Cryptography with the Pigpen Cipher
Cryptography with Pigpen Cipher 
A pigpen cipher is a method of protecting information that goes by meny names, some text call it the tic-tac-toe or the masonic cipher. It is sometimes referd to as the Freemason's cipher, the Rosicrucian cipher or the Napoleon cipher.
This simple substitution cipher exchanges each letter of the alphabet with a specific symbol obtained from a grid as shown below.
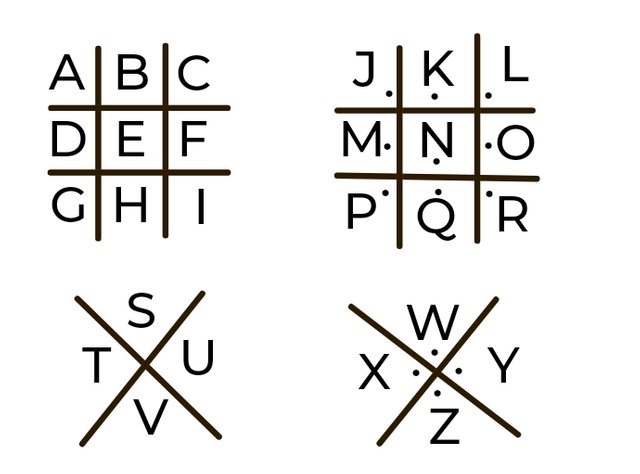
The pigpen as a cipher is not a very secure encryption method and can easily give in to cryptanalytic proceses. It is particularly susceptible to frequency analysis, ciphertext-only attack and brute force attack. Because of these weakness, you can not trust the pigpen cipher with real sensitive information.

The standard pigpen cipher shown above can not accommodate numbers and as such the extended pigpen cipher was developed with an additional twist that accommodates number 0 to 9.
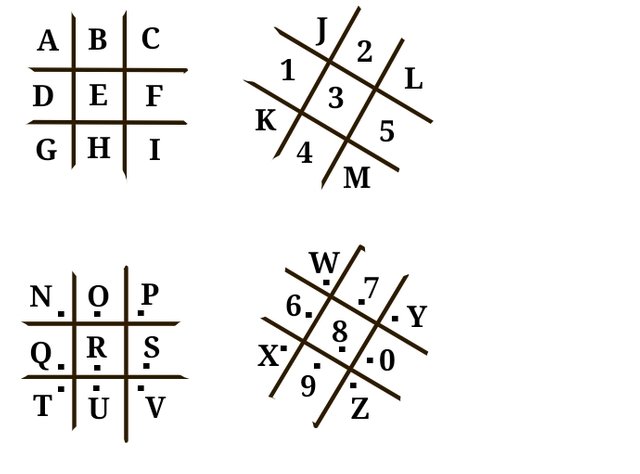
The extension has created room for new symbols representing numbers and has also altered the position of some alphabets.
Using the extension on the pigpen cipher has not improved the fragile nature of pigpen itself. As a substitution cipher, even the extended pigpen will still crumble under the weight of frequency analisis.
Encrypting with a key will significantly make the cipher a lot safer.

Encrypting with a key
A key is the sender's personal twist added to the pigpen cipher such that even when you know how the cipher works, the key acts like a password such that only a person with the correct key will be able to easily convert the cyphertext in to plaintext that is readable.
Applying a key on the extended pigpen cipher further disrupts the position of the alphabets in the grid in such a way that only the right key will have it re-arranged in the correct order for both encrypting and decrypting.
The same key that will be used in encrypting the message will be used to decrypt it, making it a symmetric key. The best type of key for this purpose is a perfect pengram used as a one-time-pad.
Note that having a key is one thing and being able to use it correctly is a completely diffrent thing.

Using the key.
In a pigpen cipher, the key is that unique set of alphabets that are entered first in to the grid, followed by the remaining alphabet in such a way that every alphabet only appears once and is often used as a symmetric key.
For the handwriting on the wall as shown below, the key is made up of two pengram words followed by the remaining english alphabets.
| Key | Dermatoglyphics junk |
|---|
This key is as unique as a finger print itself. Even when pigpen cipher is considerd as very insecure, using a key as password still makes it difficult to crack.
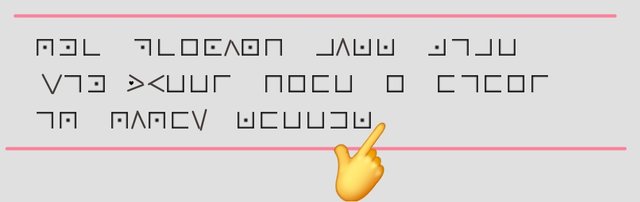
Once this key is correctly applied to the extended pigpen cipher grid, the handwriting on the wall gives up the hidden message.
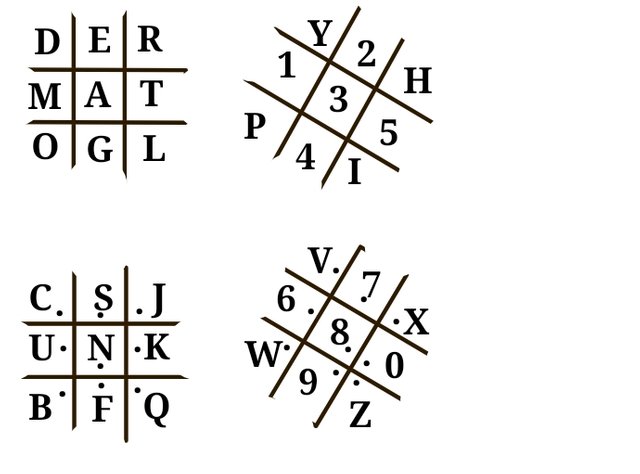
After inputing the key, this is what the setup will look like. Cryptocurrency and digital wallets are protected by encryptions like this at a much higher level.

Curiosity links
Encrypted tribute 1785 tomb stone

Special invitation to
| @samuelnkenta | @josepha | @johnmitchel |
|---|---|---|
| @justiceanietie | @bossj23 | @badmus-official |
| @jozzie90 | @bela90 | @bonaventure24 |
| @graciella | @oasiskp | @saintkelvin17 |
| **** |

#cryptanalysis #learnwithsteem #steemexclusive #nigeria #club5050 #hooks

I actually got a lot of letters in the extended cipher...
Should we still answer it?
Vous le pouvez, même si cela ne compte pas comme un concours, mais si vous souhaitez avoir un prix de consolation, suivez les liens Curiosity et fouillez autour.
Okay
Should we answer with the hints you've given?
Après avoir fourni 95 % de la réponse, j'adorerai toujours vous voir essayer, même si cela ne comptera pas comme un concours, mais si vous aimerez avoir un prix de consolation, suivez les liens Curiosity et fouillez-y.
Okay
Thank you
The X link for this post 👇
https://x.com/manuelhook41759/status/1801894506477806007
Please dear friend, to properly promote your article on Twitter you must use the tags #steem #steemit $steem as the first 3 tags before adding any other relevant tag