Crypto Academy / Season 3 / Week 8 - Homework Post for @stream4u | Let's Open the Cryptography
Hey steemians in this post I will be submitting my homework post for professor @stream4u.



Q-1)Explain the Blockchain CryptoGraphy and mention few names which are the Blockchain Platforms (Few names of the Blockchain Platforms)?

Cryptography is a mixture of two words, "Crypt + graphy", where the crypt means hidden or secret and graphy mean writing, so to make it simple cryptography means to write something in a secretive or hidden manner so that only the receiver could read that.
Cryptography is a process of preventing any type of data (whether it's private or public) leakage to the third person or third party that is not involved in the communication by using several techniques.
In the blockchain, cryptography is used to mitigate the 3 limitations and these limitations are:
(a) Privacy: Privacy is the utmost requirement of any user in a blockchain, as anyone in the block gain serving as a node can get the information the sender wants to send to the receiver in the blockchain, so by using cryptography one can encrypt the information that can only be accessed by the receiver.
(b) Reliability: As anyone can get access to the information without cryptography, a node can easily send false information to the receiver by pretending a receiver. By using cryptography, we can tackle this problem as we need keys to encrypt and decrypt the information.
(c) Altering of information: As a node can easily get access to the information without cryptography so a node can also manipulate or alter the data that has been sent by the sender to the receiver. By using cryptography, we can easily tackle the problem as the key is required to encrypt the data and the key is possessed by the real sender so it becomes nearly impossible to change the information sent by the sender using cryptography.
How cryptography works??
(A) Encryption of data: As the name refers, it is the process of making an information secret or hidden or unable to read for anyone except the receiver.
Encryption involves the conversion of information into ciphered information and it can be done using Cipher. Cipher is an algorithm used to convert information into ciphered information.
Note: Ciphered information is a random number or a sequence that consists of bits in it.
(B) Decryption: As the name refers, it is the process of making information unhidden or able to read by using the reverse process of encryption called decryption.
(C) Key: A key plays a crucial role in the encryption and decryption of data in cryptography, a key is used to generate the ciphered information and to convert ciphered information into normal or understandable information.
Some Blockchain platforms
Blockchain has become a necessity when it comes to cryptocurrencies because of decentralised, immutability, security and transparency. So now I will be listing some blockchain platforms and their blockchain explorer so that you can go and explore that blockchain.
Tron Blockchian and Tronscan
Ethereum blockchain and Etherscan
Steem blockchain and SteemScan
Binance blockchain and Binance explorer
Ripple blockchain and Ripple explorer

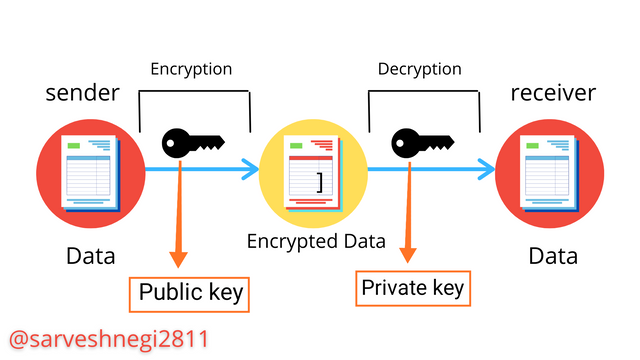
Q-2) Explain the Public Key CryptoGraphy.

Public key cryptography is a method or process of encrypting information with the help of two types of keys, the private key and the public key, these two keys are related to each other as they are required to encrypt and decrypt the information, the point here is that they are only related to each other not a similar or exact copy of each other.
Public keys are open or known to the public as it will be impossible to get access to private keys using public keys and that is the reason that private keys are shared in the network to be used for the encryption of the information.
The private Key must remain unknown to everyone except the owner of the key as the private key will come in handy while decryption of the information sent using the public key.
Working involved in public key cryptography
A sender will use the public key of the receiver that is available or known to everyone on the blockchain to encrypt the information and converting information into ciphered information, now the public key of the receiver got used for the encryption of the information so the private key of the receiver will only be used to decrypt the information.


Advantages of Public-key cryptography
(A) Security: As public-key cryptography requires only the public key of the receiver to encrypt the information and a private key to decrypt the information which is unknown to anyone except the owner of the key, it makes it safe to communicate or send information using public-key cryptography process.
(B) Resistance to alteration in information: A slight difference or alteration in the data or information can make it impossible to decrypt the ciphered information using the private key.

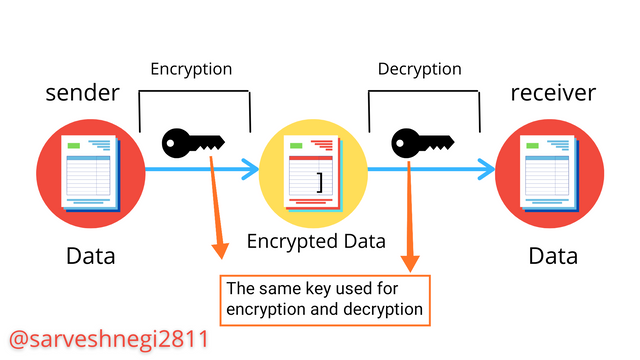
Q-3) Explain the Private Key CryptoGraphy.

Private key cryptography is a method of encrypting and decrypting information using the private key only, there is only one key involved here unlike public-key cryptography which involves the use of two keys. The sender and the receiver both possess the same key that will be used for the encryption and decryption of the data air information.
The private Key must remain unknown to everyone except the sender and receiver of the information as the private key will come in handy while encryption and decryption of the information.
Private key plays a crucial role in maintaining a wallet and broadcasting a transaction by signing a transaction that makes the sharing of the private key more forbidden with the third party.
Working involved in the private key cryptography
A sender will use the private key that is known to him/her or the receiver only to encrypt the information and converting information into ciphered information, after sending ciphered information to the receiver, the sender must share the private key that was used to encrypt the information with the receiver so that the receiver can use that private key to decrypt the information and get access to it.


Advantage of private key cryptography
The advantage of private key cryptography is the security it provides to its user by restricting the third party to get access to the information, only the sender and the receiver with the same private key that was involved in the encryption and of information can have access to the information by decrypting the ciphered information.
Disadvantage of private key cryptography
The biggest disadvantage of private cryptography is to use different keys to communicate with different people, so if I have to talk or communicate to 50 people I must possess 50 keys so that only I and the receiver have the access to information which makes it is a very difficult job to keep tabs on 50 keys and use them while communicating.

Q-4)Explain the Digital Signatures CryptoGraphy and what is Singing Of Transaction/Message?

When we submit a check to the bank or give a check to someone else, it requires the signature of the check holder or account holder so that we can know who is spending money.
The same is the case here, Digital signature cryptography is a method or process by which one can check the authenticity or originality of a digital transaction or information that took place in a blockchain.
Signing algorithm is used to generate a hash value and then encrypt that hash value using the private key, after the encryption of hash value by the private key, the information is attached and sent along with it, now this group of encrypted hash and information are known as a digital signature.
How digital signature cryptography works?
As we all know that asymmetric cryptography requires two types of key, the private key and the public key that is related to each other, so the sender uses his private key and the receiver's public key to encrypt the data and converting the information or data into ciphered information, now receiver will only be able to decrypt the information by receiver's private key and sender's public key if and only if the information is signed by the sender using his private key.
(A) Originality or Authenticity of information: As digital signature cryptography requires both the public and the private key, the real sender of information can be easily found by using the public key of the sender.
(B) Resistance to alteration of information: As it will require the private key of either the sender or receiver to decrypt the message it makes the information difficult to prone to alteration.
By signing a transaction/message, a sender is giving proof that he/she was the one who sends the transaction/message to maintain authenticity, originality and to resist alteration of information.
How does a signing of a transaction happen?
I will be listing the steps by which signing of a transaction can be understood easily:
(A) A hash has been created corresponding to the transaction/message that the sender wants to send using a signing algorithm.
(B) Now that hash that is corresponding to the transaction/message gets encrypted by using the private key of the sender.
(C) Now after encrypting the hash, a transaction/message is sent in conjunction with the hash that is encrypted by the private key of the sender.
(D) Now the transaction/message has been broadcasted on the network and the verifier or receiver will verify the digital signature of the sender.
(E) Now verifier or received will verify the transaction/message using the public key of the sender by decrypting the hash.
(F) A message direct will appear to the verifier that will produce a hash value related to the sender's information.
(G) If the hash value of the sender's hash and the verifier or receiver's hash is equal then it can be said that the transaction/message was sent by the real sender.
(H) If the hash value of sender and receiver doesn't match then someone is pretending to be the sender and the digital signature will not allow the transaction/message to decrypt.
So I have listed all the steps included in the signing, broadcasting and verifying a transaction in a blockchain and how does a transaction/message get signed?

Q-5) Explain what is Symmetric and Asymmetric cryptography?

As the name suggests, symmetric cryptography requires the symmetric key or the same key to encrypt and decrypt information. The sender and the receiver must possess the same key to communicate with each other in the blockchain via symmetric cryptography.
Working of Symmetric cryptography
In symmetric cryptography, the sender encrypts the information using a key and converts the information into ciphered information that is unable to understand. Now after sending that particular information the sender will send the same key that he/she used for encrypting information to the receiver via another mode than blockchain. Now if the receiver possesses the same key that was used by the sender to encrypt the data, he or she can easily decrypt the data using that key and get access to the information.



For instance, I want to send a message to professorstream4u and I encrypted that message using key "K1" so if professorstream4u possesses the key "K1", he can easily decipher my message and get access to my message. Now if I want to send a different message to a different guy will I use the same key??, so the answer to this question is no if I share the same key with everyone else, anyone can read the messages sent to the other receiver so to tackle that we have to send different information to different people using different keys.
Advantage of Symmetric cryptography
The advantage of symmetric cryptography is the security it provides to its user by restricting the third party to get access to the information, only the sender and the receiver with the same key that was involved in the encryption of information can have access to the information.
Disadvantage of Symmetric cryptography
The biggest disadvantage of symmetric cryptography is to use different keys to communicate with different people, so if I have to talk or communicate to 100 people I must have 100 keys so that only I and the receiver have the access to information so it is a very difficult job to keep tabs on 100 keys and use them while communicating.
Unlike symmetric cryptography in which we need the same key to encrypt and decrypt the information, asymmetric cryptography requires two types of key, the public key and private key and either of them can be used to encrypt the information but the decryption of information will only happen with the other key that was not involved in the encryption process.
Private key: A key that is kept secret or unknown to other people except for the owner of the key, this key can use used to encrypt and decrypt the information in asymmetric cryptography.
Public key: A key that is kept known to other people or known to the public or everyone in the blockchain, this key can use used to encrypt and decrypt the information in asymmetric cryptography.
Working of Asymmetric cryptography
In asymmetric cryptography, the sender encrypts the information with the public key of the receiver and convert the information into ciphered information that can be seen by anyone but can't be deciphered or decrypted by anyone except the receiver. Now after sending that particular information, the receiver can use his/her private key that is possessed by only him/her to decrypt the information.



For instance, I want to send a message to professorstream4u and I used the public key of professorstream4y to encrypt the data so to decrypt the data professorstream4u has to use his private key that only he possesses by doing that I can send the information using the public key of professor and professor can decrypt the data using his private key. Now if I have to send different information to a different user I can use his/her public key to encrypt the data and in turn, he/she can use his/her private key to decrypt the information and get access to it.
Advantages of asymmetric cryptography
The advantage of asymmetric cryptography is the security it provides to its user by restricting the third party to get access to the information, only the sender and the receiver with the public and private key that was involved in the encryption and decryption of information can have access to the information.
Another advantage of asymmetric cryptography is that it tackles the problem that is faced by the users in symmetric cryptography to use different keys to communicate with different people.

Q-6) How Blockchain Wallets CryptoGraphy works and explains the available types of Crypto Wallets?

Blockchain wallet, as the name, suggests, is a digital wallet that stores assets related to that particular blockchain but as we all are familiar with crypto assets, we will be talking about all the relevant wallet cryptography of crypto assets.
When an individual joins a blockchain, he/she possesses a digital wallet in which he/she will carry his/her asset. You may have also seen when you entered the Steemit, you downloaded a file that contains all the keys related to the functioning of the wallet.
In the same file, you must have seen Tron public key and Tron private key, so these two keys public key and private key are the cruces of a wallet.
Elements required in blockchain wallet cryptography
(1) Private key: Private key as the name suggests rains private as this key will sign the transaction which is required to send or transfer the assets.
The private key is a mixture of randomly generated alphanumeric numbers and with the help of a private key, one can recover his/her account in case of losing his phone or laptop.
(2) Public key: As I have already mentioned in the above questions, the private key and the public key are related to each other and the process of verifying the transaction is incomplete without having both the keys.
The public key is also a randomly generated number that is related to the private key such that the whole process of signing and verifying the transaction is incomplete if the one is lost. The public key is necessary for the verification of the transaction/message by verifying the digital signature by the nodes or miners.
(3) Address of wallet: You can only go to your friend's house if you know his/her address and without knowing the address you might go to the wrong place.
The address of the wallet is also a randomly generated number that can't be the same in a blockchain. The main purpose served by the address of the wallet is by sending the address to the receiver to receive funds/assets.
Working involved in Blockchain wallet cryptography
For instance, the sender wants to send 10 BTC to another account for which he needs his/her private key to encrypt the transaction and signing the transaction after signing the transaction the sender will need the receiver's address at which he wants to send BTC, now a node or a miner that possesses the public key of the sender will verify the authenticity of the transaction and the sender and then broadcast it to network to the receiver, now the receiver that has the same address the sender used will receive 10 BTC.
There are 2 types of crypto wallets:
(A) Hot wallet
(B) Cold wallet
| Hot wallet | Cold wallet |
|---|---|
| Hot wallets are wallets that need an internet connection or get operated via the internet somehow. | Cold wallet does not require any internet connection to perform its function. |
| Hot wallet | Cold wallet |
|---|---|
| Hot wallets are less secure when compared to a cold wallets due to the requirement for the internet and that is the reason that makes them prone or vulnerable to hacking. | Cold wallets don't require any internet connection as they don't require any internet connection. |
| Hot wallet | Cold wallet |
|---|---|
| A hot wallet is more resilient and accessible as we can use a hot wallet anywhere in the world because of an internet connection. | A cold wallet is less resilient than a hot wallet as we have to carry a cold wallet with us every time. |
Now under the hot wallet and cold wallet category there comes three types of wallets:
(1) Software wallet: As the name suggests they are software wallets and can get operated via the internet. There are many software wallets but some are very popular and these wallets are:
(1a) Web wallet: As the name suggests it requires a web browser to get operated and we don't have to download a wallet on our mobile phone or computer or laptop but in turn out keys got saved in the web browser and that leads to a half control of someone over someone's asset.
(1b) Desktop wallet: As the name suggests it requires a desktop to operate in so we have to download that wallet to our desktop or laptop, as we do for Metamask. The owner of the wallet is the sole holder of the keys that are required to operate a wallet.
(1c) Mobile wallets: As the name suggests it requires a mobile phone to operate in so we have to download that wallet to our mobile phone. The owner of the wallet is the sole holder of the keys that are required to operate a wallet. It is a very resilient wallet as it can be taken and accessed anywhere in the world.
(2) Hardware wallet: As the name suggests, hardware wallets require hardware to store information relevant to the wallet. It falls into the category of cold wallet.
Being a cold wallet it is less vulnerable or more secure to hacking as it is not connected to the internet.
(3) Paper wallet: As the name suggests, all the relevant information to the wallet is stored in the paper. It also falls under the category of cold wallet as this wallet doesn't have access to the internet.
But being only a piece of paper it might get lost or stolen so despite being a cold wallet it is more vulnerable or provides less security.

Q-7) What is the Merkle trees and What its importance in blockchain?

As the name suggests, the Merkel tree is a tree-shaped structure that contains all the data for verifying and identifying a specific transaction.
Merkel tree must be a binary tree that means the no of hashes the Merkel tree contains must be even or multiple of two.
After going for an example we must know what hash is.
Hash is a 255-bit number and unique that means a hash can't be repeated in a blockchain, hashes are crucial to finding a transaction in a blockchain. previous task
Now, for instance, there is a block that contains 8 transactions and we know that every transaction has a different hash of its own, so for verifying transactions and get the hash value of the block we can not verify each transaction one by one, so we will just combine the hashes of transactions till we get a root hash that serves as a hash for the block.
Who discovered Merkel Tree?
Ralph Merkel was the one who invented or discovered the Merkel tree in 1979(patent), as you can see the tree has got its name.
Components of Merkel tree and how binary merkel tree works?
There are three components of the Merkel tree:
(A) Leaves: Leaves denotes the hashing pair of two transactions in a block, for instance, if a block contains 8 transactions(T1, T2, T3, T4, T5, T6, T7, T8T8), so the leaves will represent the combined hash of (T1T2, T3T4, T5T6, T7T8).
(B) Branches: Branches denotes the hashing pair of the leaves, for instance, if a block contains 8 transactions(T1, T2, T3, T4, T5, T6, T7, T8T8), so the leaves will represent the combined hash of (T1T2, T3T4, T5T6, T7T8) and the branches will be represented like (T1T2T3T4, T5T6T7T8).
(C) Root hash: Root hash represents the main hash of the block or the hash that contains all the data of that block needed to verify transactions. for instance, if a block contains 8 transactions(T1, T2, T3, T4, T5, T6, T7, T8T8), so the leaves will represent the combined hash of (T1T2, T3T4, T5T6, T7T8) and the branches will be represented like (T1T2T3T4, T5T6T7T8) and try the main root or root hash will be represented by (T1T3T3T4T5T6T7T8).
Merkel tree with odd no of transactions
As I mentioned above, the Merkel tree is a binary tree that means the number of hash or transactions must be in the even number but what about when a block contains an odd no of transactions.

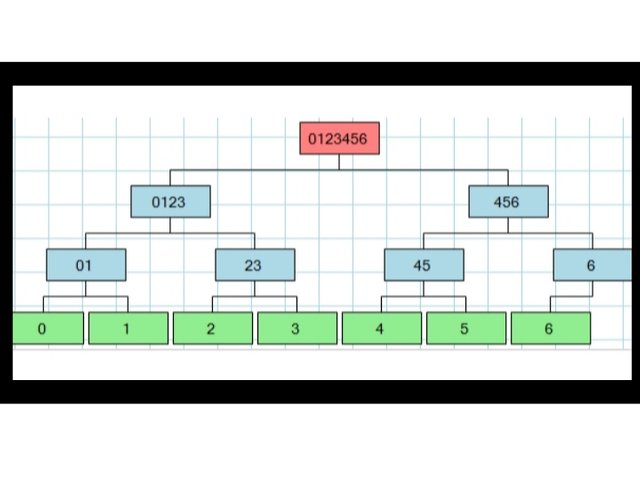

For instance, there are 7 transactions in the block so there must be 7 hashes that are T0, T1, T2, T3, T4, T5, T6 you can see that number of transactions is odd.
(a) Leaves for 7 transactions: Leaves represents the combined hash of the transaction hash so the leaves will be T0T1, T2T3, T4T5, T6T6 you can see that the hash of transaction 6 got repeated due to lack of pair.
(b) Branches: Branches represents the combined hash of leaves so the branches will be T0T1T2T3, T4T5T6T6, you can see that hash of transaction 6 got repeated and get added to branch.
(c) Root hash: Root hash represents the main hash of the block or combined hash of the branches, so the root hash will be T0T1T2T3T4T5T6T6, it can be seen that due to lack of pair for transaction 6 it gets repeated and reflects repeated on the root hash.
(1) Verification: It is the foremost thing and the main purpose that has been served by the Merkel tree.
Without the Merkel tree, it will be very hard for the nodes or miners to verify a single transaction in the block so there comes the Merkel tree into play to verify all the transactions in a block at once by using root hash.
How can we verify a transaction in the Merkel tree?
I am taking an example of 8 transactions that took place in a block.

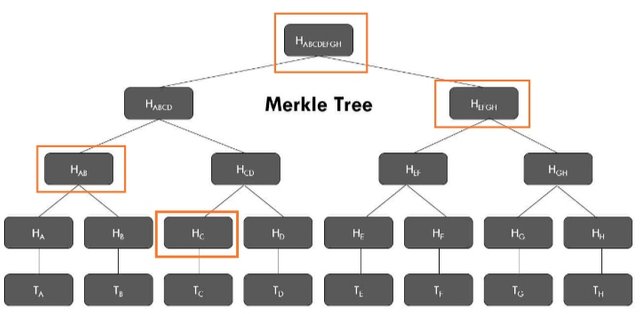

I will be verifying Transaction D, so the steps to verify transaction D are as follows:
(1) Verify the pair of the transaction D that is transaction C.
(2) Then verify the leaf of the pair of transaction A and transaction B.
(3) Then verify the branch that combines the pair of leaves Transaction EF and Transaction GH that is Transaction EFGH.
(4) And finally verify the root hash of the Merkel tree, if the root hash contains the data of transaction D then the transaction D is verified and available in the block.
(2) Save storage as well as time: As with the help of the Merkel tree we can easily verify any transaction without checking all the transactions one by one it saves our time and if we don't have to check every single transaction then we don't have to save the hashes for any transaction that leads to the saving of the storage space.
(3) Immutability: The data which once gets stored in the root hash because of the combination of the hashes of transaction can not be altered as if it was altered the hash of the whole block will get changed leading to an invalid block.

Q-8) Practical + Theory, do some practical research, study on Blockchain Demo: Public / Private Keys & Signing and then explain the functionality of Key, Signature, Transaction, Blockchain with proper screenshots of yours practical. (Do study well for this topic)

In the above questions, we talked about keys very much but to be more precise or brief, in the topic of public-key cryptography and asymmetric cryptography we used two different keys to encrypt and decrypt the information.
Public key and Private key are related to each other and if one gets changed the other one gets changed automatically
To prove my statement i opened Blockchain demo

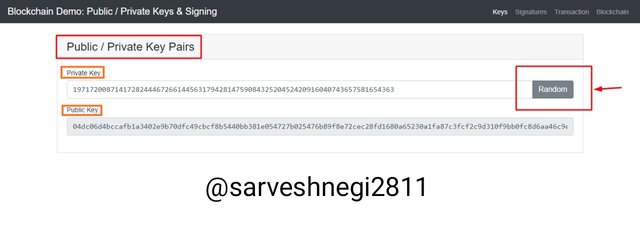

Public key: 04dc06d4bccafb1a3402e9b70dfc49cbcf8b5440bb381e054727b025476b89f8e72cec28fd1680a65230a1fa87c3fcf2c9d310f9bb0fc8d6aa46c9e8e2f73548df
Private key corresponding to public key: 19717200871417282444672661445631794281475908432520452420916040743657581654363
Now to proof my statement i will change my private key a kittle but and then see the change in public key as Public key and Private key are related to each other and if one gets changed the other one gets changed automatically

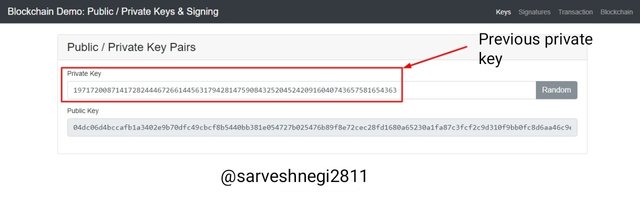
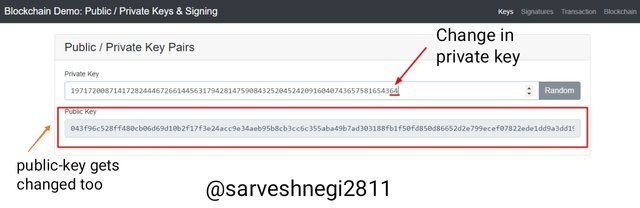

You can see in the screenshots above that i just changed the last digit of the previous private key from 63 to 64 and a new corresponding value of public key can be seen.
Private key changed: 19717200871417282444672661445631794281475908432520452420916040743657581654364
Public key corresponding to private key: 043f96c528ff480cb06d69d10b2f17f3e24acc9e34aeb95b8cb3cc6c355aba49b7ad303188fb1f50fd850d86652d2e799ecef07822ede1dd9a3dd194f9913bba7f
Now to further prove my point i will be putting a random private key that is 12345 and now i will be looking for the change in the public key.

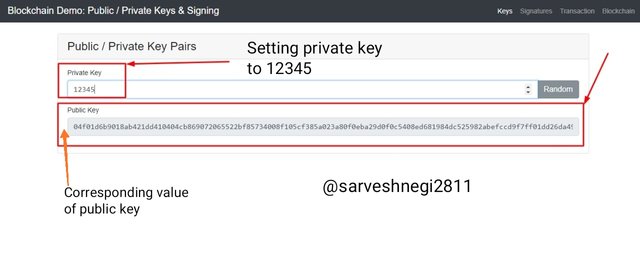

You can see that i set my private key to 12345 and tye public key gets changed too with repesct to my private key.
Private key changed: 12345
Public key corresponding to private key: 04f01d6b9018ab421dd410404cb869072065522bf85734008f105cf385a023a80f0eba29d0f0c5408ed681984dc525982abefccd9f7ff01dd26da4999cf3f6a295
So I have shown you how key vary with the other key in a blockchain with the help of screenshots and changing private key to see change in public key.
(1) Sign
As we talked about the digital signatures in the previous questions that with the help of digital signature one can easily know the sender and the sender and the authenticity of the message/transaction.
When we read about digital signature cryptography we came to know that we need a private key and hash to sign a transaction and then broadcast it to network by miners or nodes using public key of the user for verifying authenticity of the transaction/message. So I will be showing you the same with the help of Blockchain demo signature

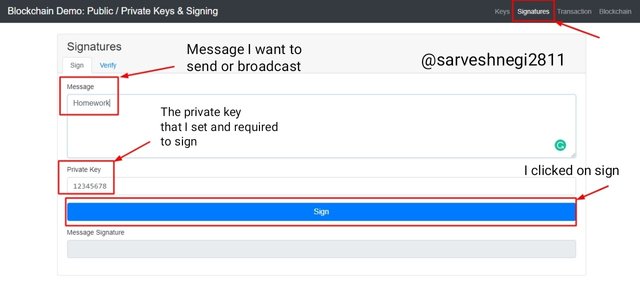

In the above screenshot you can see that I set my private key as 12345678 and the message I want to send is Homework.
This is the process of signing a transaction now I just have to click on sign so that my message signature gets generated. Then finally I clicked on sign.

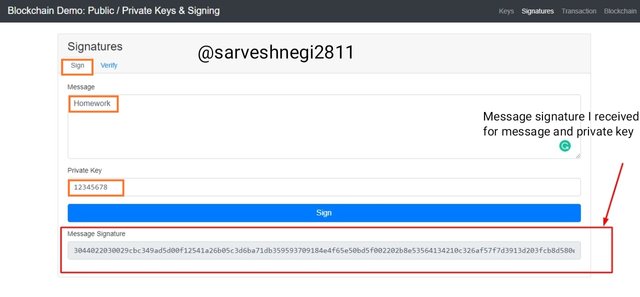

So I used,
Message: Homework
Private key: 12345678
Message signature I got: 3044022030029cbc349ad5d00f12541a26b05c3d6ba71db359593709184e4f65e50bd5f002202b8e53564134210c326af57f7d3913d203fcb8d580ecda85bd33f176aea221f4
So this was the process of signing a transaction but whole process isn't complete yet we have to verify the message.
(2) Verify
Verification means verifying the authenticity of the message by using the public key of the sender if the message is sent by the sender then public key of the sender will verify the message and if sender hasn't send the message then the public key will not be able to verify the message.
So I will show you how a message get verified by the use of public key.

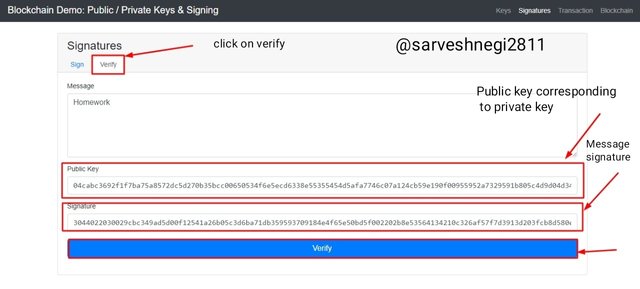

I clicked on verify option on the top to verify the authenticity of the message and as soon as I clicked on the verify option my public key corresponding to the private key I set got filled along with the message signature in the required places.
Public key corresponding to 12345678 private key: 04cabc3692f1f7ba75a8572dc5d270b35bcc00650534f6e5ecd6338e55355454d5afa7746c07a124cb59e190f00955952a7329591b805c4d9d04d34abe8a803a74
Message signature: 3044022030029cbc349ad5d00f12541a26b05c3d6ba71db359593709184e4f65e50bd5f002202b8e53564134210c326af57f7d3913d203fcb8d580ecda85bd33f176aea221f4
Now I just have to click on verify to verify the authenticity of the message.

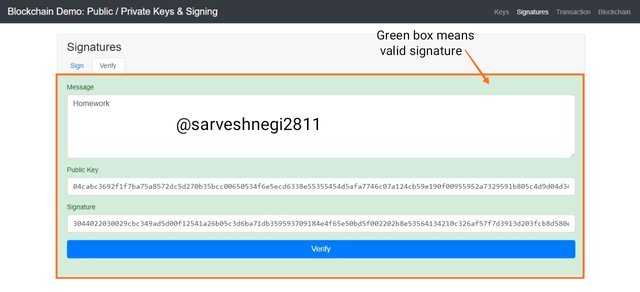

A green box denotes a verified or valid signature that means my message signature and public key was same as the sender.
In asymmetric cryptography, we use public key of the receiver to send information so that only receiver with his private jeet can see the transaction/message.
Transaction requires signing and verifying and for signing and verifying we need Public key and Private key along with the address of receiver.
(1) Transaction signing
I opened Blockchain demo transaction and saw what to do in transaction signing.

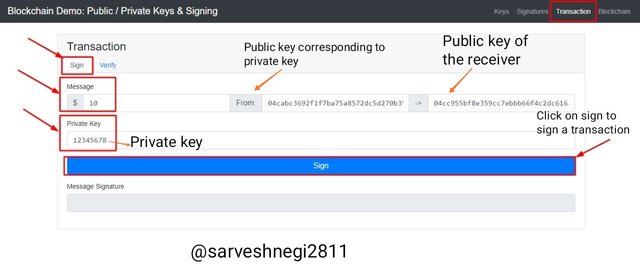

In the above screenshot it can be seen that I put message amount $10 and set my private key to 12345678 you can see that the corresponding public key to my private key is same as in 2nd section of signature.
Amount/message: $10
Private key: 12345678
Public key corresponding to 12345678 private key: 04cabc3692f1f7ba75a8572dc5d270b35bcc00650534f6e5ecd6338e55355454d5afa7746c07a124cb59e190f00955952a7329591b805c4d9d04d34abe8a803a74
Now I just have to click on sign button to get message signature and sign my transaction.

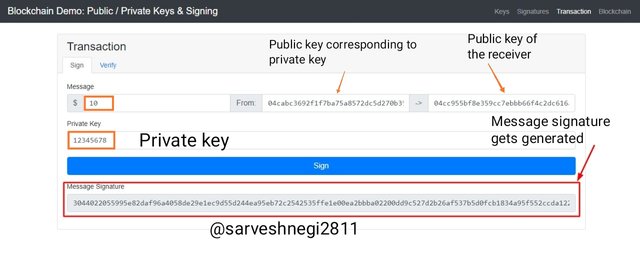

For using,
Amount/message: $10
Private key: 12345678
Public key corresponding to 12345678 private key: 04cabc3692f1f7ba75a8572dc5d270b35bcc00650534f6e5ecd6338e55355454d5afa7746c07a124cb59e190f00955952a7329591b805c4d9d04d34abe8a803a74
The message signature I got is: 3044022055995e82daf96a4058de29e1ec9d55d244ea95eb72c2542535ffe1e00ea2bbba02200dd9c527d2b26af537b5d0fcb1834a95f552ccda122be9c0dcab5584a823ac94
Now this message signature will help in verifying the transaction as our signing of transaction is completed.
(2) Transaction verification:
Verification is done by the miners or node to add transaction in the block. So for doing this I clicked the verify button.
For verification the things we require is public key and message signature, so I will be putting the corresponding public key to my private key and message signature.

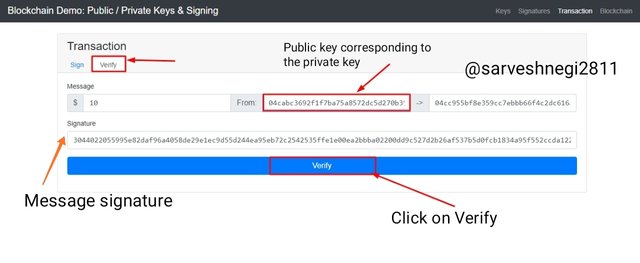

You can see my,
Message signature : 3044022055995e82daf96a4058de29e1ec9d55d244ea95eb72c2542535ffe1e00ea2bbba02200dd9c527d2b26af537b5d0fcb1834a95f552ccda122be9c0dcab5584a823ac94
Public key corresponding to 12345678 private key: 04cabc3692f1f7ba75a8572dc5d270b35bcc00650534f6e5ecd6338e55355454d5afa7746c07a124cb59e190f00955952a7329591b805c4d9d04d34abe8a803a74
Now I just have to click on the verify option.

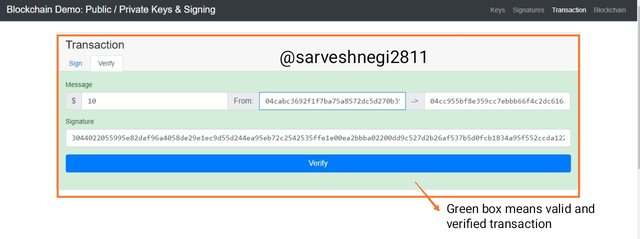

You can see a green box that denotes a valid and verifies transaction that is added to a block.
As we all know that,
A block is an entity that contains the information, this information could be everything but in the case of cryptocurrency, a block contains all the relevant information regarding transactions(ex: address, hash, parent hash or previous hash etc.) that are taking place in that block. Now when we join more than one block it constitutes a chain called a blockchain. previous task
Due to immutable nature of blockchain we can't alter a little thing in a block as if we do such things all the blocks after that altered block and the altered block will be considered as invalid block.
I opened Blockchain demo and further opened the blockchain section.

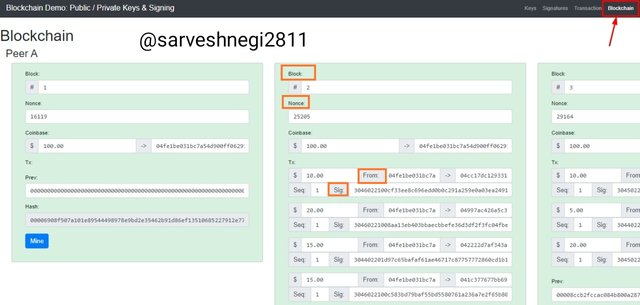

You can see that all the blocks are arranged serially via hash valus and are green in colour that shows all the blocks are valid.
You can see the block no 2 with a nonce value of 25205
And there are also transactions that took place in block 2 with the information like public key of the receiver and the sender and message signature.
Now we will check the immutability of blockchain by altering the message or amount.

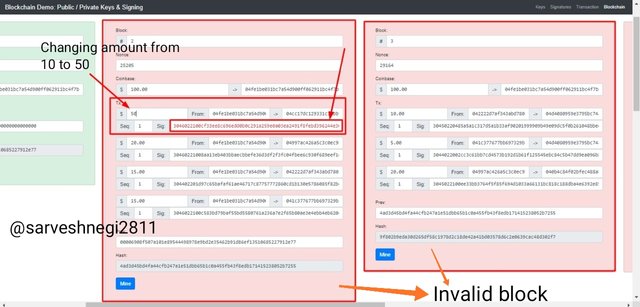

You can see that I have changed the value or amount from 10 to 50.
So by just changing the amount from 10 to 50 I changed the hash of the block no 2 and by changing the hash of of block 2 its nonce value didn't match the changed hash thus resulting in the invalidation the block number 2, now block no 3 is added to the block no 2 by the previous hash of block 2 but by changing the amount we changed the hash of block 2 which is not the previous hash for block 3 this resulting in the invalidation of block 3 too.
Now the blockchain after block 2 and block 2 are invalid and we have to mine them to make them valid.

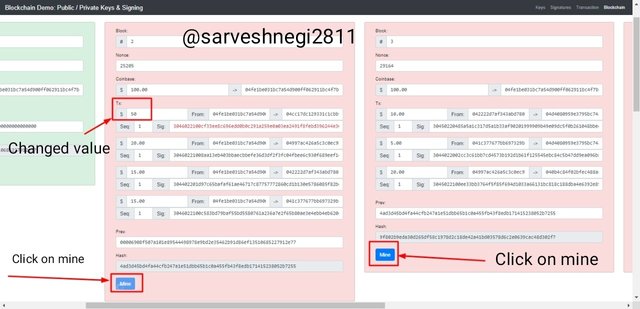

In the above screenshot you can see that both the blocks 2 and 3 are invalid because of altering data in the block 2 and I clicked on the mine button to get correct Nonce value for the altered block and the following blocks.

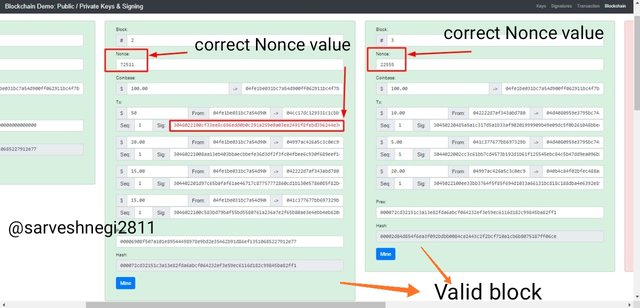

Block no 2 with a nonce value of 25205 without alteration of amount
Block no 2 with a nonce value of 72511 with alteration of amount
Block no 3 with a nonce value of 29164 without alteration of amount
Block no 3 with a nonce value of 22555 with alteration of amount
It is clear that by mining the nonce value gets changed and the blocks get validated, so for a correct Nonce value we have to done mining and the hash of the block 2 becomes the previous hash for block 3 and thus both block 2 and 3 gets valid.
The message signature is still in red colour that means it is invalid, to make it valid we have to go to transaction section and then put amount to 50 and then get a message signature and then put it here in the altered block 2 of blockchain section.

Q-9) Conclusion

In a nutshell, cryptography is the method by which we can keep our assets and information safe by using many methods and many blockchains use cryptography methods to attain security, authenticity and privacy in the blockchain.
Public key cryptography can be made more secure if we use the receiver's public key to encrypt the data so that the data get encrypted only by using the receiver's private key.
Private key cryptography can be done between the people who trust each other as they are sharing the same private key that is involved in sending funds and transferring funds, so it would be better if we use private key cryptography with someone whom we trust.
A digital signature is a way to know the real sender of the message or data by using a public key and it also helps in checking the authenticity of the message by using a public key too.
Symmetric and asymmetric key cryptography both are good methods to rely on, as symmetric-key cryptography can be done with someone we trust and provides us with security and the same is the case in asymmetric case it provides us security too but we use two different keys one to encrypt the information and other to decrypt the information.
Sending and transferring funds require a private key, the public key and the address of the receiver, it is a two-step process that includes signing and verifying if the transaction using the private key and public key.
Merkel tree helps us by combining the hashes of multiple transactions and providing a single root hash that can verify the transaction in the block that leads to the saving of time and storage space.
And finally, I did practical with keys/blockchain/transaction/signature and was able to soot all the important information along with identifying the reason for valid and invalid blocks.

Note: All the taken things are referenced to their sources and i have used some points from my previous task
Thank you
That was all from my side
For the attention of the professor @stream4u.
Your explanations are very detailed and the structure of writing is also very neat.
It's not that good it can be further improved, btw thanks for the complement and reading the homework post.