Understanding Blockchain Technology in Healthcare
Blockchain technology has transformed a number of industries in recent years, and has the potential to revolutionize many more as the public increasingly embraces its benefits.
Quite simply, a blockchain is a distributed tamperproof database, shared and maintained by multiple parties simultaneously on multiple systems. The database keeps secures the records that are added to it sequentially via links to private data, including personal health care data. Each file in the database contains a timestamp and secure links to the previous record. Records can be added to the database, but not removed, with each new record cryptographically linked to all previous records in time. New records can only be added based on synchronous agreement or “distributed consensus” of the parties maintaining the database. By doing so, it is impossible for one party to manipulate individual records. This type of process eliminates the extensive need for trust because participants in the blockchain can have mathematical certainty for every digital asset that constitutes the system you want to protect.
Blockchain technology will revolutionize healthcare. When storing healthcare data using a blockchain database, cryptography is used for encrypting the contents of a message or transaction, so that only intended users can open and read that content. The encryption process works via ‘Public Key Cryptography’ or asymmetric cryptography, an encryption system that uses pairs of keys. A “public key” may be disseminated widely to everyone, while a “private key” is known only to its holder. Either key may be used to encrypt a message, but the other key must decrypt the message. In this way, a patient can encode their health care data, including genomic data with a public key and be sure that only the holder of the private key can decrypt it. Second, the data can be encrypted with a private key. If the data, e.g. a hospital discharge letter, makes sense when it is decrypted using the corresponding public key, it is guaranteed that the holder of the private key is the party that encrypted the data. Such a process is equivalent to “signing” a message because it is analogous to someone putting their unique signature on a document.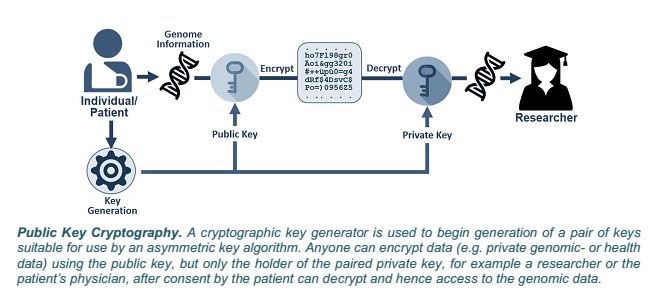
Public Key Cryptography:
A cryptographic key generator is used to begin generation of a pair of keys suitable for use by an asymmetric key algorithm. Anyone can encrypt data (eg private genomic or health data) using the public key, but only the holder of the paired private key, for example a researcher or the patient’s physician, after consent by the patient can decrypt and hence access to the genomic data.
Blockchain technology, in the form of a universal model for record keeping and data storage and access (a secure, decentralized, pseudonymous file structure for data stored and accessed in the cloud) is the technology that is needed to move into the next phase of industrialized genomic sequencing.
At Shivom, we are working towards making this a reality. We aim to be at the forefront of data security and cryptography and our team works in close collaboration with leading cryptographers to add additional security levels to our platform that go well beyond using a blockchain for decentralization.
Multi-level cryptography:
It is necessary to integrate security and privacy into the design of a IT-platform (preventive action) as opposed to perceive it as an addition to a developed business solution.
There are several layers of security and data provenance that we aim to implement, for example:
∙ Security for all parties of a transaction the owners of the solution as well as its users
∙ Stored information about the user is not to be ascribed directly to their physical identity unless it is strictly necessary and negotiated
∙ User’s data is not to be linkable even if more external parties work together on extracting more information than the user has explicitly approved
∙ Service providers using the platform only receive valid user information without getting informed about the user’s identity
We will also work on algorithms to implement so-called proof of liability that makes it possible to identify a user who does not follow the playing rules e.g. by attempting to commit fraud (e.g. uploading data from another person).
In summary, our advanced blockchain-based architecture is aimed at enabling:
∙ That only the necessary healthcare information about the user is disclosed
∙ That disclosure is done under the user’s explicit control
∙ That the user may perform transactions under a virtual identity including not being identified unless strictly necessary/wished by the user
This will enable Shivom to be the safest, most robust health care and genomic data record and storage infrastructure globally, and enable collaborative R&D and precision medicine across health care systems.
— By Natalie Pankova, CSO of Project SHIVOM
Such brilliant ideas,this is great platform with huge potential.
Thanks for your support. Please stay tuned as we have further substantial announcements.
This project will make the investor very happy!excellent project Shivom
Thanks for your support. Please stay tuned.