Crypto Academy Season 3 Week 8 Homework Post for (@stream4u) Let's Open The CryptoGraphy
The professor explained Cryptography in detail this week. I read the professor's course article. I've done my research and now I'm writing the homework.
1.) Explain the Blockchain CryptoGraphy and mention few names which are the Blockchain Platforms (Few names of the Blockchain Platforms)?
Cryptography is all of the mathematical techniques used to encrypt any information or message in such a way that it cannot be read by an undesired person or persons.
The protection of information and ensuring its security have been of great importance for people since ancient times. Therefore, the science of cryptography was used even before Christ. For example, the Roman emperor Julius Caesar used an encryption technique in the communication of the state and in the transfer of information to the institutions. Julius Caesar's encryption technique was exactly as follows: each letter in a word was formed by substituting the third letter after it in the alphabet. For example, the encrypted version of the word "Hi" is :KL''.
To explain cryptography simply, the first message sent by the sender is encrypted using mathematical techniques, rendering it unreadable. This message is forwarded to the recipient. In order for the message to be read, the recipient must have private keys. The receiver reads the encrypted message using the private key.
It is important for 3 things in making data unreadable. 1) To prevent the disclosure of information in the data. 2) Preventing data from changing 3) Adding false information to data
Blockchain CryptoGraphy
Cryptography has a great role in the popularity of blockchain technology and its adoption by people today. Blockchain is encrypted with cryptography, the data in blocks is secured and made immutable. For example, every new block produced in the bitcoin blockchain has a hash of the previous block. This hash is a summary of the information in previous blocks. Each time a new block is created, a different hash is generated. In this way, the information in the blockchain is transferred to new blocks in an up-to-date manner without being changed. Bitcoin today uses SHA-256 as its hash algorithm. SHA-256 calculates 256-bit summary data each time. Think about it, transactions have been taking place on the Bitcoin blockchain for 12 years, and these transactions are in the form of a 256-bit digest.
All transactions on the blockchain are encrypted as I mentioned, and are copied, stored and recorded on all devices in the system due to the distributed ledger structure. This structure is very important to blockchain technology and it is what makes the technology popular. Being secure, transferring data to blocks without modification.
Blockchain Platforms
The first blockchain platform is Bitcoin. People are showing a lot of interest in platforms because of blockchain technology. Thousands of blockchain platforms have been created today due to some problems in Bitcoin or its insufficiency. The Blockchain platforms that I like the most are:
- Ethereum
- Tron
- EOS
- Monero
- Steem
- Ripple

2.) Explain the Public Key CryptoGraphy.
We can think of the Public Key as a bank account number, an IBAN number. No one can transfer it to you without your public key. If we go a little further, we can compare the Public Key to a mailbox. Anyone can know the address and number of the mailbox, because people need it for you to receive mail. There is also a key that opens the mailbox that no one should know. This is private key.
The Public Key is an alphanumeric password consisting of the letters A-Z and the numbers 0 to 9. As I will address in the next question, it is the "Private Key" that derives the Public Key. It is derived via a private key using cryptographic mathematical formulas. It is possible to generate a public key using a private key, but not vice versa. In other words, it is not possible to generate a private key using a public key. Each public key is unique to a private key. So your public key cannot be associated with any other private key.
There is no harm in having someone else know your Public Key. It might even work for you sometimes.
Another usage area of Public Key, which I will explain shortly, is digital signature. Hash is generated with the document to be signed, for example SHA-256. A password is created with the private key of the person to be signed. The digital signature is transmitted along with the document to reach the recipient. The recipient who owns them gets the hash of the document. Then it decrypts the signature with the public key. Finally, the document is signed and the transactions are completed.

3.) Explain the Private Key CryptoGraphy.
As the name suggests, the private key is private and should not be known to anyone other than its owner. You will lose all control over your wallet if it is known to someone else. It is obtained as a result of the combination of alphanumeric characters. The private key is necessary to ensure full control of the assets you own, to perform the transactions.
The only way to prove that you have an asset on the blockchain is to own the private key yourself. Once you have the private key associated with an address, you have the authority to transact, spend the assets at that address.
When creating a wallet, the private key is also generated. Private keys are private to public keys. A public key is generated through private keys, but the opposite cannot be done.
Private keys also take on the task of adding a digital signature to transactions. Digital signing consists of 3 steps. These are hash generation, signing, and verification. A special key is required for these steps to be processed perfectly.

4.) Explain the Digital Signatures CryptoGraphy and what is Singing Of Transaction/Message?
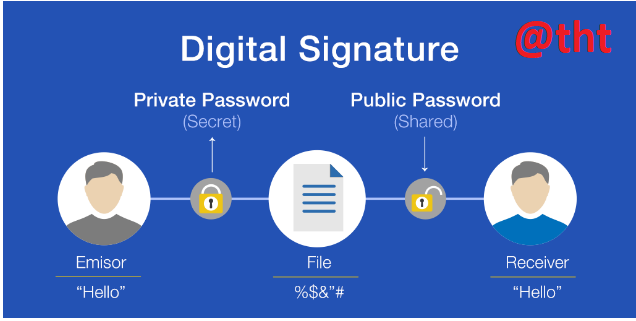
It is possible to say that digital signatures are technically more complex and more reliable than real-life signatures. Because there is an encryption and it is impossible to fake. Digital signatures are a cryptographic mechanism used to confirm the realization, verification and integrity of digital data in the blockchain.
To make it more understandable, we can explain the digital signature as follows. The sender creates a message, encrypts it using a private key. It reaches the buyer. The public key is shared with the recipient so that they can read the message. In this way, it is understood who the sender is and the person who sent the message cannot refuse it. It also makes sure that the message has not been changed since it was sent.
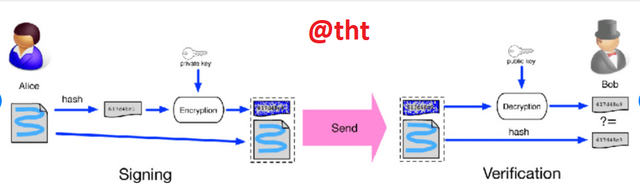
The digital signature step in cryptocurrencies is completed in 3 steps. These are hashing, signing, and validation.
To perform the first step, it is necessary to hash the data. To do this, a hash value is generated by passing the data through a hash generator (for example, SHA-256). Here the person signs the hashed data using his private key.
After the information to be transmitted to the other party has been hashed, the sender must sign it. The hashed message is signed using the private key. The validity of the message is checked using the public key sent to the receiver. The private message must be included when creating the signature because the recipient cannot use the public key used to verify the validity of the message.
Both the public key and the private key message are created by the sender, but only the public key is given to the other party.
The last step is verification. When the message is reached by the sender to the receiver, the receiver can read the message via the public key and verify it. Because the sender cannot create a public key without using the private key.
You can see the schematized version of all these events in the picture below.

5.) Explain what is Symmetric and Asymmetric cryptography?
Data encryption is generally done in 3 ways. These ; keyless encryption, symmetric encryption, asymmetric encryption.
In the keyless encryption method, no keys are used when encrypting data. I will not touch on this encryption method further because the professor asked us to talk about symmetric encryption and asymmetric encryption methods.
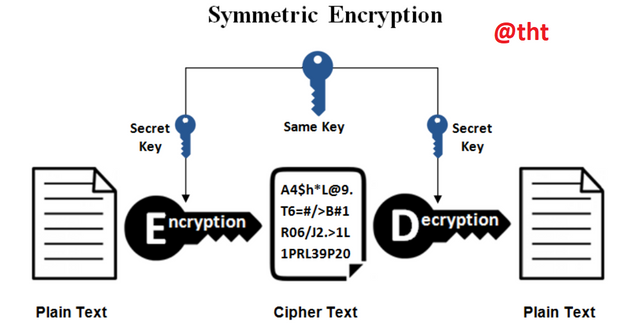
Symmetric Cryptography
Symmetric encryption is a method that has been used since ancient times.
The type of encryption in which the key used when encrypting a data and then decrypting the data is the same in both cases is called the symmetric encryption method. Before the data transfer, the receiver and the sender must determine the private key and decide on the key. This is also called secret key encryption by some people.
The parties, namely the sender and the receiver, must have the secret key to encrypt or decrypt the data.
It is possible to cite Blowfish among examples of symmetric encryption. AES-256 is also an example of a symmetric encryption algorithm and is widely used.
The biggest disadvantage of this type of encryption is the following. It will create a security vulnerability if the receiver and sender exchange the key they will use for encryption.
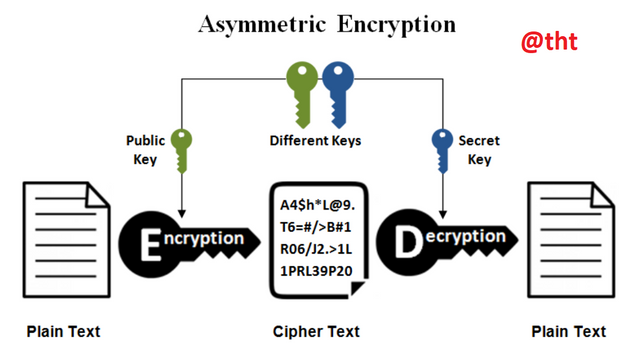
Asymmetric Cryptography
In this encryption method, the key used for encryption and the keys used for decryption must be different from each other. In other words, two different keys are used when encrypting a text. This encryption method is called private key encryption. A public key and a private key are used for encryption and decryption.
The public key is public. Anyone who wants to send you a message can access it. But the private key is secret, it only exists on one side.
This encryption method is generally used in applications used in daily communications over the Internet. ElGamal is among the most popular asymmetric encryption algorithm.
Symmetric encryption and asymmetric encryption methods have different properties.
Symmetric encryption is faster than asymmetric encryption in terms of speed.
Symmetric encryption is used to send large data while asymmetric encryption is used to transmit relatively smaller data.
Symmetric encryption requires lower resource consumption, while asymmetric encryption requires greater resource consumption.
Asymmetric encryption is much more reliable than symmetric encryption. Because, while two keys are used in asymmetric encryption, only one key is used in symmetric encryption.
While the symmetric encryption technique is one of the old encryption techniques, the asymmetric encryption technique is one of the more modern encryption techniques that are used more and more today.

6.)How Blockchain Wallets CryptoGraphy works and explains the available types of Crypto Wallets.
Blockchain wallets serve to store our assets. Blockchain wallets are decentralized and the user is completely in control of the wallet. The user protects the assets in his wallet with the keys he has, and can transfer them to others.
A user who wants to send or receive any cryptocurrency can perform transactions using software called wallets. Just like bank account numbers, each wallet has a unique address. These addresses are handled mathematically, without the intervention of any person or determined by any person.
Blockchain wallets consist of private keys and public keys. By using these addresses, users have the freedom to transact on the blockchain network as they wish.
Wallet addresses consist of lowercase and uppercase sensitive randomly generated numbers and letters. As I said before, private and public keys are needed to access wallet addresses.
A public key is required for transferring to a Bitcoin wallet. Anyone who knows the public key can transfer to this wallet. A private key is required to transfer from wallet to other wallets. The person who has the private key has full control of the wallet. The private key is a 256-bit code and should not be shared with anyone.
There is a mathematical relationship between the public key and the private key, and each public key is private to the private key. It is not possible to access another wallet with the private key you have.
When creating any wallet, the private key is first generated. After the private key is generated, it is hashed twice and a hash value is generated.
Types of Crypto Wallets
Cryptocurrency wallets are categorized in two ways, cold and hot wallets. According to some, cryptocurrency wallets are categorized differently, but by looking at the way they work, it is possible to divide cryptocurrency wallets into cold and hot wallets.
A hot wallet is a wallet that we use online, with internet access. If you send cryptocurrencies to any exchange, you send cryptocurrencies to that exchange's hot wallet. Such wallets are considered to be of low security and it is recommended to keep a small amount of cryptocurrencies in such wallets. Exchanges make small transfers through these wallets.
Cold wallets have no internet connection at all, they are offline. Keys are stored offline to ensure their security. This is how long-term investors or whales store cryptocurrency.
Software wallets
There are many different types of software wallets, they all have different working principles. Most software wallets have an internet connection, so they count as hot wallets. Web, desktop, mobile wallets are examples of software wallets.
Web Wallets
You do not need to download any files to your device to use such wallets. It is possible to access the blockchain by using your internet browser and completing the necessary procedures. For example, Steemitwallet.com is a web wallet. We have the possibility to access it using our internet browser.
Desktop Wallets
As the name suggests, you download the wallet software to your device, and then you start using it. When you use a desktop wallet, you have full control of your funds. In order to use desktop wallets, it is also recommended to create a password as an extra security measure. Desktop wallets have good security levels, but you may experience security threats.
Mobile Wallets
Mobile wallets have more similarities with desktop wallets. Of course it is designed to be used on smartphones. These wallets use QR codes to receive or send cryptocurrencies.
Today, there are mobile wallets that contain many features. TrustWallet is the most popular and most secure of mobile wallets. We have the opportunity to carry out all the transactions you can do in the cryptocurrency sector through TrustWallet.
Hardware Wallets
Hardware wallets are among the cold wallet types. Private keys are securely stored on devices without internet access. Hardware wallets are also expensive, as the security level is quite high. They are not wallets that small investors would prefer. For this reason, they are generally the wallets used by whales who want to store them for a long time.
Paper Wallets
It is not one of the most preferred wallets today due to its high security vulnerability and some flaws. Previously, it was preferred by many segments. The public wallet address and the private key are in the form of a QR code on the paper wallet. According to some, it takes place in the cold wallet format.
The biggest flaw of paper wallets is this. You can transfer all of your assets at once. It is not possible to perform part-by-part transfer operations.

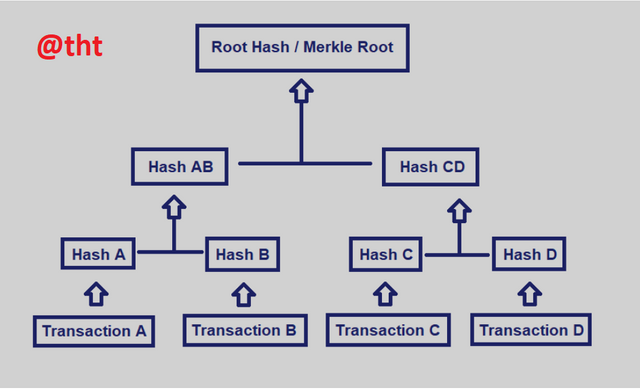
7.) What is the Merkle trees and What its importance in blockchain?
The concept of Merkle tree was defined by Ralph Merkle about 40 years ago. A computer engineer, Merkle was known for his work on public key cryptography.
Similar to the pedigree, there are blocks arranged at the bottom. There is a cryptographic digest of the blocks. Big data structures are securely and perfectly validated through the merkle tree.
The Merkle tree is also referred to as a hash tree by a number of segments. It can also be used to verify all data that can be moved in devices such as computers.
Today, and especially in blockchain technology, its use is of great importance. In peer-to-peer networks, data from peers checks whether the information was sent in an original way. Prevents sending fake, erroneous data blocks.
Merkle trees simply exist in binary form. Each node is connected to the previous two sub-nodes. These nodes can also be connected to the previous two sub-nodes. You can clearly see this in the screenshot.
Here is an example for the Merkle tree to work. You will download a large file to your computer. Consider this an open source software file. So you can see all the codes. The file you downloaded has a hash, it is necessary to check whether this hash is the same as the hash that the developers shared with everyone. If both hashes are the same, you know that the file you downloaded is the same as the developer's file.
The Importance of the Merkle Tree
The Merkle tree is used to verify transactions in blocks much faster and more efficiently. When the data in question matches the root of the merkle tree, the confirmation process takes place safely and quickly. Due to the nature of the blockchain, it is not possible to change these data and replace them with different data. Because the decentralized nature of the blockchain prevents this. Merkle tree is very important for blockchain in terms of speed, security and efficiency.

8.) Practical + Theory, do some practical research, study on Blockchain Demo: Public / Private Keys & Signing and then explain the functionality of Key, Signature, Transaction, Blockchain with proper screenshots of yours practical. (Do study well for this topic)
As in the previous assignment, I will perform the practical operations at https://andersbrownworth.com/.In this lesson, practical transactions will be related to Keys, signature, transaction and blockchain.
Keys
In the Keys section, we will consider the Public key and the private key. We know that there is a mathematical connection between the two. So public key and private key are compatible with each other. So they are unique and have a single owner. They are formed during the wallet setup. While it is possible to generate a public key from a private key, it is not possible to do the opposite.
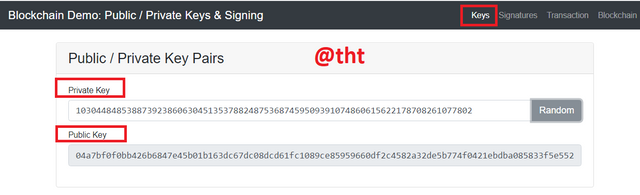
As you can see in the screenshot, there is a private key and a public key. They are different from each other but compatible with each other.
Private Key:
103044848538873923860630451353788248753687459509391074860615622178708261077802
Public Key:
04a7bf0f0bb426b6847e45b01b163dc67dc08dcd61fc1089ce85959660df2c4582a32de5b774f0421ebdba085833f5e552fb8ab0ab00a72af1952d665e215f9667
When I click on a random private key on the website, it will give me a public key that is compatible with the private key. And they are unique to each other.
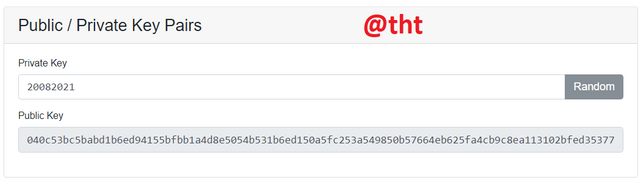
We learned that it is possible to generate a public key from a private key. I manually entered today's date in the private key field (20082021). It created me a public key compatible with this key.
Private Key:
20082021
Public Key:
040c53bc5babd1b6ed94155bfbb1a4d8e5054b531b6ed150a5fc253a549850b57664eb625fa4cb9c8ea113102bfed35377d80825b2c8f1bbe92da4f63113e8b8e5
Since the private key is different from the previous private key, the public key has also changed. Now I will change the private key a bit. Let's see if the public key will change again?
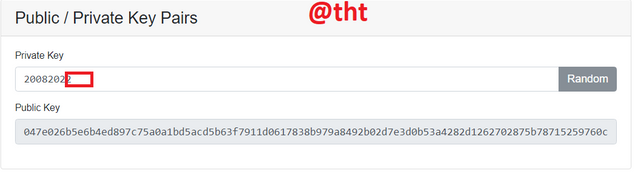
The previous private key was 20082021. The current private key is 20082022. Notice that only the last character is different. Differently, the first private key has 1, the other private key has 2.
Private Key:
20082022
Public Key:
047e026b5e6b4ed897c75a0a1bd5acd5b63f7911d0617838b979a8492b02d7e3d0b53a4282d1262702875b78715259760c9daef39608f81e530c907304470a0b49
As you can see in the screenshot, when the private keys change, the public keys also change. Whether you change the whole private key or change some of it, the public key changes completely.
There is something we must forget. It is not possible to perform the opposite operation when generating a public key from a private key. If the opposite was possible, that is, if it were possible to generate a private key from a public key, the security of our wallets would be compromised. Assets in our wallets were stolen very easily.
Signatures
After practicing the keys, now let's move on to the part about the signature. I wrote Steemit Crypto Academy in the message section. Private key: 20082021
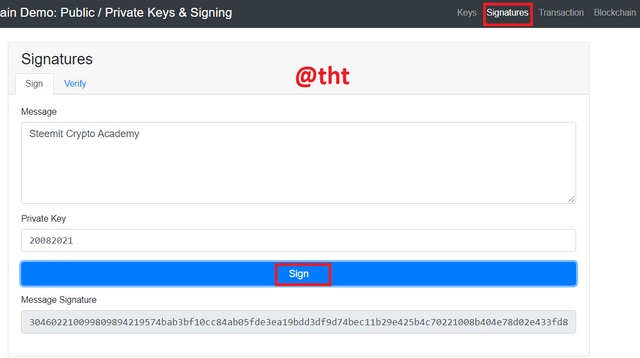
Then I clicked "sign" at the bottom and the message was signed.
Message Signature:
304602210099809894219574bab3bf10cc84ab05fde3ea19bdd3df9d74bec11b29e425b4c70221008b404e78d02e433fd858f3535ce86058b7be0cf9804dec78db3f6237c5d772dd
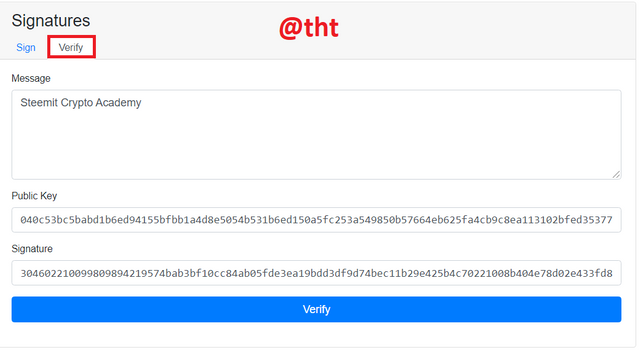
Now the message needs to be validated. In order to verify the message, the Public key that I generated from the Private key (20082021) is written (040c53bc5babd1b6ed94155bfbb1a4d8e5054b531b6ed150a5fc253a549850b57664eb625fa4cb9c8ea113102bfed35377d80825b928b483)
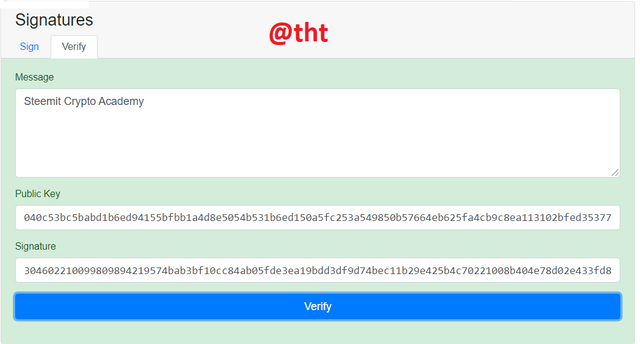
Now I clicked "verify" to confirm its correctness. Everything is fine as the screen is green.
In this way, we understand that the private key and the public key are compatible and are interconnected. It also means that the data has not been altered, but is just like the original.
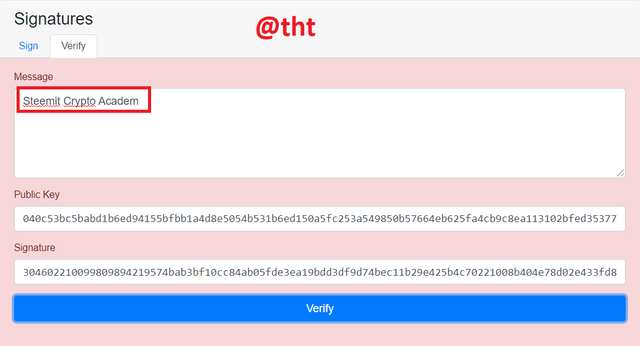
I changed the post above.
Original post: Steemit Crypto Academy
Modified message: Steemit Crypto Academ
I clicked 'verify' to verify. The screen turned red because the message has been changed and is not the same as the original message. Messages are case sensitive, which should be taken into account.
Transactions
Now it's time for transactions. In this section, there is the signing part with the private key and the verification part with the public key.
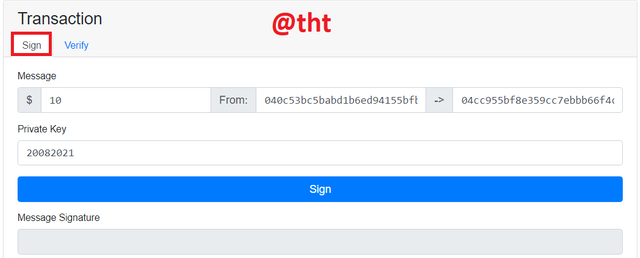
From:
040c53bc5babd1b6ed94155bfbb1a4d8e5054b531b6ed150a5fc253a549850b57664eb625fa4cb9c8ea113102bfed35377d80825b2c8f1bbe92da4f63113e8b8e5
To:
04cc955bf8e359cc7ebbb66f4c2dc616a93e8ba08e93d27996e20299ba92cba9cbd73c2ff46ed27a3727ba09486ba32b5ac35dd20c0adec020536996ca4d9f3d74
Private Key: 20082021
I will transfer $10 worth of assets from one address to another. I will sign it with private key.
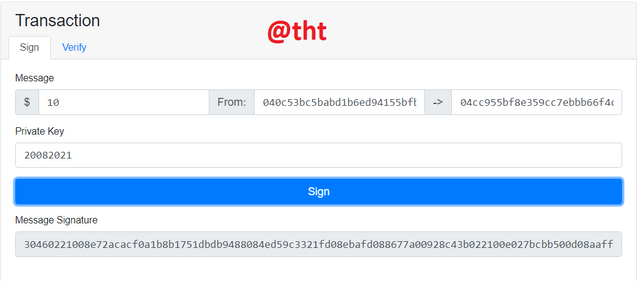
Message Signature:
30460221008e72acacf0a1b8b1751dbdb9488084ed59c3321fd08ebafd088677a00928c43b022100e027bcbb500d08aaffd075cf155d8ae97caa538e5474c0763a1a525049828ea8
I will use it during the validation process.
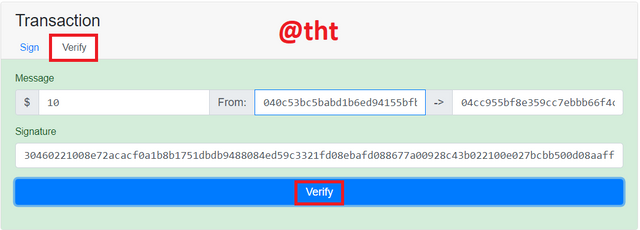
For the verification process, I entered the signature I created with the private key and clicked "verify". The screen turned green. This indicates that the verification process was completed successfully. This concludes that the signing process is done with a private key.
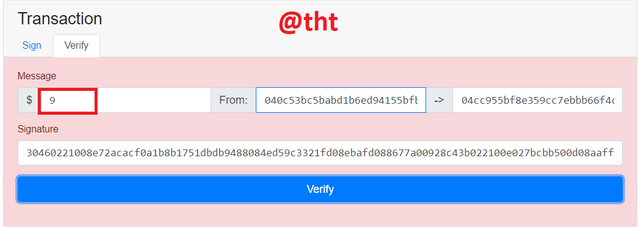
I replaced $10 with $9. The screen turned red. This indicates that some things have been changed.
Blockchain
Now it's Blockchain's turn. We will observe what happens when we change the data contained in the blocks.
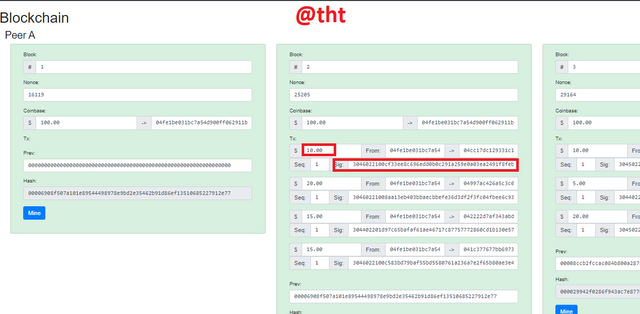
As you can see in Block 2, the screen is green. Everything is OK. I will change the $10 I marked in the screenshot to $20.
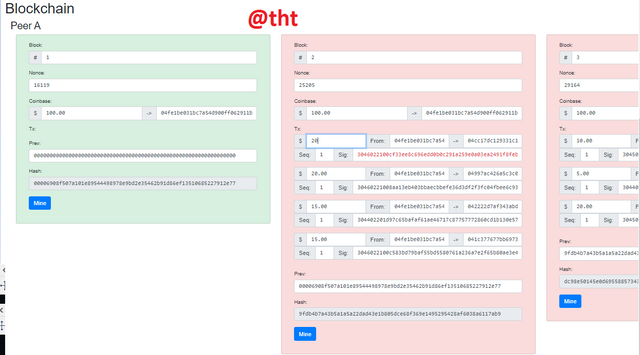
As you can see in the screenshot, the screen has turned red. It gave a warning in the signature section. Indicates that this data has been modified, not original.
Since Block 2 and Block 3 are linked to each other, you can see that Block 3's screen also turns red.
I will click "Mine" to make Block 2 valid.
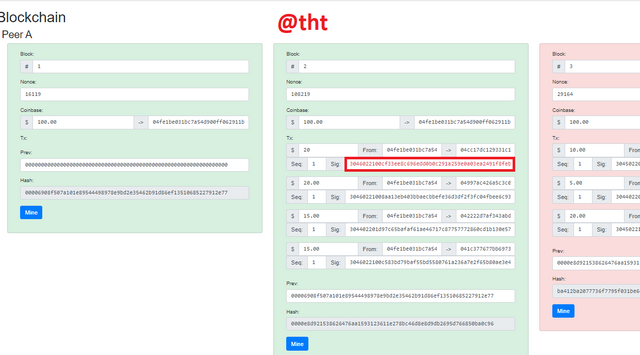
I clicked it and the screen turned green. The Nonce value is different from the previous value. Also, the signature is still red, meaning that this signature is an invalid signature for the data in the block. The color of the blocks after block 2 is also red. The hash of block3 has changed because the data in block2 has changed. For Block 3 and other blocks to turn green, they must be mined one by one.

Conclusion.
One of the ancient times people have done studies on cryptography, but today's technology is more reliable and more modern.
The popularity of blockchain technology today, of course, depends on cryptography. Not only is it popular, but blockchain technology is highly secure and owes it to cryptography.
By means of cryptography, the blockchain has become protected and secure. The change you try to make in any block in blockchains will occur instantly and will be noticed immediately. Therefore, cryptography keeps the blockchain away from dangers.
When we try to generate a blockchain address, the private key is first generated. Then public key. It is possible to generate public key via private key. However, the reverse of this process is not possible. If the reverse of this transaction were possible, the security of our funds would be at stake. We can sign a data with private key. The other party can confirm the accuracy of this, it uses the public key for this.
One of the subjects we touched on in this lesson is the asymmetric and symmetric encryption method. While two keys are used in asymmetric encryption, a single key is used in the symmetric encryption method. Symmetric encryption has been used since ancient times, but asymmetric encryption is more modern and more efficient and secure.
We learned how important a digital signature is. The digital signature is signed with a private key. Without a digital signature, the security of data is compromised.
There are many blockchain wallets available today. In general, it is divided into 2 as cold and hot wallets according to their working capabilities. Hardware wallets are considered the most secure wallets today. These are also expensive and are often used by whales.
Merkle tree is very important in terms of encoding blockchain data efficiently, securely and quickly.
Finally, our practical work on key, signature, transcation and blockchain was very important. We understand that any changes to the data are not possible and this will occur immediately.
Thanks to the professor for this enjoyable lesson. I would love to join your homework as a repeat student next season.

Twitter sharing
https://twitter.com/Steemtht/status/1428667433380888578
Congratulations! Your post has been selected as a daily Steemit truffle! It is listed on rank 16 of all contributions awarded today. You can find the TOP DAILY TRUFFLE PICKS HERE.
I upvoted your contribution because to my mind your post is at least 10 SBD worth and should receive 38 votes. It's now up to the lovely Steemit community to make this come true.
I am
TrufflePig, an Artificial Intelligence Bot that helps minnows and content curators using Machine Learning. If you are curious how I select content, you can find an explanation here!Have a nice day and sincerely yours,

TrufflePig