Grassroot Crypto Education Vol.4; Cryptography| 10% to steemkidss.
Define Cryptography. Explain Private-Key Encryption, Public-Key Encryption, and Hash Functions. What is the distinctive difference between Private-Key Encryption and Public-Key Encryption? .
What happens to outsiders if a message is encrypted? Give a brief example. Visit https://andersbrownworth.com/blockchain/hash, enter two different inputs, and show your observation. (Screenshot required).
Introduction.
Thank you proffessor @fredquantum for the lesson on Cryptograhy on the blockchain. It has really taught me alot about security on the blockchianof many cryptocurrencies today and i would like to begin my homework by defining cryptography.
Define Cryptography.
Cryptography is a security protocol that allows users to share information without giving unwanted parties access to the information shared. It is where only the sender and the one recieving the message can see the content in the presence of other users but without exposing the contents of the messages sent between the two meaning that only and only these two have the power to unlock the details using the different keys available such as the private key and the public key used for encryption of messages.
What is encryption and decryption?
This is the process whereby readable messages or plain text are changed to a secret code so that it prevents outsiders from seeing the details of the message while Decrypting means solving the code product of encryption allowing it to change back to its original form before encryption. For instance, "I love you mummy and daddy" can be ecrypted to become "8 %97w n@k ls$h6 #& Fg)&*". After decryption, the sentence will go back to the original statement of " I love you mummy and daddy"
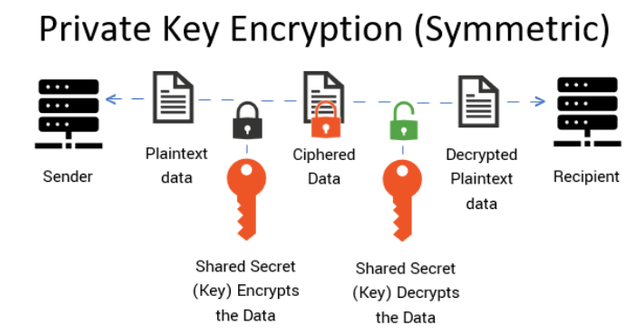
Private-Key encryption.
This is also called the symmetric encryption whereby there is only one key that is used to encrypt as well as decrypt the messages. The sender shares this key with the recever and the one receiving uses it to decrypt the message when it arrives. The message cannot be accessed by those who do not have the key or be leaked to them outside of the two people with the key.
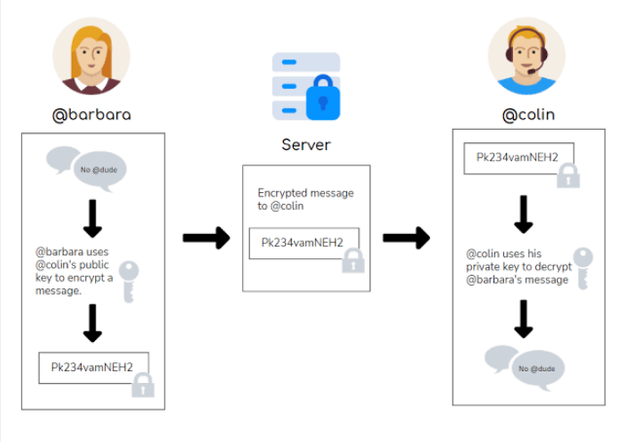
Public-Key encryption.
This is called the Assymetric encryption whereby two keys are used and that is one key for encryption and another key for decryption.
The key that is used to encrypt is called the public key and the key that decrypts is the private key. When the message arrives, the private key makes it change back to its original form. This encryption prevents other users from accessing the information that is intended with only the one with the private key.
What is the distinctive difference between Private-Key Encryption and Public-Key Encryption?
The distinctive difference is that the private key encryption uses one private key for encryption and decryption while the public key encryption uses tow keys, the public and the private key for encryption and decryption respectively.
Hash Functions.
A hash function is an irreversible protocol where data is stored in a way that data that is shared on the blockchain cannot be reversed or altered with. It is one way and one hash is always generated for one transaction, therefore not more than one transactions can have the same hash generated. It also has the same number of fixed-length string characters but they are never the same. The "Hash" is a long stip made up of alphabets and numbers in combination.
What happens to outsiders if a message is encrypted?
When a mesaage is encrytpted, outsiders are blinded and cannot gain access to the information as it is put in code wrod that cannot be understood by a human mind, unless they have the key to decrypt the message. This means that even though the information is on the network, they will not see or even understand it. For example James may be sending John a message in private key encrytption, but Mary who is also on the network will not be able to see the message as it is protected, and only John can view the message using the same private key. If it is on a public key encryption, James will have a public key to encrypt, and John will have a private key to dercypt.
Visit https://andersbrownworth.com/blockchain/hash,
Enter two different inputs, and show your observation
When i visit https://andersbrownworth.com/blockchain/hash, the first input i will use is Dad because i love him so much. So this is the result,
.png)
The input is Dad and the Hash generated ends with ......f47969f3.
The second input is the word Mum and this is the result.
.png)
The Hash generated ends with ......7eb2ebec5e. This clearly shows that the two inputs generated two different Hash.
Conclusion
I want to conclude by thanking my teacher, @feedquantum and @steemkidss for this big chance for us to et ti know all about cryptography and the Security on the blockchain through private and public key encryption, as well as using the Hash mecahnism. Now i know why they saud that it is hard to alter or change information on blockchain system and i think this is a big advantage over the usual systems that have little security and where many things are seen and altered by outsiders. Thank you so much for the lesson once again, i am so grateful to be taking part in this discussion. I love you all, bye. I invite all kids to participate.

Thank you for your participation in this week cryptocurrency home work. We at glad you learning new things. We will appreciate if you keep building your steempower so you can delegate to the community.
Thank you. Waiting for @yohan2on and @boomingcurator to vote me