Crypto Academy / Season 3 / Week 8 - Homework Post for [@stream4u] **LET'S OPEN CRYPTOGRAPHY** BY @sammylinks
Hello everyone,
I'm very delighted to participate in this week's lecture. This week's class mentored by our crypto-professor @stream4u focused on "WHAT'S CRYPTOGRAPHY AND IT'S SIGNIFICANCE OF BLOCKCHAIN TECHNOLOGY".
This post is designed based on the various homework tasks given at the end of the class as stated below:
- EXPLAIN THE BLOCKCHAIN CRYPTOGRAPHY AND SOME NAMES OF THE BLOCKCHAIN PLATFORMS
- WHAT'S THE PUBLIC KEYS CRYPTOGRAPHY
- WHAT'S THE PRIVATE KEYS CRYPTOGRAPHY
- EXPLAIN THE DIGITAL SIGNATURE CRYPTOGRAPHY AND WHAT'S THE SIGNING OF TRANSACTION/MESSAGE
- EXPLAIN WHAT'S SYMMETRIC AND ASYMMETRIC CRYPTOGRAPHY
- HOW BLOCKCHAIN WALLET CRYPTOGRAPHY WORKS AND TYPES OF CRYPTO'S WALLET
- WHAT'S MERKLE TREE AND ITS IMPORTANCE IN BLOCKCHAIN
- PRACTICAL + THEORY, DO SOME RESEARCH STUDY ON BLOCKCHAIN DEMO: PUBLIC/PRIVATE KEYS & SIGNINGS AND EXPLAIN THE FUNCTIONALITIES OF KEYS, SIGNATURE, TRANSACTION, BLOCKCHAIN WITH PROPER SCREENSHOTS
- CONCLUSION

EXPLAIN THE BLOCKCHAIN CRYPTOGRAPHY AND SOME NAMES OF THE BLOCKCHAIN PLATFORMS
The term "CRYPTOGRAPHY" is a system of securing the information in the communication channel with methmatical codes. This methmatical codes converts plaintext which are understandable by humans into unintelligible but machine coded language and vice versa to secure the information from undesired recipients and for user's authentication (i.e, the process of encryption and decryption).
Etymologically, Cryptography comes from two Greek words; krypto meaning hidden and graph meaning words/expression of thoughts. Therefore, in simple terms, Cryptography means a hidden/secured ways of expressing thought (i.e, information) between intended individuals. This means of secured communication have evolved over the years. It was dated back to the system of Egyptians writing that involves pictures and signs to communicate within themselves thereby securing their business records. Alexander the Great adopted a systematic order of communicating with his Generals thereby protecting their military Strategies and empire and other examples over years But now, the invention of computers with strongly mathematical/algorithm sequence have developed codes to secure informations too.
In Blockchain, a chunk of information of various types are verified as blocks which are linked together strongly but will be securely transmitted within a communication channel involving the sender and intended recipient via cryptographic functions. The strong linkage of the verified blocks of information and secured means of transmission of those information are achievable via the hashing functions of the cryptography.
THE SIGNIFICANCE OF CRYPTOGRAPHY TOWARDS BLOCKCHAIN TECHNOLOGY.
- CONFIDENTIALITY
With the means of cryptography, only intended recipient of the message will be able to view the message and undesired audience can't read them.
- INTEGRITY
With cryptographic functions, Data can't be manipulated or altered, once verified. This engeared reliability over the communication route and the people involved.
- AUTHENTICATION
The sender/recipient of the message are validated and known as well as the origin/destinations of communication channel are known too.
- NON-REPUBIATION
Once the Data is created, both sender and receiver can't deny their involvement.
NAMES OF BLOCKCHAIN PLATFORMS
Over time, there are many blockchain platforms/networks been developed with several purposes and their consensus mechanism are established to solve a particular challenge noticed. Some of those platforms are
- ETHEREUM
This is a decentralized blockchain platforms that run with several smart contracts. It is been developed by Ethereum Foundation. It's native coin is ether, which have second largest market capitalization after Bitcoin.
Consensus mechanism: Proof Of Stake (POS).
Language: serpent etc.
Website: www.ethereum.org
- EOS
This is one of the wonderful open-source blockchain platform that's developed by EOSIO. It is a highly decentralized network that provides a great platform for highly powered decentralized applications.
Consensus mechanism: Delegated Proof Of Stake (dPOS).
Language: C++ etc.
Website: www.eso.io
- KOMODO
A Highly efficient Blockchain network that provides end to end blockchain technology solutions. It is very secure, scalable and fully interoperable network.
Consensus mechanism: Delayed Proof Of Work (dPOW).
Language: c++ etc.
Website: komodoplatform.com
- LISK
This Blockchain platform merged the Blockchain technology with the Java world through Sidechain Development Kit (SDK).
Consensus mechanism: Delegated Proof Of Stake (dPOS).
Language: JavaScript
Website: www.lisk.io

WHAT'S THE PUBLIC KEYS CRYPTOGRAPHY
As the name implies, Public keys are generally shared with others. When known publicly, it does not compromise the cryptographically protection of the message. Rather it is best way to validate the sender/receiver's identities. They are alphanumerical letters used to authenticate the sender and receiver of the message cryptographically.
However, The cryptographic functions of encryption and decryption process from the sender and receiver involves the use of keys. The sender encrypted messages with the well known public key of the intended recipient of this message. The public key of an individual serves as it's identities for message to be encrypted and securely transmitted within the communication channel. It can only be decrypted by the intended recipient's private key. This set of key will matched with the public key of the intended recipient used for the encryption process for easy accessibility (i.e, decryption) to the message.

WHAT'S THE PRIVATE KEYS CRYPTOGRAPHY
This is the set of cryptographic hashed strings of alphanumerical letters used for the authenticity of the account. It's not to be disclosed to another person. Owning of this key can compromise the CONFIDENTIALITY and other great tenets of cryptography as it will exposed the encrypted messages to intended recipients.
Also known as a hidden key, Private key can only be shared with keys generators in order to generate other keys like the public, actions and memo etc. Having access to the private key makes the person "presumed owner" of the account on the Blockchain.
Private keys can be used both for data encryption and decryption process. Its very lengthy in the number of bits sampled and difficult to second-guessed because it's randomly generated. With the data are secured and difficult for hackers.

EXPLAIN THE DIGITAL SIGNATURE CRYPTOGRAPHY AND WHAT'S THE SIGNING OF TRANSACTION/MESSAGE
Postal stamps are affixed on the parcel from the sender to show that the sender have completed the prerequisite requirements for his/her mail to be couriered. It is a standard set in several postal agencies of several countries. Without it, the mail and it's sender will be trusted/authenticated and the recipient will lose his/her integrity on the postal agencies when receive a parcel/mail without a postal stamps.
Digital signature works exactly like postal stamps, it is a standard set on cryptography that any encrypted/decrypted message must be duly signed digitally. It authenticate the sender and improve the integrity level of the recipients.
Digital signature are cryptographic functions that validate the identity of the sender, ascertaining his existence and awareness of his involvement in the message encrypted with the public key of the intended recipient and confirm the ability of the intended recipient's private key to decrypt the message. The confirmation under digital signature tells the recipient that the sender's identities is known/validated and the message is valid.
HOW DIGITAL SIGNATURE WORKS
Digital signature works in two basic ways.SIGNING OF TRANSACTION/MESSAGE
The sender/author of the message/transaction must signs it with it's private key. It is necessary to authenticate the sender with it's private key by the digital signature so that his/her message/transaction will be valid and be transmitted. As the private keys of individuals different, so the digital signature varies thereby promoting it's uniqueness and difficult to be compromised.VERIFICATION OF TRANSACTION/MESSAGE
The public key of the recipients is needed/required for the message to be decrypted/verified. The involvement of the digital signature is needed to match the messages sent to the pool for the verification process of the miner/validators with the correct public keys of recipients used by the sender when authentication process of the message sent.

EXPLAIN WHAT'S SYMMETRIC AND ASYMMETRIC CRYPTOGRAPHY
With Cryptographic functions, the message are hidden/securely transmitted to the intended recipient. To achieve this, Data are encrypted and decrypted with keys. There are two major types of the encryption and decryption process of the data. They are:
SYMMETRIC CRYPTOGRAPHY
Symmetric Cryptography involved the use of one single set of key for the encryption and decryption process of the data. Assuming that John sent "I Love you" to his wife Jennifer, the message will be encrypted with a secret key and transmitted securely to Jennifer, who can decrypted the message with that same secret key. It is very easy to set up, the secret key or password are optimally shared only by the parties intended.
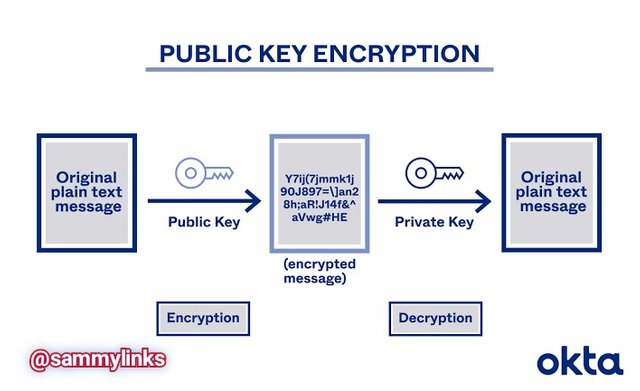
ASYMMETRIC CRYPTOGRAPHY
Asymmetric Cryptography involved the use of different sets of keys but related to the encryption and decryption process of the data. Public keys is used for the encryption process while the private key will be used for the decryption. Assuming that John sent "I love you" to his wife Jennifer, the message will be encrypted with her public key and will be securely transmitted to her but will need her private key to decrypt the message.
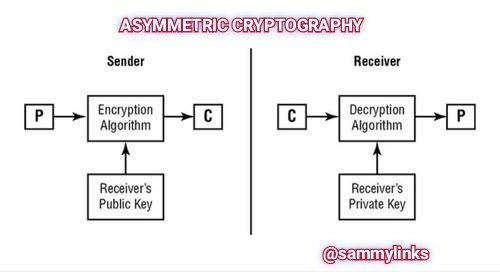
Image Source
This system of securing the message with two keys are unique and safer.

HOW BLOCKCHAIN WALLET CRYPTOGRAPHY WORKS AND TYPES OF CRYPTO'S WALLET
Crypto asset are secured on the wallet, just as our money are kept safely in the bank. As everyone makes transactions there, the issue of the identity of the accounts for everyone must be unique and different from one another. Cryptographic hash strings of alphanumerical letters are used. Each wallet have a unique set of alphanumerical letters known as the "WALLET ADDRESS". This address can't be understood perfectly by humans. It is machine coded language that's generated cryptographically. It can be disclosed publicly and used to authenticate the "said" wallet. Any interaction with that wallet must correspond with the wallet address. If not, such transactions/interaction will be invalid.
Every wallets have their addresses. They might be the same length and contains alphanumerical letters but they are unique and specially different from one another. Using of the wallet alone, does not compromise the security of the wallet's portfolios.
Another sets of alphanumerical letters are categorically referred to as keys. There are two major types.
- PUBLIC KEY
- PRIVATE KEY.
PUBLIC KEY and PRIVATE KEYS serves as the password for the wallet. Owning of them, make that one the owner of the wallet. But keys are use for the every owner's authentication process. It gives access to the wallet. It keeps assets safely and keep track of the digital signed transaction. Private keys are hidden from others, just like some pin/passwords to our conventional banking sector so that out funds/transactions will be secured.
There are basically two types of crypto wallets. They are
- Cold wallets
- Hot wallets.
Cold wallet are hardware-designed, not internet-bounded, very secure and protected. It's come in various forms like USB, Smartphones etc with software already installed on them. and hardly attacks by hackers. Examples are Trezor, Ledger etc
Hot wallet are software-designed, Internet-based. It shows real-time prices of coins/asset and mostly have a Exchange platforms attached because they are mostly been provided by Exchange platforms or web-based. Its often attack by hackers. Binance, Poloniex, Luno, Roqqu etc provides this type of wallets.

WHAT'S MERKLE TREE AND ITS IMPORTANCE IN BLOCKCHAIN
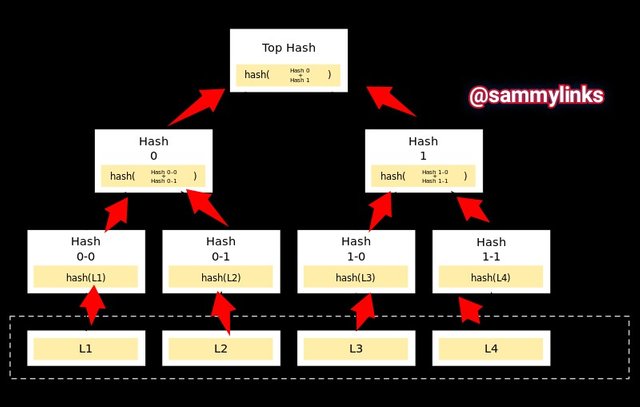
Named after Ralph Merkle, it is a systematic order of verification process of large chunks of data in blockchain in very simplest ways and accurate way.
This is a hierarchical order of data verification process. There are several blocks of information chained together on several layers forms various levels and connect with the topmost block of the information via hashing functions. This Data verification structured like tree and very efficient.
The binary functions used by Merkle's tree as seen on picture above makes the verification process unambiguously and binary functions computationally based on the number of hashes proportional to the logarithmic sequence of the number of blocks in layers/structures.
SIGNIFICANCE OF MERKLE TREE TO BLOCKCHAIN
Merkle tree have compressional process of verification of Large volumes of the blocks of information in a simple way and efficiently structured. Blockchain technology employed this hash functions to validate large chunks of blocks/transactions efficiently.
Verification process of merkle tree helps to avoid Double-spending as several verified blocks of information are linked together and validated and can't be altered. Any data/block copied or duplicated remains invalid and can't be validated.
Blockchain works as peer to peer network and several blocks from several nodes needed to be verified as a unit and be reported on commitment scheme. Merkle tree helps to harmonies the several blocks as a unit and do so in simple way with binary functions.

PRACTICAL + THEORY, DO SOME RESEARCH STUDY ON BLOCKCHAIN DEMO: PUBLIC/PRIVATE KEYS & SIGNINGS AND EXPLAIN THE FUNCTIONALITIES OF KEYS, SIGNATURE, TRANSACTION, BLOCKCHAIN WITH PROPER SCREENSHOTS
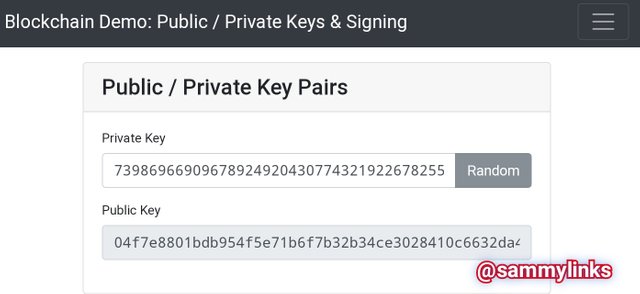
Image Source
Here, in the Blockchain Demo, let's demonstration the pairing of the private and public keys. In the default Page as shown in the picture above, Below are the default Private and Public keys.
- Default Private key
73986966909678924920430774321922678255180231965514327234598089987306587980753
- Default Public keys:04f7e8801bdb954f5e71b6f7b32b34ce3028410c6632da467436042524147f7017fab359844b81ad153ba37a05f704f1eb5889c3c6a8e58edca965713d7a92a5f1
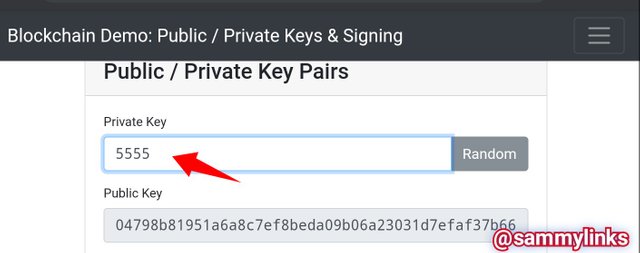
Let's manipulate it a bit by randomly generated public key from a chosen private key (i.e, 5555).
Private key 5555
New Public keys generated 04798b81951a6a8c7ef8beda09b06a23031d7efaf37b663265e0188ab3781240469592da1b0baea4303644a7e54e67476fd91382b5f1181de7a1bf9d44e02b1bf6
Private keys are not to be displayed or shared with anyone but public key can be shared with anyone and it does not compromise the confidence scheme of the procedure.
SIGNING AND VERIFICATION OF MESSAGE WITH KEYS.
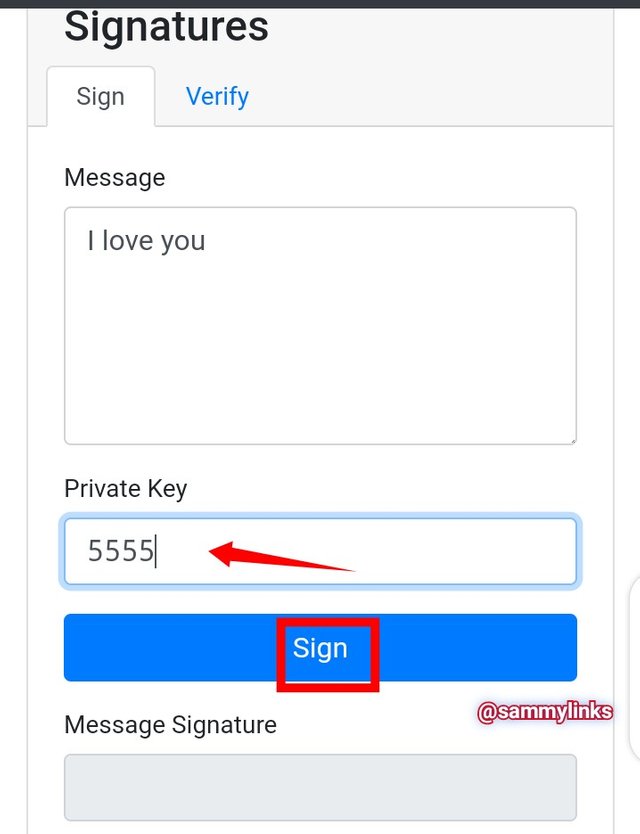
Private key: 5555
In the picture above, the message "I Love you" will be signed with a chosen private key (i.e, 5555) and securely transmitted to a destination with the message signature generated as stated below
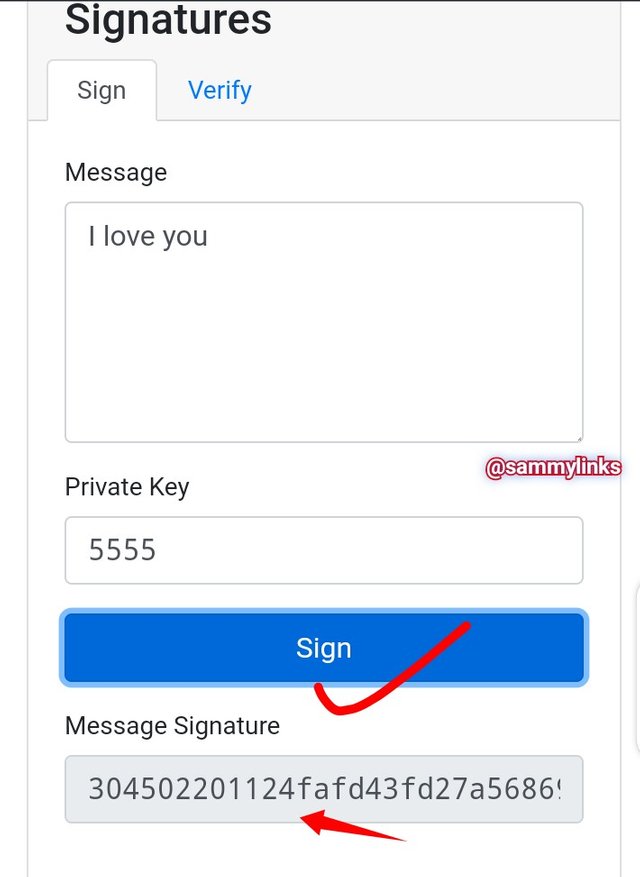
Private key: 5555
Message signature: 304502201124fafd43fd27a56869d72d62c128b08b32304b27cd8deda334aca62d4dea58022100ea38a74327dc0bec8c1b83567b4141c9dc28727ef201936f52d9e70d63e623ba.
- Verification of message with public key and message signature.
Public keys: 04798b81951a6a8c7ef8beda09b06a23031d7efaf37b663265e0188ab3781240469592da1b0baea4303644a7e54e67476fd91382b5f1181de7a1bf9d44e02b1bf6
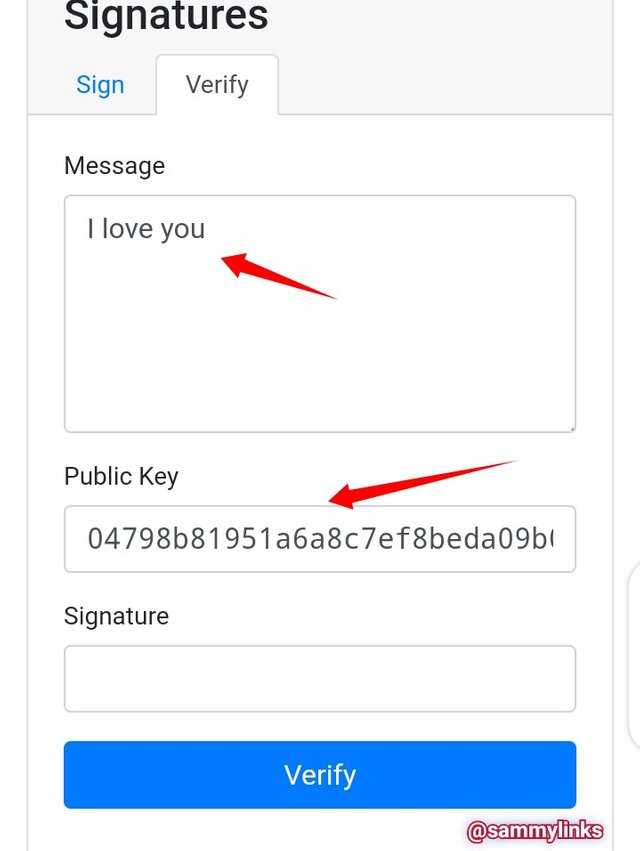
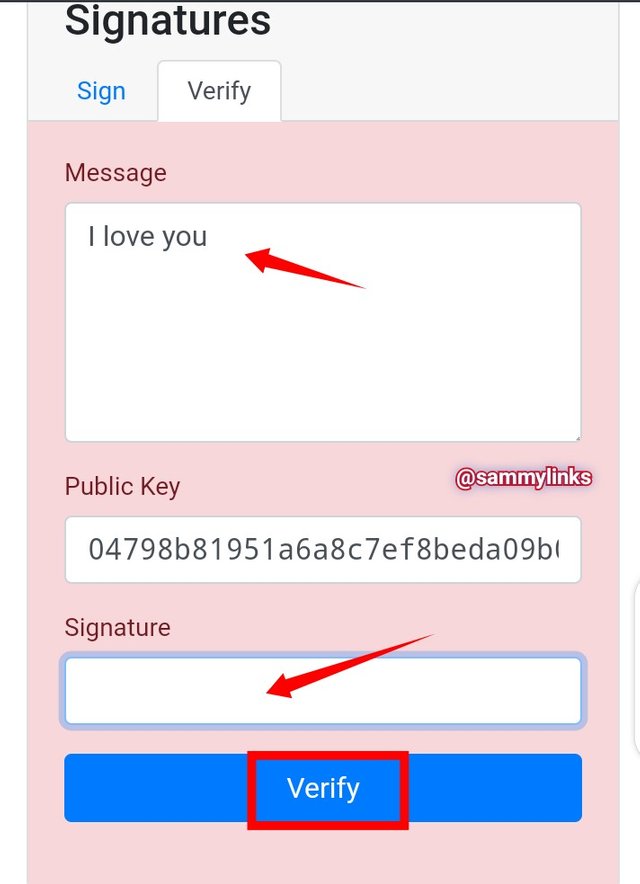
In the picture above, For a message; "I Love you" to be verified by the public key generated without message signature.
- RESULT
The picture above shows that the message did not verified. Let's used the message signature and see:
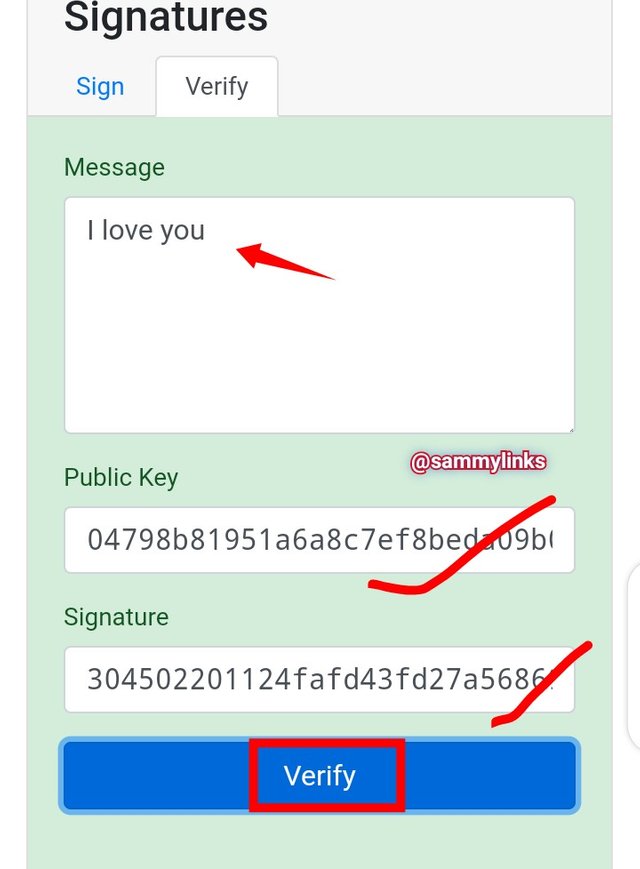
- RESULT
The picture below shows that the message was duly verified by the public key and message signature given.
Public keys: 04798b81951a6a8c7ef8beda09b06a23031d7efaf37b663265e0188ab3781240469592da1b0baea4303644a7e54e67476fd91382b5f1181de7a1bf9d44e02b1bf6
Message signature: 304502201124fafd43fd27a56869d72d62c128b08b32304b27cd8deda334aca62d4dea58022100ea38a74327dc0bec8c1b83567b4141c9dc28727ef201936f52d9e70d63e623ba.
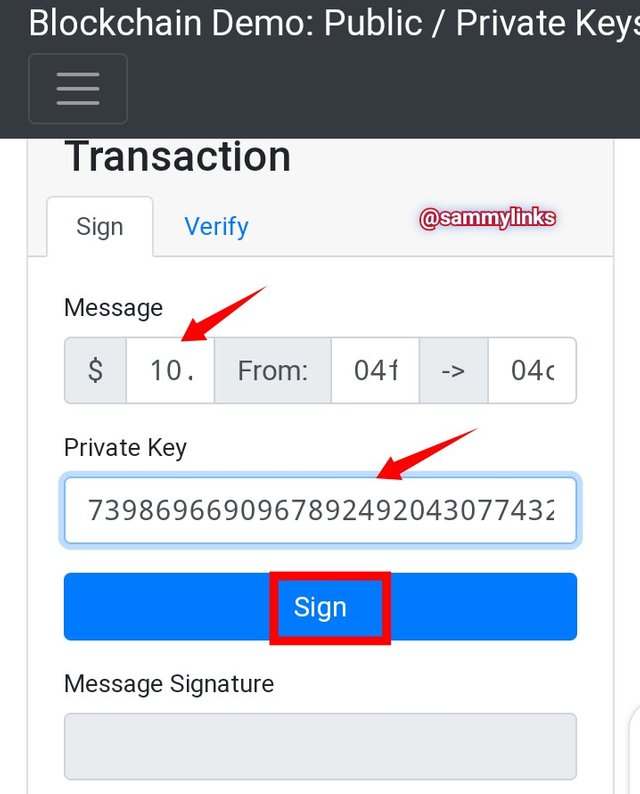
TRANSACTION WITH PRIVATE KEY
For transaction to be verified and a fund send my Public key to intended recipient's Public key. My private key will be requested. Let's demonstrate; I'm sending $10 to another person. As shown in the picture below:
FUND: $10
PRIVATE KEY: 73986966909678924920430774321922678255180231965514327234598089987306587980753
When signed with PRIVATE KEY by clicking on SIGN. A message signature generated is:
304402202f7a69937f48d216143c4e47540a76a2c216ac6185b971258ec8c8b994e6d27d0220073935fe8d6e6a464f21b7178e4162d7eadb5acc7eb1ee9ae0247c583c0bb930.
- VERIFICATION OF TRANSACTION
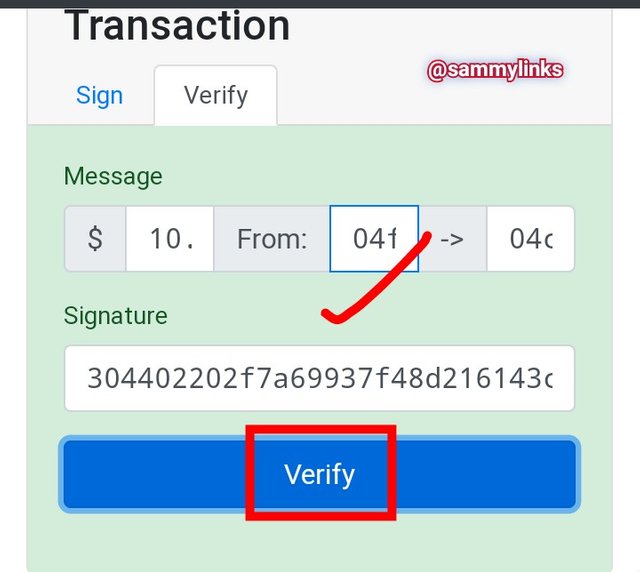
Image Source
In the picture above, the transaction authenticated initially with private key and message signature will be verified by the miner/validators because the transaction is valid

CONCLUSION
Blockchain technology verifies several message/transactions as a blocks between nodes securely cryptographically. The keys are used to authenticate the transaction/message to protect them along the communication channel.
However, there are two separate but related keys, the private key and the public key. Private keys are not to be shared with anyone as it means transfer of the ownership/access of the account/message. It's difficult to be guessed and longer. But Public keys can be shared and encryption of message/transactions are done with it for the intended recipient.
Symmetric Cryptography is simple and the encryption and decryption process are done with one secret key that is known by the sender and the intended recipient too while the asymmetric Cryptography is more secured and complex because of the use of two sets of keys. The public key of the intended recipient will be used for encryption signed by the sender's private key and the decryption process is verified by the recipient's private key.

Ahhhhhh this crypto academy things no be here oh
You lost me at the code part…. Lol
Nice one sir
With great crypto-professor @stream4u, cryptoacademy and extensive research, we are developing ourselves better!