Crypto Academy / Season 3 / Week 8 - Homework Post for professor @stream4u : Let's Open The CryptoGraphy by @salma78



Cryptography comprises of two Greek words which are Kryptos and Graphein whereby Kryptos refers to hidden and Graphein refers to write. This indicates that to a layman's understanding of these two Greek words one can say cryptography refers to a hidden written word or something.
Cryptography refers to the technology that helps in protecting any third party from getting access to data or information that exist between two parties in the process of communication. Cryptography messages are first encrypted and to have access to it unless you decrypt the message before which is done with the private key.
Blockchain Cryptography refers to the technology that is implemented in order to provide secured data within the blockchain network. There are two types of cryptographic algorithms and are Hash functions and Asymemmetric-keys algorithms. This Hash function contains a fixed length of alphanumeric combinations called the Hash. This hash is very unique and can never be altered. The other type of cryptographic algorithm which is the asymmetric-keys algorithm is where private and public keys are used to sign digital signatures in order to confirm and validate transactions. Every participant on the blockchain network possesses his/her own private key which functions as his/her own digital signature of transactions performed.
Some of the Significance of Blockchain Cryptography
Blockchain cryptography is very unique by producing a unique output hash for specific input. This implies that there are no two inputs that can produce a single and similar output in blockchain cryptography thereby making it unique.
Also blockchain cryptography as described above is highly secured. This is in the case where messages are being encrypted and only users with the private key can decrypt and read the message sent without the information or message getting leaked to the public.
Lastly, data sent on blockchain cryptography is irreversible and cannot be altered or edited.
Blockchain Platforms
The blockchain platform is a platform on which blockchain-based applications are built on which can be centralized, decentralized, permissioned, permissionless, etc. The following includes examples of blockchain platforms;
- Steem
- Tezos
- EOS
- Ethereum
- Neo
- REEF Chain


As I stated earlier the public key is one of the components of the asymmetric-keys algorithm in Blockchain cryptography. Public Key refers to the type of keys that can be shared among others within the blockchain network for either verification process or identification process. It is made up of alphanumeric combinations hashed together that give the public addresses of cryptocurrency wallet in order to receive funds into it. The Public Key can be regenerated by the private key but vice versa is impossible.
The Public key functions in verifying digital signatures that correspond to the user's private key. Also, the public key is used by receivers in the verification process so as to decrypt messages or data. Furthermore, Public keys are used in verifying transactions before adding them to the block of a chain. For instance, two parties that agree to a transaction would have to exchange their public keys in order to confirm and verify the transaction.


The private key is also a combination of alphanumeric hash that should be kept secret and only known to the owner of the key. The Private key unlike the public key must not be shared with any other person other than the owner of the key. The private key is mainly used in signing transactions so they can be broadcasted on the blockchain network. The private key helps maintain the safety of a transaction performed before being broadcast onto the network. Messages or data sent using the private key can be accessed by decrypting the message or data through the use of the private key of the recipient.
The Private can be used to generate the public key as we already stated before. The Private key adds digital signatures to transactions performed but before the transaction can be added onto the block unless the Public key associated with it is used. The Private key is a very important key that secures one's wallet and as such must not be shared with any other person and should also be kept at a safe and secured location.


Digital Signatures CryptoGraphy
Digital signature cryptography refers to certifying one's signature to a transaction performed in a cryptographic manner before the transaction is being broadcasted to the network for the validation process to take place. This is just similar to the financial markets were such as the banking system where real signatures are signed in order to broadcast transactions. Digital Signature cryptography requires the use of the private key in order to sign for a transaction to be broadcasted onto the network. In digital signature cryptography, private keys are used in signing transactions to be broadcasted to the network whilst the Public key of the associated private key is used in validating the transaction.
Importance of the Digital SIgnature Cryptography
The digital signature cryptography messages or data are said to be authentic. There is high authenticity of messages using the digital signature cryptography because of the verification of the message or data done with the public key of the signer.
Also, digital signature cryptography makes it so easy in signing large data. The signing of large data is usually costly and difficult to do but with digital signature cryptography, it is very easy and secured to sign large data without much cost.
Another vital importance of digital signature cryptography is that the signed data are not modifiable. This means that in a situation where there is a change in data, the signature does not verify such data because it doesn't correspond and as such denies the document or data.
Signing of Transaction/Message
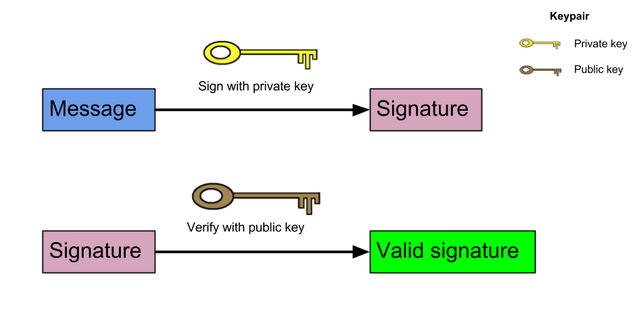
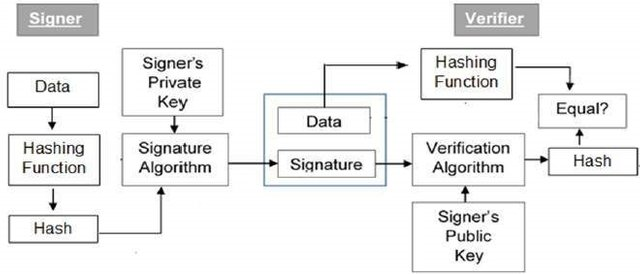
I would like us to look at the following illustration and use that to explain the signing of transactions or messages. It should be noted that the signing of transactions involves two main steps i.e. signing and verification and the diagram below illustrates these two steps.
First of all it should be noted that every user of this process possesses a public-private key pair to sign and verify the transaction.
The signer inputs data into the hash function which then generates the hash data as indicated.
The Hash value generated and the signature key is then inputted into the signature algorithm which then gives out the digital signature of the hash inputted. The signature is then added to the data and both are sent to the verifier/receiver for verification.
After the verifier receives this, he then inputs the digital signature and the verification key into the verification algorithm which produces an output.
The verifier also performs a hash function similarly to the signer on the data received in order to generate the hash value which he then compares the hash value to the output hash value by the verification algorithm.
The verifier after comparison then decides the validity of the digital signature.


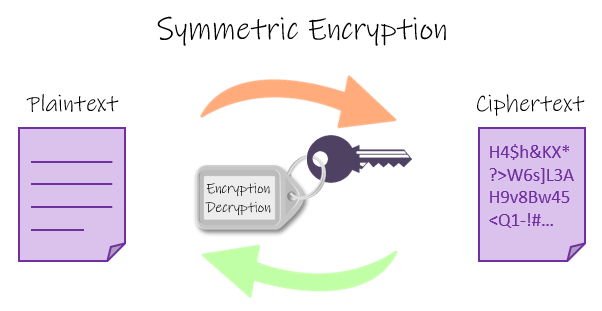
Symmetric Cryptography
Symmetric Cryptography is a type of cryptography that uses the symmetric-key algorithm in which the same or single key is used for both encryption and decryption of data. It is also referred to as the secret key or private key cryptography. In symmetric cryptography, there is no public or private key but instead, the single key is used in both encryption and decryption of data.
Examples of symmetric cryptography include; IDEA (International Data Encryption Algorithm), AES (Advanced Encryption Standard), and DES (Data Encryption Standard). The Symmetric cryptography keys are either 128 or 256 bits longer in length whereby the 128-bit key has a possible combination 340,000,000,000,000,000,000,000,000,000,000,000,000 encryption code possibilities. It should be noted that the larger the key size the harder it becomes for hackers to hack or crack the key.
Advantage of the Symmetric Cryptography:-
Symmetric cryptography does not require the use of high computational power in its functioning. Also, symmetric cryptography does not require large storage space to store files or data because they produce a small file size. Lastly, the small size of data or files produced helps in the faster transfer of files.
Disadvantages of the Symmetric Cryptography
How to manage the single key within a large group is an issue to symmetric cryptography. This means that for a large group using symmetric cryptography, a large number of keys is also needed which is very challenging in maintaining all those keys. For instance, using the formula n(n-1)/2. let's say 200 people using the symmetric cryptography key, then 200(200-1)/2 keys would be needed. This implies that 19,900 keys are required in this cryptography which will be very cumbersome to manage.
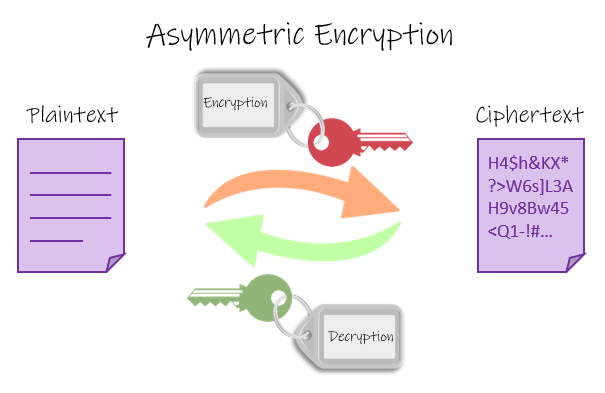
Asymmetric Cryptography
Asymmetric Cryptography is also a type of cryptography that uses the asymmetric-key algorithm in which two different keys are used for the encryption and decryption of data. Unlike symmetric cryptography where only a single is required for both encryption and decryption of data, over here two different keys (Public key and Private key) are needed to perform these two functions i.e. encryption and decryption of data.
The Private key (sender) is the key used in the encryption of data whilst the sender's public key is used by the receiver to decrypt the data being sent before one can have access to the data sent.
It should be noted that the encrypted data can only be decrypted by the sender's public key and not any public key you think of.
Considering two users B and D want to share data secretly between both of them. In that case, user B would use User D's public key and encrypt the data and also share his public key with the receiver. Once the data or message gets to the receiver (User D), User D then uses the private key of D and decrypts the data or message so as to have access to it. The private key of user D is used here because the data was encrypted using the public key of user D.
Asymmetric keys are generally 1024 or 2048 bits long. This tends to produce a value of 21024 or 22048 encryption codes respectively. These are very huge digits as we can see.
Advantage of the Asymmetric Cryptography:-
Asymmetric cryptography is highly secured as a number of keys is used unlike in the case of symmetric cryptography where only a single key is required.
Disadvantage of the Asymmetric Cryptography:-
Asymmetric cryptography as compared to symmetric cryptography is very slow in processing.
Difference betwwen Symmetric and Asymmetric Cryptography
| Symmetric Cryptography | Asymmetric Cryptography |
|---|---|
| It is mostly used for bulk encryption and decryption of data | It is not suitable for the use of bulk encryption and decryption of data as compared to symmetric |
| The single or secret key is shared between both the sender and receiver | Only the public key is shared between the sender and the receiver |
| Only a single key is used in encryption and decryption of data | Both private and Public keys are required in encryption and decryption of data. |


Blockchain Wallet CryptoGraphy
Crypto wallets refer to software that keeps or stores public keys and private keys at a safer place which can only be accessed by the respective keys of such wallets. In order to prove ownership of a digital asset, one has to use the private key as proof. Blockchain wallets' cryptography has three components i.e. private key, public key, and wallet address which we would be discussing further in this article.
The Private Key
Blockchain wallet's private key is a combination of alphanumeric codes with a fixed length and grants the owner of the wallet full access and control of the wallet. The private key is a confidential key and must be kept secret without disclosing it to any other user. The private is the key that secures one's funds in the wallet, meaning that without the private key one cannot have access to the funds and perform transactions within the wallet.
Also, the private key makes it possible for users to re-import their funds in terms of any fraudulent act by backing up the crypto wallet using the private key. As we discussed earlier the private key is also used in certifying digital signatures to transactions before they can be broadcasted onto the blockchain network. An example of the private key is shown below;
Private Key = E9873D79C6D87DC0FB6A5778633389F4453213303DA61F20BD67FC233AA33262
The Public Key
The Public Key is a key that is used in the validation of transactions after it has been signed using the associate Private Key. The Public key is the key that is used in receiving funds into one's wallet. The Public key can say that it is used in authenticating or verifying the validity of the Private Key used in signing the transaction. The Public key can be regenerated by the private key but vice versa isn't possible. The Public key is also an alphanumeric combination of keys just like that of the private key. An example of a public key is shown below.
Public Key = Zpub6xTveCGBydVjqWzVVvvi3eHASr4GRRitkDQGa7wS56a758ZhT7tXdVGFvZW3EzAXfUSWVGM274QBTn3H8VfdS5rPYqtXNj4nu8WTpqJLpTi
The Wallet Address
Wallet address refers to a fixed length of cryptographic alphanumeric unique codes. It is mostly found to be the hash of the public key generated. Every crypto wallet has a unique wallet address such that there is no crypto wallet of the same wallet address. The wallet address serves as the bank where funds are received and stored into. The wallet address is also shared with other users when they want to receive funds from them. An example of a crypto wallet address is shown below.
Wallet Address = bc1qar0srrr7xfkvy5l643lydnw9re59gtzzwf5mdq
The Types of Crypto Wallets
There are two main types of crypto wallets and they are Hot wallets and Cold Wallets. Let's take a look at these types of crypto wallets we have.
Hot Crypto Wallets
Hot crypto wallets are crypto wallets that are connected online for use. These are wallets in which one must have access to the internet before using. Examples of hot wallets include; MetaMask, Trust Wallet, Exodus Wallet, etc. Hot crypto wallets are also classified into the following types; Mobile wallets, Web wallets, and Desktop wallets. Looking at each of them briefly;
Mobile wallets:- These are mobile application software that is installed and run on mobile devices and can be used at any place at all. Mobile wallets are faster as compared to desktop wallets.
Desktop wallets:- Desktop wallets are wallets that can only be installed and run on laptops or DEsktop computers. They are very secured but prone to virus attacks.
Web Wallets:- Web wallets are wallets that can be accessed by everyone from any location possessing an internet connection. The web wallets keep private keys online which makes them more prone to attacks or hacks.
Advantages of Hot Crypto Wallets
- It is easy to access and permits faster transactions
Disadvantage of Hot Crypto Wallet
- They are prone to attacks or hacks
Cold Crypto Wallets
Unlike the Hot crypto wallets that involve the use of the internet connection in their operation, the cold crypto wallets are wallets that do not require the use of the internet and are mostly termed offline crypto wallets. The cold wallets are less prone to attacks as compared to the hot crypto wallets where they are connected to the internet. Cold crypto wallets are also classified into Hardware wallets and paper wallets. Let's briefly discuss these two.
Hardware wallets:- These are wallets that store keys offline in hardware devices and are connected to the computer when needed for use and disconnected immediately when done with it. Examples of such hardware devices include USB devices. Hardware wallet transactions are easy and more secured as compared to hot wallets because they do not function online. Trezor is a good example of a hardware wallet.
Paper wallets:- These are wallets that contain printed copies of both private and public keys on paper. Funds are transferred to and fro of the paper wallet by using QR code scanning to scan keys on the paper or by manually typing in the keys. The paper wallet is highly secured as compared to the other types of wallets.
Pros of Cold Crypto Wallets
It stores huge crypto assets offline safely
Cold crypto wallets are not prone to online attacks because they do not function online.
Cons of Cold Crypto Wallets
User loses all of his/her assets once the hardware device is stolen.
Cold crypto wallets do not favor faster exchange of assets, unlike hot wallets.


The Merkle tree idea was named after Ralph Merkle in the year 1979. He created a way in which verification of data can be done easily and faster without any hindrance using computers. It has the structure of a tree in which different hashes are arranged in a tree-like manner with the top of the tree being the root hash. This can be seen like an inverted tree where the top hash is the root hash of all the other hashes transactions.
The Merkle tree can be defined as a data structure that is made up of different hashes of transactions that are stored in blocks in that it becomes very easy and faster to verify any data of preference. As the name implies a tree, the Merkle tree is composed of leaf nodes, branches, and a root with the leaf nodes containing the different hashes of transactions that are stored in the block. The branches are the means where the hashing process continues until a fixed hash of fixed length is produced at the top of the Merkle tree called the Root Hash.
The Merkle tree makes it very easy in verifying data of transactions by reducing the consumption of memory, the computational power, and also reducing the time to verify transactions on the blockchain.
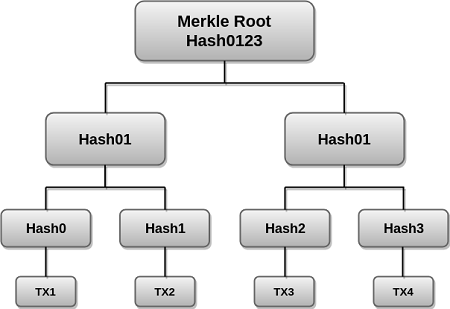
I would like us to use the illustration shown below to further explain the Merkle tree concept.
The above illustration is the simplest and commonest type of Merkle tree which is known as the Binary Merkle tree. The Merkle tree above is composed of the leave hashes.
Hash0 - transaction TX1, Hash1 - transaction TX2, Hash2 - transaction TX3, and Hash3 - transaction TX4. There are four different transactions in a block from this example shown above.
Each of these four transactions in the block (TX1, TX2, TX3, and TX4) is hashed repeatedly to produce the Hash 0, 1, 2, and 3 which is then stored in each leaf node as shown above.
Later, consecutive pairs of the nodes also hashed together to produce the parent nodes. That is hashing of Hash0 and Hash1 to produce Hash01 and then hashing of Hash2 and Hash3 to produce Hash23 respectively. The resulting two hashes i.e. (Hash01 and Hash23) are then hashed together which results in the Merkle root or root hash as seen in the illustration.
This Merkle root produce is then stored in the block header so as to make the transaction tamper-proof. This means that when any change is made to the transaction and it reflects in the hash of the transaction, an invalidation of the block would occur because of a change of the value of the Merkle tree.
Importance of the Merkle tree
The Merkle tree aids by saving memory or storage disk space by reducing the amount of memory or storage space required in data verification and validation.
Merkle tree also helps to maintain the integrity and the validity of data on the blockchain.
The Merkle tree does not require large amounts of information to be carried across blockchain networks as evidence of efficiency but instead requires just a tiny amount of information.


I would be using the Blockchain Demo website which was created by Anders Brownworth Blockchain Demo to practically illustrate the above task.
Keys
As we already stated in the questions that asymmetric cryptography requires the use of two keys i.e. the public key and the private key and these two keys are associated with each other. This means that every private key and the public key that it generates and I would illustrate that here using the Blockchain demo website. Without much time-wasting let's dive into the practical aspects.
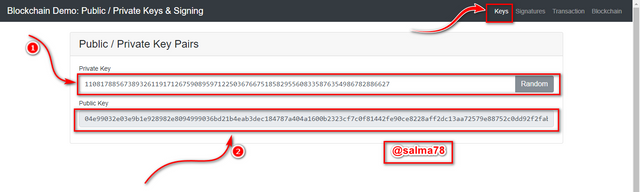
From the above illustration, we can clearly see that the private key shown has generated its own public key, and any time I click on Random the new Private key generates another new Public key which indicates that every private key and its public key associate. The first private key and its public key associate are shown below.
Private Key:-
110817885673893261191712675908959712250367667518582955608335876354986782886627
Public Key:-
04e99032e03e9b1e928982e8094999036bd21b4eab3dec184787a404a1600b2323cf7c0f81442fe90ce8228aff2dc13aa72579e88752c0dd92f2fab0cee8b0b10b
Again, I clicked on random and the new Private key generated another different Public key as shown below.
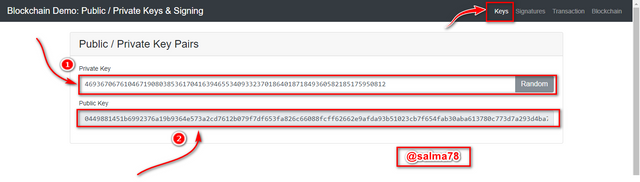
From the above illustration, the Private Key and the associate Public key generated is as follows;
Private Key:-
46936706761046719080385361704163946553409332370186401871849360582185175950812
Public Key:-
0449881451b6992376a19b9364e573a2cd7612b079f7df653fa826c66088fcff62662e9afda93b51023cb7f654fab30aba613780c773d7a293d4ba70b10e422395
I would now enter my own private key and see the outcome of the results.
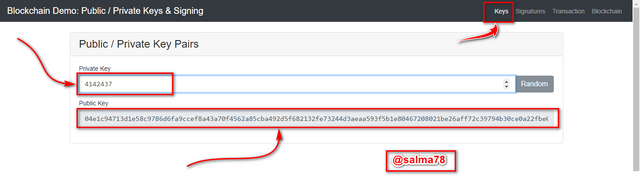
From the above illustration, I entered the Private key as 4142437 and its associate public key generated was;
Public Key:-
04e1c94713d1e58c9786d6fa9ccef8a43a70f4562a85cba492d5f682132fe73244d3aeaa593f5b1e80467208021be26aff72c39794b30ce0a22fbe04a73d488276.
I would try and alter the Private key again and see the output. So this time around I would use 4142438 as the Private key by changing the last digit from 7 to 8.
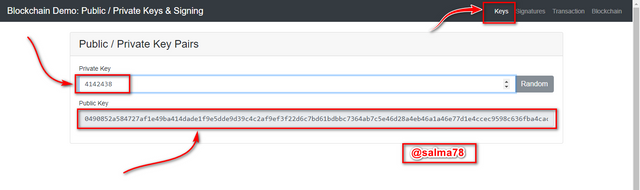
We can see from the illustration above that when the last digit of the previous Private key is changed the Public key was also altered as well giving us the following key.
Public Key:-
0490852a584727af1e49ba414dade1f9e5dde9d39c4c2af9ef3f22d6c7bd61bdbbc7364ab7c5e46d28a4eb46a1a46e77d1e4ccec9598c636fba4cac33f984aace7
The above illustrations clearly indicate that every Private Key and the associates Public Key it generates. This proofs the statement that there are no two or more Public Keys generated by the same/single Private Key.
Signatures
I would be signing the message (Steem for life) and I would use the Private Key I entered in the previous task i.e. (4142437). Now to do that, the following steps are followed;
- First of all I enter my message (Steem for life) in the message space box.
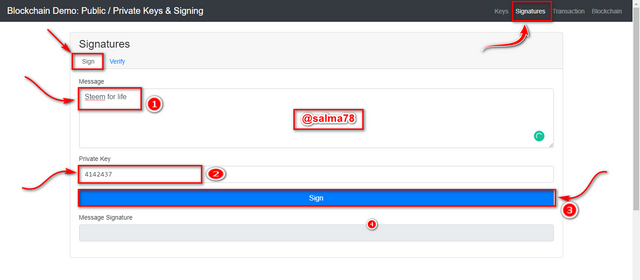
- I then enter y Private key 4142437 and then click on Sign which generated a digital signature as shown below.
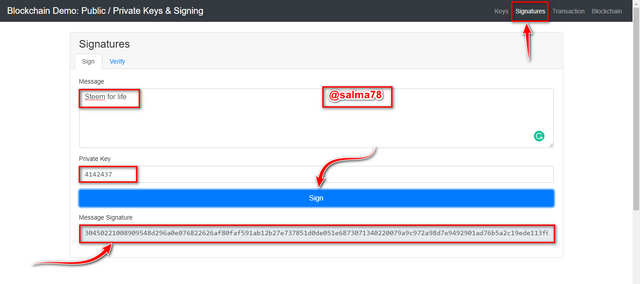
The transaction signature is given below;
30450221008909548d296a0e076822626af80faf591ab12b27e737851d0de051e6873071340220079a9c972a98d7e9492901ad76b5a2c19ede113f609a152befbf91ecf53f4207
I would now verify this transaction by clicking on the Verify section to validate this transaction performed and I would be required to use the associate Public Key of the Private key I used (4142437).
I would then enter the associated public key of the private key and then click on Verify to validate the transaction.
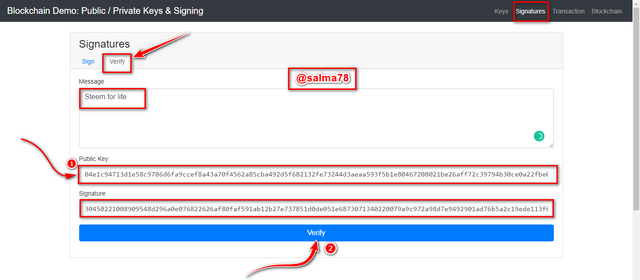
- After clicking on "verify" the window changed to green color which implies that the Private Key used in adding the signature to the transaction is valid by verifying it with the associate Public Key. This can be shown in the illustration below.
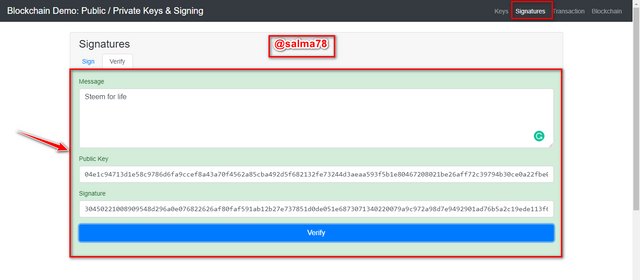
Transaction
I would be making a transaction of $40 by using the Private Key to sign and then verify the signature with the associate Public Key. Let's do this by following the steps below.
- First of all, I will input the amount $40 in the amount section and then also input my Private Key **(4142437). This automatically enters my Public Key and my Receiver's Public key too as indicated below.
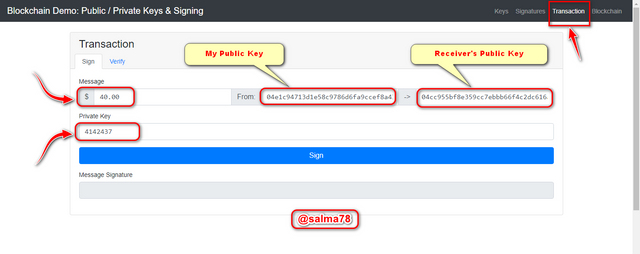
- Now I would click on Sign to generate the digital signature.
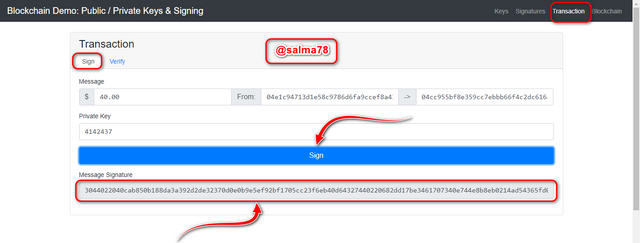
The digital signature generated is shown below;
3044022040cab850b188da3a392d2de32370d0e0b9e5ef92bf1705cc23f6eb40d64327440220682dd17be3461707340e744e8b8eb0214ad54365fd050730a729f967e07e41c2
Now I would verify the transaction by clicking on the Verify section to add a block to the network.
The Public key would be used here. Now click on Verify after confirming your Public Key.
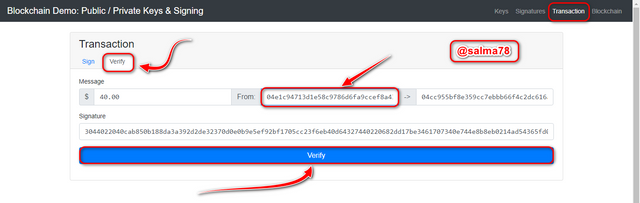
- Immediately after clicking on verify the window changed to green color which indicated a validated transaction and it was verified as shown below.
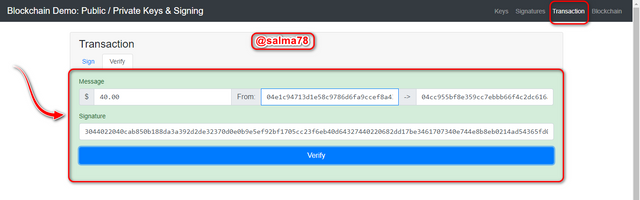
Blockchain
I would be illustrating how the blockchain response to changes in transaction details in this section. From the screenshot taken below, we can see all the blocks shown below are valid blocks and are all seen to be in green color. Now I would try to alter the transaction amount of block #5 and see what happens.
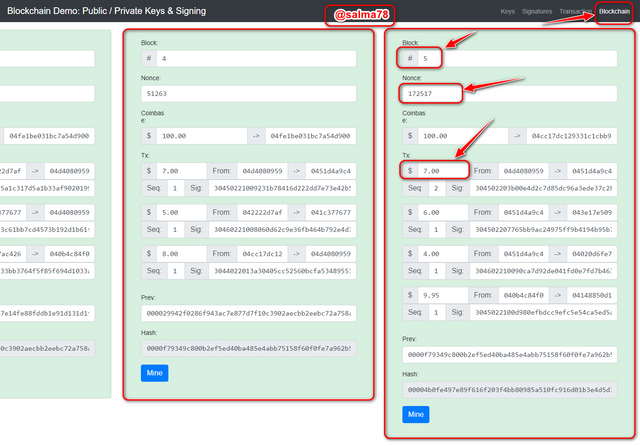
- Now I would change the amount from $7.00 to $40.00 and we can see from the screenshot below that the block window has changed from green to Red which indicates an invalid block number 5. If there was to be another block after block #5 then all those blocks would have also been invalidated. Because of the invalid of the previous hash output which would also be stored in the next blocks making it invalid as well and as such all subsequent blocks would have been invalid too.
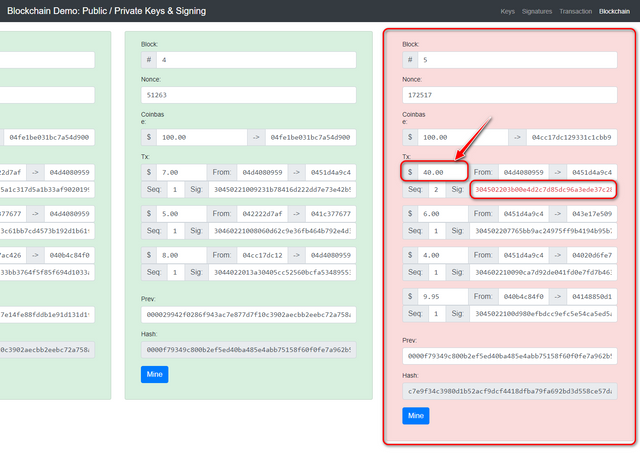
- Now to make block #5 valid we have to change the Nonce and to do that we will just click on Mine but the previous Nonce was 172517. Now we go by clicking on Mine and the following result was given.
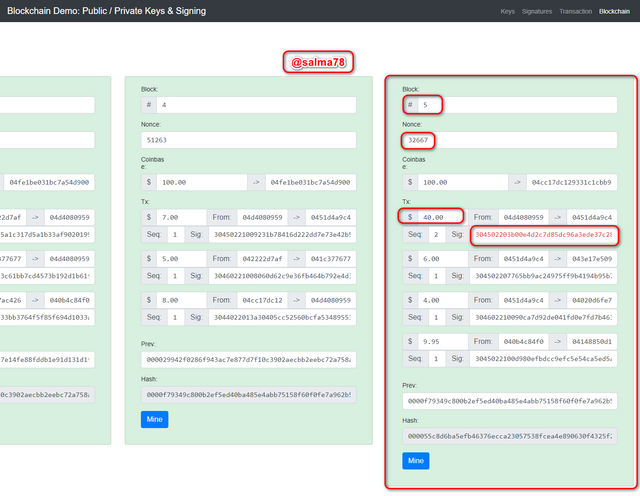
- We can see from the screenshot above that after I re-mined block #5 a new Nonce of value 32667 was generated and the block now changed back to green but the digital signature still remains red (invalid) and this is because the Private Key used in signing this transaction amount is not associated with the Public Key above. Thus the digital signature remains invalid after re-mining the block.
This illustration has proven to us how invalid previous block(s) affects subsequent blocks and also proven to us how cryptography provides high security to data in blocks of the blockchain.


To conclude with I would like to briefly summarize my understanding of cryptography and what we have done so far in this homework task. First of all, we discussed the concept of blockchain cryptography where we also looked at some of the examples of blockchain platforms. We again discussed Public Key cryptography and its functions. We also did the same with Public Key cryptography including the functions. In addition, we discussed the concept of digital signatures cryptography and its importance. We further went on and looked at the steps in the signing of the transaction where we explained in detail by providing an illustration on that.
Furthermore, we looked at the concept of symmetric and asymmetric cryptography and their functions each. We also discussed some of the differences between symmetric and asymmetric cryptography. We also discussed how blockchain wallets cryptography works and the available kinds of crypto wallets including examples. We also discussed the concept of the Merkle tree and its importance in the blockchain. Finally, we looked at the practical approach study of a Blockchain Demo where we used that to explain the functionality of Keys, Signature, Transaction, and Blockchain by providing screenshots of my work. I have really learned something new and I enjoyed doing this assignment.
For the matter of doubt, I leave below references I used in performing this homework task.
Reference 1
Reference 2
Reference 3
Reference 4
Reference 5
I would like to say thank you to professor @stream4u for such a wonderful lecture taught this week and I look forward to participating in your subsequent homework tasks.
Thank You.
Hi @salma78, you have used an incorrect tag. Kindly remove the #asaj-s3week8 from your post as it is not in congruence with the tag.