Blockchain Wallet(Types, Uses, Installation) - Steemit Crypto Academy Season 5 - Homework Post for Task 9.
(1) How do you store/secure your keys? What are the different forms of Private Key(Examples/Screenshot)? Download & Install TronLink Wallet(Android/iOS/Extension)? How do you store the key(Hint- write it down on a notepad, demonstrate it with examples)? Which form of the key are you comfortable with to handle your TronLink Wallet? Include Screenshots & hide/blur the sensitive information.
(1) How do you store/secure your keys?
Blockchain Key AR Cryptographical Secret Key which develops and creates the user in the market, a user United Nations Agency creates a new billphalone.
In fact, these keys are employed to make and execute their transactions by users. Group action addresses will be created to accept digital payouts. Key AR is important in blockchen technology.
You can also be done in many ways to be smart for you to store or secure your keys. The first step in the protective key is to store offline, which is protected from malware or phishing attacks to the user.
Apart from this, after saving or writing your keys, you should do it completely on individual basis on individual papers so that the scale is back. Shrink back To cut back} Thus reduce the other person to reach paper.
The other means that which saves it, remembers your keys, thus only the main owner will access it, although it will rarely forget or not. It is advisable that do not print our keys, take screenshots, save them in your email or Gmail, or try to store them online, it will be the risk of hackers and they will reach your keys with your data.
What are the different forms of Private Key(Examples/Screenshot).
There are three main styles of private keys and those we're going to look at below.
private key.
It is also known as alphamerical key because it is made up of letters and numbers of the alphabet. This key is generated randomly like currently when you create a blockchain pocketbook.
An example of this key was found when someone got a new signal. keys, individual posting keys, individual active keys all individual keys on the square measure.
Example of a non-public key.
mnemonic key
Mnemotechnical key also known as seed phrase, mnemotechnical section square measure is usually composed of twelve, 15, 18, 21 words.
This section is usually created by the user who has created the affiliate account.
And the example of such a key received after the user downloads the affiliate creates an account on TronLink PocketBook.
Although this key is never encrypted, it is very secure to use. Unless someone gets hold of those keys, he can't access your account. The good thing about mnemotechnical key is that it will be easy to read and handle.
keystore file.
A keystore file is a security file accustomed to storing a collection of microscopic cryptographic keys that prey on the binary JSK format.
It is worth noting that the keystore file is the associated encrypted key and is extremely secure (password encrypted). It will generally be accustomed to installing the AM app's author.
Download & Install TronLink Wallet(Android/iOS/Extension)?
Step1- type TronLink wallet on search section of your mobile app store
Tap on first option
Step2- then new screen is open so click on install
Step3- click on open
New screen is open
Step4- tap on create account
Use your email to create account when you click on create account new screen open
Step5- click on accept after reading it
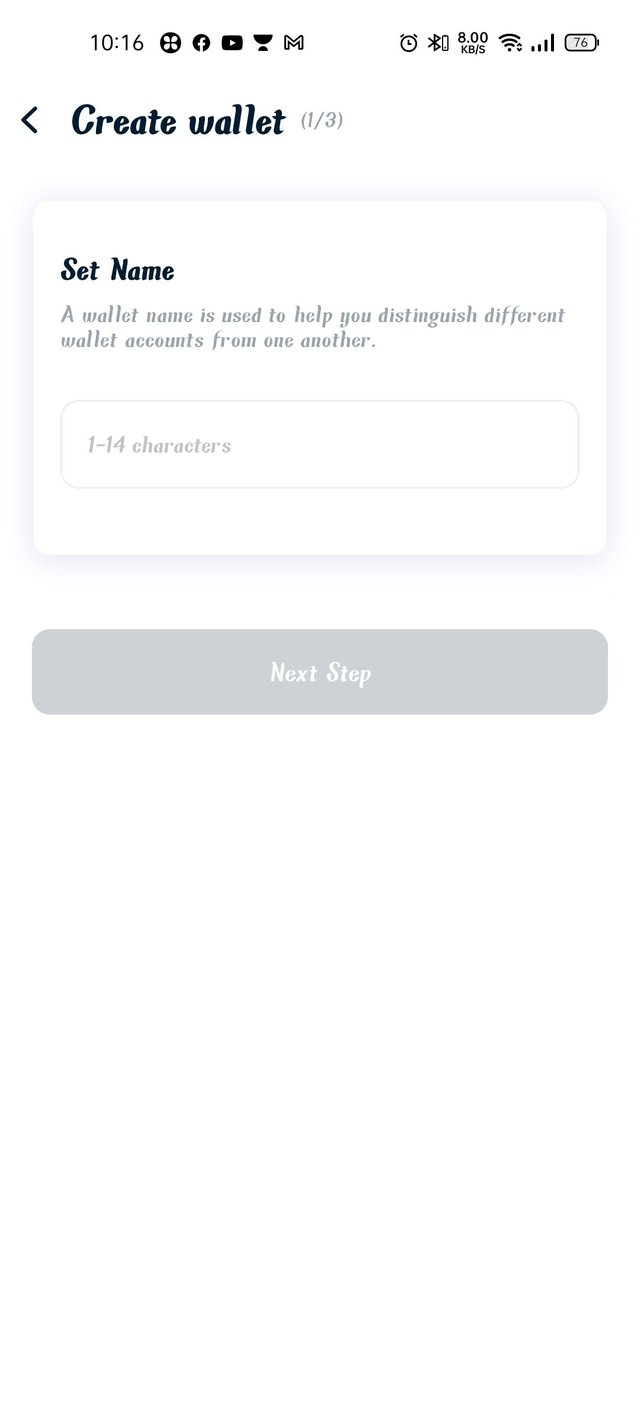
Step6- set your user name
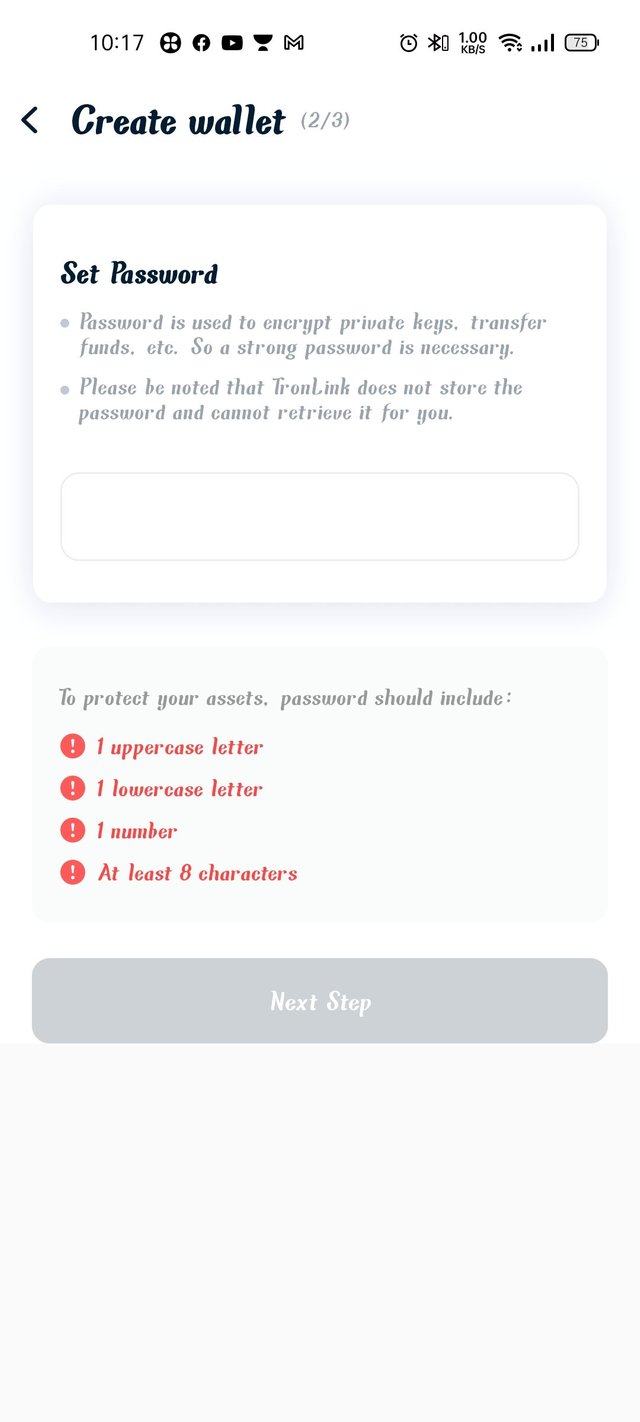
Step7- set your password by following all the conditions given bellow
After that your wallet completely installed
How do you store the key(Hint- write it down on a notepad, demonstrate it with examples)?
I store the key AN in a very cold notecase that the aide in nursing will be in an offline environment, or the associate degree will be in an offline device, that the aide in nursing, the connection will not like a hot notecase that has high security. Virus, cyber attack or hacking threats.
The Internet and similar threats are responsible. Cold Notecase Sample Hardware Notecase, Paper Notecase and Really Cold Case is a secure case that doesn't connect online.
Right now, I will only be able to discuss the many security measures I personally take to absorb storage keys, and what are they? In fact, I key in an associated degree offline device such as a flash drive, a bit of paper and keep it in a highly secure or secure place.
In fact, these offline storage devices are hardware wallets that are considered a secure technology to store keys, positive they are proof against hot wallet related threats such as viruses, cyber attacks or hacking threats.
The following screenshot may also be an associate degree example of a type of key-rolled method on a pad of paper.

Which form of the key are you comfortable with to handle your TronLink Wallet? Include Screenshots & hide/blur the sensitive information.
I am very comfortable with the method of individual keys within the first question, in the way that I keep my keys memorized. Unit Unit Words is understandable and quite simple to learn.
I have written them too. So I won't mind remembering it. I also use method key, as a result, I will restore my notice, reset password and generate new notice address.
Conclusion:-
I learned a lot here, especially about non-public keys that divide the square measure into 3 forms. Second, it is extremely important to keep a copy of your keys to avoid losing and forgetting your keys and to keep your account secure.
.png)
.png)
.png)
Hi @madhuri002,
Your first image is in breach of copyright.
Your "image source" must link to the ORIGINAL SOURCE and not a secondary source like google images which display images from other sources. Besides , the ORIGINAL SOURCE you cite must clearly indicate that the image is a "free to use" public image.
Google sourced the image from an article written by Sudhanshu Kumar which was published in medium.com. The author (Sudhanshu) himself purchased it from a commercial stock photo company (see example here).
Therefore, it is a commercial stock image that is available for licensing at a price. That also means you cannot use it unless you have signed up with a Stock Photo company and have their permission to use it.
Ok, thanks for informing. I have removed that image.
Hi @madhuri002
Thanks for the quick action.
There are many sources of free images. You should use images from these sources always to avoid being caught breaching copyright.
Some of the sources of free images are:
Unsplash
Pixabay
Pexels
FreeImages
Pxfuel
When you use these free images use the attribution format required by these free image websites and not just the "source" link as ill advised by most of the communities on Steem. Some creators do not ask for credit to be given. Yet, I would advise you give credit to show your gratitude. That is the least you can do.