations:
C: \ ProgramData \ Rondo \
C: \ ProgramData \ Rondo \ backup.om \
C: \ ProgramData \ Rondo \ WallpapeR.bmp \
The registry entries associated with this Ransomware:
HKCU \ Control Panel \ Desktop \ Wallpaper "C: \ ProgramData \ Rondo \ WallpapeR.bmp"