Risk To Many Malware (MAC OS X) Has Been Monthly
Back in 2011 MAC OS X was attacked by a lot of malware. Now is 2020 still the disease (malware) relapsed again on MAC OS X?

Source
Malware that attacks the Mac operating system. Trojan-shaped malware was successfully detected by ESET and identified as "OSX / Revir. A and OSX / Imuler.A". The Trojan is quite interesting, appears as a pdf file, and targets Macintosh computers.
speak Mandarin. The pdf file on the Trojan contains political nuances, related to territorial disputes, precisely the dispute over the ownership of the Diayou Islands between China and Japan.
Source
The pdf file on the Trojan contains political nuances, related to territorial disputes, precisely the dispute over the ownership of the Diayou Islands between China and Japan.
The mode of Trojan Mac is when the user opens the PDF file, the Trojan will hide the process of installing content by displaying PDF documents with political content in a dispute over the area, so as to be able to suck the user's attention without realizing that the installation process is ongoing.
This is a common mode that normally attacks the Windows operating system, it will usually be seen as .pdf.exe with multiple file extensions that will make it even more adept at hiding. For computers with the Mac platform, such malware is still fairly new, therefore Mac users should always be aware of the presence of PDF files, because the contents will be different from PDFs in general.
"The problem of data theft in cyberspace seems to be increasingly showing the direction of new trends, which are certain to form new patterns of attack in cyberspace."
Not yet finished with the Trojan OSX / Revir.A and OSX / Imuler.A which attacked the Mac platform in Chinese, after a few days there were still other threats targeting the Apple computer operating system, namely Mac OS X Lion (10.7). Threat identified as OSX / Flashback.A belongs to the Trojan category with the following modes:
Trojans are installed on Mac platform computers through fake Adobe Flash installers that are downloaded from third-party sites or sites that distribute Mac application content.
When compared with malware that has been identified previously that is MacDefender and Revir, Flashback malware will attack users who often use social networking sites to attract these users to download and finally the malware will be installed.
The following are some of the ways recommended by researchers at the ESET Malware Intelligence Lab to reduce the possibility of being infected with the Trojan.
- Never open an attachment or e-mail attachment that you yourself do not wish to receive, unless there is prior confirmation, from the sender of the e-mail that the e-mail and attachments are indeed sent.
- when users download files online, don't just trust sites that don't have reputation or don't have authority as outlets that distribute content.
Run an antivirus program / antivirus software for the internet on all devices that can connect to the internet. - ESET Cybersecurity for Mac successfully detected the Trojan then identified as OSX / Revir.A and OSX / Imuler.A.
- In the case of OSX / Flashback.A malware, even though the malware is not a big threat, users should be reminded to take preventative measures including the need for Adobe Flash applications and Acrobat software, download only from the Adobe.com site. Also, turn off Safari settings so that it doesn't open newly downloaded files automatically. In addition, run an antivirus program / antivirus software for the internet in realtime and always updated.
Tips to Strengthen Mac OS X Operating System Security
The article above I gave an example of an attack on MAC OS X. Although it still loses a lot from the Windows operating system in terms of users, but the Mac OS X operating system began to gain popularity in recent years. Along with the increasing popularity of the stretcher, then automatically the hackers also began to look at this operating system as the target of its operation. Evidently, the script is free of viruses that are always embedded in the Mac operating system finally revoked by Apple in 2012 ago. Therefore, this time Paseban will review several ways to improve Mac security.
Source
Some of these tips I often use (simple and easy). If you like using the operating system (MAC OS X) you can try these tips.
Create a non-admin account for daily activities
The default account on Mac OS X You are an administrator user, and malware makers can take advantage of it to infect your computer. For daily activities, you are advised to create a non-admin account and log in using an administrator account if you need it.Use Google Chrome
Google Chrome is a browser that is highly recommended because of its many advantages, one of which is because Google Chrome is updated more frequently compared to Apple's Safari browser. In addition to the sandbox, Chrome is equipped with a sandbox version of Flash Player which provides a significant barrier to malicious websites. Google Chrome also has a stable update mechanism that removes barriers to security vulnerabilities.Remove Flash Player
Adobe's Flash Player is often the target of hackers in taking over your computer. Old versions of Flash Player are very risky when you browse the internet. To delete Flash, you can use the two options provided by Adobe, for versions 10.4 - 10.5 and 10.6 and others.Delete Java
As with Flash Player, Java is also the target of hackers to embed malware in your device. Unfortunately, Apple does not allow Oracle to update Java for Mac directly. They do it themselves, usually a few months later. This makes the window of exposure on Macs take longer than PC users so you are advised to remove it from the computer.Run the Software Update
In recent years many attacks on Mac OS X have taken advantage of old or non-renewable software. Usually Microsoft Office, Adobe Reader / Acrobat, and Java Oracle, but many other applications that can be misused too. Office for Mac 2011 is better than Office security for Mac 2008. If you are still using 2008, you are advised to update it to 2011. Whenever you see Apple's "Software Update", make sure you make repairs and reboot the device if needed.Use password management
Unlike Windows, Macs have password management built into the "Keychain" system. If possible, try to make unique and strong phrases and save them in a keychain instead of having to remember passwords more easily. Whenever cybercriminals attack, they will use the same password on all your accounts - Gmail, Facebook, eBay, PayPal and others. Therefore, by having a strong and unique password at each source, it is able to create stronger security for online security.Do not activate IPv6, AirPort and Bluetooth when not in use
Turn off the connection if it is not used or not needed. This is intended for IPv6, AirPort and Bluetooth which is a gap for hackers to attack. IPv6 is the latest communication protocol that can be used on a Mac. To deactivate it, you can choose Apple menu> System Preferences and then press Network. If Network Preference is locked, click on the lock icon and enter the Admin password to make changes. Select the network service that you want with IPv6, such as Ethernet or AirPort. Click Advanced and click TCP / IP. Click on the Configure IPv6 menu that appears (usually set automatically) and select Off.Turn on full disk encryption (Mac OS X 10.7+) or Firevault
On Mac OS X Lion, Apple updated the encryption solution (FileVault) and added full disk encryption, known as "FileVault 2". This gives a security advantage for the entire disk compared to the home folder and can be very useful if your laptop is stolen.Update Adobe Reader
Adobe Reader has become the target of cyber criminals on the Windows platform and is still the highest ranking among devices worldwide. Make sure you get the latest version by downloading on the Adobe page. Unfortunately, many of the old versions are still available for download and are very confusing.Install Antivirus
"Macs are not infected with a virus" has been a theme that we usually hear since the 2006 advertisement with a picture of a "sick" PC and a "healthy" Mac. Six years have passed and the situation has changed dramatically. In 2011, cybercriminals began to suppress DNSChangers and forged anti-viruses on Mac users in an aggressive manner. The Flashback Trojan that appeared in September 2011 caused a huge blow in March 2012 which accounted for half a million users worldwide infected. Therefore you are required to install an antivirus that already has a name to ensure the security of your computer.
Thank you for those of you who have taken the time to read this article, hopefully it will be useful for you and me.
Congratulations @teach-me! You have completed the following achievement on the Steem blockchain and have been rewarded with new badge(s) :
You can view your badges on your Steem Board and compare to others on the Steem Ranking
If you no longer want to receive notifications, reply to this comment with the word
STOPDo not miss the last post from @steemitboard:
Resteemed already. Upvote on the way @teach-me :)
Thank's brother.
Solid read.
@tipu curate
Upvoted 👌 (Mana: 5/20 - need recharge?)
Thank's to your come here.
Its ultimate goal is to get the user's credit card information which may be used for fraudulent purposes.
Not only that my friend, most likely they (hackers) also want to retrieve information from your computer system(victim).
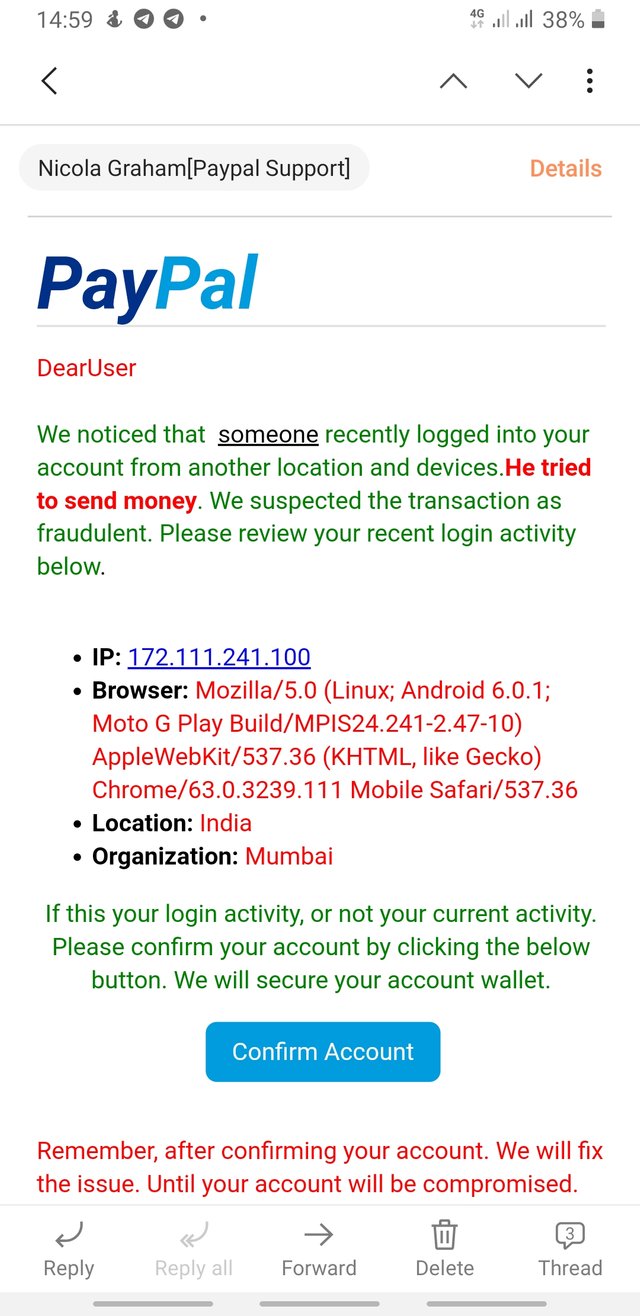
CURRENTLY, a lot of phishing links and trojan attachments are being sent via emails, and a lot of people just click on them. I was sent a link some time back via a mail, i knew it was phishing so i just closed it. Below is the mail screenshot. A lot of people have fallen prey to this but one way to always find a fake email is by confirming the sender address.
Hi @ajewa
The malware I mean isn't that different from your screen capture, buddy.
WOW, thanks a lot for the great tips, it will help a lot of people (including me) to be more careful with our internet activities.
Thanks for sharing this amazing post.
Well, after reading this post, you are going to get all the info that is required via the user. So read the post and get all the data that is needed for the users.
To find out how to Remove DNSChanger Virus
, we suggest to read the steps added to this blog post below.