Crypto Academy / Season 3 / Week 8 - Homework Post for @stream4u - Let's Open The CryptoGraphy.
Hello everyone,
let’s get started...
Question 1
The first question to be answered is about the Blockchain Cryptography. We can clearly defined the blockchain Cryptography to be ways in which data is transferred without the inference of third parties. So basically, what happens is that, messages or transactions could be shared among people without a third person getting to know what was sent.
This idea of Cryptography probably might have been brought up as a result of security seek. Like as mentioned in the lecture, The government then being able to read the messages of Warren Buffett. These means that, his mails were hack probably without his notice and that was how they were being read. But as in the case of using cryptography, I dont think there would be a case like this since messages has to be encrypted by a sender before its being sent and then the one whom is supposed to receive must have a key, in this case we call it the private or the public key to have access to these messages or transactions as in the case of the Blockchain base.
So basically, cryptography would encrypt written text of human understanding into some form of binary language which is not comprehensive to the human understanding until it is being decrypted.
Lets See Some Names which are the Blockchain Platform.
- Steem Blockchain
- Ethereum Blockchain
- TRON Blockchain
- Ripple Blockchain and so on.
Question 2
Public key cryptography is a system which encrypt and decrypt messages based on the pairs; private key and public key. Public keys are shared with friends and families on the network that is used to encrypt a message for a receiver. Encrypted messages can only be decrypted by the receivers private key link with it. The public key is being generated from the private key
In a scenario when two individuals agrees to make a transaction, the sender and receiver share their public to each other. The sender creates the digital signature with the help of his private key to transfer the asset. For the receiver to receiver the asset, he confirms with the public key.
Question 3
Private Key
The private key consist of alpha numeric characters which makes it secure and almost impossible to hack or compromise. It is meant to be kept safe and only the owner of the wallet can have access to it. It is a secret key of a wallet which is generated at the time of creating the wallet. Funds in the wallet can only be accessed with the use of the private key.
Question 4
Digital signatures are cryptographic value that is mathematically calculated to ensure the validity of a message binding to a person digital data. The binding of the person and signature can be done by the receiver or the third party involved using the public key.
Message Authentication:- When the digital signature is validated using the public key of the sender, there is an assurance that the signature has been created by the sender who has access to the secret private key only.
Data Integrity:- In a situation when data is been modified or changed by an intruder, the hash and the output provided will not match hence the digital signature verification at the receivers side fails.
No denial of signature:- A particular signature is only associated to one and only one user and can only create a unique signature. With this, the receiver can present the digital signature as an evidence should incase a third party gets involved in a dispute.
The following steps demonstrate how a digital signature works
Generate harsh :- Sender input the data into the hash function and generates the hash of that particular data.
Produce Signature:- Private key and hash are inputted to signature algorithm to produce the digital signature
Send to Recipient:- The data is sent to the recipient together with the digital signature.
Generates Hash:- The receiver confirms the transaction by inputting the senders public key together with the digital signature into the algorithm to generate a new hash.
Confirms Transaction:- Using the same hash function to generates the hash value. The newly hash value generated is then compared to the previous hash value generated if they are the same. If they are the same, the receiver get the assurance that signature is valid.
Signing A Transaction
Signing a transaction is the adding of digital signatures to transaction with the help of the private keys to prove that the transaction is being made by the actual owner of the wallet.
Questions 5
The symmetric Cryptography uses single key for encryption and decryption of data. This single key is shared between parties involved in a network. The key used to encrypt the data is the same key that decrypt the data.
The single key or secret key is used to encrypt the data from a plain text to a machine language and then sends the message to the network for the receiver. The receiver then uses the same key to convert the data from the machine language to a plain text which can be read and understood by the receiver.
Examples of Symmetric Cryptography
Rivest Shamir Adleman (RSA)
Digital Signature Standard (DSS)
Elliptical Curve Cryptography (ECC)
TLS/SSL protocol
Advantages Of Asymmetric Cryptography
There is no need to exchange keys
The security has ben high because the private keys don't have to be shared or transferred.
Digital signatures are used so the receiver can verify where the message is coming from.
The use of non-repudiations prevent a sender from denying sending a message.
Disadvantages Of Asymmetric Cryptography
Asymmetric cryptography is slow comparing to the symmetric cryptography so its not advised to use for bulk messages.
If and when an intruder or hacker gets to identify a user private key, the intruder gets to read the user messages.
If a user lost his or her private keys, he cant decrypt all the messages he receives
Question 6
A crypt wallet is a digital wallet which holds a private key that allows traders to trade and stored cryptocurrency online. These crypto wallets can only be accessed by their respective keys. The private key serve as your digital identity such that if anyone gets accessed to it can steal the asset in the wallet. Just like the banks, crypto wallets has an address which works like an account number. The use of hashing on crypto wallets makes sure that the address can be sheared with other users without being compromised. The private and public keys work as the pin or password like the banks do. The difference here is that, the private key is kept private and the public key is shared among users. To make a transaction, the owner has to input his or her private key to claim ownership of the wallet.
Example of a Private Key
92385285643550899824068394815510067817266667329473886364829713635846035258010
source
Example of a Private Key
0474904544e78f31d9eee3e6db353b0f4321cf55c6e62dbec9a41c331867bf1d3ffb7dcb9ca09cc8ac9157c6f11e64e5175d5ae960e59e9e607899640e6583b7dc
source
Every private and public key are unique linked to your wallet. They are generated at the time the wallet was created. Like our emails where a user needs to be able to send us email. With someone having the email doesnt mean they can be able to login and use your account, they will have to get your password to do that. Similarly, the scryto wallet has its public key shared to other users just like the email and the private key serves as the password as well.
There are two main categories of wallets thus hot wallet and cold wallet. The wallets that are operated on the internet are known as the hot wallets and wallets that are kept offline are known as cold wallets.
Hot Wallets
The hot wallets are wallets that store crypto assets and are operated online. This type of wallet are not 100% secured. It uses the internet on different servers which makes it vulnerable to intruders and hackers.
Cold Wallets
Cold wallets operate offline that stores crypto assets. Unlike the hot wallet which is less secured, the cold wallet is more secured because it is physically with the owner and not vulnerable to intruders on the internet.
Categories of crypto wallets are also classified into three main types;
Software Wallets
These are wallets that can be operated on *mobile devices, *laptop and online. There are software that are installed on digital devices. They can be operated anywhere as far as an internet connection is available. Desktop and web wallets are example of a software wallet
Hardware Wallets
Hardware wallets stores private key and public addresses in hardware devices offline while transactions are done online. They are the safest way to store cryptocurrency. It is a USB way like device that connects to PC or mobile devices. Ledger nano X, Cobo Vault, Safepal hardware wallet, just to mention few are hardware wallets.
Paper Wallet
Paper wallets are physical type of wallet which stores or saves the private and public keys on a paper like a documentation. This type of wallet is less secured because if the paper gets missing means the keys and asset are also lost automatically
Question 7
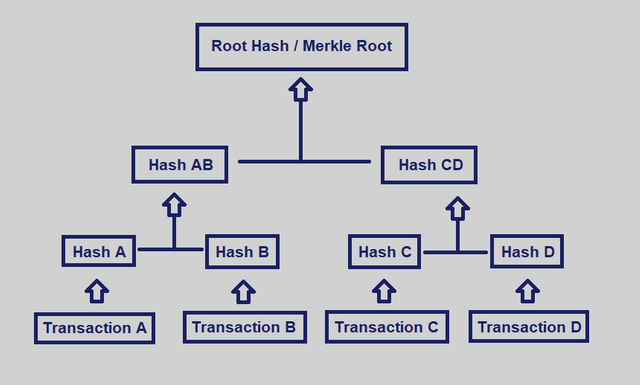
Ralph Merkle created the Merkle tree which allows data to be verified allowing computers to work more faster and efficient. It is a data structure that arrange transaction data in a blockchain. So what happens is that, the formation of roots, leaves and then branches forms the Merkle tree. That is, the bottom forms the basis of the root and the the middle forms the branch and then then leaves follows. What again happens is that, it gives miners the opportunity to actually verify all transactions made in a blockchain in a very simple way.
Above is a simple ideology of the Merkle tree. As we know that it represents transactions made in a blockchain, looking at what is happening in the picture, transactions at the bottom would represent clearly what the leaves are, that is for the Transaction A, Transaction B, Transaction C and then Transaction D. These four represents what the leaves are which shows how the transactions look like in the blockchain system. I will further explain what the branches, which also are represented as Hash AB and as Hash CD showing this in two different blocks. So here, the Hashes of AB and then that of CD in the diagram above represent the branch of the Merkle tree. Lastly, the part that's forms as the father of the Merkle tree is the root. Just like we know how roots behave, it clear and a very logical way of understanding in this case though its related to blockchain base. The root is what holds or where the Merkle Tree is formed from.
After giving an enlightenment on what the Merkle Tree is all about, I would like to state emphatically with much enthusiasm about the importance of the Merkle Tree and how beneficial it is to the Blockchain.
The first thing I want to mention is the fact that, in the verification and validation of data is much simple and safe to deal with using the Merkle tree principle.
Another most important thing is the fact that it is safe and secured to deal with, thus it helps reduce the storage space being consumed.
More so, we know how some blockchain spends so much time in the validation process and verification process of data, here in the Merkle tree principle, its much simple and very fast to deal with.
Question 8
Practical + Theory, do some practical research, study on Blockchain Demo: Public / Private Keys & Signing and then explain the functionality of Key, Signature, Transaction, Blockchain with proper screenshots of yours practical. (Do study well for this topic)
In this task I would be illustrating practical study on Keys, Signatures, Transactions, and Blockchain.
Keys
In this section we would be discussing about the Public and Private Keys. As I already explained these keys, lets dive into the blockchain now.
From the main page of the blockchain demo website Blockchain demo. A private key was provided and its associate Public Key is generated automatically. This is shown from the screenshot below.
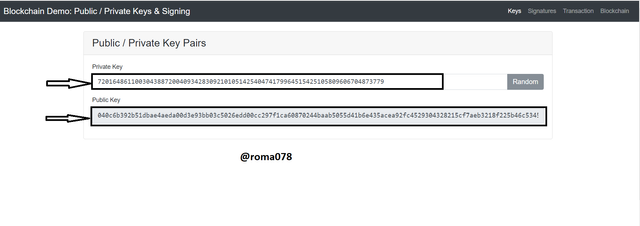
From the above screen shot the following Private and Public keys were generated.
Private Key: 72016486110030438872004093428309210105142540474179964515425105809606704873779
Public Key: 040c6b392b51dbae4aeda00d3e93bb03c5026edd00cc297f1ca60870244baab5055d41b6e435acea92fc4529304328215cf7aeb3218f225b46c534557b1beef318
I would then click on Random and generate a new Private Key which then automatically generates a new Public key as well. This is an indication that every Private key and its associate public key. The following are the Private and Public Key generated respectively as seen from the screenshot below.
Private Key: 57206201088911797162829977898640667518622391935951194684273561744129035708308
Public Key: 0477d25b4eba38ae8c5d79090d4c1785d8e266e330692ea0ce642d2a882d02740622dc944febc7adf5e03efdb476f927446af36e948262ee2a365058092153b715
Now I would like to enter my own Private Key and then generates a Public key for it. I would use 965444 as my private key. Now let's enter the private key manually and see the Public key to be generated.
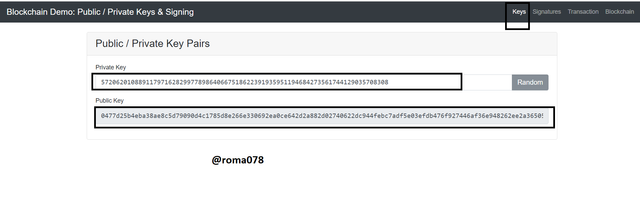
After entering the private key as 965444 the following public key was generated as shown below.
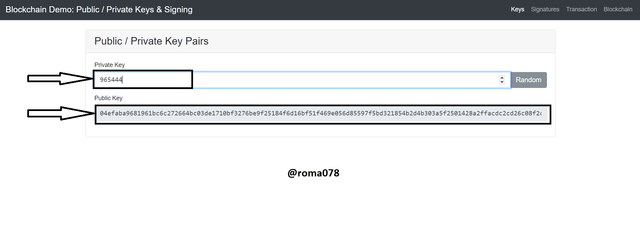
Public Key:04efaba9681961bc6c272664bc03de1710bf3276be9f25184f6d16bf51f469e056d85597f5bd321854b2d4b303a5f2501428a2ffacdc2cd26c08f2cf3ca22500be.
Now I would try to alter the Private key by changing the last digit to 9. After doing this a new Public key is generated as shown below.
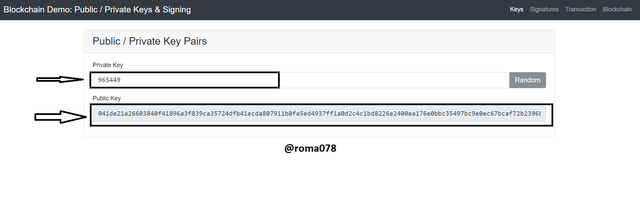
Public key generated: 041de21a26603840f41896a3f839ca35724dfb41ecda807911b0fa5ed4937ff1a0d2c4c1bd8226e2400ea176e0bbc35497bc9e0ec67bcaf72b239682767911e328
From the illustrations shown above it is an indication that every Private Key and its unique Public Key.
Signature
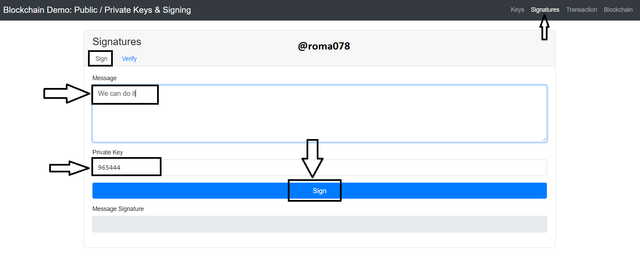
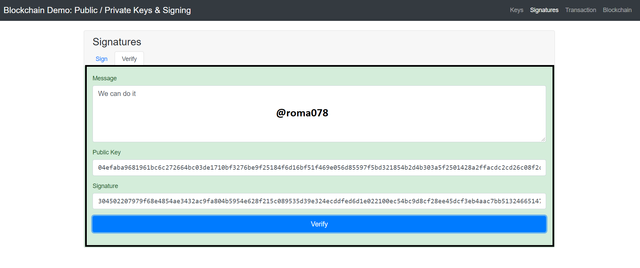
In this section I would be discussing how to sign and also verify transactions. I would be using my Private Key which I used above to sign the transaction. (965444) The message that I would be signing is We can do it.
- First of all I would add my private key and then click on sign to generate the digital signature.
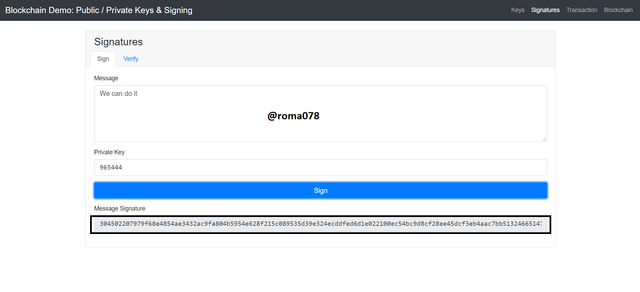
From the above screenshot we can see the new generated digital signature for the message provided.
The digital signature is shown below:
304502207979f68e4854ae3432ac9fa804b5954e628f215c089535d39e324ecddfed6d1e022100ec54bc9d8cf28ee45dcf3eb4aac7bb513246651474c061b0d569ab499a464eee
Now we would verify the above transaction by clicking on the verify tab and the we make our verification.
Once we click on Verify tab, the Public Key is automatically inputted and so we then click on Verify.
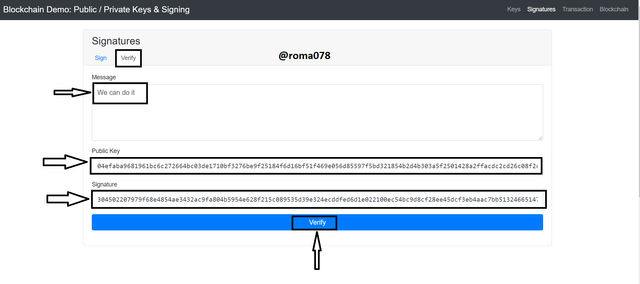
After clicking on Verify the Block window then changed to Green which implies that the above private key was used in adding the signature. This is valid by using the public key to verify as shown below.
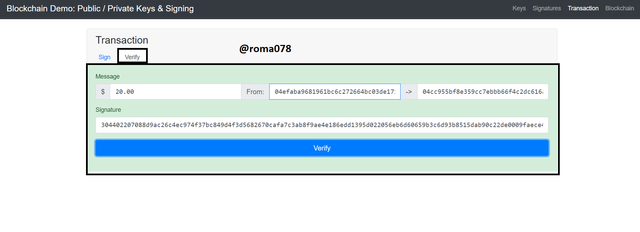
Transaction
In this section I would make a transaction by signing with my private key and then later verify that with the associate Public key. This means that two processes would be illustrated here i.e. Sign and Verify
- First of all, from the Sign Tab I would enter the amount as $20 and the enter my private key (965444). We can see that the Public key and the Receiver's key are both entered automatically.
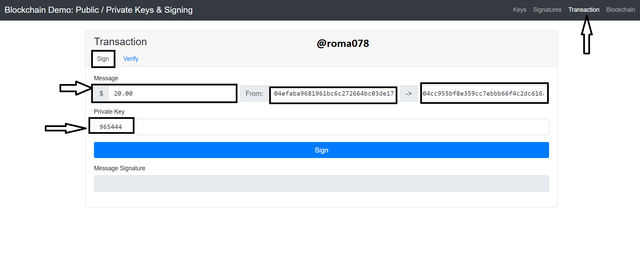
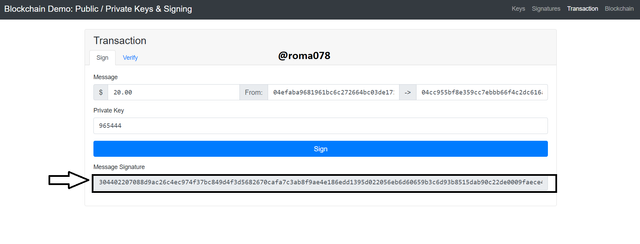
- I would now click on Sign to generate the signature. After clicking on sign the following signature was generated.
304402207088d9ac26c4ec974f37bc849d4f3d5682670cafa7c3ab8f9ae4e186edd1395d022056eb6d60659b3c6d93b8515dab90c22de0009faece40eb643ae28b18499f7fcb
This can be seen from the screenshot below.
- Now we going to verify the signature so we will then click on Verify tab. From the verify tab section we would click on Verify to verify the signature generated.
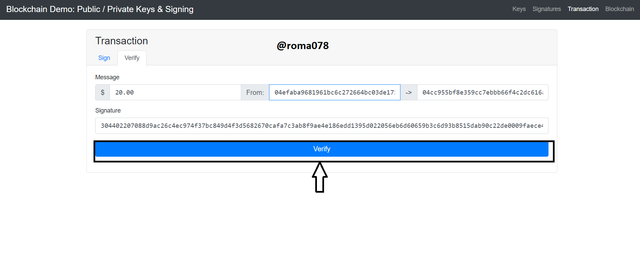
After clicking on Verify the window changed to Green color which is an indication of a valid signature. This is shown below in the screenshot.
Blockchain
In this section, I would be looking at how altering details of transactions affect the blocks in the blockchain. Let's quickly dive into it.
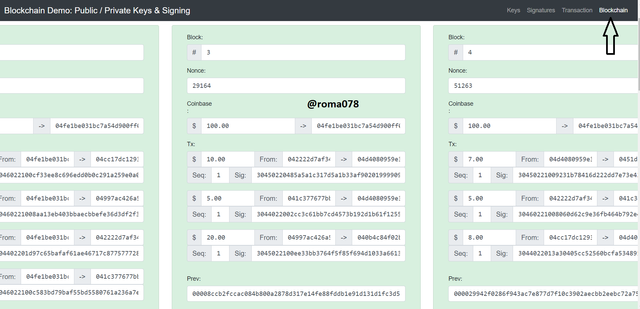
The above is a valid blocks of transactions and I would be making some changes in block 3 so we can see what happens in doing this. I would alter the amount from $10 to $15 and we can see that immediately I made this change the block window changed from green to red and this affected all the subsequent 2 blocks as shown below.
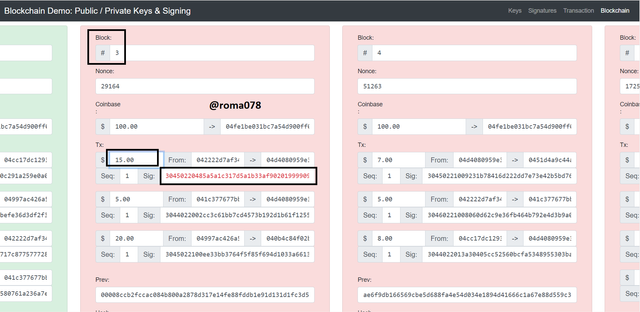
To validate this block, we would have to re-mine the block by clicking on the Mine button shown at the button of the block. The subsequent blocks after block 3 i.e. block 4 and block 5 were also invalidated because the validity of blocks relies on the hash output of the previous blocks and such, since the previous block is invalid then this affects all the subsequent blocks as we have seen above.
Now I would click on Mine for Block 3, 4 and 5 to make them valid. Block 3, 4, and 5 were previously having Nonce of values ; 29164, 51263, and 172517 respectively.
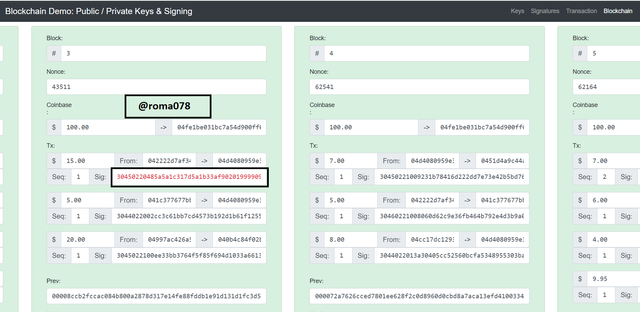
- After re-mining the blocks, new Nonce were generated that is (43511, 62541, and 62164 respectively.) We can see from the above screenshot that after re-mining the blocks block 4 and block 5 were validated but block 3 was still invalid because of the invalid digital signature and this is because of different private and public key. I hope the above illustrations clearly explains the concept of how altering details of transactions affect blocks.
First of I will like to thank the professor for this weeks crypto task. It was really a great task to deal with.
Cryptography is a key thing in the crypto world since its focus its always learned on preserving user data. So in order to prevent user data being read by people just like the case of Warren Buffet whos mails were read by the government. So we have seen the importance of cryptography in the blockchain system since it deals with encrypting and decrypting messages or transactions with the private or public key. This will help prevent the case of hackers invading the system or phishers.
Quiet apart from that, I talked about some blockchain platforms like the Ethereum, Ripple and the case of Stellar blockchains like I mentioned.
More, the other stuff I mentioned in my summary was digital signature, which represent how data is stumped with security. So here, I spoke how the encrypted data is being signed by the sender of the message or transaction .
The other thing I did not skip aside was what symmetric and Asymmetric cryptography is and I also gave some difference in tabular form about the difference.
Hashes were the other thing s I talked about and also crypto wallets, the types of crypto wallets were explained and then the Merkle Tree.
Above all, the lecture was a great one and I thank you all and the professor for this week's crypto